In May, we published a report about scammers using dating sites and apps to social-engineer victims into installing fake cryptocurrency apps on iPhone and Android . At the time, the evidence suggested the crooks behind these apps were exclusively targeting victims in Asia. But since then, we’ve seen increasing evidence of these fake apps being part of a wide-ranging global scam. We have learned of victims in Europe, most of them iPhone users, who have lost thousands of dollars to crooks through these scams. We have also identified more applications tied to the fraud campaign—which, due to its combination of romance scams and cryptocurrency trading fraud, we’ve dubbed CryptoRom.
In our initial research, we discovered that the crooks behind these applications were targeting iOS users using Apple’s ad hoc distribution method, through distribution operations known as “Super Signature services.” As we expanded our search based on user-provided data and additional threat hunting, we also witnessed malicious apps tied to these scams on iOS leveraging configuration profiles that abuse Apple’s Enterprise Signature distribution scheme to target victims.
Global Fraud campaign
A report issued by Interpol early this year warned about this growing type of fraud, noting that these scams target vulnerable people—particularly those who are looking for potential romantic partners through dating applications and social media platforms. In addition to the victims that contacted us directly, we also found some through news reports, and more through sites that maintain databases of scam reports. In addition to the Asian countries we had previously identified, we found victims of similar scams from the UK, France, Hungary and the US.
As victims contacted us to report some of these scams, we gathered more details about the campaign.
From news reports, we learned one victim lost £63000 (~ $87000). There are additional news reports in UK of these scams, with one victim losing £35000 (~$45000) to a scammer who contacted them through Facebook, and another who lost £20000($25000) after being scammed by someone who contacted through Grindr. In the latter case, the victim made an initial deposit, transferred money to a Binance application from their bank and then to crooks; they were then asked to deposit more funds in order to withdraw their money. None of these victims have gotten their money back.
We checked scam database sites for URLs associated with these scams, and for comments from those who are affected by CryptoRom. Studying the stories of victims expanded understanding of this scam operation:
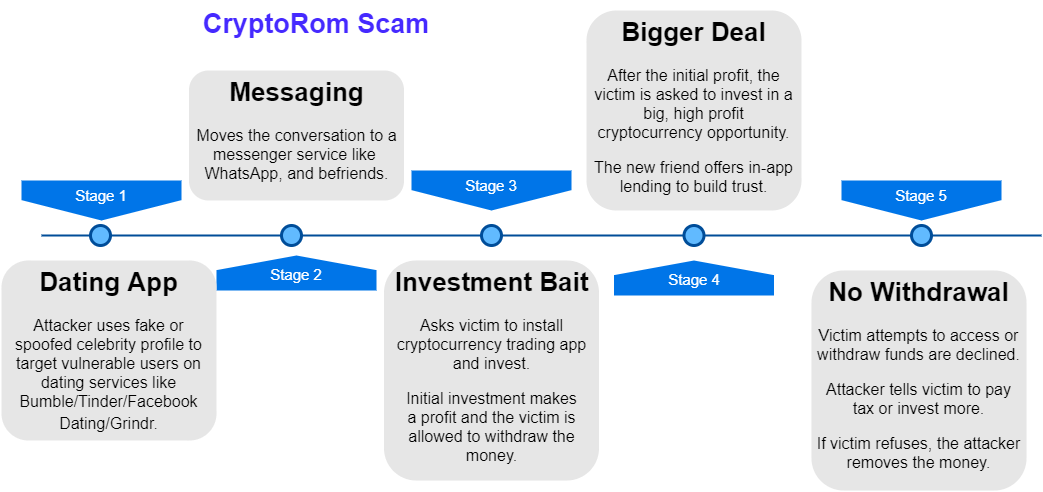
Victims are contacted through dating sites or apps like Bumble, Tinder, Facebook dating and Grindr. They move the conversation to messaging apps. Once the victim becomes familiar, they ask them to install fake trading application with legitimate looking domains and customer support. They move the conversation to investment and ask them to invest a small amount, and even let them withdraw that money with profit as bait. After this, they will be told to buy various financial products or asked to invest in special “profitable” trading events. The new friend even lends some money into the fake app, to make the victim believe they’re real and caring. When the victim wants their money back or gets suspicious, they get locked out of the account.
