You are probably familiar with the popular practice of “bug bounty” programs in software security, where an organization offers rewards or bounties to security researchers who ethically disclose security vulnerabilities in their software. Organizations set terms for bugs they will reward. Typically, the more severe the flaw, the higher the bounty.
However, if, like myself, you have worked for a software company, then regardless of whether or not it had a bug bounty program in place, you will likely have been on the receiving end of what has become known as a “beg bounty.” What are they and why are they such a menace?
The beg bounty playbook
“Beg bounty” queries run the gamut from honest, ethical disclosures that share all the needed information and hint that it might be nice if you were to send them a reward, to borderline extortion demanding payment without even providing enough information to determine the validity of the demand.
Just as in other areas of information security, ideas trickle down from experts to imitators. I began hearing from small businesses in the middle of 2020 about security researchers who had contacted them about vulnerabilities in their website. Should I worry? What do I do? Have I been hacked? Knowing these businesses did not have a bug bounty program and in fact probably didn’t even know what code ran their website, it seemed odd for a legitimate researcher to be wasting their time on the smallest fish in the pond.
As a threat researcher, my response to every situation is, “Can you send me a sample?”. Fortunately, I was able to gather a few samples from my friends at Kobalt, a firm that manages cybersecurity for small and midsize businesses.
In each example, the “vulnerability report” or beg bounty was sent to an email address available openly on the recipient’s website. It was not hard to conclude that each message was a combination of:
- Automated scanning for basic vulnerabilities or misconfigurations
- Followed up by a human to cut and paste the results of the scan into an email template
- Figuring out where to send the report to try and receive a reward
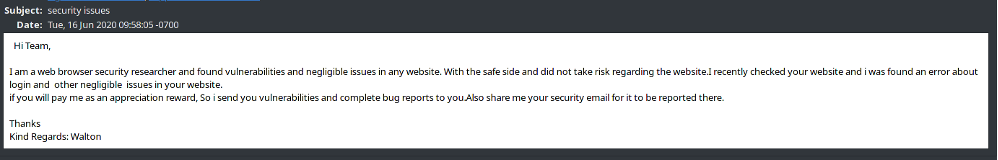
Example 1
This one certainly feels more on the side of extortion and less on the side of usefulness. Setting aside the fact that the writer is likely not a native English speaker (despite claiming the name Walton? Throwback to 70’s TV?).
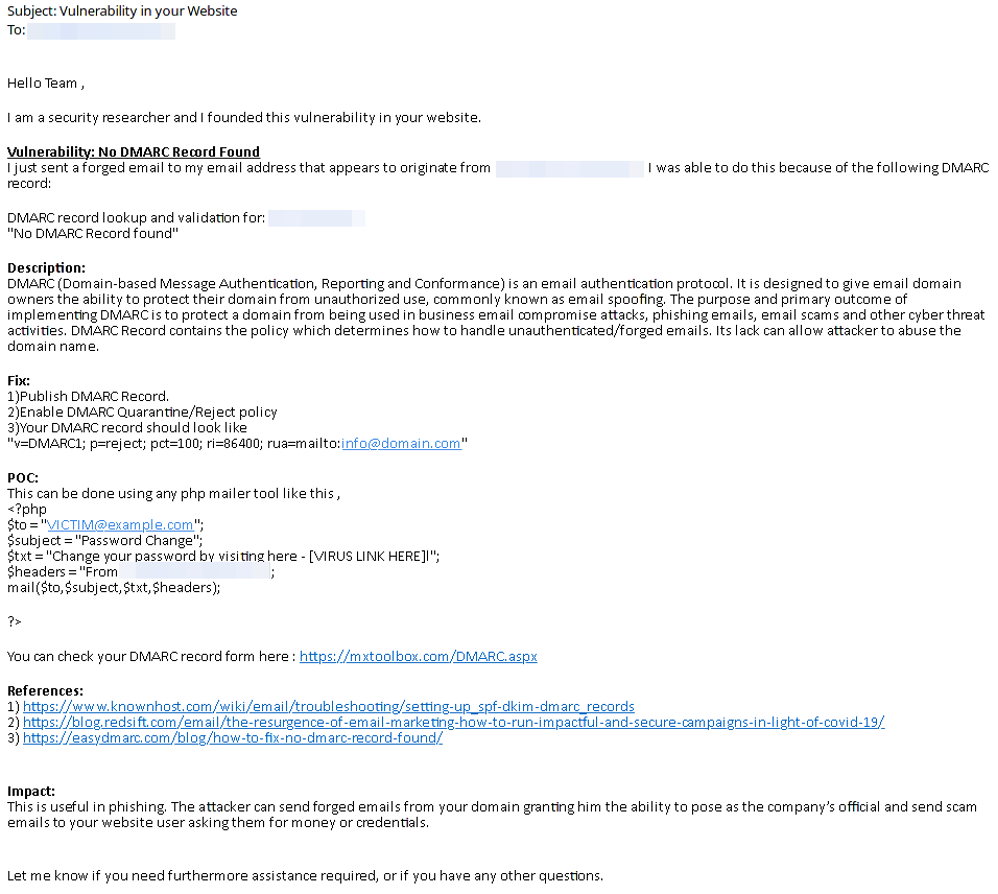
Example 2
This one starts with a factually incorrect statement. They claim to have found a “vulnerability in your website” and then go on to explain that you do not have a DMARC record for protection against email spoofing. That is neither a vulnerability nor is it in your website. While publication of DMARC records can help prevent phishing attacks, it is not an easy policy to deploy, nor is it high on the list of security tasks for most organizations.
