Phishing scams that try to trick you into putting your real password into a fake site have been around for decades.
As regular Naked Security readers will know, precautions such as using a password manager and turning on two-factor authentication (2FA) can help to protect you against phishing mishaps, because:
- Password managers associate usernames and passwords with specific web pages. This makes it hard for password managers to betray you to bogus websites by mistake, because they can’t put in anything for you automatically if they’re faced with a website they’ve never seen before. Even if the fake site is a pixel-perfect copy of the original, with a server name that’s close enough be almost indistinguishable to the human eye, the password manager won’t be fooled because it’s typically looking out for the URL, the whole URL, and nothing but the URL.
- With 2FA turned on, your password alone is usually not enough to log in. The codes used by 2FA systems typically work once only, whether they’re sent to your phone via SMS, generated by a mobile app, or computed by a secure hardware dongle or keyfob that you carry separately from your computer. Knowing (or stealing, buying or guessing) only your password is no longer enough for a cybercriminal to falsely “prove” they are you.
Unfortunately, these precautions can’t immunise you completely against phishing attacks, and cybercriminals are getting better and better at tricking innocent users into handing over both their passwords and their 2FA codes at the same time, as part of the same attack…
…at which point the crooks immediately try to use the combination of username + password + one-time code they just got hold of, in the hope of logging in quickly enough to get into your account before you realise there’s anything phishy going on.
Even worse, the crooks will often aim to create what we like to call a “soft dismount”, meaning that they create a believable visual conclusion to their phishing expedition.
This often makes it look as though the activity that you just “approved” by entering your password and 2FA code (such as contesting a complaint or cancelling an order) has completed correctly, and therefore no further action is necessary on your part.
