Qualifying for a cyber insurance policy today can be a challenging and tedious process. Gone are the days when a simple phone call to an insurance agent and selecting coverage limits lead to obtaining a policy. Today, due to the sharp increase in ransomware attacks and multimillion dollar payouts, along with stricter cybersecurity controls required by underwriters, obtaining cyber insurance is now an essential objective and corporate imperative for organizations, but not a certainty.
Attendees at the recent Sophos virtual cyber insurance event heard from cyber insurance experts on what they need to do to qualify for consideration, as well as tips on how to obtain the best coverage and terms at the most attractive price.
Our experts included Marc Schein, national co-chair of the Cyber Center of Excellence at the world’s largest insurance broker, Marsh McLennan Agency (MMA); James Tuplin, head of international at next-gen speciality insurer Mosaic Insurance; Natalie Graham, head of claims at Mosaic Insurance; Daniel Kasper, cyber risk researcher and economist at Cyber Economics; and Nicholas Cramer, senior director of global cyber risk partnerships at Sophos.
Watch the event on-demand to see the sessions in full.
The economics of cyber insurance
Laying the baseline for emerging trends in the cyber insurance market, Schein said the cost of insured cyber attacks grew by 22% in 2020 and 77% in 2021, but rates for cyber insurance grew much faster. In September 2021, the average rate increase was 128% while the capacity offered — the limits insurance companies were willing to offer — dropped by 23%. The combination of higher rates and reduced coverage effectively is driving up the cost of insurance significantly, he said.
Economist Kasper agrees. The honeymoon that organizations had obtaining cyber insurance at a relatively low price for hefty amounts of coverage are likely gone forever. Now that insurers have had a chance to better judge the market dynamics, as well as judging the relative levels of cyber security controls in place by many of the organizations seeking insurance, the stark realities are coming into focus, and it is not good news for those who are shopping for policies.
“In 2013, we had about a billion dollars in global insurance premiums in cyber,” Kasper said. The next six years the market grew by roughly 30% annually, but at the end of 2019 COVID-19 hit and ransomware skyrocketed.”
Looking at 2018 before ransomware attacks became so prevalent, he said, a cyber insurance carrier would have significantly underpriced the premium cost for a cyber insurance policy for 2019 because the carriers did not have the threat vector for the new ransomware attacks in the pricing model. The market is now addressing those losses in pricing changes.
“We are now in the renewals for 2021 and 2022 and from everything that we have heard so far on the market this year, in 2023, it will be even harsher,” Kaspar said. “It is now a seller’s market.”
If organizations want to buy cyber insurance today, they must show proactive cybersecurity preparations beyond what they had “three or four years ago when you got basically cyber insurance, sometimes even without any security scans or any meaningful information that you had to divulge,” he added.
Rising rates for less coverage
Schein told the attendees that “perhaps the most talked about conversation within cyber risk today is around systemic types of loss and systemic risk.” He noted that an increased awareness of supply-chain based attacks are causing volatility in the market. Attacks such as SolarWinds, cybercriminals breaching Microsoft Exchange, and log4j “started to cause havoc for the insurance marketplace.”
