Every month of the year has some sort of tax relevance somewhere in the world, and tax scamming cybercrooks take advantage of the many different regional tax filing seasons to customise their criminality to where you live.
In the UK, the 2019/2020 tax year ended on 05 April 2020, and the deadline for filing your taxes electronically was 31 January 2021.
With a January filing deadline, it’s not surprising for UK tax refund scams to kick in about now.
After all, everyone loves a refund, although they’re usually very modest in the UK if you get one at all, because your employer (if you have one) is supposed to get the tax calculations that they do on your behalf pretty close to the target.
So we weren’t surprised, although we were disappointed, to receive our first SMS-based tax scam of the season last night, helpfully submitted by a Naked Security reader:
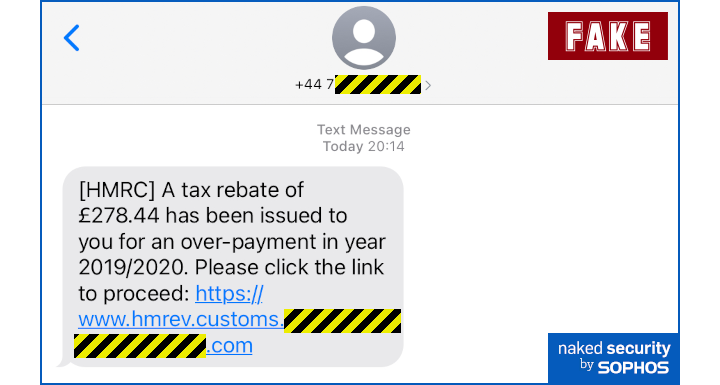
Delivered via a UK mobile number.
[HMRC] A tax rebate of £278.44 has been issued to you for an over-payment in year 2019/2020. Please click the link to proceed: https://www.hmrev.customs.[REDACTED].com
(HMRC is short for Her Majesty’s Revenue and Customs, and using that abbreviation in the UK is as usual and as expected as saying IRS in the United States.)
As regular Naked Security readers will know, there’s still a significant sector of the cyberunderworld that goes in for smishing, as SMS-based phishing attacks are colloquially known, for three simple reasons:
- Everyone with a mobile phone can receive SMS messages. There’s no need to guess which internet-based messaging apps you’ve signed up for, because anyone with a phone that can receive calls can receive SMSes too.
- SMSes are limited to 160 characters, including any web links. So there’s much less room for crooks to make spelling and grammatical errors, and they don’t need to bother with all the formalised cultural pleasantries (such as “Dear Your Actual Name“) that you’d expect in an email.
- Links in phone messages take you straight to your phone’s browser. Mobile browsers generally have much less screen space to show you the sort of security details that you can access from your laptop browser. Once you’ve tapped on the link and the browser window has filled the screen, it’s harder to spot that you are on an imposter site.
Annoyingly believable
In this scam, we have to admit that the crooks pulled off a surprisingly believable sequence of web pages – not perfect, but visually believable nevertheless.
Their pages look similar to the pages you’d see on a genuine UK government site; they’ve included niceties such as a coronavirus warning in order to add a touch of timely realism; they’ve mostly used the right sort of terminology, such as remembering to ask for your National Insurance number instead of your SSN; and they’ve remembered not to put a -Z- in the word organisation.
Fortunately, however, they were stuck with a bogus website name, because although it’s easy to register .COM and .CO.UK domains in the UK, the .GOV.UK domain has a strict registration process that a cybercrook would find hard to bypass.
Also, as you will see if you take the time to check really carefully (try “reading” the text on the page backwards using your finger – an old trick for proofreading your own documents), the crooks have made various mistakes, such as spelling errors, that you would not expect on a website such as HMRC’s:
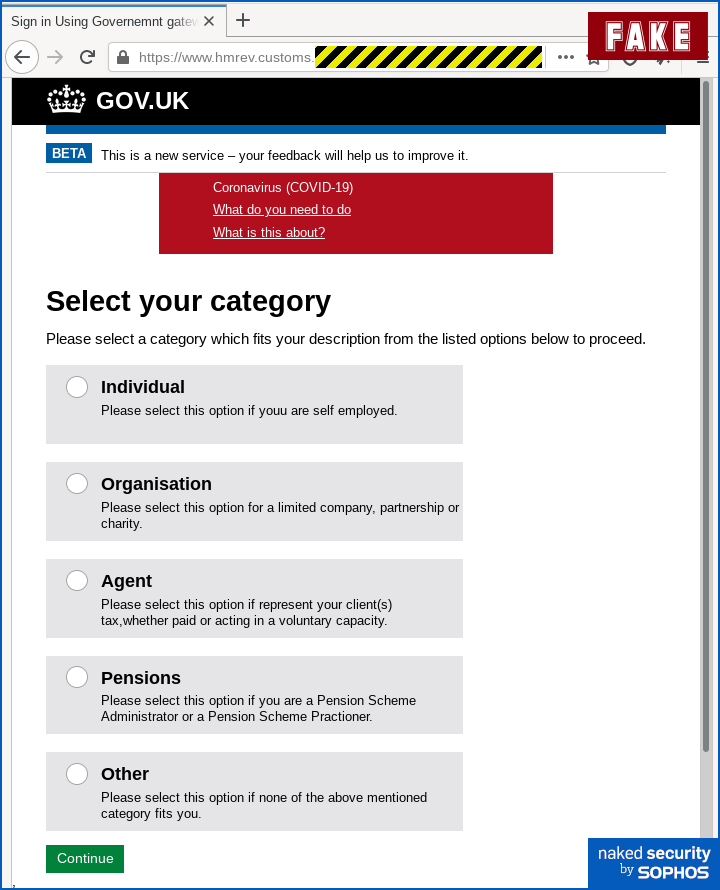
But look carefully: there are typos and errors here.
