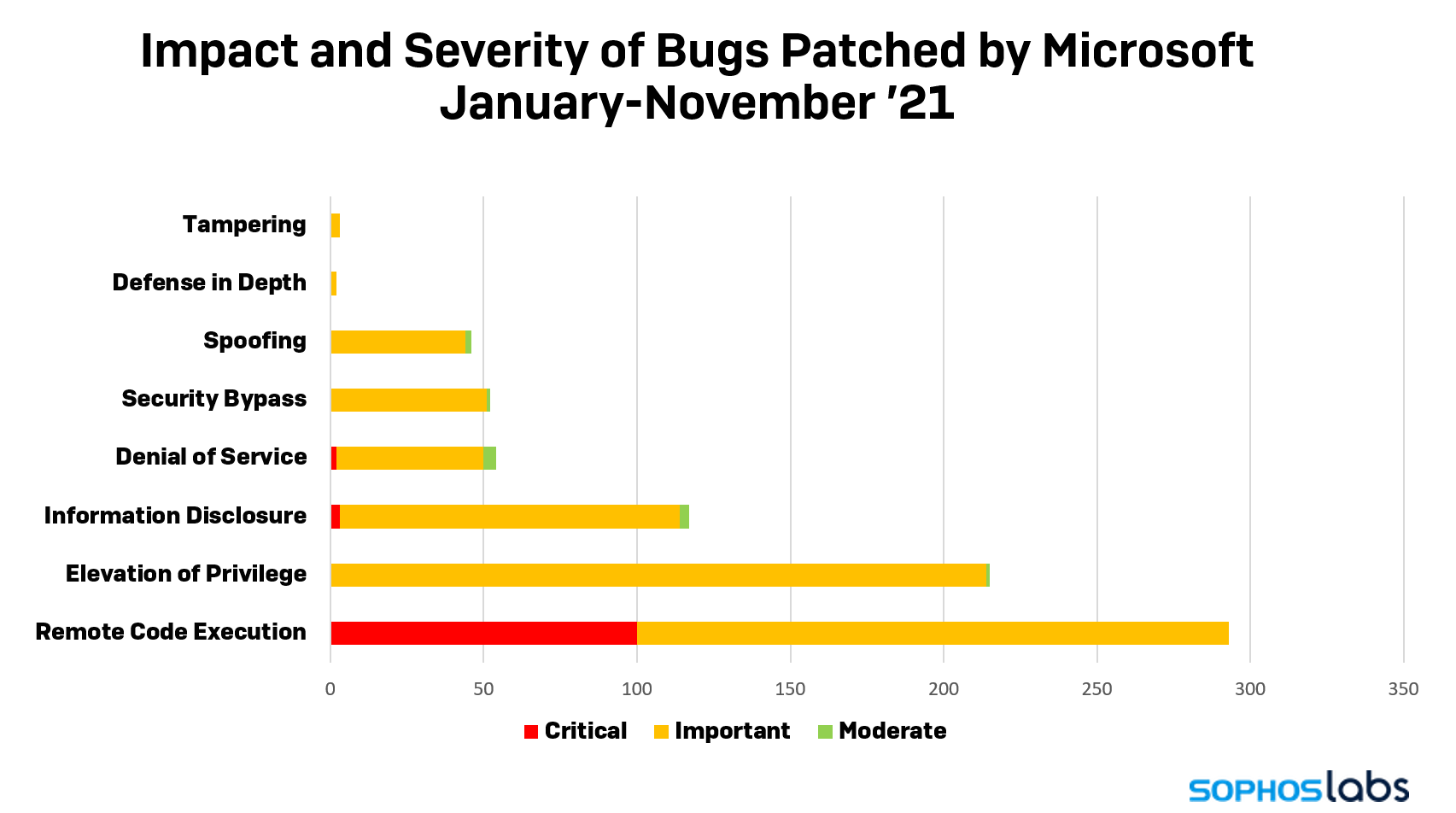
For the second-to-last Patch Tuesday of 2021, Microsoft’s big update release fixes fewer than 60 bugs in Windows, services run by Microsoft, or other applications, one of the smallest releases of the year. But the small number of patches belies the seriousness of the bugs they’re designed to fix. There’s enough severity represented here that you shouldn’t defer or delay installing them.