This is certainly an improvement with regard to explaining the problem and provides a solution without threats or demands. While unsolicited and portrayed as more important and scarier than it is, it is helpful and perhaps hopeful that you may wish to engage in a further security test or relationship.
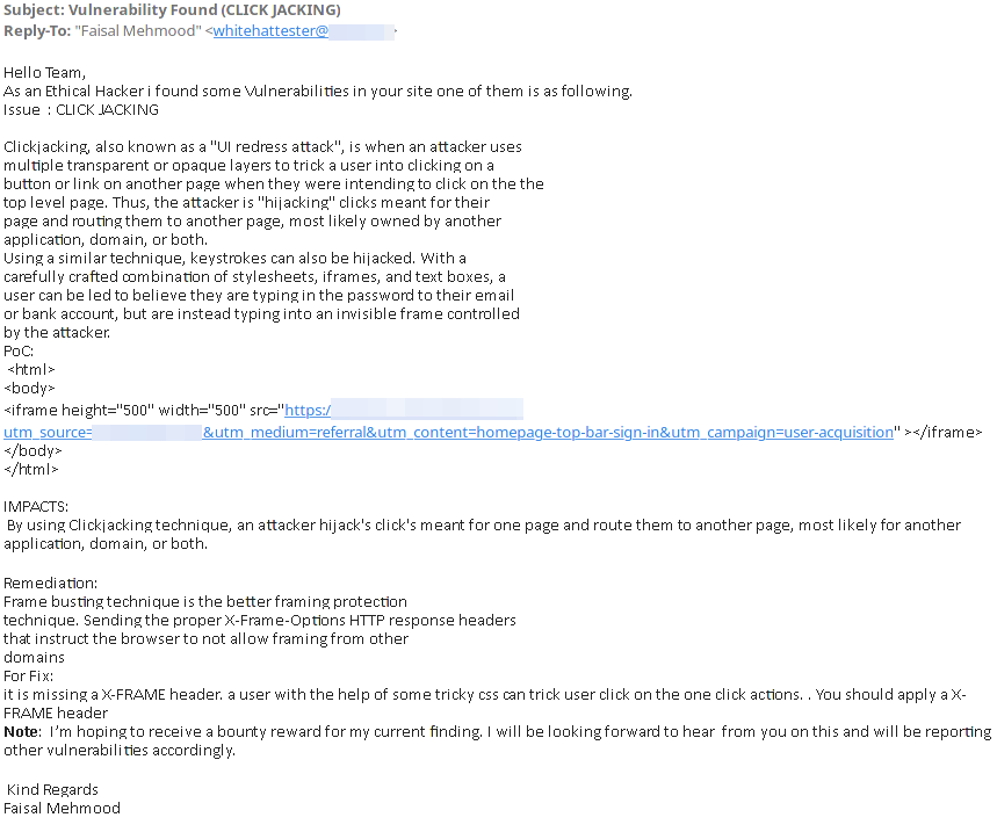
Example 3
This one starts out optimistically suggesting the sender is an “ethical hacker”. I have my own issues with this term as it suggests being a hacker is somehow unethical or morally bankrupt. I have been a hacker for more than 30 years and am quite proud of it. I have never hired an “ethical plumber” or an “ethical locksmith,” so it is unclear to me why my profession seems to require the modifier “ethical.”
Like the previous example, this “ethical hacker” provides a proof of concept (PoC), explains the impact and how to fix the issue. The explanatory text is clearly cut and pasted from websites that teach how to perform this type of basic tests/attacks.
I decided to engage with the third example as they seemed to be the most legitimate of the bunch.
