During the past year, increased demand for cloud services has caused many IT and security teams to accelerate their cloud migrations.
As teams work through the initial lift-and-shift phases — where existing server workloads and operations are moved to the cloud — they quickly find the need to adopt more efficient and secure application delivery strategies that leverage DevOps methodologies, serverless frameworks, and containers technologies.
Move faster with Sophos Container Security
To move fast and stay secure, every organization needs visibility of its cloud security posture. This ensures that security remains the enabler for cloud transformation.
With Cloud Optix, Sophos makes advanced Cloud Security Posture Management available to businesses of all sizes and cloud maturity levels.
We’ve now enhanced the service to include container image scanning:
- Cloud Optix provides visibility of container assets across multi-cloud environments
- Vulnerability scanning identifies exploitable operating system vulnerabilities in container images
- Fixes for insecure container images are automatically identified
What are containers?
Containers are a lightweight and portable way to build, test, and deploy applications in the cloud. They make it easy for development teams to put new versions of software live quickly. This is largely helped by way of off-the-shelf public registry container images available to fast-track development work.
Compared to virtual machines (VMs), containers do not run a complete operating system; this is what makes them so lightweight and portable. All the files needed to run the container are provided from the container image, allowing a single container to be used to run anything from a software process to a larger application.
A rise in the use of Kubernetes and Docker services — and increased adoption of DevOps methodologies — have all contributed to this popularity.
Containers are mainstream
According to 451 Research, 95% of all new applications are now using containers. And along with increased container use, attackers have been busy exploiting vulnerabilities. There have been many incidents of container security breaches, including elevation of privileges and allowing malware to be installed.
As noted, developers utilize off-the-shelf images from public registries as a base for application development — and such images can contain security vulnerabilities.
According to recent research at least 11% percent of open-source components consumed by developers have at least one known vulnerability. Organizations need to be aware of the risks and identify vulnerabilities before applications are released to production or live environments, where attackers can exploit these inherent weaknesses.
Guard against container image vulnerabilities with Cloud Optix
Cloud Optix, the Sophos Cloud Security Posture Management service, helps prevent security breaches by providing both visibility of container assets and scanning to identify exploitable weak points in container images.
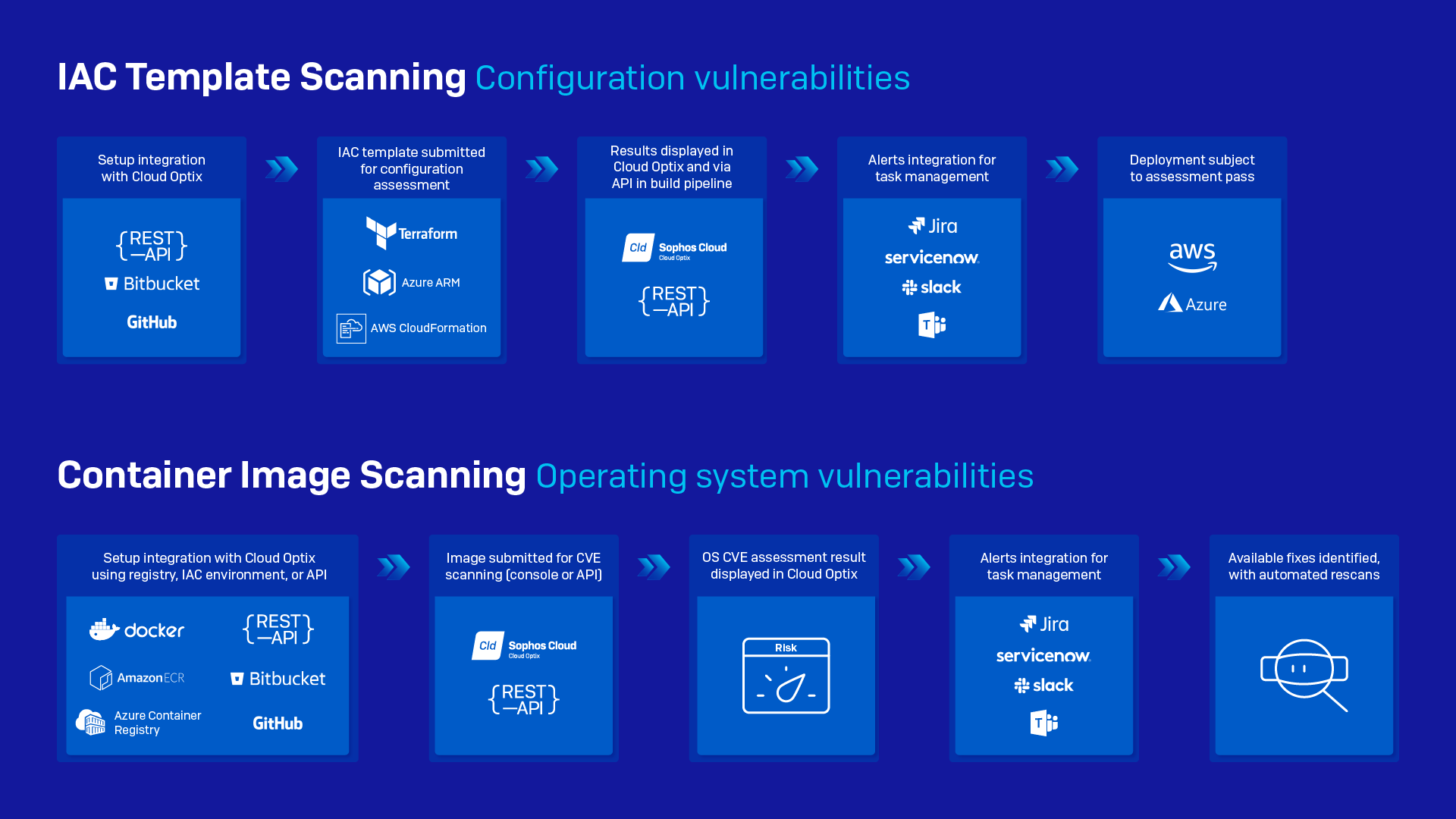
With Cloud Optix, organizations can scan container images pre-deployment to prevent threats from operating system vulnerabilities and identify newer versions of the image that may contain fixes.
