SSN is an abbreviation that’s specific to America, and DOB is shorthand that’s specific to the English language.
Nevertheless, their meanings are widely known throughout the world, not least because of their widespread use in reports and discussions about identity theft and cybercrime.
SSN is short for Social Security Number, which is effectively a US national ID number, and DOB translates into date of birth.
Ironically, of course, an SSN doesn’t actively identify you – it’s really just a label that can be used as a unique identifier for record-keeping purposes.
In other words, simply knowing someone’s SSN doesn’t prove you are that person.
Unfortunately, however, knowing someone’s SSN (or the equivalent personal identifier in your country) is a good starting point if you’re an identity thief, because it can often be combined with other personal information to get past identity checks.
The theory is that if there’s, say, a 1% chance that you’ve figured out someone’s SSN and a 5% chance of guessing their DOB, then there’s only a 1% × 5% chance (that’s 0.01 × 0.05 = 0.0005) of getting both of them right, and that multiplied-together chance of 0.05% chance represents odds of just 1 in 2000.
Roll in other personal details such as a passport number, a scan of a driving licence, precise home address, phone number and so on…
…and, in theory at least, you can keep trimming the probability down until it’s as good as certain that the only way someone could provide all the data you’re requesting is if they were, indeed, the true owner of the the SSN they presented to start with.
This theory, of course, is bunkum.
You can only multiply probabilities together as we did above if they are completely independent of each other, such as two consecutive coin tosses.
But the probabilities that someone can “guess” both your SSN and your DOB correctly are not independent.
For a start, you need to factor in the probability that if they’e found a way to discover your SSN, then they may have found a similar way to discover your DOB at the same time.
In some countries, the local equivalents of SSNs are far from random. In South Africa, for example, the country’s national ID numbers are constructed from data including your DOB (in the abbreviated form YYMMDD), gender, and citizenship status, together with a sequence number that depends on how many other people were born on the same day as you. In other words, if you already know someone’s ID number then you have about a 50-50 chance of figuring out their DOB correctly, given that there is no one still alive who was born in the 1800s. Of course, if also you know roughly how old they are, you can be pretty sure whether they were born in this millennium or the last, so you’ll know whether their real DOB starts 19xx or 20xx. In such cases, if you know someone’s ID, the probability of “guessing” their DOB is effectively 100%. Likewise, if you know their DOB, their gender and where they were born, you can almost certainly predict 8 digits of the 11 digits required to construct their 13-digit ID number yourself. (The 12th digit is almost always 8, and the 13th digit is a checksum computed from the others.)
SSNs rarely get breached on their own
As you can imagine, data breaches where crooks get hold of personal data that includes SSNs rarely come away with just those SSNs, given that few database files include a list of SSNs and no other data at all.
When crooks penetrate company networks, for instance, they often go after HR records because employers are usually required both by law and operational necessity to collect significant amounts of personal information about each employee.
Employers typically need to retain evidence that you are who you claim, and that you’re legally entitled to seek work in the country; they need to know how to pay you; they’re obliged to report your earnings to the tax office; they may need to keep your driving licence on file if you’re expected to drive for your job; and much more.
Furthermore, as we wrote about just yesterday, data in our Active Adversary Playbook 2022 suggests that an increasing number of network intrusions aren’t about disruptive ransomware attacks, they’re about taking the time to accumulate corporate data to sell on to other crooks.
In other words, darkweb data brokers typically don’t just acquire and sell one sort of data point for each victim.
