Editor’s note: This is the first part of our continuing research on a fraud campaign we’ve labeled “CryptoRom”. Follow-up reports on continued research can be found here and here. All our research on this topic can be found on the topic page here.
Recently, we were tipped off to a fraudulent mobile trading application that masqueraded as one tied to a well-known Asia-based trading company. As we investigated, we uncovered several other counterfeit versions of popular cryptocurrency trading, stock trading and banking apps on iOS and Android, all designed to steal from those fooled into using them.
These fraudulent applications are aimed at exploiting the increased interest in trading apps, driven by the recent significant rise in the value of cryptocurrencies and interest in low-cost or free stock trading driven by stories like that of the recent social-media driven speculation in GameStop stock.
In some cases, the schemes to distribute these applications leveraged social engineering through dating sites to lure in victims, and websites designed to look like those belonging to legitimate companies. These websites forwarded victims to third-party sites that delivered iOS mobile applications via configuration management schemes, iOS mobile device management payloads carrying “Web Clips”, or Android apps depending on the device used.
During investigation of one of the apps, we encountered a server which was hosting hundreds of fake trading, banking, foreign exchange, and cryptocurrency apps. Among them were counterfeit apps impersonating major financial firms and popular cryptocurrency trading platforms, including Barclays, Gemini, Bitwala, Kraken, Binance, BitcoinHK, Bittrex, BitFlyer, and TDBank. Each of these fake apps had a dedicated website tailored to the impersonated brand to better fool potential victims.
Gathering victims
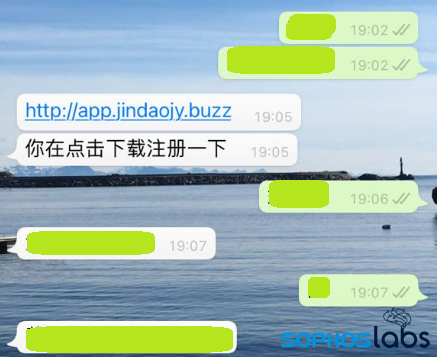
Our research began when we were asked to investigate an application by a user who fell victim to a scam. According to the victim, the initial contact with the actors behind the app came through a social media and dating site.
The scammers befriended the victim, and shifted communications to a messaging app. They avoid requests for face-to-face meetings, citing the Covid-19 pandemic. After gaining trust, they then convinced the victim to download a cryptocurrency trading app, sending the victim a link.
The link was to a page impersonating a Hong Kong based trading and investment company called Goldenway Group. The page had options to download both iOS and Android apps.
The scammers then walked the victim through the installation and encouraged the victim to buy cryptocurrency and transfer into their wallet. When the victim asked to withdraw the cryptocurrency, the scammers behind the fake persona at first started making excuses, and then finally blocked the victim’s account—with all the purchased cryptocurrency in the scammers’ possession.
Goldenway is aware of these sorts of scams. A warning on the company’s actual website opens with an alert about fraudsters scamming users with a similar named site and asks its users to steer clear of such apps.
As we investigated the fraudulent Goldenway app, we discovered that the scheme was much more wide-ranging. We found hundreds of fake trading apps being pushed through the same infrastructure, each disguised to look like the official trading apps of different financial organizations.

Bypassing the iOS App Store
Apple’s iOS App Store and enterprise private app store programs screen applications regularly and revoke the developer account of fraudulent app developers—killing the malicious or fraudulent apps deployed with the accounts’ digital signature. To evade this sort of oversight, the malicious apps we investigated use third-party services to deploy that leverages what’s known as a Super Signature process.
Some of these services, such as Dandelion (pgyer[.]com), are intended to support small application developers perform test deployments of their apps before pushing them to the iOS App Store. They allow app developers to use Apple’s ad-hoc application distribution method to deliver applications to iOS devices—a process intended to allow developers to distribute apps directly to a limited number of devices for testing.
But some of these services are easily abused by malicious app developers. Ad hoc distribution abuse allows malware developers to avoid App Store screening and the threat of revocation of apps’ certificates.
To deploy applications, these sites distribute a manifest file called mobileconfig, which contains details such as the URL of the app payload, the app’s display name and a universally unique identifier (UUID) for the payload. The owner of the target device is prompted to install this manifest file; upon installation, the UDID (unique device identifier) of the iOS device is sent to the server, and the user’s device gets registered to a developer account. The IPA (iOS App Store package) containing the app is then pushed to user for download. Tutorials for this process—the exact one used by these fake applications—are available on the Dandelion site and others, including full demonstration video.
