We’re sure you’ve heard of the KISS principle: Keep It Simple and Straightforward.
In cybersecurity, KISS cuts two ways.
KISS improves security when your IT team avoids jargon and makes complex-but-important tasks easier to understand, but it reduces security when crooks steer clear of mistakes that would otherwise give their game away.
For example, most of the phishing scams we receive are easy to spot because they contain at least one, and often several, very obvious mistakes.
Incorrect logos, incomprehensible grammar, outright ignorance about our online identity, weird spelling errors, absurd punctuation!!!!, or bizarre scenarios (no, your surveillance spyware definitely did not capture live video through the black electrical tape we stuck over our webcam)…
…all these lead us instantly and unerringly to the [Delete] button.
If you don’t know our name, don’t know our bank, don’t know which languages we speak, don’t know our operating system, don’t know how to spell “respond immediately”, heck, if you don’t realise that Riyadh is not a city in Austria, you’re not going to get us to click.
That’s not so much because you’d stand out as a scammer, but simply that your email would advertise itself as “clearly does not belong here”, or as “obviously sent to the wrong person”, and we’d ignore it even if you were a legitimate business. (After that, we’d probably blocklist all your emails anyway, given your attitude to accuracy, but that’s an issue for another day.)
Indeed, as we’ve often urged on Naked Security, if spammers, scammers, phishers or other cybercriminals do make the sort of blunder that gives the game away, make sure you spot their mistakes, and make them pay for their blunder by deleting their message at once.
KISS, plain and simple
Sometimes, however, we receive phishing tricks that we grudgingly have to admit are better than average.
Although we’d hope you’d spot them easily, they might nevertheless have a good chance of attracting your attention because they’re believable enough, like this one from earlier today:
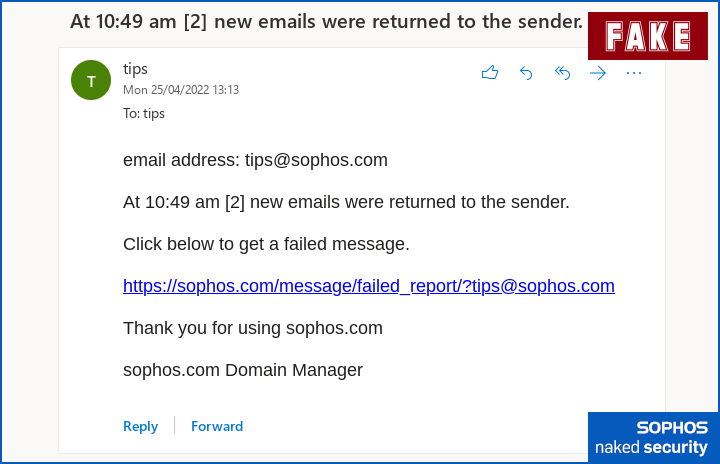
At 10:49 am [2] new emails were returned to the sender.
Click below to get a failed message.
https://sophos.com/message/failed_report/?tips@sophos.com
Thank you for using sophos.com
sophos.com Domain Manager
OK, so the English grammar and usage isn’t quite right, and our IT team would know who they are, so they wouldn’t sign off as company.name Domain Manager…
…but if we were a smaller company, and we’d outsourced our IT and email services, this sort of message might not so obviously be out of place.
Also, these crooks have used the simple and effective trick of creating a clickable link in which the text of the link itself looks like a URL, as though it was your email software than automatically converted a plain-text-only URL unto a clickable item.
Of course, the email isn’t plain text; it’s HTML, so that the offending link is actually encoded like this…
<a href="somewheredodgy">https://sophos.com/nothereatall</a>
…in the same way, but much more convicingly, than an email link such as…
Click <a href="someweredodgy">here</a> to see the message.
The link doesn’t take you to a real site, of course; it’s diverted to a server that was either set up for this specific scam, or hacked by the crooks to act as a temporary portal for collecting their data:
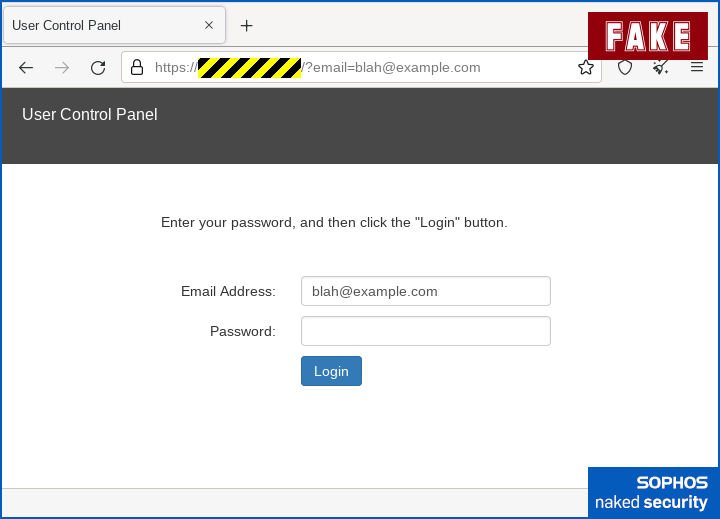
Fortunately, at this point the scam adheres to the KISS principle a bit too fiercely, relying on a web form that’s so stripped down as to be unusual, but it still doesn’t contain any obvious blunders other than the unexpected server name in the address bar.