Millions lost and over $1.3 million in one case
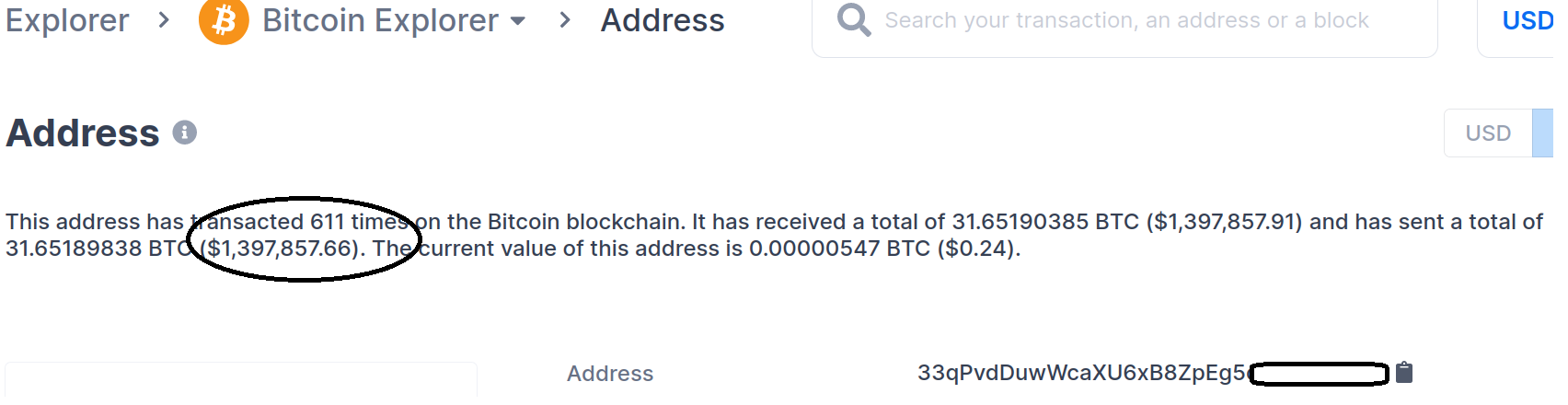 One of the victims shared the bitcoin address to which they transferred their money, and when we checked at the time of writing it has been sent over $1.39 million dollars to date. This shows the scale of this scam and how much money fraudsters are making from vulnerable users. This is just one bitcoin address, the tip of the iceberg. There could be several, with millions being lost. So, this scam is more serious as it hurts real people. Though it’s hard to believe, we could see from comments and news reports that these are vulnerable common folks who are losing their hard-earned money and struggling to get it back. In most cases we have come across, crooks have asked victims to transfer money by buying cryptocurrency through the Binance app and then to a fake trading application. This is probably done to avoid the tracing of funds to its destination and recuperation .
One of the victims shared the bitcoin address to which they transferred their money, and when we checked at the time of writing it has been sent over $1.39 million dollars to date. This shows the scale of this scam and how much money fraudsters are making from vulnerable users. This is just one bitcoin address, the tip of the iceberg. There could be several, with millions being lost. So, this scam is more serious as it hurts real people. Though it’s hard to believe, we could see from comments and news reports that these are vulnerable common folks who are losing their hard-earned money and struggling to get it back. In most cases we have come across, crooks have asked victims to transfer money by buying cryptocurrency through the Binance app and then to a fake trading application. This is probably done to avoid the tracing of funds to its destination and recuperation .
iPhone users targeted
Based on the victims we have come across, most have been iPhone users and the webpages created to distribute these apps have also been mainly mimicking the App Store, suggesting these scammers are targeting iPhone users assuming they are likely to be wealthy. The following image is from one of the recent fraud web pages and the destination for app download resembles the Apple App Store page.
Apple Enterprise Program Abuse
Crooks need to find a way to circumvent the Apple App Store review process but still reach their victims successfully. In our first post on this scam campaign, we showed how the ad-hoc Super Signature distribution scheme was used to target iOS device users. We also found mobile provisioning profiles used to distribute this malware.
Since then, in addition to the Super Signature scheme, we’ve seen scammers use the Apple Developer Enterprise program (Apple Enterprise/Corporate Signature) to distribute their fake applications. We have also observed crooks abusing the Apple Enterprise Signature to manage victims’ devices remotely. Apple’s Enterprise Signature program can be used to distribute apps without Apple App Store reviews, using an Enterprise Signature profile and a certificate. Apps signed with Enterprise certificates should be distributed within the organization for employees or application testers, and should not be used for distributing apps to consumers.