In this scam, the crooks also decided to take you straight to a bogus tax-related page.
However, the UK government gateway would make you login first, including using two-factor authentication, which would give you a different user experience:
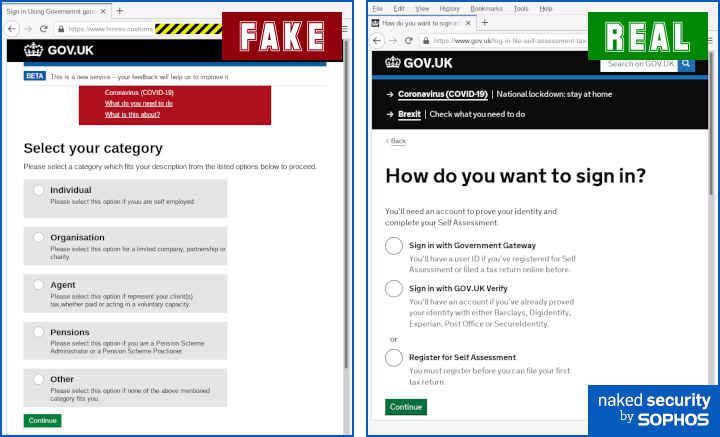
Right.Access to the UK tax site requires login first (2FA is compulsory).
You might think that 2FA is a hassle you could do without, but you can actually turn the “hiccup” that it puts in your way to your advantage.
Whenever your workflow is interrupted by a 2FA request, for example to retrieve a text message code or open up an authenticator app, use it as a reminder to implement the “Stop. Think. Connect” principle, and take some extra time to look again at all the security indicators you can find before you put in the 2FA code.
Check the address bar; go back and review which links you clicked to get there; take another look for giveaway mistakes in the messages and web pages you’ve seen so far. (Did you spot the weird word youu in the fake page above? If not, go back and look again now – it’s in the selection box labelled Individual.)
The phishing starts
The first phishing page asks for quite a lot of personal data:
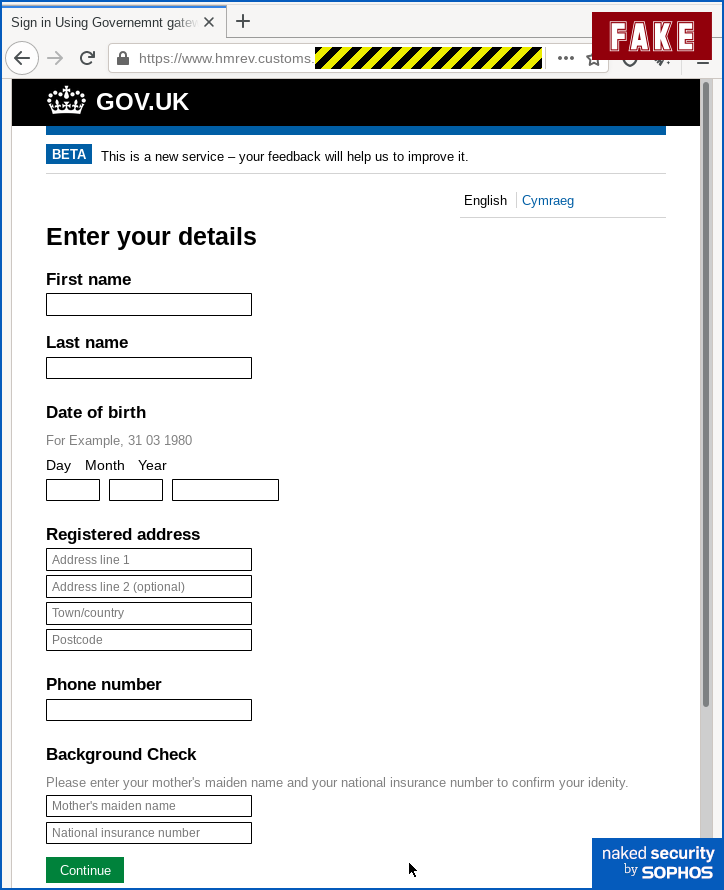
Field names follows typical UK terminology, but HMRC doesn’t use “mother’s maiden” name as ID.