Thus the attackers not only get into your account, but also leave you feeling unsuspicious and unlikely to follow up to see if your account really has been hijacked.
The short but winding road
Here’s a Facebook scam we received recently that tries to lead you down exactly that path, with differing levels of believability at each stage.
The scammers:
- Pretend that your own Facebook page violates Facebook’s terms of use. The crooks warn that this could lead to your account being shut down. As you know, the brouhaha currently erupting on and around Twitter has turned issues such as account verification, suspension and reinstatement into noisy controversies. As a result, social media users are understandably concerned about protecting their accounts in general, whether they’re specifically concerned about Twitter or not:
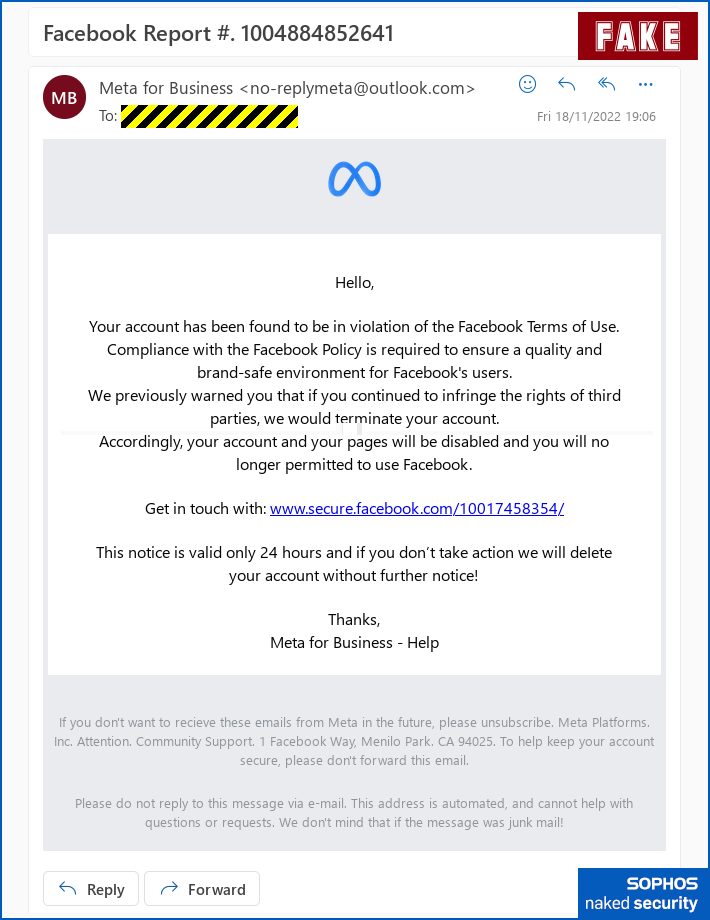
The unsolicited email “warning” that starts it all. - Lure you to a real page with a
facebook.comURL. The account is fake, set up entirely for this particular scam campaign, but the link that shows up in the email you receive does indeed lead tofacebook.com, making it less likely to attract suspicion, either from you or from your spam filter. The crooks have titled their page Intellectual Property (copyright complaints are very common these days), and have used the offical logo of Meta, the parent company of Facebook, in order to add a touch of legitimacy: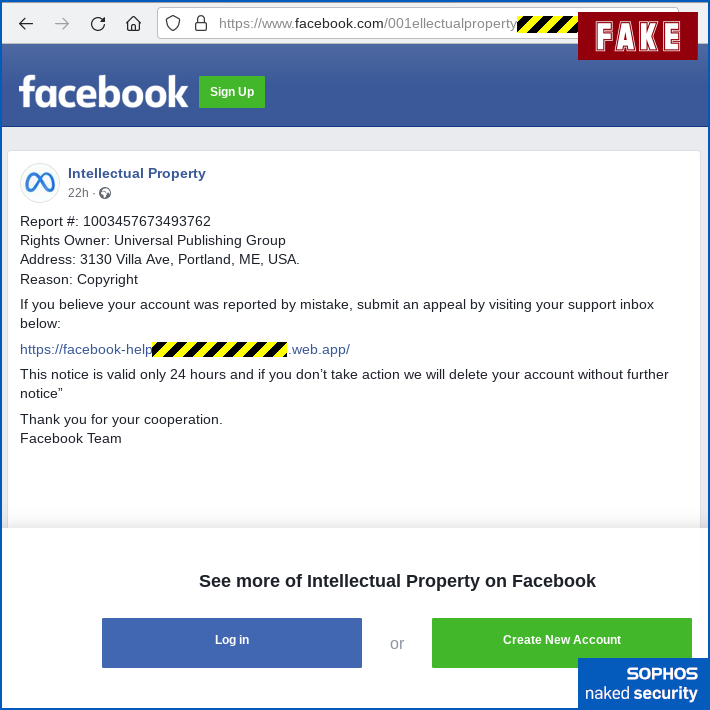
A fraudulent user account page with an official-looking name and icon. - Provide you with a URL to contact Facebook to appeal against cancellation. The URL above doesn’t end in
facebook.com, but it starts with text that makes it looks like a personalised link of the formfacebook-help-nnnnnn, where the crooks claim that the digitsnnnnnnare a unique identifier that denotes your specific case: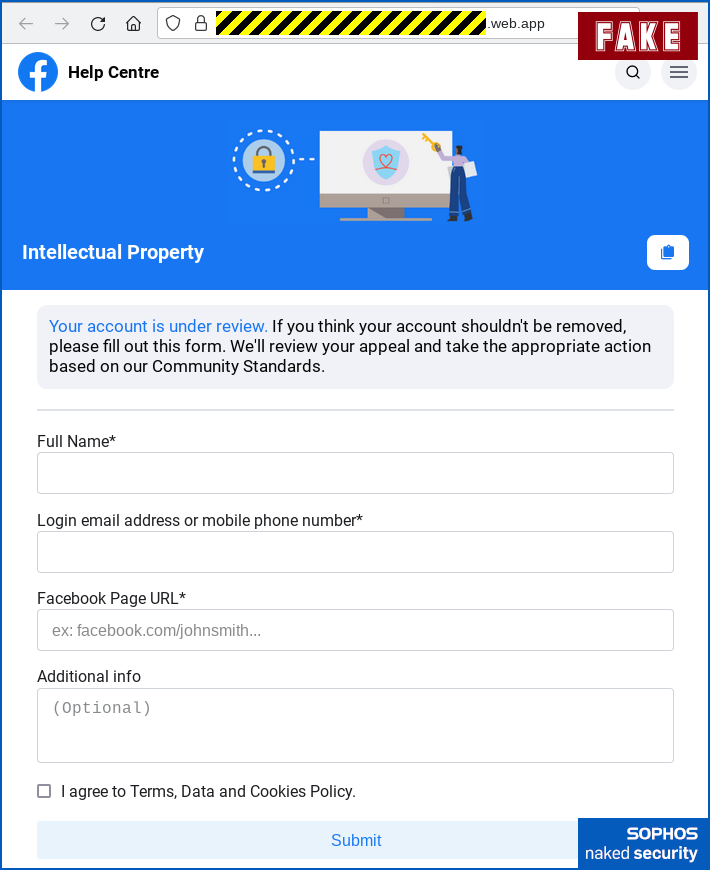
The phishing site pretends to bea “personalised” page about your complaint. - Collect largely innocent-sounding data about your Facebook presence. There’s even an optional field for Additional info where you’re invited to argue your case. (See image above.)