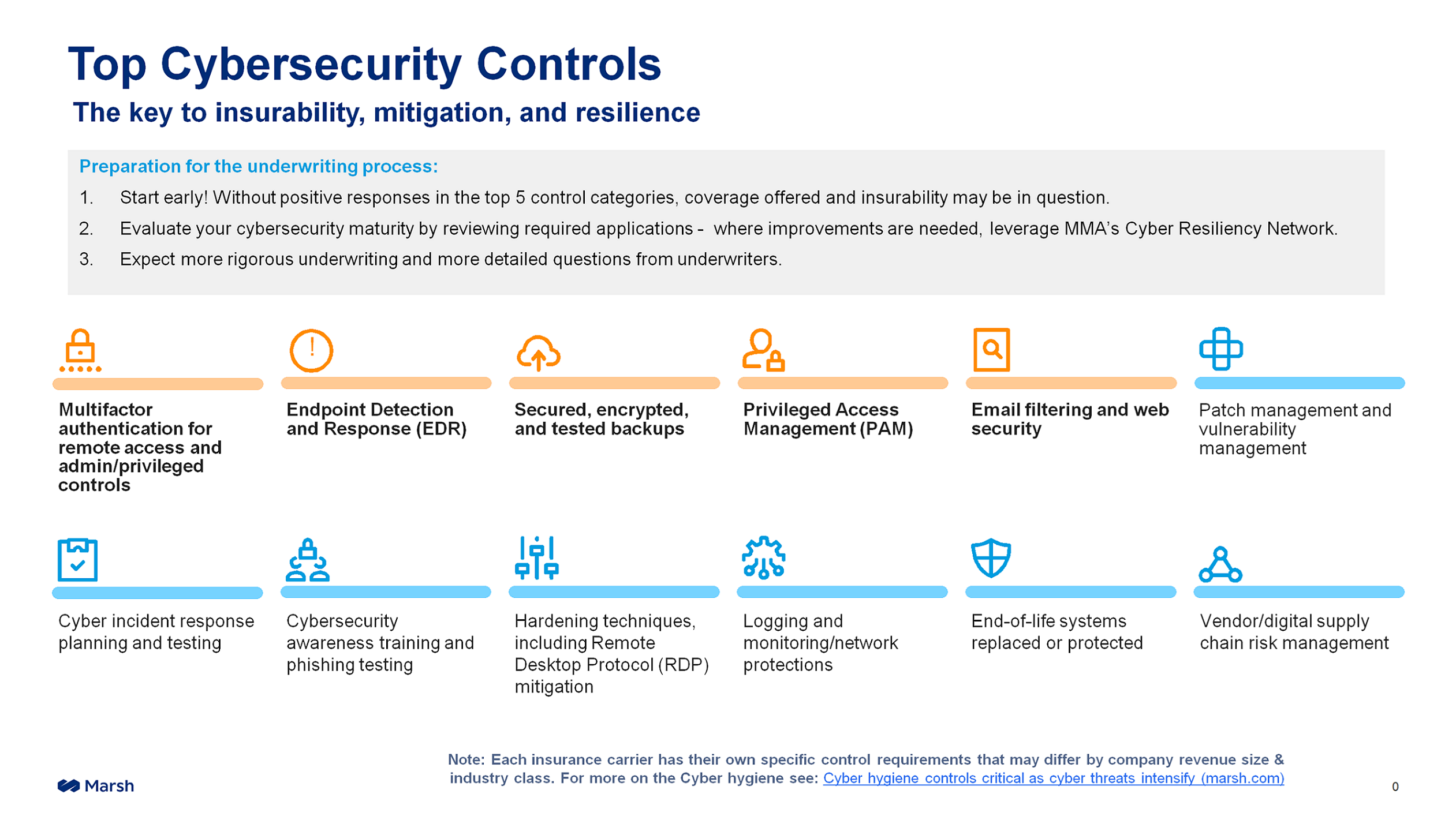
To qualify for cyber insurance today, Schein emphasized the need to put in place 12 security controls that address very basic cyber security. These controls are “absolutely critical for businesses that are looking to apply for insurance and or increase the current limits that they currently have. And then from a coverage standpoint, we’ve spoken about carriers are now starting to scale back coverage. The market is starting to harden and you’re starting to see prices increasing.”
The first five controls, highlighted in orange, are essential before MMA will sit down with a prospective client, he said. The other seven controls also are crucial, but MMA will consider submitting an insurance policy to underwriters even if not every blue control is in place.
That said, cyber insurance carriers simply will not offer a policy if the prospect is not willing to put forth the effort to reduce their risk. “[Cyber insurance carriers] can’t charge enough to make up for poor [security] controls,” he said.
Business interruption
While brokers such as MMA have their own requirements to consider before submitting an insurance application to underwriters, it is the carriers for whom the underwriters work and who decide if an application is approved or not.
Mosaic’s Tuplin said most insurers find that organizations seeking insurance are most concerned about business interruption first due to ransomware and then data breaches or misuse of data. In order to identify the appropriate policy for a prospective customer, Tuplin said Mosaic uses three core triggers to determine the coverage the cyber insurance policy offers.
The first trigger is security failure, which is the inability of your IT security to stop an event. An example of a security failure is a virus that stops your system from working correctly. Taking security failure to the next level, you come to the second trigger: system failure. An example of system failure is turning on your computer, but nothing happens at all, he said. The third trigger, which formerly was part of system failure but now is a discrete trigger, is ransomware.
“We’ve split that out as an industry so that insurers can choose whether to include or exclude that as a trigger within their policies,” Tuplin said. “It will make your policy more expensive to include it, but it’s generally the area you want to cover most.”
The base area of coverage in a cyber policy is if it affects the organization’s own IT systems, he noted. That would include software that runs on-premises on workstations and servers, as well as networking equipment. The second level of coverage addresses key partners’ systems — an outsourced IT system. This could include cloud services or perhaps a payment system for a retail customer.
“What you have to think about is if an event such as a virus affects that payment processor, rather than affecting your own IT systems,” Tuplin said. “Do you want that to be covered within your policy? It is an extension of coverage, but it is a very important one and it is one that most people do opt to purchase.”
The third area is the most extreme version of business interruption — an interruption to any service provider’s operations. He used the example of an automobile manufacturer who was unable to obtain specific parts because of a cyberattack on that partner’s manufacturing operations. A car manufacturer cannot ship a car without breaks, so such a business continuity interruption due to an attack on a third party directly that impacts the ability for the insured to make its products is a covered event.