Super Signature services, which use personal developer accounts rather than Enterprise accounts, have a limit on the number of devices that apps can be installed on and requires the UDID of the device for installation. On the other hand, the Enterprise Signature service can be used to distribute apps directly to a higher number of devices that are managed by one account. In both cases, apps do not have to be submitted to the Apple App Store for review.
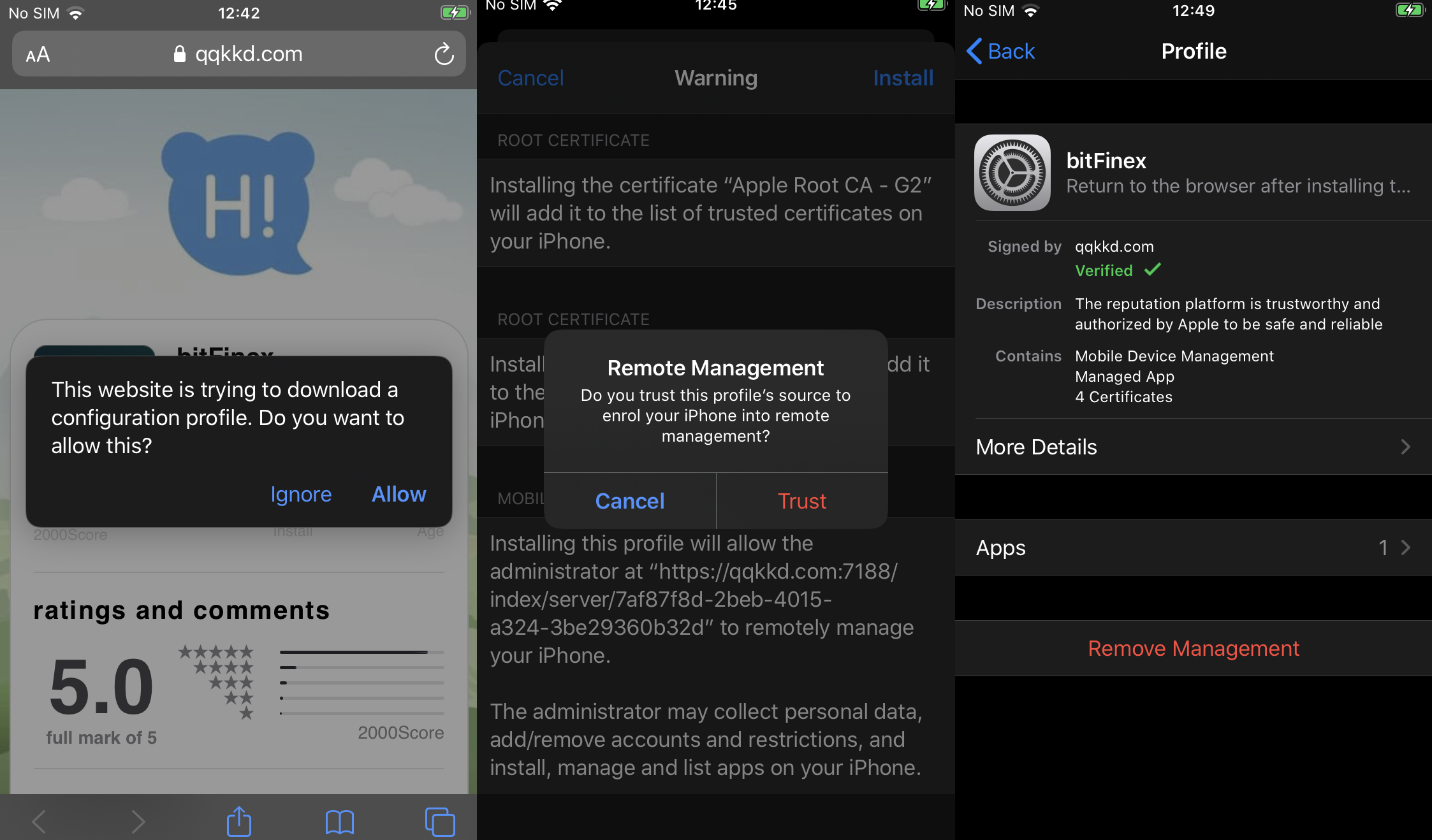
When an iOS device user visits one of the sites used by these scams, a new profile gets downloaded to their device. Instead of a normal ad hoc profile, it is an MDM provisioning profile signed with an Enterprise certificate that is downloaded. The user is asked to trust the profile and, after they do that, the crooks can manage their device depending on the profile contents. As warned in the image below the crooks can potentially collect personal data, add/remove accounts and install/manage apps.