Then the crooks go after your bank account and credit card details.
If you didn’t realise before, you should figure that this is a scam at this point, because there’s simply no reason for anyone to ask for your credit card data in order to make a refund to your bank account.
In particular, the CVV code (usually three digits on the back of your card) is used for verifying online payments, and in this case you aren’t paying for anything:

But putting in credit card data (including CVV “secret code) is what you do for payments, not for refunds.
Next comes a rather neat “decoy page” – a sort of polite placeholder page that brings this fraudulent process to a believable finish, along with a believable reason to discourage you from checking up right away with the real HMRC website:

But look carefully: there are typos and errors here.
After a few seconds, the final fake page above (did you spot the typo asking you to bare with us?) redirects you to the official UK government gateway home page, and wipes out your browsing history so far.
This leaves you on a genuine page with no easy way to go back and double-check what just happened on the fake pages:
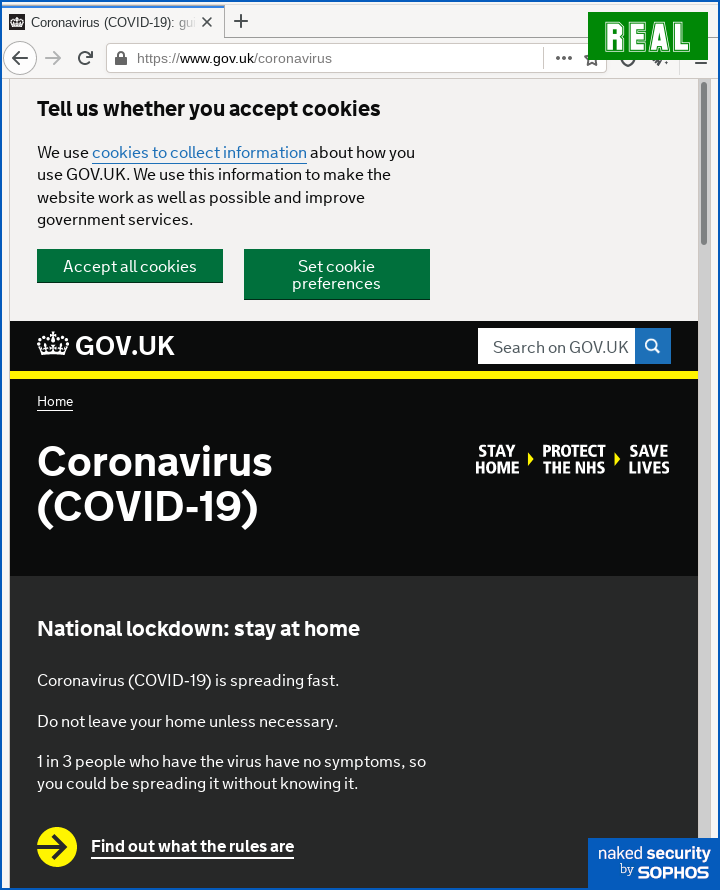
in order to round off the scam neatly.
What to do?
- Find your own way there. If you can, ignore links in emails, SMSes or other messages, even if you think they are genuine. Bookmark the official website of your country’s tax office and only ever go there using your own link. (Or if you are in the UK, type in GOV.UK by hand and start there.) If you only ever visit important websites using bookmarks of your own, you will always sidestep crooks who send you phishing links.
- Look for every hint of bogosity you can. This scam was surprisingly believable, but the telltale signs were there nevertheless: a giveaway spelling blunder by the crooks on the starting page, an obviously incorrect URL in the address bar, and a request for personal information that was irrelevant to the claimed refund.Take the time to look for signs of fakery – if the crooks make a visible mistake, take advantage of their error and make sure they don’t get away with it.
- Consider an anti-virus with web filtering. Phishing prevention isn’t really about keeping the bad stuff, such as malware, out. It’s about keeping the good stuff, such as personal data, in. An anti-virus such as Sophos Home (available free for Windows and Mac) or Sophos Intercept X for Mobile (free for Android) doesn’t just block malware that tries to get onto your device but can help to stop you getting to rogue web pages in the first place, thus keeping you one step further away from harm.
LEARN MORE ABOUT SMS SCAMS AND HOW TO STAY SAFE
(Watch directly on YouTube if the video won’t play here.)

Anonymous
It’s always a bit unsettling the fact that a fair portion of our ability to spot these scams relies on the crooks’ clumsiness.
How much more vulnerable will we be once they learn to spell properly…?
Paul Ducklin
Well, there’s still the incorrect domain name, which won’t match up; there’s using a password manager, which helps stop you putting the right password in the wrong site (your password manager is very literal when it matches up the domain of the displayed page with the domain associated with the account); and there’s our advice simply to avoid links in messages and to “find your own way there” so you never click links (or call back phone numbers, etc.) that came from an untrusted source.
Whatever the crooks do, *some* part of any fake site has to be fake, so just remember to take your time and check as much as you can!