Amusingly, because the hosting company that the criminals have used is based in Japan, turning JavaScript off results in an error message that we’re guessing the crooks didn’t care about (or perhaps were unable to change), giving you a JavaScript warning in Japanese:
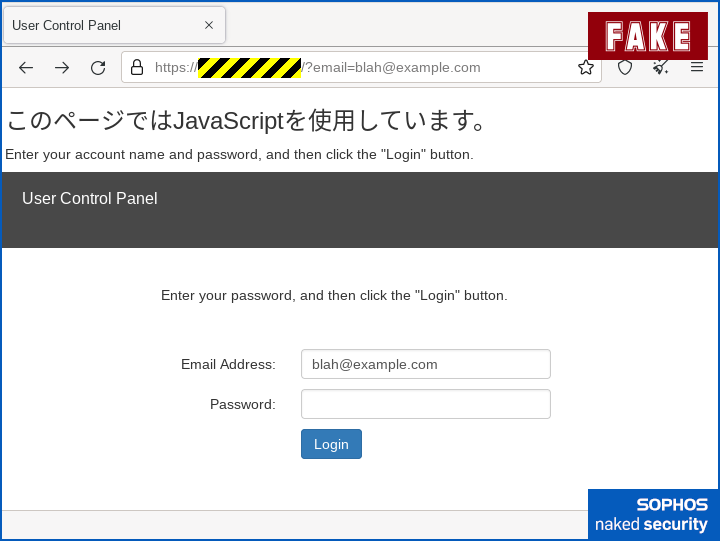
Ironically, the web form works just fine without JavaScript, so if you were to fill in the form and click [Login], the crooks would harvest your username and password anyway.
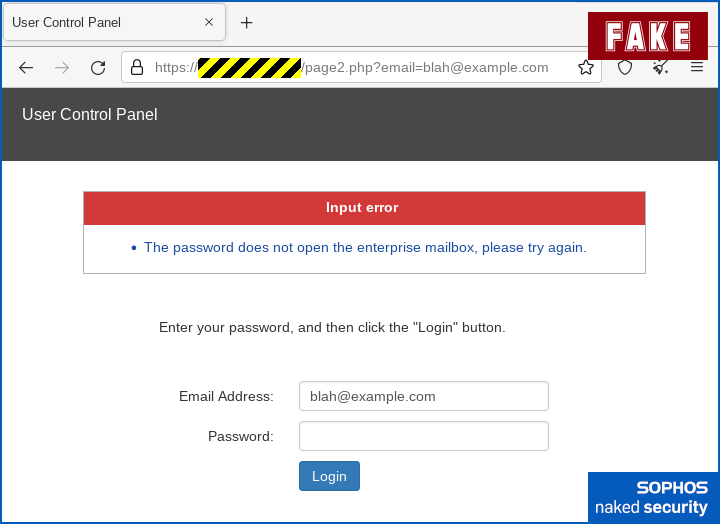
As we often see, the scam page neatly avoids having to simulate a believable login by simply presenting you with an error message, until you your either give up, contact your IT team, or both:
What to do?
- Don’t click “helpful” links in emails or other messages. Learn in advance how to find error messages and other mail delivery information in your webmail service via the webmail interface itself, so you can simply login as usual and then access the needed pages directly. Do the same for the social networks and content delivery sites you use. If you already know the right URL to use, you never need to rely on any links in emails, whether those emails are real or fake.
- Think before you click. The email above isn’t glaringly false, so you might be inclined to click the link, especially if you’re in a hurry (though see point 1 about learning how to avoiding click-throughs in the first place). But if you do click through by mistake, take a few seconds to stop and double-check the site details, which would make it clear you were in the wrong place.
- Use a password manager if you can. Password managers prevent you putting the right password into the wrong site, because they can’t suggest a password for a site they’ve never seen before.
- Report suspicious emails to your own IT team. Even if you’re a small business, make sure all your staff know where to submit suspicious emails samples (e.g.
cybersec911@example.com). Crooks rarely send just one phishing email to one employee, and they rarely give up if their first attempt fails. The sooner someone raises the alarm, the sooner you can warn everyone else.
When it comes to personal data, whether that’s your username, password, home address, phone number, or anything else that you like to keep to yourself, remember this simple rule: If in doubt, don’t give it out.

Bryan
Maybe they didn’t care about the JS warning since most people run it without question, dropping most security precautions the first time they get a popup saying “you can’t view this (video|image|page) unless you enable X.”
Also:
Keep It Simple and Straightforward.
I can’t be the only stupid individual who’s never heard the K.I.S.S. principle articulated with the word “straightforward.”
Paul Ducklin
You heard it here first!
I generally dislike cybersecurity people who still talk about “luzers” and laugh at people who don’t grok technical stuff. Often that lack of grokkery was because some “expert” was a poor teacher, not because the “stupid” person was a poor student.
So a while ago, I reinvented “KISS” with a redefinition of my own that I think is less judgemental and more in keeping with the spirit of the times.
RichardD
I always thought the “stupid” in KISS was aimed at the senior enterprise “software architect” with a penchant for abusing design patterns to the point of absurdity. :)
Tony Pattison
Very helpful and could save us a lot of trouble!
Anonymous
Curious as to the advice being to Delete the email rather than report as Spam/Junk.
Paul Ducklin
If you have somewhere useful to report it, as suggested in Tip 4, then report it and then delete it…
…but delete it second if you don’t delete it first!
Wirtec W
If a mail client plugin could show the real domain when you hover over it for ex
Https://sophos.support.net/ domain : support.net and not sophos as an experienced user would see that would be a great help for non it end users
Paul Ducklin
Most mail clients will do just that. But in this case, because the email looks like plain text (being unadorned and unfancified “straight” HTML), the temptation is to assume that the link *is plain text* and therefore is simply what it says, turned blue and clickable by the helpfulness of your email client.
Thus many users may assume that there is no need to hover as you usually do… the blue text *looks like the actual URL already*, though it is not the URL that the link actually goes to…