In this instance, the crooks wanted victims to visit the website with their device’s browser again. When the site is visited after trusting the profile, the server prompts the user to install an app from a page that looks like Apple’s App Store, complete with fake reviews. The installed app is a fake version of the Bitfinex cryptocurrency trading application.
Apple’s Enterprise provisioning system is an Achilles heel on the Apple platform, and like the Super Signature distribution method it has been abused extensively by malware operators in the past. Apple began to crack down on the use of Enterprise certificates; even Google and Facebook Enterprise certificates were revoked (and later reinstated) for distributing apps to consumers using this method. This slowed down the abuse of Enterprise certificates by malicious developers, but we believe they are moving towards more targeted abuse of these signatures to bypass Apple App Store checks.
There are commercial services which do Enterprise certificate distribution, and crooks abuse these third party services. Below is a screenshot of a Chinese paid service advertising about Enterprise Signatures and highlighting the evasion of an App Store review.
 There are several commercial services selling Apple signatures for apps that can be purchased for couple of hundred dollars. There are different versions of signatures: stable versions which are expensive and less stable ones that are cheaper. The cheaper version is probably preferred by the crooks as it is easy to rotate to a new one when the old signature gets noticed and blocked by Apple.
There are several commercial services selling Apple signatures for apps that can be purchased for couple of hundred dollars. There are different versions of signatures: stable versions which are expensive and less stable ones that are cheaper. The cheaper version is probably preferred by the crooks as it is easy to rotate to a new one when the old signature gets noticed and blocked by Apple.
Conclusion
While Apple’s iOS platform is generally considered safe, even apps in the walled garden of the App Store can pose a threat to Apple’s customers—it remains riddled with fraudulent apps like Fleeceware. However, CryptoRom bypasses all of the safety screening of the App Store and instead targets vulnerable iPhone victims directly.
This scam campaign remains active, and new victims are falling for it every day, with little or any prospect of getting back their lost funds. In order to mitigate the risk of these scams targeting less sophisticated users of iOS devices, Apple should warn users installing apps through ad hoc distribution or through enterprise provisioning systems that those applications have not been reviewed by Apple. And while institutions dealing with cryptocurrency have started implementing “know your customer” rules, the lack of wider regulation of cryptocurrency will continue to draw criminal enterprises to these sorts of schemes, and make it extremely difficult for victims of fraud to get their money back. These scams can have have a devastating effect on the lives of their victims.
We have shared details of of the malicious apps and infrastructure with Apple, but we have not yet received a response from them. IOCs for the malicious IOS app sample we analyzed for this report are below; a full list of IOC’s from the first part of campaign available on SophosLab’s GitHub.
IOC’s
TeamIdentifier – 63H9VMJFHA
TeamName – TECHNOLOGY LINKS (PRIVATE) LIMITED
Bundle ID – com.aabbcc.bitfinex
IPA – 3c346a89f8e2151660137c2dcddc07df1ae7060d725d626e47a11bb7b1387940
URL – qqkkd[.]com/





Robert Berg
I am a cryptoRom victim. Nearly 500k USD
Asian woman I met on Facebook, after reading your articles it matches exactly what has happened to me. BTG crypto trade site/ global currency exchange.
Account assets frozen unless I pay 20% tax, I believe it’s safe to assume if I were to “ pay the tax” the funds won’t be released, or only partially. Please reach back to me if you can offer any guidance or to help others. This stupid error in judgment has caused financial ruin for me.
Richard
Like you I have lost more than $600k to Cryptorom scammers, wiping out most of my retirement savings. Like you I kick myself for being so gullible. The most terrible thing about these con artists is they easily elude the law by vanishing into cyberspace.
Oscar Robles
Hello Robert, yesterday an Asian woman contacted me indicating that she works on cryptocurrency. Do you have any information on someone who can help catch these criminals. I started to investigate before they scammed me. But I’d like to help catch them.