Depending on your organization’s needs, you may be running servers on-premises, consuming cloud-based applications, or hosting resources in private and public cloud environments on AWS, Azure, or GCP. More likely, you’re doing all of the above.
The cloud is rapidly becoming more and more central to most organizations’ day-to-day operations. In fact, 90% of enterprise services are in cloud computing environments. Because of this, cybercriminals are alert to opportunities provided by the cloud — so much so that 70% of companies using the public cloud suffered a cloud security incident in the last 12 months.*
Securing the hybrid cloud
Organizations are increasingly adopting a hybrid cloud model with a mixture of services across SaaS, public, and private environments, while also maintaining legacy infrastructure on-premises until its ultimate migration.
When it comes to securing your resources — wherever they are located — you want to do two things:
- Protect the actual data on on-premises servers and hybrid cloud workloads
- Secure the networks where resources are held, whether they are in the cloud or the office
Protecting data and workloads
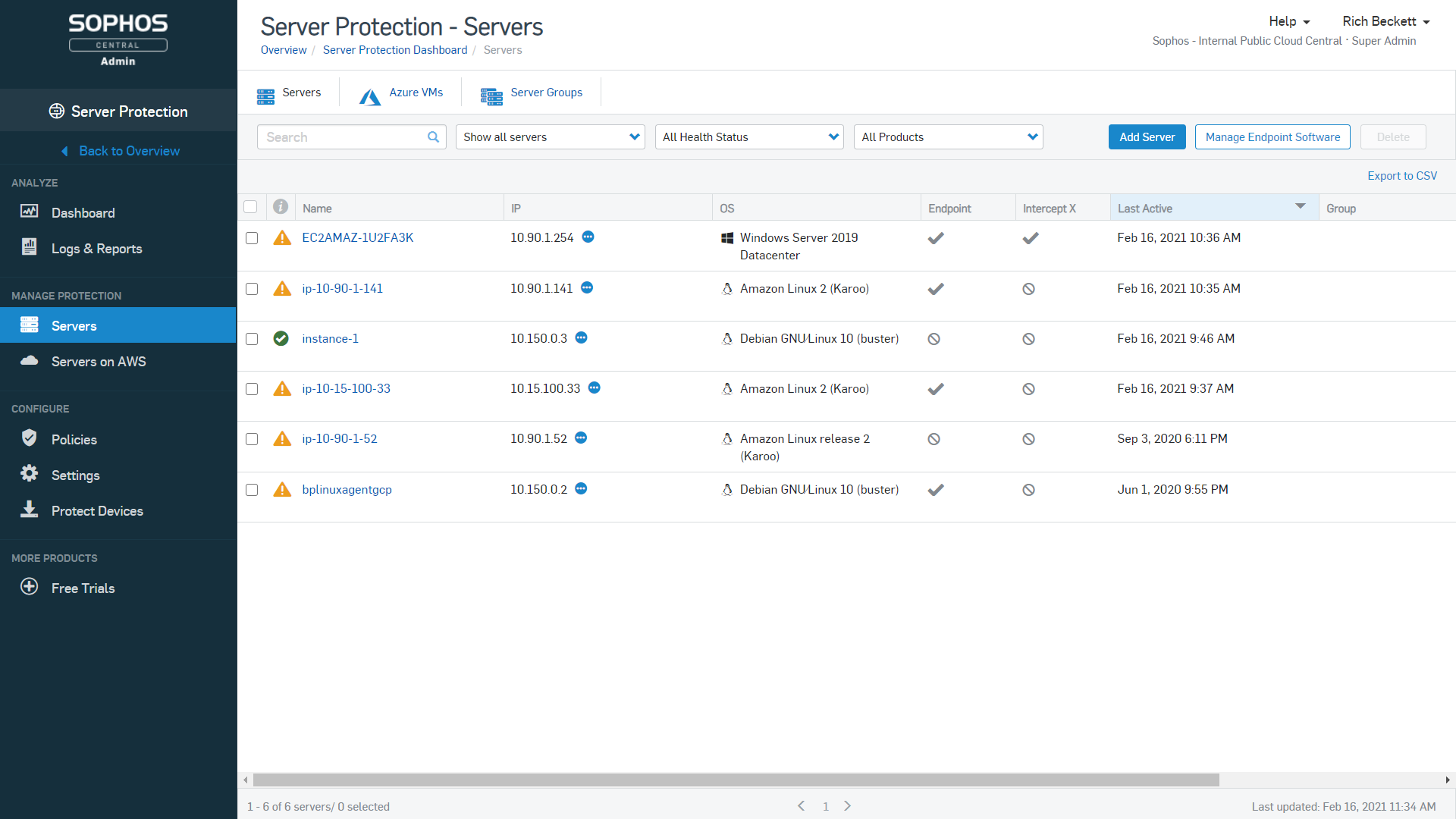
Sophos Intercept X for Server, protects data and workloads on your Windows and Linux (on-prem or in the cloud) servers, with the core focus to:
- Stop advanced malware, including ransomware, exploit-based attacks, and server-specific malware
- Protect virtual desktop environments to support critical remote working teams
- Lockdown your servers by controlling what can and can’t run and get notifications for any unauthorized change attempts