While many of these Super Signature developer services may be targeted at helping legitimate small app developers, we found in our investigation that the malware used many such third-party commercial app distribution services. These services offered options for ‘One-click upload of App Installation’ where you just need to provide the IPA file. They advertise themselves as an alternative to the iOS App Store, handling app distribution and registration of devices.

While these services claim they were not responsible for the risk posed by the malicious apps deployed through them, and that they do not check the contents of apps or configuration profiles associated with them, they likely violate Apple’s terms and conditions by using a distribution scheme intended for limited testing as a way to deploy commercial applications and malware—especially those in Apple’s developer License Agreement. Some of the third-party services seen distributing this malware were hxxps://www.appleabc1[.]com and abcv120[.]com—sites that are no longer reachable.
Making this all work requires significant social engineering of the victim. If the user chooses from the website for the fake app to install the app on an iOS device.
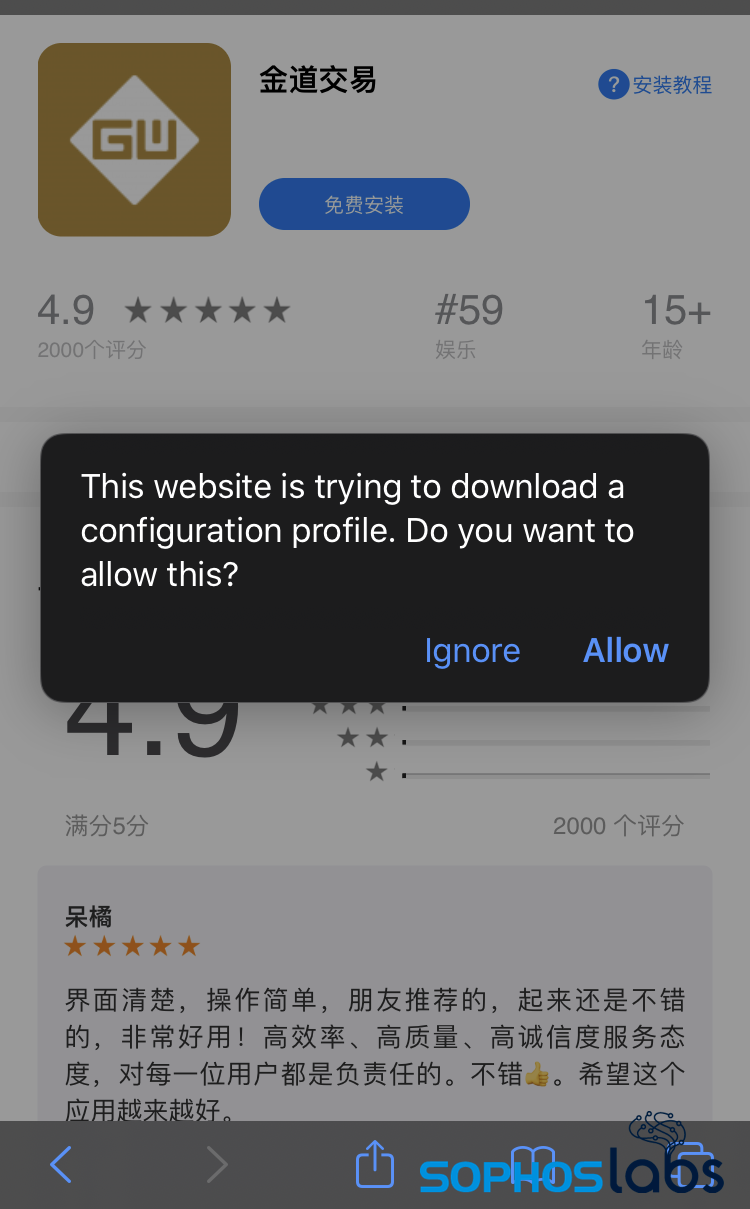
If the targeted user decides to download the iOS app, the click takes them to a web page that mimics the iOS app store and attempts to download mobile device management configuration file. The page even has fake reviews to help convince the target that the application is legitimate.
