It’s just under a month since iOS 16.1.1 came out for Apple iPhone users, fixing a pair of bugs that were listed with the worrying words “a remote user may be able to cause unexpected app termination or arbitrary code execution”.
Both macOS 13 Ventura and iPadOS got updated at the same time, with a pair of security bulletins published on Apple’s web site.
Now, there’s another security update, apparently moving iPhone users only up to version iOS 16.1.2.
We did it so we could report back to you
We have installed it, and after a comparatively modest download (by Apple standards, at least) of about 250MBytes, the reboot-and-update process completed reassuringly quickly, and our phone still seems to be working just fine.
But this update is mysterious even by Apple’s usually tight-lipped standards, with the company living up to, and perhaps even beyond, its official statement that the it “doesn’t disclose, discuss, or confirm security issues until an investigation has occurred and patches or releases are generally available.”
Apple insists that this veil of secrecy exists “[f]or the protection of our customers”, and if silence really is golden when it comes to cybersecurity updates, then we can only assume there’s an awfully serious bug getting fixed this time round.
Indeed, we haven’t yet received an Apple Security Advisory email, which is the usual way we hear about the latest patches, and Apple’s official security update portal HT201222 says nothing more than this:
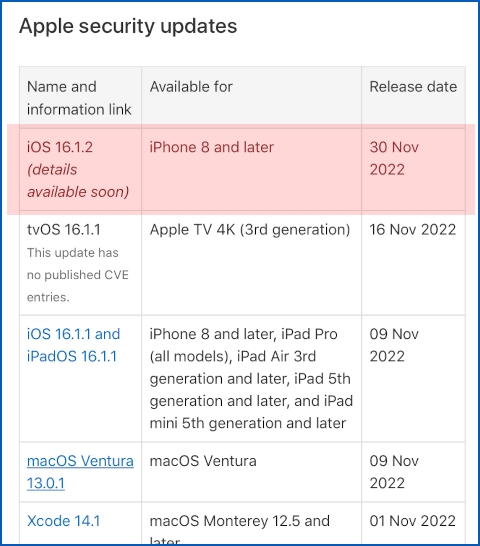
iOS 16.1.2 (details available soon) – iPhone 8 and later – 30 Nov 2022
It’s now 2022-12-02, two days after than the official release date shown above, and we can’t tell you anything more than what we learned from the popup that appeared when we went to Settings > General > Software Update.
This assured us that “this update provides important security updates”, and sent us back on a fruitless loop back to the uninformative HT201222 page for “information about the security content”:
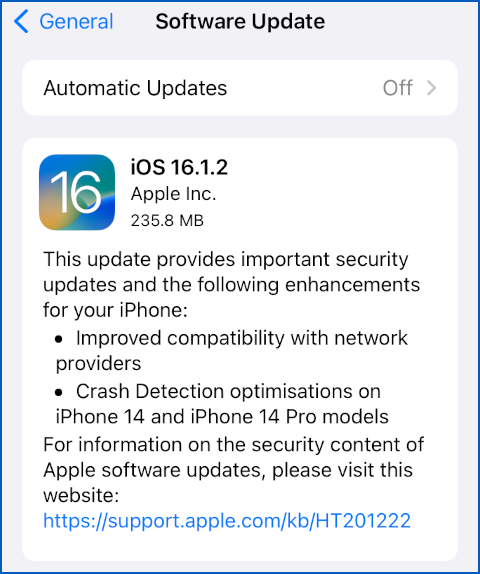
As you can see from the HT20122 screenshot above, this is, for now at least [2022-12-02T21:00Z], an iPhone-only patch, with no updates listed for any versions of iPadOS, macOS or Apple’s Watch and TV platforms.
What to do?
As mentioned above, we updated right away, on the grounds that the mystery only served to convince us that something serious was probably afoot…
…and because we are in the fortunate position of having an Android phone to fall back on if something goes wrong.
We therefore figured we’d take one for the team (by which we mean for the Naked Security community!) and see if there were any compelling reasons to advise you against the update.
