It’s Patch Tuesday again, and this time, it’s again a relatively quiet one. The June security update drop has a mere 49 new vulnerability fixes, plus five synchronized fixes delivered by Adobe. Only five of Microsoft’s bug fixes are rated as critical. But that doesn’t lessen the importance of applying patches as soon as possible; all five critical patches are for bugs that are potentially exploitable for remote code execution (RCE). And one of them—a vulnerability in the Windows MSHTML “platform”, the proprietary browser engine originally developed for Internet Explorer that remains as a component of some HTML-rendering applications—is already being exploited.
Microsoft also pushed a fix for an elevation of privilege vulnerability in the Chromium-based Microsoft Edge browser (CVE-2021-33741) on June 4. That vulnerability, also reported in Chrome, was already being actively exploited in the wild.
Criticals
The Windows MSHTML bug (CVE-2021-33742) is of greatest concern, as it is already being actively exploited by malicious actors. A malicious web page visited by an application using the Internet Explorer HTML engine could be used to execute commands on the affected system—this could happen either within browser context, within an e-mail, or any other application using the MSHTML engine to render HTML content. The update includes cumulative updates to Internet Explorer on Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows Server 2012, Windows 8.1, and Windows Server 2012 R2, and in EdgeHTML (used to support Internet Explorer mode in the Edge browser) on more recent Windows versions.
Two other critical bugs are of particular interest. The first is CVE-2021-31959, a memory corruption vulnerability in the Chakra JScript scripting engine. Like the bug in MSHTML, this vulnerability is addressed in the Internet Explorer cumulative update. But the JScript engine is also also supported for legacy support, and so it’s being patched on newer operating systems as well. The second is CVE-2021-31985, an RCE vulnerability in Microsoft’s Defender antimalware software; a similar vulnerability was patched in January.
Since both of these components process files delivered from outside the network, and are already on the target list of many malicious actors, they are more likely to be exploited. Installing updates for these components is the only mitigation for the Scripting Engine vulnerability. Customers who use Sophos or other third-party malware software should not be overly concerned about the Defender bug, as systems with Defender disabled are not vulnerable to this type of attack. And no action is required to patch this if Defender updates are active—the current signature update corrects the vulnerability.
The other RCE vulnerabilities are less likely to be exploited in the near term, but still call for immediate patching. CVE-2021-31963 is a vulnerability in SharePoint Server. The last critical bug is CVE-2021-31967, a flaw in Microsoft’s VP9 Video Extensions (a video compression codec used by YouTube and other video streaming platforms).
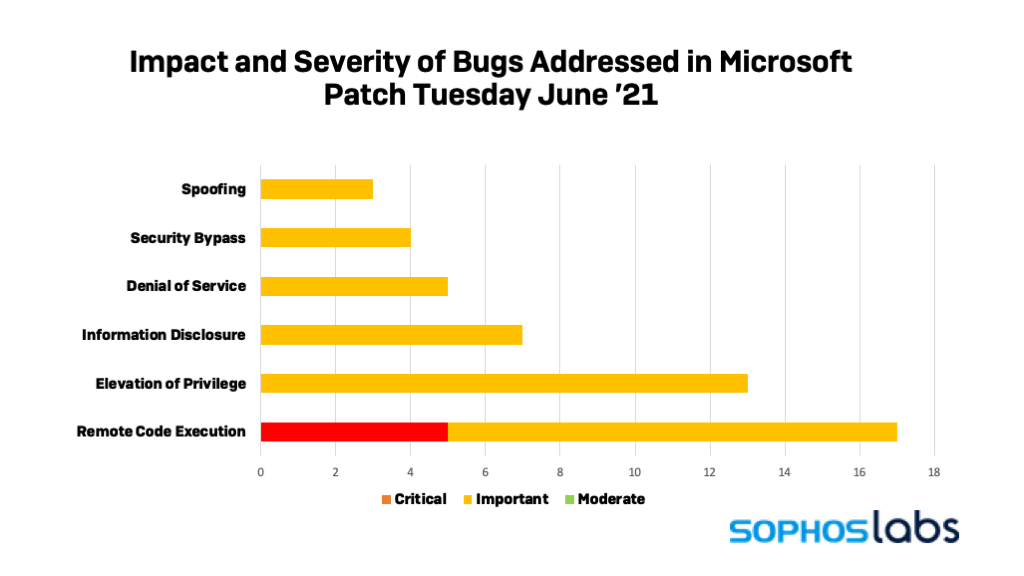
While not rated as critical, there are five fixes in this month’s updates that address additional vulnerabilities already being exploited by malicious actors. Four of them are Elevation of Privilege bugs. The first two ( CVE-2021-31199 and CVE-2021-31201) are vulnerabilities in Microsoft’s Enhanced Cryptographic Provider, one of Windows’ cryptographic support components. The remaining actively exploited elevation of privilege bugs are in Windows NTFS (CVE-2021-31956) and Microsoft’s DWM Core Library (CVE-2021-33739) (for which a proof-of-concept exploit has been posted on Github). And the remaining known-exploited vulnerability is an information disclosure bug in Windows Kernel (CVE-2021-31955).
Two of these vulnerabilities—CVE-2021-31955 and CVE-2021-31956—have been used as part of a series of targeted attacks. Exploits of those vulnerabilities, in combination with a remote code execution bug in Chrome, were chained together in attacks reported to Microsoft by Kaspersky Lab.
There are also seven more remote code execution vulnerabilities addressed in June’s fixes rated as important by Microsoft. Three of these are enterprise-focused. In addition to the critical bug mentioned earlier, there’s also another SharePoint Server RCE issue (CVE-2021-31966). There’s also an RCE fixed in a management extension for Microsoft’s Intune mobile device management platform (CVE-2021-31980), and another in the Microsoft Outlook email and calendar client (CVE-2021-31949).
The remaining remote code execution issues are in two Microsoft applications connected to three-dimensional rendering . Two of them (CVE-2021-31942 and CVE-2021-31943) are in Microsoft’s 3D Viewer software, a tool used to view three dimensional model files on the PC or HoloLens. There are three such bugs in another Microsoft app, Paint 3D (CVE-2021-31945, CVE-2021-31945, and CVE-2021-31983).
Sophos protection
Here is a list of protection released by SophosLabs in response to this advisory to complement any existing protection and generic exploit mitigation capabilities in our products.
| CVE | SAV | IPS (XG) |
|---|---|---|
| CVE-2021-31199 | Exp/2131199-A | |
| CVE-2021-31201 | Exp/2131201-A | |
| CVE-2021-31955 | Exp/2131955-A | |
| CVE-2021-31956 | Exp/2131956-A | |
| CVE-2021-33739 | Exp/2133739-A | |
| CVE-2021-31959 | 9000225 |