- Deploy and maintain everything from a single console, including mixed scenarios with cloud workloads and on-premises servers
We also have Sophos Intercept X for Servers with EDR (Endpoint Detection and Response) further extends your protection, helping you to:
- Expose evasive threats, search for issues, understand how attacks took place, and systematically respond to incidents
- Automatically detect cloud workloads as well as critical cloud services, including S3 buckets, databases, and serverless functions
- Detect insecure deployments with constant AI monitoring of your cloud environments for insecure configurations, network and user access anomalies
The other side to protecting your cloud workloads is visibility: seeing what’s running and securely configuring cloud provider services to prevent breaches.
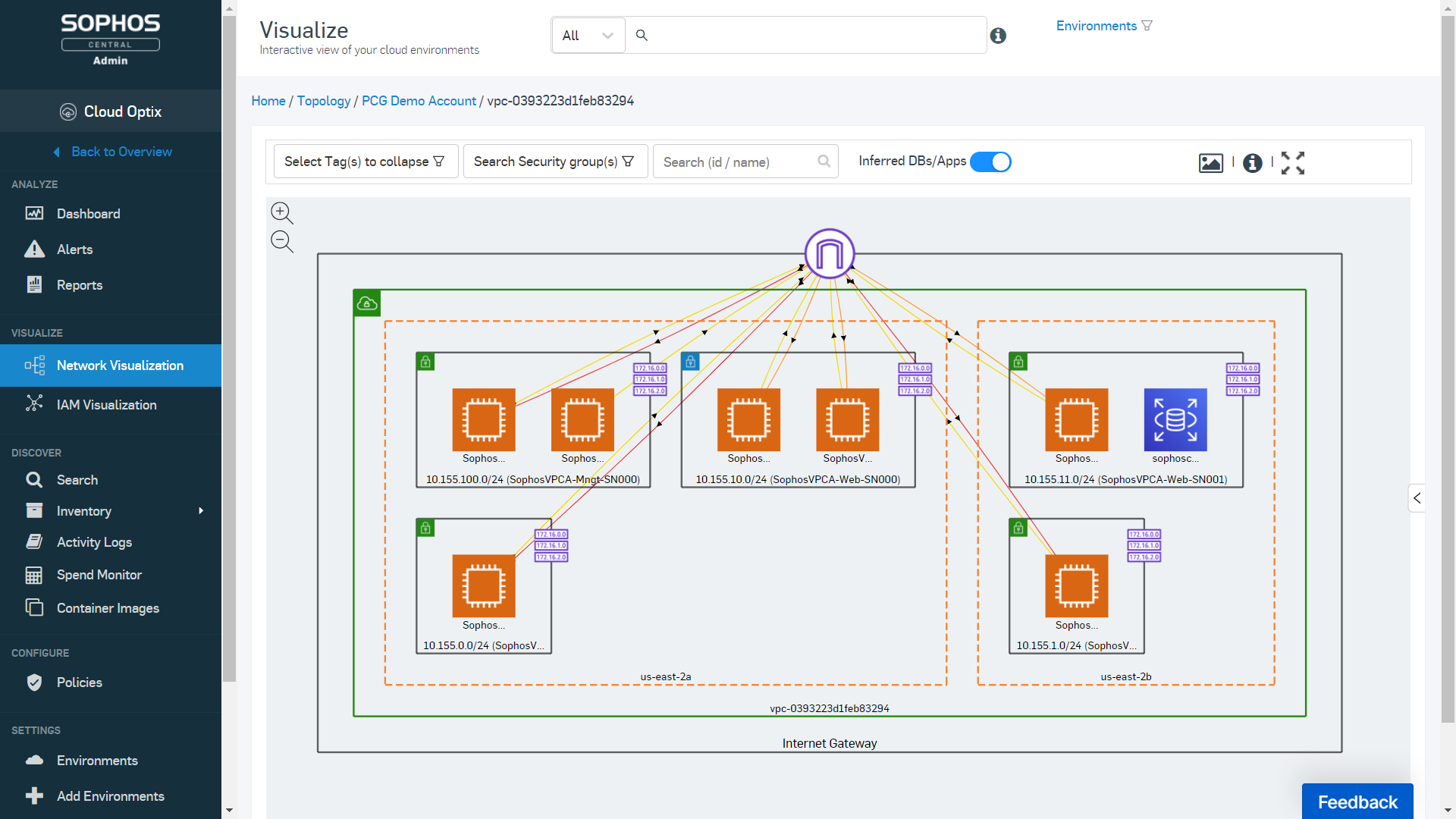
For unrivalled visibility, turn to Sophos Cloud Optix, the Sophos Cloud Security Posture Management service. We use Cloud Optix ourselves to easily identify cloud resource vulnerabilities, ensure compliance, and respond to threats faster across the Amazon Web Services environments that host Sophos Central.
Cloud Optix can provide you with:
- Asset and network traffic visibility for AWS, Azure, and Google Cloud
- Risk-based prioritization of security issues with guided remediation
- Identification of over-privileged IAM roles before they’re exploited
- Optimization for AWS and Azure consumption costs on a single screen
- Visualization of Sophos firewalls and server workload protection agents
While notifications and warnings are helpful, it’s all too easy to get overwhelmed by alerts. And it can be tough to decide which ones should be dealt with first and foremost.
One of the main benefits of Cloud Optix for the Sophos team is that it pinpoints where to focus attention so that you can proactively secure any vulnerabilities before breaches occur.
Securing the network
With your data and workloads secure, the next consideration is securing the network.
Sophos Firewall provides powerful protection and performance, securing on-premises networks, private cloud, and public cloud AWS and Azure environments. It protects networks, applications, and ensures security of ingress and egress traffic.
With Sophos Firewall, you get:
- An all-in-one solution: our preconfigured templates are purpose-built to secure environments from known and emerging threats, and maintain high web-application availability
- Extensive reporting, including full insight into user and network activity
- Cloud application visibility, shadow IT discovery, and automated threat response
Sophos Firewall enables you to harden your cloud workloads against hacking attempts like SQL injection and cross-site scripting. To make deployment easy and ensure that applications and users can always connect, everything is available in a single, preconfigured virtual-machine for maximum uptime.
Securing the anywhere organization
To learn more about how Sophos can help you enable users to work securely on any device from any location, read our solution briefSecuring the Anywhere Organization.
* The State of Cloud Security 2020, Sophos