If the targeted user chooses to allow the download, the following manifest file gets downloaded:
PayloadContent
URL
https://sj9956[.]com/ios/udid?tag=xxxxxxxxxxxcc
DeviceAttributes
UDID
IMEI
ICCID
VERSION
PRODUCT
PayloadOrganization
授权安装进入下一步 (Authorize installation to the next step)
PayloadDisplayName
金道交易 --【点击安装】 (Golden Way Trading --【Click to install】)
PayloadVersion
1
PayloadUUID
3C4DC7D2-E475-3375-489C-0BB8D737A653
PayloadIdentifier
com.eletradeapp.jdjy
PayloadDescription
该配置文件帮助用户进行APP授权安装!This configuration file helps users with APP license installation!
PayloadType
Profile Service
The profile, once installed, launches a web download of the IPA file.
The profile automatically registers the victim’s device to the developer account used It obtains the victim’s UDID and automatically registers it to the developer account used to sign the downloaded IPA. It then pushes the app to the victim’s device.
Webbing it
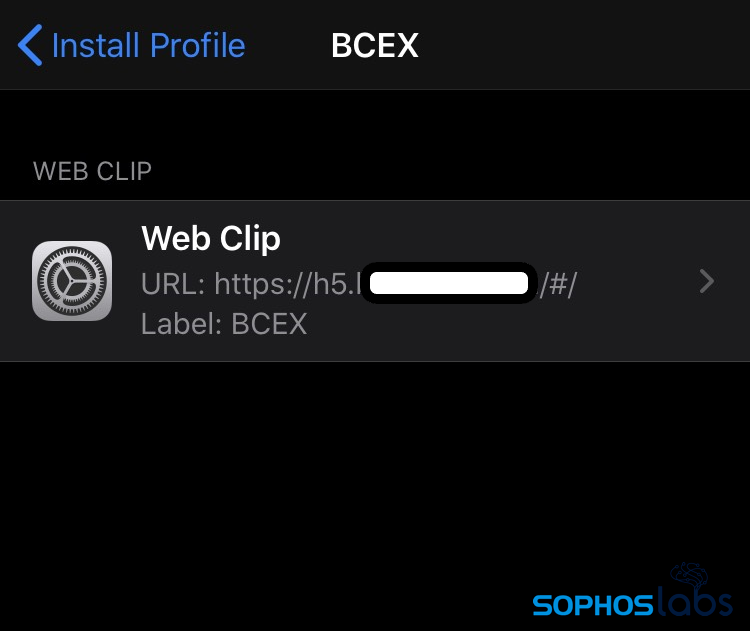
In some instances, the iOS distribution sites dropped “web clips” rather than IPA files. Web clips are a mobile device management payload that add a link to a web page directly to the iOS device’s home screen—making web-based apps act (at least from the perspective of the user) more like mobile apps. A tap on the icon on the home screen takes the user directly to the URL associated with the web application.
These web clips pointed to web versions of the fake apps, with interfaces similar to those seen in the iOS applications.
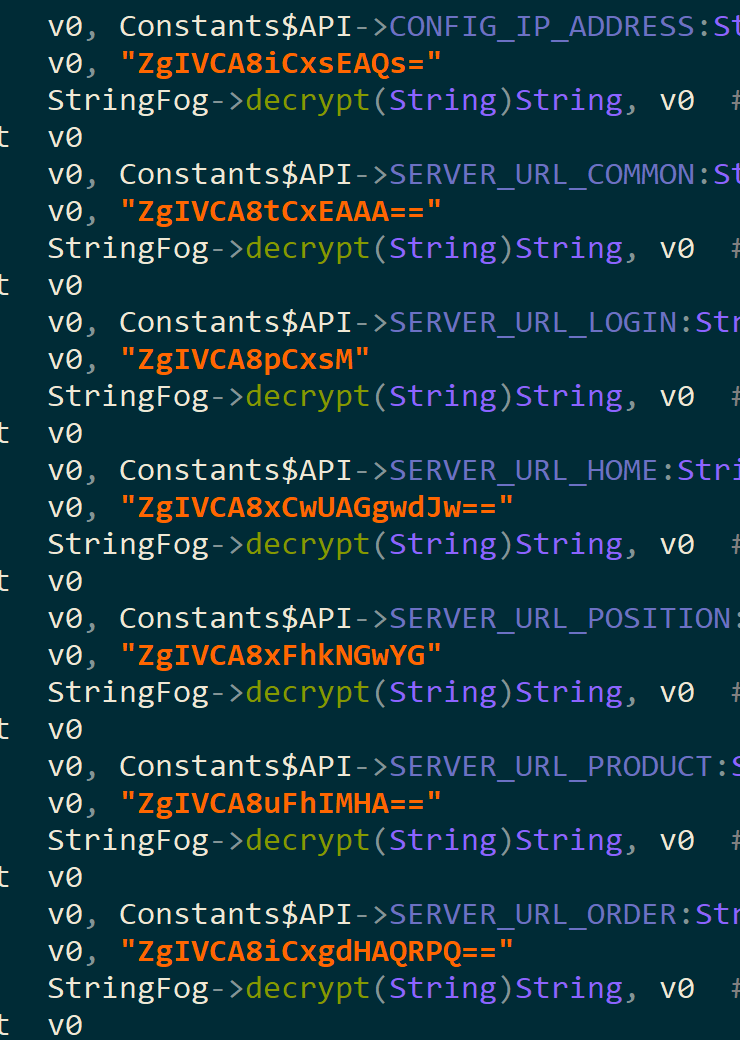
The Android apps we found used a slightly different approach to making web apps look like native ones. They have a server URL coded into the app and use a WebView to display the pag4 at this embedded URL. The URL and some of the other important strings in the Android apps are encoded using an opensource project called StringFrog, which uses a combination of base64 and xor with a hardcoded key.