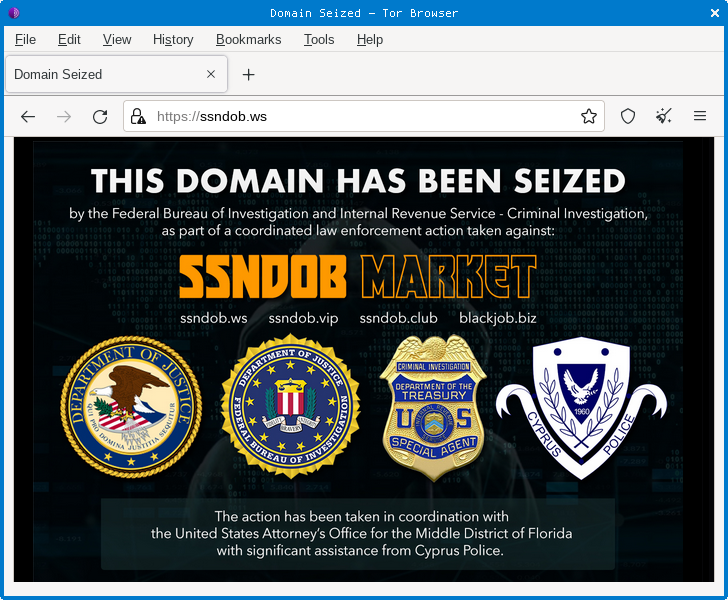
Thus the name SSNDOB Market that you see in the headline – an online data bazaar that wanted visitors to know that it sold at least matched-up SSNs and DOBs, along with other personally identifiable information (PII).
According to the US Department of Justice (DOJ), SSNDOB claimed to have PII for up to 24,000,000 Americans (though we don’t know how much data there really was, or how accurate it was).
The DOJ says that the site’s operators made more than $19,000,000 over the past few years, handing this data on to willing buyers in return for pseudoanonymous payments, typically using Bitcoin.
Unfortunately, the DOJ hasn’t arrested the suspected operators of the SSNDOB Market, but, with the help of law enforcement partners in Latvia and Cyprus, it did get a court warrant allowing it to take over the server names used by the crooked data brokers.
Visitors to any of ssndob.ws, ssndob.vip, ssndob.club and blackjob.biz will no longer end up where they were probably expecting.
Instead, they’ll see this:
This may not be quite the result that the DOJ and its European counterparts were hoping for, but every little helps.
As David Walker of the US FBI remarked in the DOJ’s press release:
These seizures demonstrate the FBI’s strong working relationship with our international partners in disrupting malicious cyber activity Dismantling illicit marketplaces that threaten the privacy and security of the American public is a priority of the FBI.
This is also a good reminder that getting cybersecurity right on your network doesn’t just protect your company, but also protects your employees, your business partners, your suppliers, your customers, and everyone else on the internet, too.
In other words, cybersecurity represents a very attractive sort of altruism: it’s something that you do of necessity, to protect yourself and your business, but that also helps the online world stay safer as a whole.
Don’t be part of the data leakage problem, be part of the solution!
Not enough time or staff? Learn more about Sophos Managed Detection and Response:
24/7 threat hunting, detection, and response ▶

Kevin English
The ssndob*.onion address is still working. Seizing these domain names that were basically marketing on-ramps in a noisy way probably will help their business more than hurt it. This was NOT a server seizure! Calling this an infrastructure seizure is a big stretch. This was a minor metadata seizure. Their servers are still running, they are just now a little harder to find for new wanna-be criminals. Their existing customers know exactly how to reach them.
Paul Ducklin
TBH, I didn’t start off with to “servers” in the headline, to avoid the ambiguity you mentioned, but I ended up doing so because the word “domain” isn’t exactly plain English.
But I agree with you and have now changed it, given that physical property was not actually confiscated. (You didn’t notice that I had imbalanced quote marks in there, too, so I was able to fix that typo quickly at the same time :-)
As an aside, I’m not sure that “metadata”, as you wrote above, is the right word either. Domain ownsership was tranferred, and I don’t think that the jargon word “metadata” quite hits the spot there, at least not in plain English.
I agree that this wasn’t a very severe blow to the crooks, but as I suggested in the article, every little helps. So I am willing to have a “glass half full” outlook in cases like this, even though we may be talking about a small glass to start with, and to say thanks to the FBI+DOJ for at least doing something.
After all, the alternative would be for the FBI to do nothing at all, which I would see as a “glass half empty” situation.