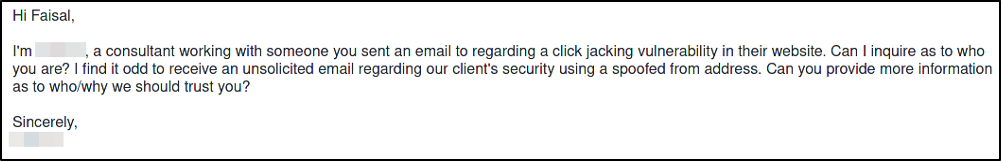
Within 24 hours I had a response from “Faisal.” I am not sure if that is the person’s real name, but the correspondence suggests this person probably means well and is who they say they are.
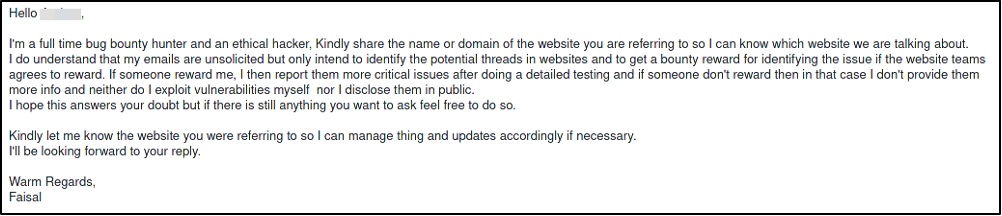
It is a bit of a stretch to call yourself a full-time bug bounty hunter when you are targeting websites of companies that do not offer bug bounty programs, but this person seems sincere and because of cultural differences may perceive this to be a legitimate marketing activity for their business. I proceeded to ask of them about their credentials and prices.
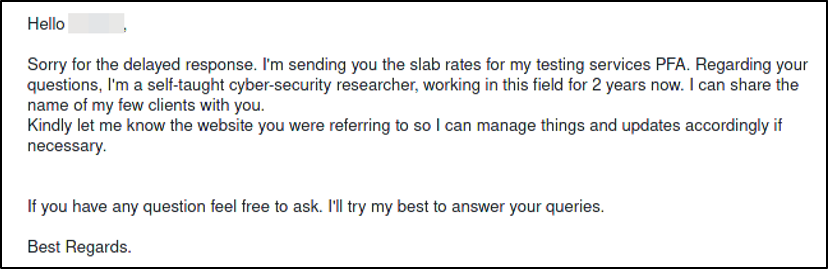
The prices quoted ranged from $150 to $2,000 per bug, depending on severity. Presumably this is in US Dollars.
There are reports that paying beg bounties leads to escalating demands for higher payments. One organization apparently said it started out at $500 and then, as further bugs were reported, the senders quickly demanded $5,000 and were more threatening.
Scaremongering for profit
Of the few examples I investigated, “Faisal” certainly seems to be the most professional and helpful, but that doesn’t mean that this type of behavior is acceptable. Most of the bugs that were found were not even bugs. They were simply internet scans that discovered the lack of an SPF or DMARC record. Others were genuine vulnerabilities that could be easily found without skill by using freely available tools.
None of the vulnerabilities I investigated were worthy of a payment.
The problem is that there are millions of poorly secured sites owned by small businesses that don’t know any better and are intimidated into paying for services out of fear.
Advice for recipients
If you receive one of these emails it is worth taking seriously, as you likely have a very poor security posture, but you should not engage with the person soliciting your business.
Contact a local trustworthy firm to assess your security weaknesses, one that can work with you to prioritize and improve your security situation.
If you are a security professional whose colleagues or customers have come to you with one of these emails, please reach out to me on LinkedIn or Twitter (@chetwisniewski). I am interested in talking to people conducting these unauthorized penetration tests to see if there are patterns or details that we can learn about their tactics.

Frazer
Just had a DMARC email come through and they seemed nice enough on the email though the issue is minor. I just felt the email was odd, especially how no price was given but a suggestion of a donation. I didn’t know what was the expectation or reason for the random check.
A helpful article here.
Ariya Rathi
I just felt the email was odd, especially how no price was given but a suggestion of a donation. I didn’t know what was the expectation or reason for the random check.
thanks for share a helpful article here.
JK
Had an open email from someone asking about our bug reward program, as they had found a security hole which seemed a bit off to me. So I decided to have a look around… Thanks for the heads up
Phil
Hi Chester, thanks for this helpful article. We recently received the DMARC email from a couple of different people requesting a bounty.
I’ve previously engaged with some of these ‘ethical hackers’ in the past, as one had identified a minor but useful-to-known vulnerability that we did fix. It seems they are small-time guys looking to earn a few bucks.