Faking it
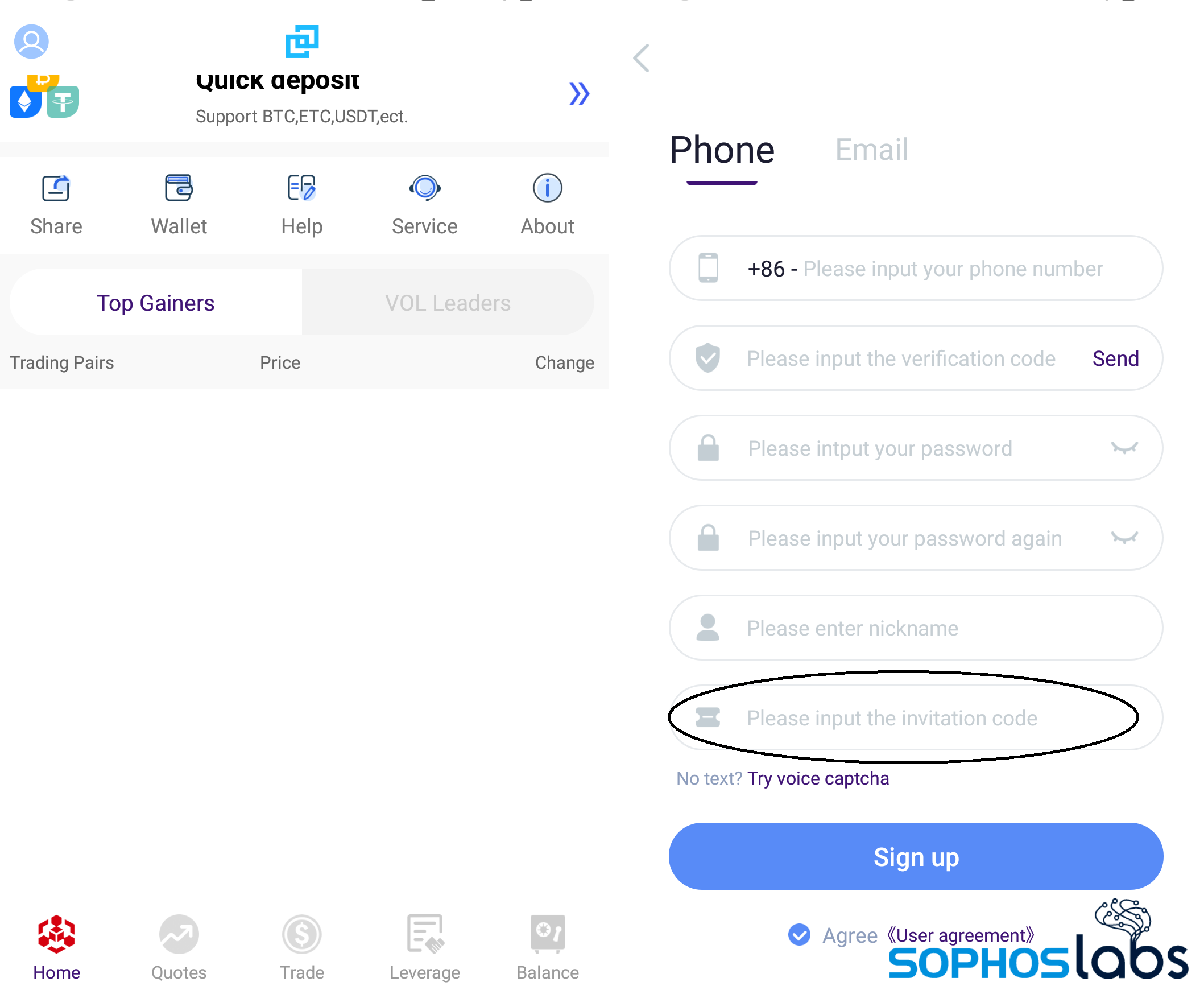
If the user completes the process of installing and launching the app, the user is asked to create an account—and in some cases, the app request an invitation code, possibly to restrict app access to those who were intentionally targeted.