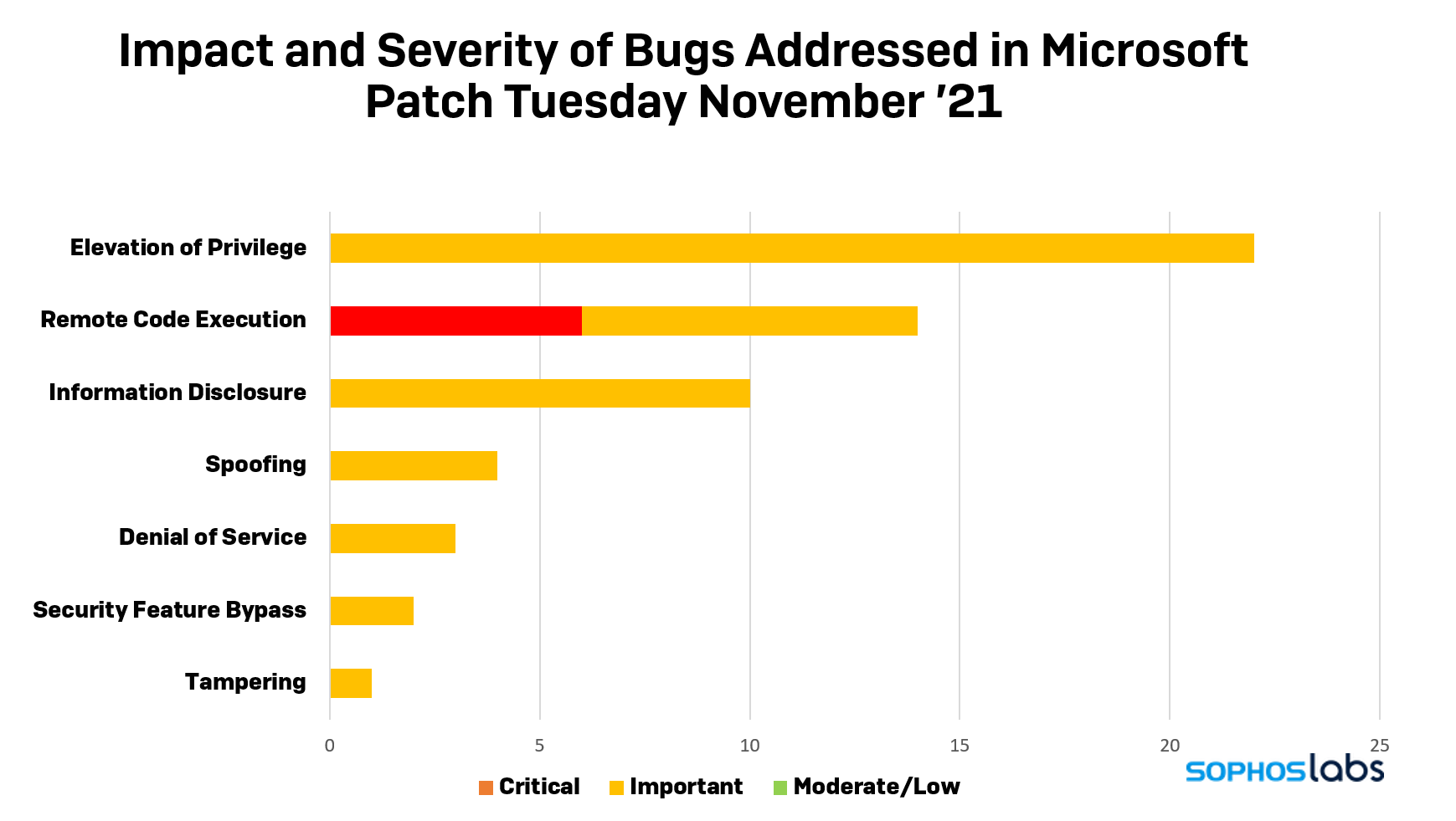
The company fixed a raft of privilege escalation bugs (“Elevation of Privilege” in Microsoft parlance) in 18 different products or Windows subcomponents, including the Windows kernel, the NTFS filesystem, the Azure RTOS, and Active Directory Domain Services.
There is also a critical patch to the Windows Servicing Stack, which is how Windows delivers and installs updates, especially to machines that are running versions of Windows no longer receiving regular support. That’s especially important this month, because several of the updates have been released for systems as out-of-date as Windows 7, which as of today is 665 days past its official end of life on January 14, 2020.
Here are some of what we think will be the most significant updates to watch for.
Remote Desktop Client Remote Code Execution Vulnerability
CVE-2021-38666
Nearly every Windows machine since Windows XP has had a version of the Windows RDP client preinstalled on it, and this month’s fixes will repair a bug that could permit remote code execution on the machine using the RDP client to connect to a server. In order to trip the bug, someone would have to use an unpatched version of the RDP client to connect to a server hosting malicious code; That code could then execute on the machine attempting to connect to the server. It isn’t hard to imagine several different scenarios where attackers would take advantage of this, so this alone is a very good reason to patch.
Microsoft Virtual Machine Bus (VMBus) Remote Code Execution Vulnerability
CVE-2021-26443
The VMBus component acts as a “para-virtualization” bridge between virtual machine hardware and physical, real-world devices. In a hypothetical exploit scenario, an attacker could send a deliberately malicious, crafted set of information over the VMBus channel, and have that execute code on the host machine. Such VM escapes are rare, but incredibly serious, so this is another fix that you probably shouldn’t defer if you can help it.
Sophos protection
Here is a list of protection released by SophosLabs in response to this advisory to complement any existing protection and generic exploit mitigation capabilities in our products. Additional protection signatures may be released after this article is published.
| CVE | SAV |
|---|---|
| CVE-2021-42298 | Exp/2142298-A |