Fortunately, we didn’t encounter any trouble that made us think you shouldn’t update, and many iPhone users probably either already have or will soon receive the update automatically.
But if, like us, you prefer to have at least some technical information to go on first, then, as we pointed out right in the headline itself, you’ll find Apple less communicative than ever this time.
Keep your eyes on that HT20122 portal page to keep up with the full story, and to watch out in case other Apple platforms (e.g. iPadOS, macOS) or earlier supported versions (e.g. iOS 15) get belated-but-related updates for the same security holes.
You’re welcome.

Al Varnell
It has always been Apple Security policy to not publish details of a security fix until all OSs needing that fix have been updated, so it’s not at all surprising to me that details have not yet been provided in that no other OS has received an update since iOS 16.1.2 was released. As a minimum, I would guess that iPadOS needs the patch and perhaps other related OS.
Paul Ducklin
That may be Apple’s policy but [a] they have occasionally violated it when it suited them and [b] it’s not IMO as helpful to their customers as they claim.
Are there going to be other patches? Are other platforms at risk? Are other iOS versions at risk? Do they need updates and will at some random time get them? Do they need updates but will just be ignored? Or are they suddenly out of support for ever more? Enquiring minds want to know…
(Anyway, the policy, which I quoted word-for-word in the article, doesn’t say that information is suppressed until all OSes affected have patches. And we have often seen, say, iOS X get patches with update notes, followed by patched for X-1 with notes to say the same bugs have been fixed there.
The HT201222 web page still says “details available soon”, so at least we know that “soon” means “more than a week”.
If it’s so important that iOS needs an urgent update, it would at least be polite to tell us what we’re defending against and why.
“Your car has been recalled for a safety fix. Please bring it in for a service at once. Note that we aren’t going to tell you whether it’s the brakes, the steering, the engine or the gearbox because this fault also exists in some of our other models but we’re not quite sure which ones yet, and we don’t want those vehicle owners freaking out if it ultimately turns out they were safe all along.”
Al Varnell
“If it’s so important that iOS needs an urgent update, it would at least be polite to tell us what we’re defending against and why.”
The main reason for non-disclosure, especially if it’s a serious vulnerability that exists in other OSs is to prevent it from being exploited in those unpatched OSs. I for one would rather Apple not be so polite as to reveal any details about such things.
Paul Ducklin
It’s not about being polite, it’s about clarity. It’s possible to say what you are defending against and why (e.g. attackers from country X are suspected of trying to install spyware on visiting foreign journalists) without revealing to the world exactly what code fragment is being abused and how the exploit works.
We’ve often seen Apple update iOS version X before now, and list all the modules that were patched and what sort of bug it was (e.g. RCE in WebKit), and then follow up days or weeks later with an update for iOS (X-1) that included exactly the same bug.
Apple rarely reveals bug *details* anyway… but there is a huge difference between knowing some facts and being kept entirely in the dark so you can’t evaluate your own risk at all.
You make it sound as though everyone on iOS below 16 or iPadOS ought to stop using their devices for the time being, if indeed it’s such a serious hole that it would be dangerous even to hint at its nature – especially given that the hole is already known and may already be in use.
[NB. The last sentence of this comment was edited for clarity at 2022-12-11T14:15Z; see the following two comments to see why.]
Al Varnell
“You make it sound as though everyone on iOS below 16 or iPadOS ought to stop using their devices for the time being, if indeed it’s such a serious hole that it would be dangerous even to hint at its nature…”
Sorry I wasn’t clear, I certainly didn’t mean to say any of that. I have no idea how serious the vulnerability is which is why I used the word “if” in addressing that aspect.
“especially given that the hole is already known and already being used.”
Where did you learn that? I thought the premise of this article was that we know absolutely nothing yet about the security aspects of the patch?
Paul Ducklin
Correct, I should have said “given that the hole is already known and may already be in use”. I will edit the comment above and add a note to say “see below” so your new comment is not made to seem confusing :-)