Some of the fake trading apps we looked at had an interface with trading updates, wallets, fund and cryptocurrency deposit and withdrawal features that appeared to function just like their legitimate counterparts. The main difference, however, was that any transaction went into the pockets of the crooks instead.
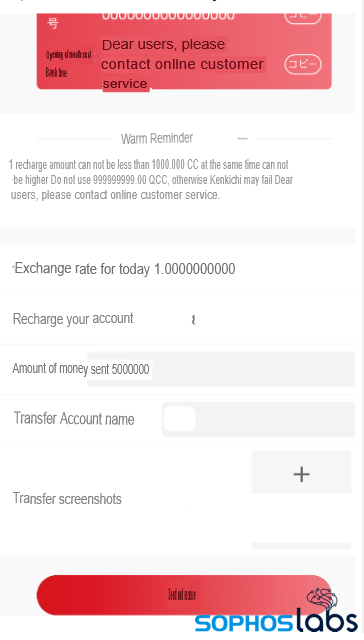
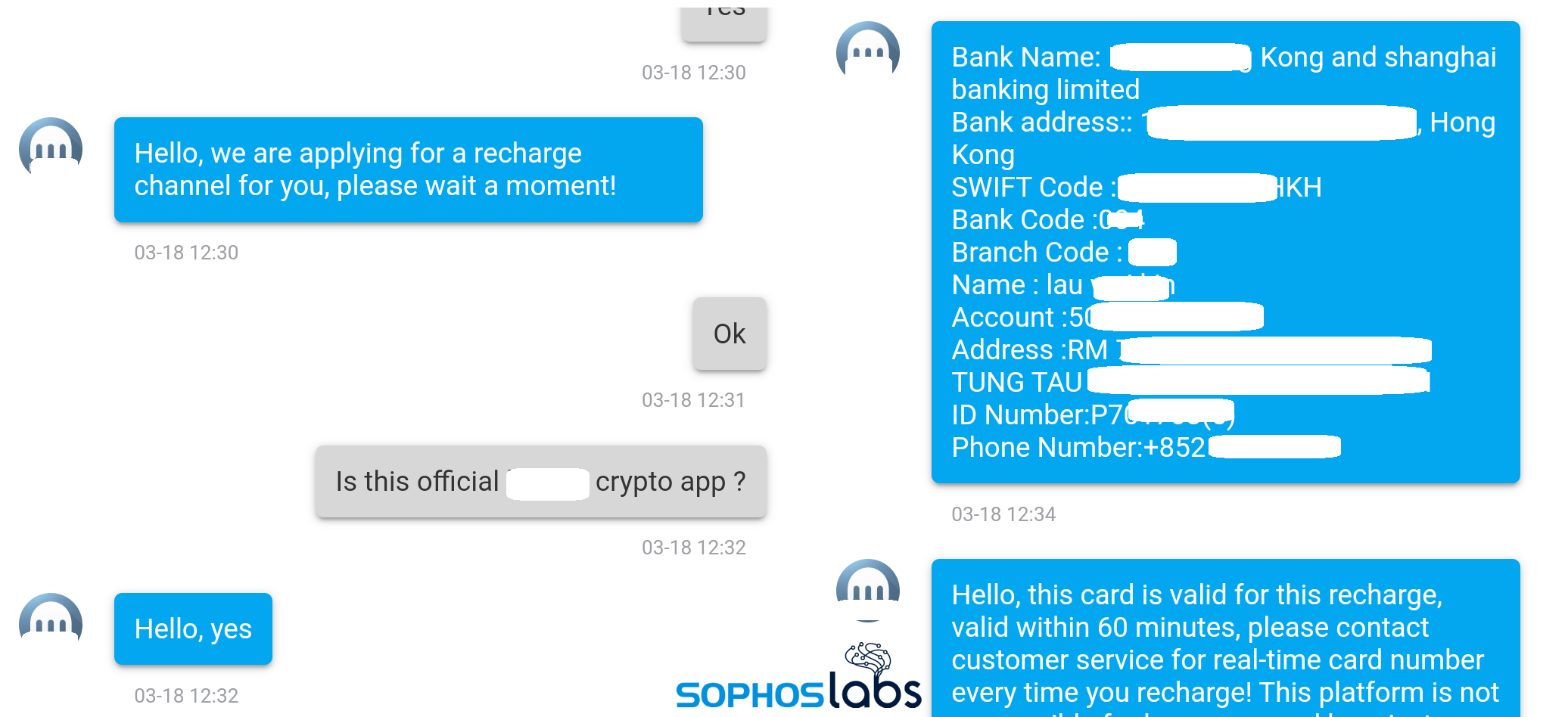
A translated transfer receipt from the fake app. These apps also had a customer support team. We tried communicating with the support teams using the chat embedded in the various fake apps; all of them resulted in similar replies indicating the possibility of same actor or actors behind all of them.
