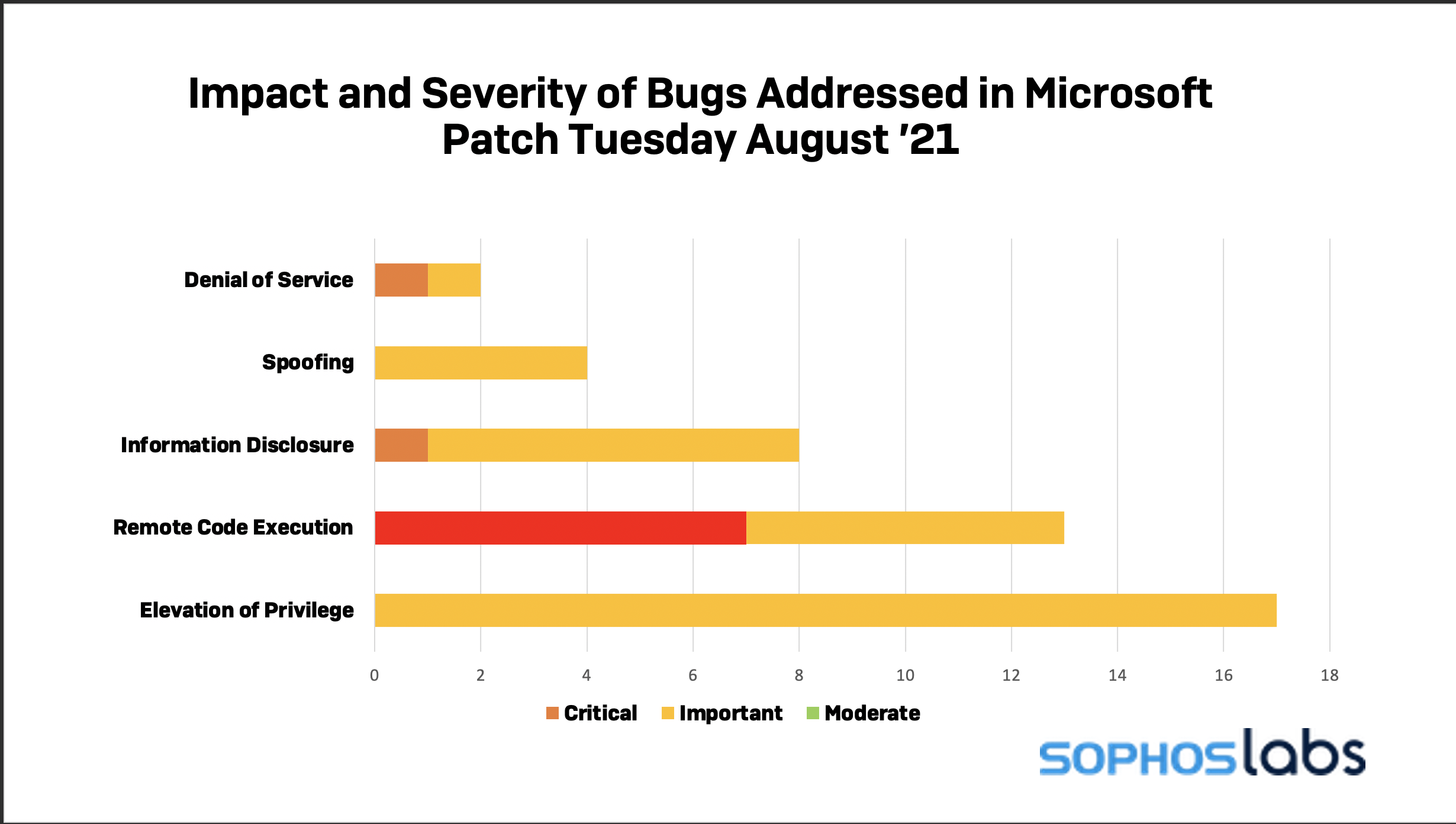
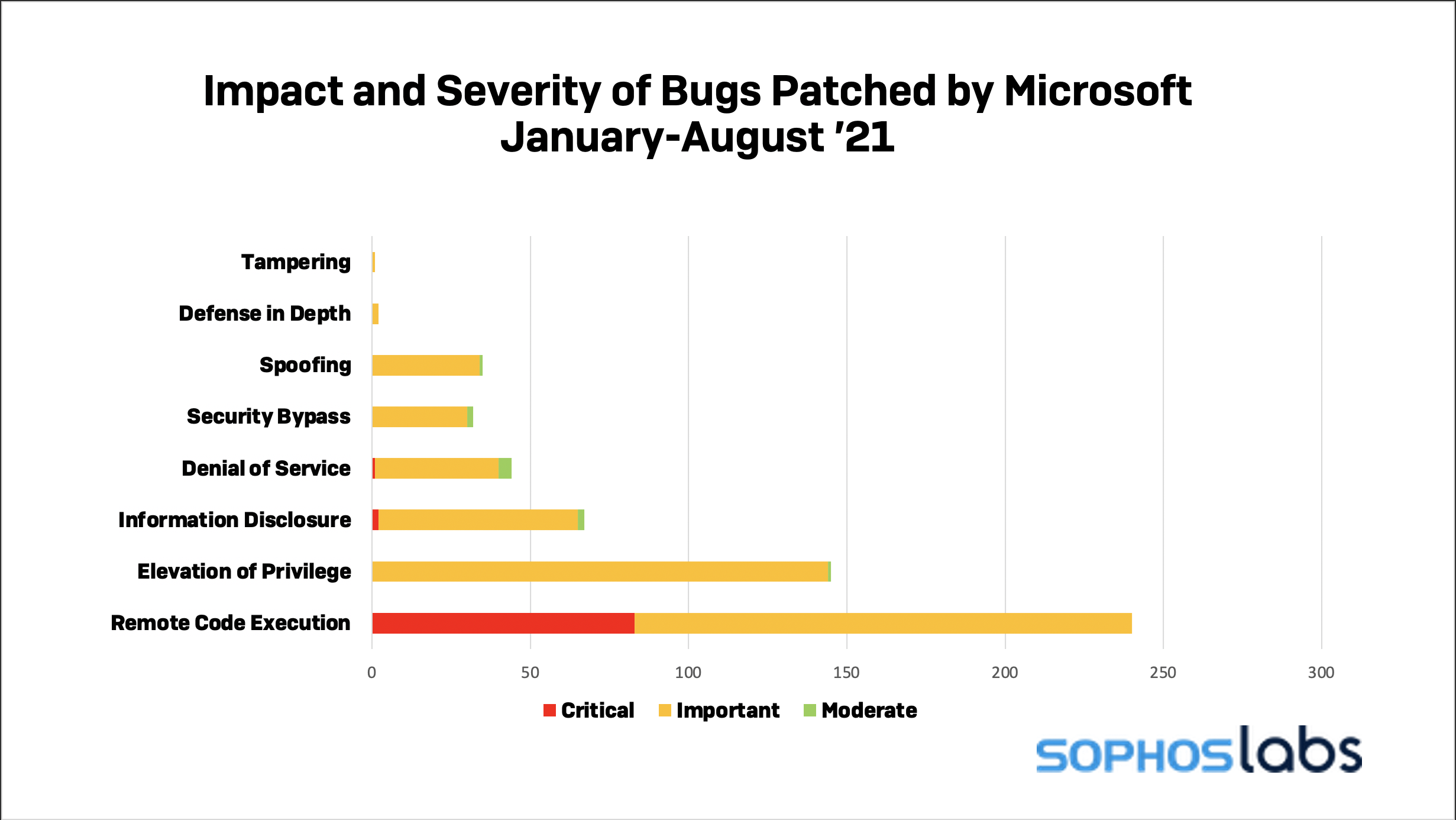
Today, Microsoft released fixes for 44 vulnerabilities, nine of them rated as critical. While that’s fewer than half the number pushed out by Microsoft in July overall, the smaller volume doesn’t diminish the urgency of the fixes published today: Seven of them have a high potential for exploitation, including one that has already been publicly disclosed, and one vulnerability is already being exploited by malicious actors.
In total, thirteen of the 44 bugs addressed in August’s security update can be exploited for remote code execution. Seven of these are rated as critical.
