Microsoft on Tuesday released patches for 62 vulnerabilities in nine Microsoft product families. This includes nine Critical-class issues affecting Exchange and Windows. As in previous months, the majority of CVEs affect Windows, with a total of 41 CVEs, followed by eight in Office and four in Exchange.
As with October’s release, Azure admins get a welcome breather, with only two patches – one a Remote Code Execution bug, the other an Elevation of Privilege vulnerability, both rated Important. SharePoint and the Open Database Connectivity (ODBC) driver also come in at two apiece, while there’s one patch each for Visual Studio, .NET, and Dynamics 365.
One vulnerability (CVE-2022-41091, a Mark of the Web bypass bug) has been publicly disclosed and exploited in the wild. Three others (CVE-2022-41073, a Print Spooler Elevation of Privilege vulnerability; CVE-2022-41125, a CNG Key Isolation Elevation of Privilege vulnerability; and CVE-2022-41128, a Windows Scripting Languages Remote Code Execution Vulnerability) have been exploited. According to Microsoft, everything else is undisclosed and unexploited.
It’s worth noting that CVE-2022-41040 and CVE-2022-41082 (two flaws in Exchange, collectively known as ProxyNotShell) are not among the issues listed in this month’s release. However, CVE-2022-41080 (Microsoft Exchange Server Elevation of Privilege Vulnerability), a Critical Elevation of Privilege bug, has been patched; Microsoft assesses that exploitation is more likely in the latest software release. (Microsoft released patches for CVE-2022-41040 and CVE-2022-41082 under separate cover, pointing users directly to the Microsoft Update catalog and describing guidance for customers who had already followed previous mitigation advice. As such, those patches are not tallied as part of this Patch Tuesday release.)
By the numbers
- Total Microsoft CVEs: 62
- Total advisories shipping in update: 1
- Publicly disclosed: 1
- Exploited: 4
- Exploitation more likely in latest version: 18
- Exploitation more likely in older version: 10
- Severity
- Critical: 9
- Important: 53
- Moderate: 0
- Low: 0
- Impact
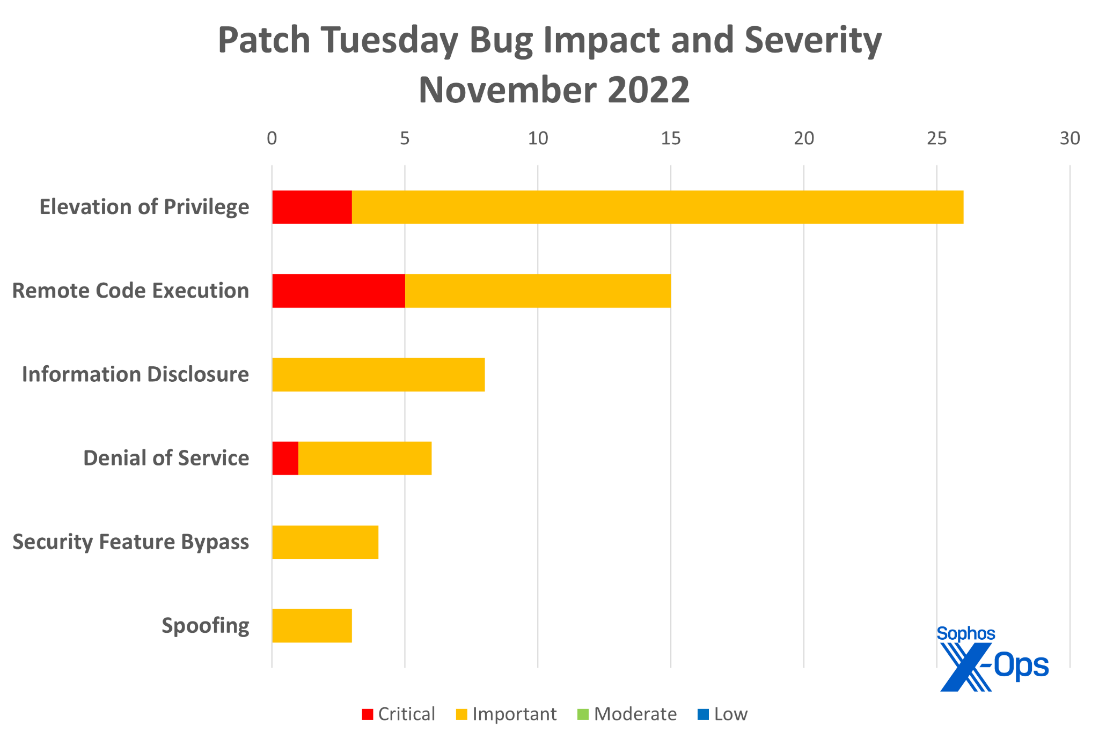
- Elevation of Privilege: 26
- Remote Code Execution: 15
- Information Disclosure: 8
- Denial of Service: 6
- Spoofing: 3
- Security Feature Bypass: 4
Figure 1: Elevation of Privilege vulnerabilities are top of the pile
- Products:
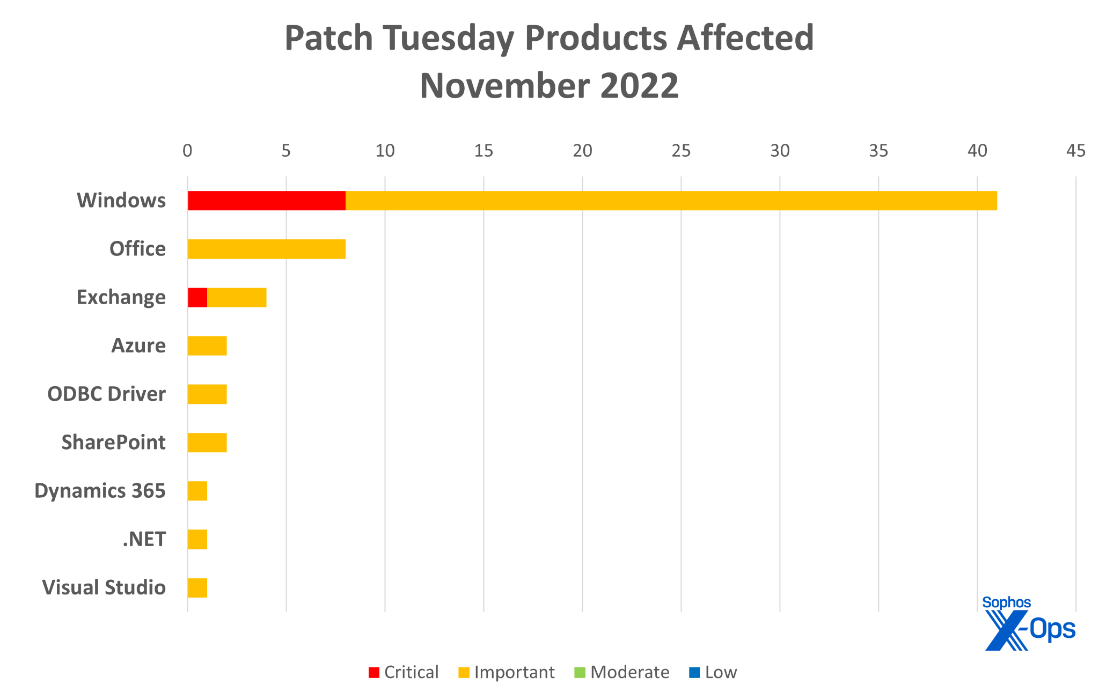