This approach paves the way for security teams to enjoy fast and secure development by enabling DevOps teams to scan container images for security vulnerabilities in the following locations:
- Amazon Elastic Container Registries (ECR)
- Microsoft Azure Container Registries (ACR)
- Docker Hub registries
- IaC environments (Bitbucket and GitHub)
- Images in build pipelines (using the Cloud Optix API)
Thanks to the SaaS-based, agentless service, there’s nothing to install – making this new Cloud Optix capability is easy to set up.
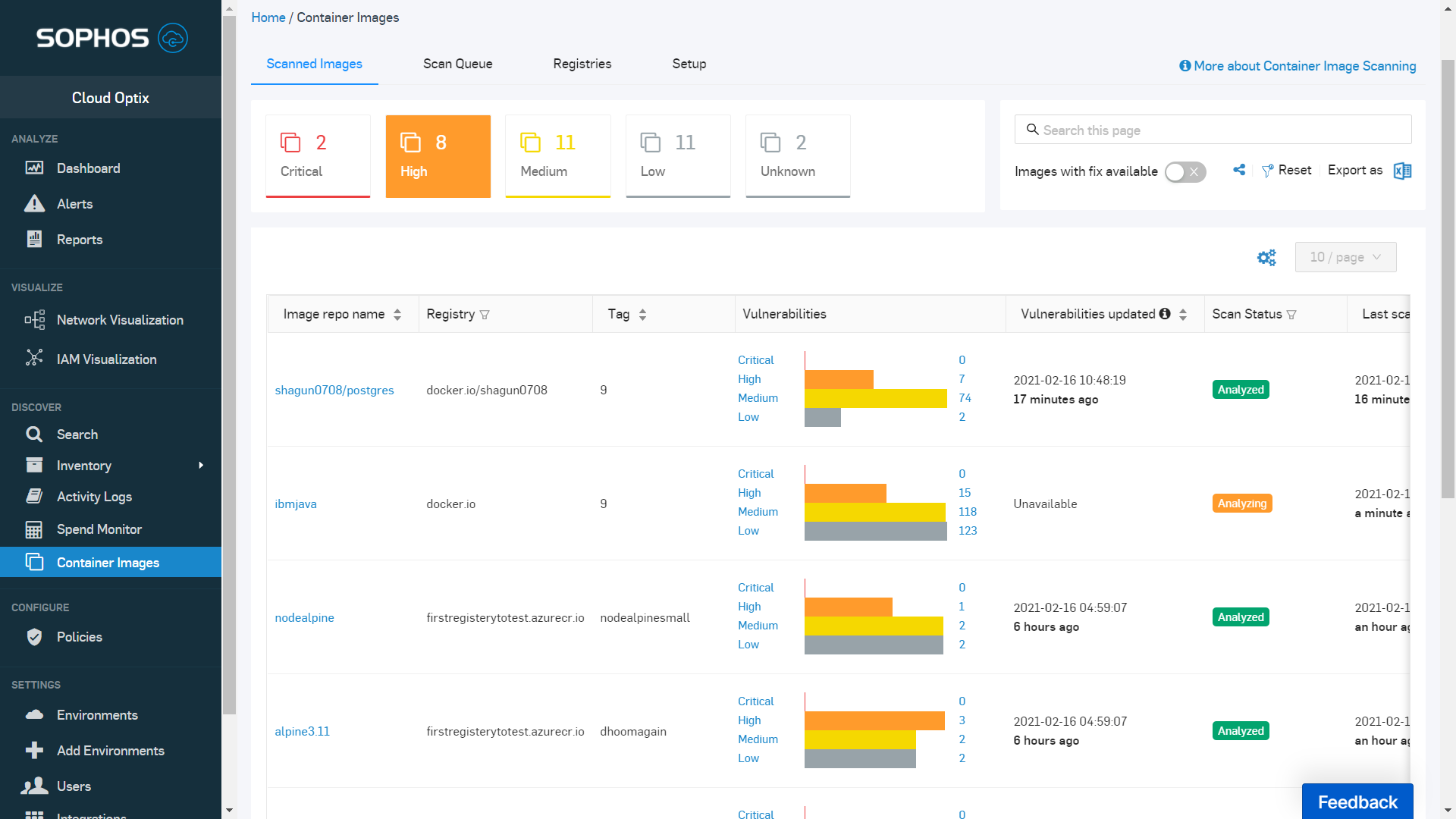
Once customers link their container registries to Cloud Optix, they will see details of scans performed, images queued for scanning, and vulnerabilities detected. The image-scanning process is regularly repeated automatically to identify new vulnerabilities and available fixes to existing container images.
Alerts for images with critical vulnerabilities can be sent to development teams via Jira, ServiceNow, Slack and Microsoft Teams integrations, providing visibility of security vulnerabilities and the tracking of fixes. With container vulnerability scanning from Sophos, you can ensure breach points are blocked before they can be compromised.
Visit Sophos.com/Cloud-Optix today to test container scanning for free.