Now “prove” yourself
At this point, you need to provide some proof that you are indeed the owner of the account, so the crooks then tell you to:
- Authenticate with your password. The site you’re on has the text
facebook-help-nnnnnnnin the address bar; it uses HTTPS (secure HTTP, i.e. there’s a padlock showing); and the branding makes it look similar to Facebook’s own pages: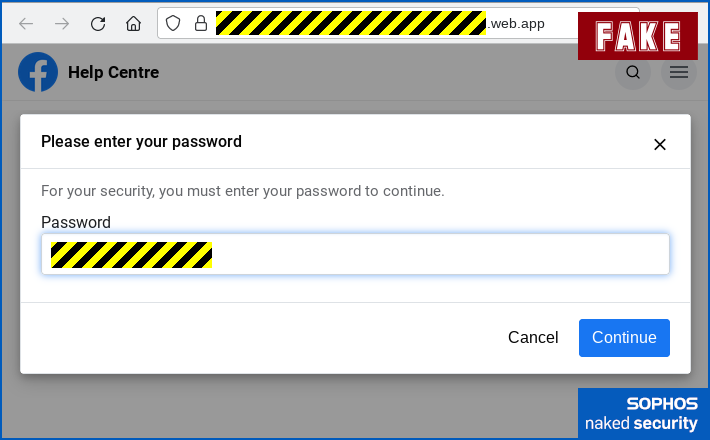
The crooks ask you to “prove” your ID via your password. - Provide the 2FA code to go with your password. The dialog here is very similar to the one used by Facebook itself, with the wording copied directly from Facebook’s own user interface. Here you can see the fake dialog (top) and the real one that would be displayed by Facebook itself (bottom):
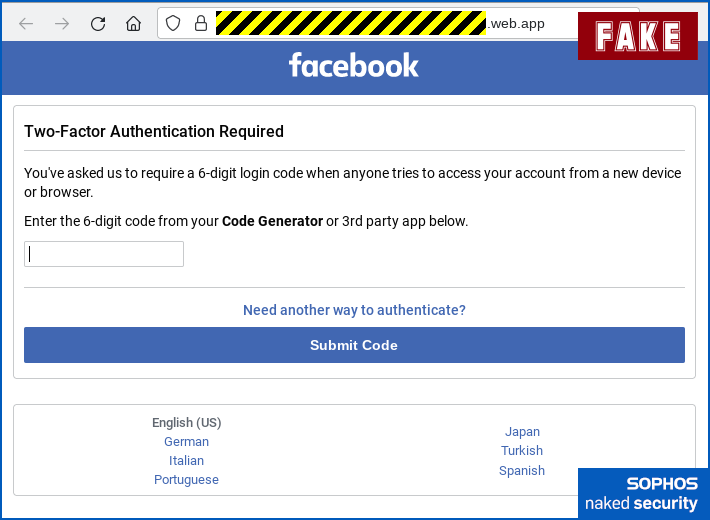
Then they ask for your 2FA code, just like Facebook would. 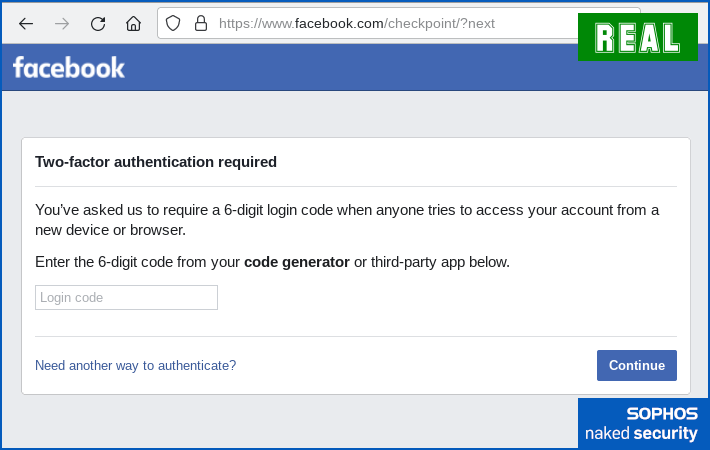