- Microsoft Windows: 41
- Office: 8
- Exchange: 4
- SharePoint: 2
- Azure: 2
- ODBC Driver: 2
- Visual Studio: 1
- .NET: 1
- Dynamics 365: 1
Figure 2: Windows vulnerabilities continue to dominate releases, with Office and Exchange a distant second
Notable vulnerabilities
CVE-2022-41091 (Windows Mark of the Web Security Feature Bypass Vulnerability)
There are two of these in this month’s release (the other is CVE-2022-41049, reported by researcher Will Dormann), but we’ll focus on the one that has been publicly disclosed and reportedly exploited. Mark of the Web (MOTW) is a security mechanism in Windows – an Alternate Data Stream (ADS) tag which is added to files that originate from untrusted zones. As we noted in our recent research on attackers using archive and disk image formats (likely a result of Microsoft disabling macros by default in documents from the internet, based on MOTW), it’s not infallible. Information about at least one MOTW bypass in Windows was circulating on Twitter back in July, and was reportedly being exploited in October.
CVE-2022-41125 (Windows CNG Key Isolation Service Elevation of Privilege Vulnerability)
Another bug that has been exploited in the wild, according to Microsoft, this is an elevation of privilege vulnerability which could lead to an attacker gaining SYSTEM privileges, with low attack complexity and no user interaction required. CNG Key Isolation is a service hosted in the Local Security Authority (LSA) process, and is part of Windows’ cryptography stack. Microsoft rates the severity as Important.
CVE-2022-41088 (Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability)
This is a Remote Code Execution vulnerability, rated Critical, with a base CVSS 3.1 score of 8.1. To successfully exploit it, an attacker would need to craft a malicious PPTP packet and send it to a PPTP server, potentially resulting in remote code execution on that server. The good news: it hasn’t been publicly disclosed, or exploited, and Microsoft rates the chance of exploitation as less likely in both older and newer versions. It also appears to be quite a complex attack, and an attacker would need to win a race condition to exploit the bug. There are two similar vulnerabilities in this month’s release, both rated Critical and both affecting PPTP (CVE-2022-41039 and CVE-2022-41044). In each case, an unauthenticated attacker could a crafted connection request to a RAS server, leading to remote code execution.