The other two critical bugs, both in Azure Sphere, are a denial of service vulnerability and information disclosure vulnerability, respectively.
As always, Windows will automatically download and install the patches when a computer is idle. If there’s a delay, and you want to update immediately, the company offers them as downloadable update packages from the Microsoft Catalog website. Sophos recommends against deferring these necessary updates.
The nine critical vulnerabilities patched in August’s security update are:
| CVE-2021-26424 | Windows TCP/IP Remote Code Execution Vulnerability |
| CVE-2021-26432 | Windows Services for NFS ONCRPC XDR Driver Remote Code Execution Vulnerability |
| CVE-2021-34480 | Scripting Engine Memory Corruption Vulnerability |
| CVE-2021-34535 | Remote Desktop Client Remote Code Execution Vulnerability |
| CVE-2021-36936 | Windows Print Spooler Remote Code Execution Vulnerability |
| CVE-2021-34530 | Windows Graphics Component Remote Code Execution Vulnerability |
| CVE-2021-34534 | Windows MSHTML Platform Remote Code Execution Vulnerability |
| CVE-2021-26428 | Azure Sphere Information Disclosure Vulnerability |
| CVE-2021-26430 | Azure Sphere Denial of Service Vulnerability |
Most likely to be pwned
Among the seven bugs rated as most likely to be exploited by Microsoft, five are potentially exploitable for remote code execution. CVE-2021-34480, described as a Scripting Engine memory corruption vulnerability, is a pointer dereference flaw in Windows’ JScript engine. A crafted script could potentially write code to memory outside of the context of the script engine, resulting in remote code execution. Another memory corruption vulnerability in the collection of bugs more likely to be exploited is CVE-2021-26432, a flaw in a remote procedure call external data representation (RPCXDR) kernel driver for Windows Services for NFS.
CVE-2021-36936, yet another remote code execution vulnerability in Windows Print Spooler, has already been publicly disclosed. This is a separate flaw from the elevation of privilege vulnerability (CVE-2021-34481) revealed last month, and from the “Print Nightmare” remote code execution bug (CVE-2021-34527) that Microsoft partially patched in an emergency fix. CVE-2021-36936 has not yet been exploited by attackers (as far as anyone knows).
The roll-up security update also includes changes to address the group of vulnerabilities that resulted in “PrintNightmare.” Microsoft has changed the default Point and Print driver installation and update behavior in Windows to require administrator privileges, in order to mitigate CVE-2021-34527 and related documented vulnerabilities in installation of this update with default settings will mitigate the publicly documented vulnerabilities in the Windows Print Spooler; the changes are documented in CVE-2021-34481.
The remaining critical bugs at a higher risk of exploitation:
- CVE-2021-26424, a Windows TCP/IP remote code execution vulnerability, and
- CVE-2021-34535, a remote code execution vulnerability in Windows’ Remote Desktop Client
Other flaws patched in this month’s release that Microsoft’s assessment determines are more likely to be exploited were rated as “important” rather than “critical.” But in at least one instance, the bug designated as CVE-2021-36948–an elevation of privilege vulnerability in Windows Update’s Medic Service–is already, reportedly, being exploited.
The final vulnerability assessed by Microsoft to be more likely to be exploited in this round of fixes is CVE-2021-36942, a spoofing vulnerability in Windows’ Local Security Authority, which authenticates access to the local Windows system.
Sophos protection
Here is a list of protection released by SophosLabs in response to this advisory to complement any existing protection and generic exploit mitigation capabilities in our products.
| CVE | IPS | ||
|---|---|---|---|
| XG | EPIPS | SG | |
| CVE-2021-34480 | 2305922 | 57998,57999 | |
| CVE-2021-26432 | 2305923,2305924 | 2305923,2305924 | 58003 |
| CVE-2021-34535 | 57997 | ||

barnhata
The way I read the vulnerability in CVE-2021-34481, any user privileged or non-privileged could be affected. Yet the fix seems to be not allow non-privileged accounts the ability to install and update printer drivers.
Which leads me to believe we’re going to see an update to this fix at some point or it’s time to move away from point and print.
Am I reading this wrong or misunderstanding the vulnerability?