The real 2FA dialog used by Facebook itself. - Wait up to five minutes in the hope that the “account block” may be removed automatically. The crooks play both ends here, by inviting you to leave well alone in order not to interrupt a possible immediate resolution, and suggesting that you should stay on hand in case further information is requested:
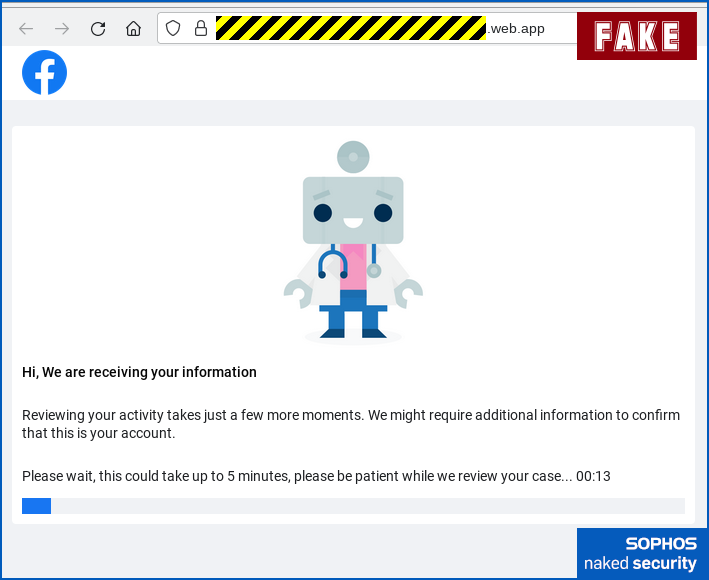
As you can see, the likely result for anyone who got sucked into this scam in the first place is that they’ll give the crooks a full five-minute window during which the attackers can try logging into their account and taking it over.
The JavaScript used by the criminals on their booby-trapped site even appears to contain a message that can be triggered if the victim’s password works correctly but the 2FA code they supplied doesn’t:
The login code you entered doesn't match the one sent to your phone. Please check the number and try again.
The end of the scam is perhaps the least convincing part, but it nevertheless serves to shift you automatically off the scammy site and to land you back somewhere entirely genuine, namely Facebook’s official Help Center:
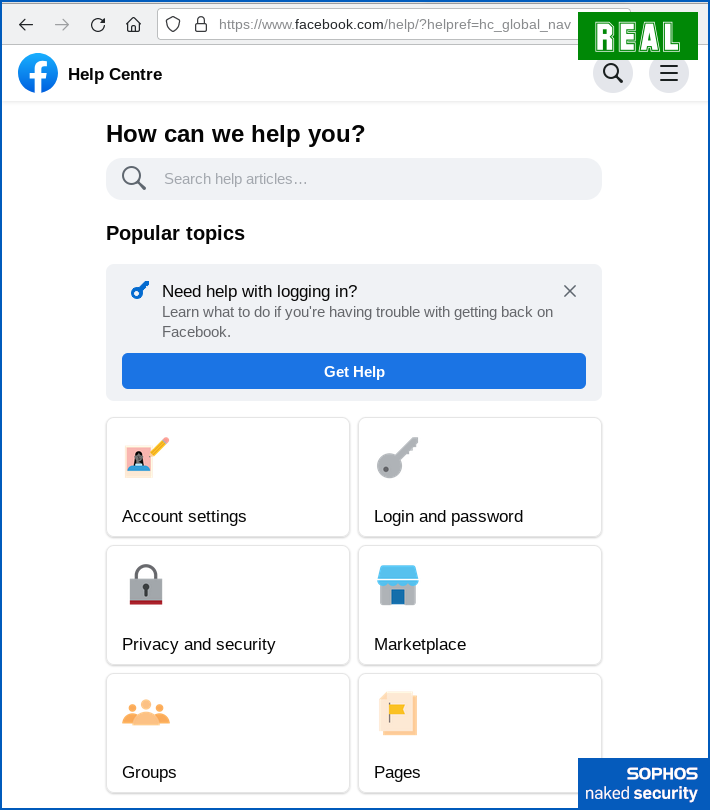
What to do?