CVE-2022-41118 (Windows Scripting Languages Remote Code Execution Vulnerability)
Another Critical Remote Code Execution bug, and this one is rated more likely to be exploited in both older and newer versions. The vulnerability affects both the JScript9 and Chakra scripting languages, but there are some prerequisites: an attacker has to host a malicious server, and convince a victim with an affected version of Windows to visit it. The attacker would then have to win a race condition to successfully exploit the vulnerability.
CVE-2022-37967 (Windows Kerberos Elevation of Privilege Vulnerability)
This flaw is rated Critical and assessed as more likely to be exploited in the latest software release. It’s accompanied by CVE-2022-37966, another Critical Elevation of Privilege bug affecting Kerberos. To successfully exploit it and gain administrator privileges, an attacker would need to leverage cryptographic protocol vulnerabilities in the Windows Kerberos AES-SHA1 cipher suite. If the attacker gains control of the service that is allowed for delegation, they could modify the Kerberos PAC (Privileged Attribute Certificate) to elevate their privileges.
CVE-2022-41128 (Windows Scripting Languages Remote Code Execution Vulnerability)
This issue affects JScript9 and is assessed as Critical in severity. To make use of it, an attacker would have to entice a user running an affected version of Windows to visit a malicious website or share server. The issue appears to affect all versions of Windows, including older versions, which will take the patch as part of their month update rollups. The find is credited to Clément Lecigne of Google’s Threat Analysis Group and the bug is known to be under active exploit.
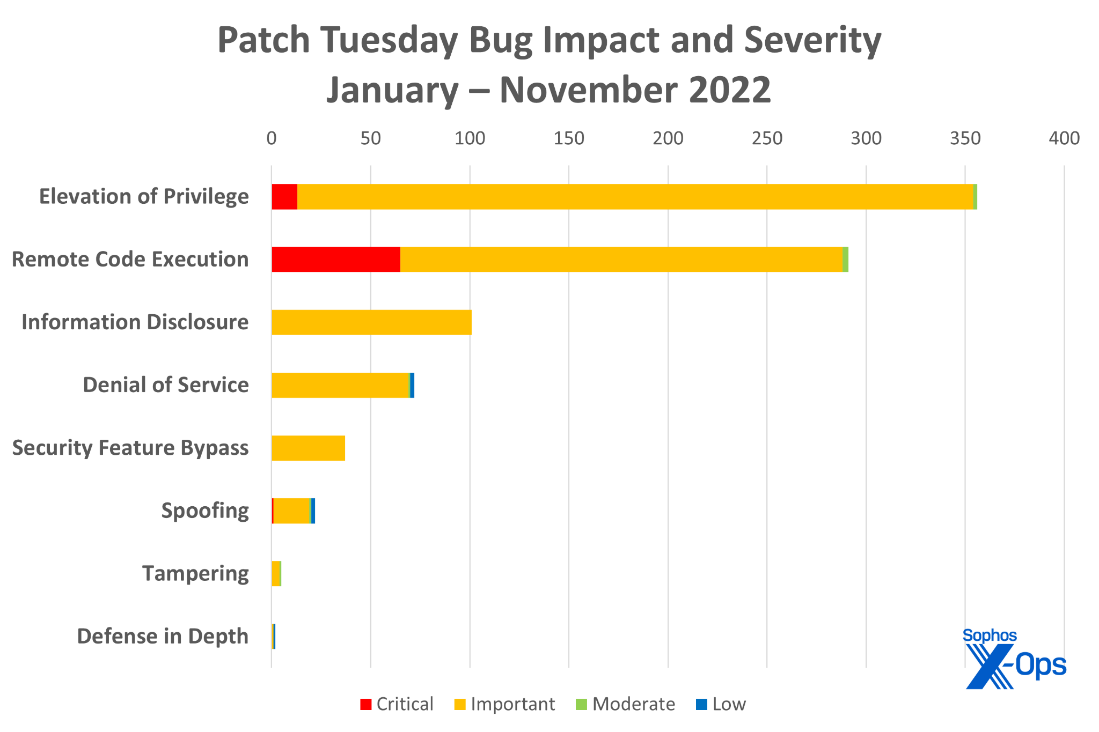
Figure 3: Elevation of Privilege vulnerabilities still lead as we head towards the end of the year, although the Remote Code Execution category contains significantly more Critical bugs
Sophos protection
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2022-41113 | Exp/2241113-A |
(Ever wondered about behavior names, by the way? Sophos’ naming conventions line up with the MITRE ATT&CK framework. Details are available elsewhere on our site.)
As you can every month, if you don’t want to wait for your system to pull down the updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system’s architecture and build number.