Data breaches
A data breach simply refers to information that should have been private is now disclosed and perhaps public. Tuplin used credit card data, legal documents, healthcare records and passport information as common types of private data that is obtained by someone who is not supposed to have the data. Private data that is made public or is stolen triggers the data breach element of a cyber insurance policy, he noted.
Data misuse is another component of a breach. If the owner of private data tells a company not to disclose or sell their private data but the company does so anyway, that disclose triggers the data breach portion of a cyber policy as well.
“We don’t care how the data was breached, cyber policies will cover it,” he said. Beyond how the data was compromised, the cyber insurance policy is not concerned where the data was breached. The policy will pay if you store data on your server or in the cloud. Each misuse still triggers the policy, he noted.
When triggered, the policy covers notification costs, which can be quite expensive. Both the European Union’s General Data Protection Regulation (GDPR) and the U.S. Health Insurance Portability and Accountability Act of 1996 (HIPAA) require informing anyone whose personally identifiable information (PII) has been compromised.
Cyber insurance also generally pays for investigating and identifying how an attacker got into the network and if they are still there. It also pays for identifying exactly what was compromised and reporting to regulators. Insurance companies generally have teams of attorneys who step in to handle all the required legal work from disclosure to reporting to handling covered lawsuits.
In some jurisdictions, where the practice is legal, the insurance company might also pay any extortion fees. That can be problematic in such countries as the United States and Italy where government regulations do not permit payments to sanctioned organizations, which could include organized crime, foreign criminal organizations and some foreign state-sponsored groups and terrorists.
Tuplin noted that it can be difficult to determine at first blush the kinds of data a company needs to protect. He cited the example of a small company that had just a handful of employees with roughly £4.5 million in sales, but the company had data on more than half of the population of Great Britain. When a company takes out a policy to protect its most important data, it is essential to know exactly what that entails. In the case of this small British firm, he said, it would be the database with the pertinent information on the citizenry that was the company’s core data.
Being clear on exactly what your organization needs to protect will go a long way to ensure that your cyber insurance policy is written so that it covers exactly what you need protected.
Paying claims
Cyber insurance, like other business functions, is shrouded in its own myths. One popular story, according to Mosaic’s Graham, is that organizations do not need cyber coverage because their other insurance will cover cyber events. That generally is not accurate, she said.
While some policies might have a small amount of cyber coverage, it normally is insufficient to meet the very high costs related to cyberattacks. Popular business coverage, such as errors and omissions, key person insurance, general liability, commercial property and other kinds of business policies simply are not designed to meet the specific needs of a cyber insurance policy.
“Other than a standalone cyber insurance policy, there is no other policy that will cover you for data breaches data, misuse, ransomware, malware, everything that we’ve talked about,” she said.
It is important to notify the insurance company if there is a breach or ransomware attack, even if the company plans to cover the loss themselves. During the investigation and mitigation process, the investigators might find additional damage the organization was not aware of from the attack. Additionally, all discussions with attorneys are protected by attorney/client privilege so no secrets can be disclosed in case of a lawsuit.
Another myth Graham dispelled is that insurance companies do not pay claims for cyberattacks. That, she said, is simply incorrect, as is the notion that filing a claim is difficult. “If you avail yourself of the tools that are available, it is straightforward,” she said.
“Ransomware is far and away the largest cause of cyber claims at the moment,” Graham added. “It is prevalent, but the cyber insurance does cover it. Ransomware itself can also be accompanied by data breaches.”
If an attacker installs ransomware and at the same time steals data and essentially hold that data to ransom, you have two actions — introduction of ransomware and a data breach with extortion. However, she noted, they are not necessarily two totally distinct events.
A lot of organizations think, “I don’t need cyber insurance because my environment is secure,” Graham continued. “But it isn’t just your environment that you need to be concerned about, she noted. While your environment might be safe, you still need to be concerned with your third-party suppliers and services and other organizations that that that you rely on to carry out your business. So, if any of those are hit by any kind of incident, then it can have a knock on effect.”
Hoping to put at rest the concern that cyber insurance was an unnecessary expense, she noted: “If you suffer a cyber event, you will be covered. And your insurance company, as long as they are reputable, will pay.”
Sophos solutions
Looking at the cybersecurity controls that MMA uses to identify potential customers who have proactive cybersecurity efforts in place, Sophos can play a significant role in providing tools to address those controls, said Nicholas Cramer, senior director of global cyber risk partnerships at Sophos. In fact, Sophos can help with 11 of the 12 controls, including all five of MMA’s essential controls needed to obtain a seat at the proverbial table. You can find which Sophos products map directly to the essential cyber security controls by downloading the Sophos Cyber Insurance Controls Solution Brief.
To learn more about Sophos products, visit the website or reach out to the Sophos team.
Watch the event on-demand
The full event is available on-demand, allowing you to watch – and re-watch – the sessions at your convenience.