Even if you aren’t a particularly serious social media user, and even if you operate under a pseudonym that doesn’t obviously and publicly link back to your real-life identity, your online accounts are valuable to cybercriminals for three main reasons:
- Full access to your social media accounts could give the crooks access to the private aspects of your profile. Whether they sell this information on the dark web, or abuse it thesmselves, its compromise could increase your risk of identity theft.
- The ability to post via your accounts lets the crooks peddle misinformation and fake news under your good name. You could end up kicked off the platform, locked out of your account, or in public trouble, unless and until you can show that your account was broken into.
- Access to your chosen contacts means the crooks can aggressively target your friends and family. Your own contacts are not only much more likely to see messages that come from your account, but also more likely to take a serious look at them.
Simply put, by letting cybercriminals into your social media account, you ultimately put not just yourself but also your friends and family, and even everyone else on the platform, at risk.
What to do?
Here are three quick-fire tips:
- TIP 1. Keep a record of the official “unlock your account” and “how to deal with intellectual property challenges” pages of the social networks you use. That way, you never need to rely on links sent via email to find your way there in future. Common tricks used by attackers include concocted copyright infringements; made-up infringements of Terms and Conditions (as in this case); bogus claims of fraudulent logins you need to review; and other fake “issues” with your account. The crooks often include some time pressure, as in the 24-hour limit claimed in this scam, as further encouragement to save time by simply clicking through.
- TIP 2. Don’t be tricked by the fact that the “click-to-contact” links are hosted on legitimate sites. In this scam, the initial contact page is hosted by Facebook, but it’s a fraudulent account, and the phishing pages are hosted, complete with a valid HTTPS certificate, via Google, but the content that’s served up is bogus. These days, the company hosting the content is rarely the same as the individuals creating and posting it.
- TIP 3. If in doubt, don’t give it out. Never feel pressured to take risks to complete a transaction quickly because you’re afraid of the outcome if you take time to stop, to think, and only then to connect. If you aren’t sure, ask someone you know and trust in real life for advice, so you don’t end up trusting the sender of the very message you aren’t sure you can trust. (And see TIP 1 above.)
Remember, with Black Friday and Cyber Monday coming up this weekend, you’ll probably be receiving lots of genuine offers, plenty of fraudulent ones, and any number of well-meant warnings about how to improve your cybersecurity specifically for this time of year…
…but please keep in mind that cybersecurity is something to take seriously all year round: start yesterday, do it today, and keep it up tomorrow!

Bryan
A Facebook scam aimed at Facebook users, hosted on the very Facebook platform they’re frightened into losing access to.
Meta platforms, indeed.
Bryan
I’m a bit surprised that co-opting the “Meta” logo didn’t trigger a Big Brother Red Flag in the Facebook backend infrastructure.
These days–with all the data collection, facial recognition, and machine learning–it’d not be much of a stretch for that to trigger a manual “hey check this out” prompt to the DRM division, if not an anti-phishing task force.
Paul Ducklin
I wondered that, too. The company’s own logo matched with an account title of “Intellectual Property” would seem to be a self-descriptive indicator of intellectual property misbehaviour for a company that is expected to mediate in intellectual property disputes on its platform.
Sometimes, it’s hard to imagine the phrase “machine learning” without adding in your head the words, “without understanding”, or to hear the words “artificial intelligence” without thinking, “says what it is on the tin”.