When asked to deposit money, we were given details of the recipient bank accounts based in Hong Kong. This looked like an individual account to which money was to be transferred using wire transfer. The bank details were different at various times, though all were based in Hong Kong.
People in Asia targeted
One of the servers referenced in the app had an open directory, from which we were able to collect a significant amount of uploaded data. It included several images of passport details, national Identity cards of both men and women, drivers’ licenses, insurance cards and bank and crypto transfer receipts. The passports and ID cards belonged to nationals from Japan, Malaysia, South Korea, and China.
We believe the ID details could have been used to legitimize financial transactions and receipts by the crooks as a confirmation about the deposits from the victims. We also found several profile pictures of attractive people likely used for creating fake dating profiles, which suggests that dating could have been used as a bait to lure victims.
Conclusion
Innocent people tend to put trust in things that are presented by someone they think they know. And since these fake applications impersonate well-known apps from all over the world, the fraud is that more believable. If something seems too good to be true—promised high returns on investments, or professional-looking dating profiles asking to transfer money or crypto assets—it’s likely a scam.
To avoid falling prey to such malicious apps, users should only install apps from trusted sources such as Google Play and Apple’s app store. Developers of popular apps often have a web site, which directs the users to the genuine app. Users should verify if the app was developed by its genuine developer. We also advise users to consider installing an antivirus app on their mobile device, such as Sophos Intercept X for Mobile, which defend their device and data from such threats.
The distribution scheme used in these fraud campaigns poses a larger threat. The Super Signature process can be abused by crooks to install additional malware in a targeted way on vulnerable users’ devices. This threat could (and should) be mitigated by Apple, which could stop abuse of third-party app distribution by alerting users when Super Signature distribution is used to install apps, or when such ad-hoc distributed apps are in use on the device.
Sophos detects these apps as Andr/FakeApp-DC, iPh/FakeApp-DD and iPh/FakeApp-DE. A full list of IOCs associated with the apps in this campaign is available on Sophos’ GitHub page.




Tom
What GitHub page? SophosLabs, Sophos, Sophos IaaS? Why didn’t you provide a link?
Jagadeesh Chandraiah
It was updated the next day, it should be active for you
TT
Thank you, I wish these were more highly publicized. I encountered the same scam with similar screenshots to the ones posted in this article but for a fake fxtm app.
Jagadeesh Chandraiah
Hi, If you still have the app/screenshots, feel free to DM me at @jag_chandra. I can take a look.
Nick
Hello i have a suspicious web / app , can you check if its legit or fake ?
Jagadeesh Chandraiah
Please send a message at @jag_chandra on twitter, I can take a look.
Marc
I feel like I’m currently being walked into a similar scam. Instead of using BTCbox’s authentic site, BTCbox.co.jp, I’m being directed to https://web.btcbox.app.
ZOSHOSH
Thanks for the information guys.
EC
Hi, I wished I had come across your article sooner because I fell victim to the same kind of scam described in the article. Could you please tell me if there is anything that can be done to help.
Jagadeesh Chandraiah
We can verify the scam app for you, though we can’t recover the funds, if you tell us about the scam ,Please send a message at @jag_chandra on Twitter.
Ching
I believe I am also a victim of this scam described here on this article as well. I was told to buy crytpcurrency from a wallet app BRD on google playstore and then to use their cryptocurrency platform app that I had to install on on their website called hxexfor.com. I was wondering if you guys are able to verify this app if it is a scam app.