Example: when YouTube shows me an ad that I skip after 5 seconds… then plays the very same ad about two minutes later, and then again, and *again*, and AGAIN, even if I end up putting more and more effort into timing my next “click to skip” to get it closer and closer to the 5-second cutoff every time, as a signal of my obvious disaffection for the product being advertised. (Ironically, the ads that I seem to be bombarded with most aggressively of all are for Gra**arly, which is supposed to help me improve my communications skills.)
Or when my iPhone sees me type “https COLON SLASH SLASH” immediately followed by “nak”, and not only doesn’t realise I am almost certainly about to enter the domain name that is most obviously intertwined with both my work and personal digital life these days, but also waits until I have typed “nakedsecurity DOT” and corrects my typing by assuming I want to start a brand new sentence with “Naked Security”, casually finishing the previous sentence with https://, which isn’t even a word. That’s not machine stupidity, it’s machine vexatiousness! (Though perhaps true machine vexatiousness would be a sign of both learning and intelligence, albeit a disquieting one.)
Perhaps I’m just holding it wrong?
Bryan
The Grammarly ads are indeed rather persistent. And yes, I also find it ironic. Even though I can no longer name the difference between present perfect, past subjunctive, and future confusing–I still tend to use the structures correctly.
Now, if there was a product called Brevitee, capable of consolidating my twenty-seven sentences into a more-concise-yet-no-less-coherent-six… that’s a product which could help me.
Thanks for the chuckle. Evidently I’m usually holding my keyboard wrong as well.
Dave Bolt
Tip 1 sounds fine, but Facebook keep changing things so it might not look like that the next time you need to use it :(
Paul Ducklin
As long as you remember roughly how you found out where to go last time, you will at least know that the information can be found by searching by yourself…
…rather than relying on contact data in a message or via a link you aren’t sure of!
(My experience has been that the when FB changes links and processes of this sort, there’s often an overlap period when the old page or menu option tells you about the new one. And if the old one stops working it’s usually obvious that’s because something has changed rather than that something is temporarily broken.)
Wilbur
I am continually amazed when scammers use obviously phony email addresses; like a major business will use generic outlook, hotmail, gmail, etc accounts. In this case they used [Meta for Business no-replymeta@outlook.com]. Really? Facebook/Meta would use generic email instead of their own branding? I have received scam emails purporting to be from major banks using Gmail addresses. Domains (the whole thing, not the truncated version) are one of the first things I look at with messages like this.
Common Sense
Scam emails are easy to catch out. As long as you pay attention to the email address of the sender.
Alot of them are just generic free 2 use email accounts.
Paul Ducklin
That’s true, as long as you replaced your opening sentence with “Scam emails are often easy to catch out.”
The problem comes when people get so used to relying on spotting “obvious” errors, given that so many crooks make them, that they accept emails that don’t make any “obvious” mistakes as genuine, because “obvs.” the criminals wouldn’t take that much care.
(Some do. So make them pay if they *do* make an obvious mistake, but don’t let them trick you just because they *don’t*!)
Sarah Lee
I think I somehow sell victim to this. I’m locked out of my account and it looks like my mobile number was removed from the account in general I actually got an email about it but I didn’t remove it but when it was removed it also removed it under the two-way authenticator because when it says to resend a code it pulls up a box which should confirm the mobile number and then it allows you to click okay assuming it’s resending the code but the box that should contain the mobile number is empty. This is a disaster and there’s no fix for it. I’ve done the whole send in your ID tell us who you are thing and they’ve approved it but that just logs me in which I can do because I know my password it’s a two way authentication and it’s got me tripped up every single time. And there’s no way to get hold of any human being to let them know what’s happening. I even went as far as to hand write a letter to the PO box that pops up when you click contact us via meta. I’m not expecting a response from snail mail but I’m desperate! Does anyone know how to fix this or reach somebody I can provide screenshots to show you this is legit happening and there’s no way to let Facebook know about it. At this point I’m just sitting here hoping though do away with the SMS to authenticator technology and I figured that if it doesn’t exist I can’t be locked out anymore maybe? Any help or knowledge on this would be so so appreciated!
Paul Ducklin
If you can still log in to your account, without even needing a 2FA code, then it sounds as though the problem is that 2FA is turned off on the account… if 2FA were turned on but not connected to your phone number, surely you wouldn’t be able to login at all?