It’s the first Patch Tuesday of the New Year, bringing 83 new security fixes to Microsoft products—a relatively quiet month compared to many last year. Only seven of the vulnerabilities fixed in today’s release are as Critical—all of them remote code execution bugs. And one of those vulnerabilities is being actively exploited: CVE-2021-1647, a bug in Windows Defender, Microsoft’s built-in anti-malware software.
The Defender vulnerability allows remote code execution, triggered when a crafted file is scanned by Defender. An error in Defender’s handling of how it parses section information structures in certain executable files can result in the execution of code embedded in a scanned file. This would allow attackers to remotely execute code by sending a file in any way that triggers a Windows Defender scan. Since this is already being exploited, CVE-2021-1647 is an essential patch for many Windows users—the only short-term mitigation would be to disable Windows Defender. Fortunately, Sophos Windows end-point security customers have already done this, as installing end-point security software deactivates Defender.
A less critical, but likely to be exploited vulnerability is CVE-2021-1709, a bug in Windows Win32k component that could be used by attackers to gain escalation of privilege for malicious code execution. The bug, related to how Win32K processes handle private Device Context (DC) objects, allows an attacker to force Win32k to free the same DC object twice during the process cleanup. This results in memory corruption, which—if successful—would allow an attacker to control objects in kernel memory that could result in code execution with the highest privilege. However, this bug can only be exploited locally via interactive user access.
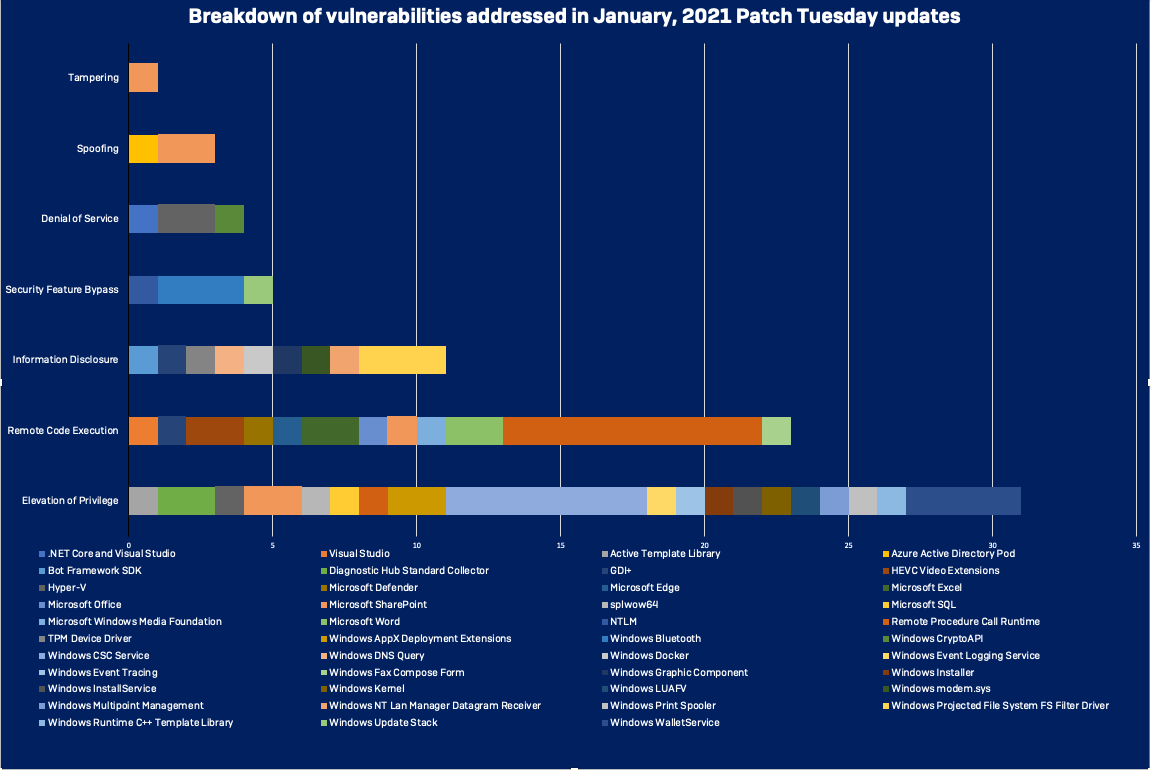
A breakdown by type and product of the vulnerabilities fixed in Microsoft’s January patch release. (click to enlarge)
More reasons to patch
All of the remaining “Critical” vulnerabilities are remote code execution bugs. Five of them (CVE-2021-1658, CVE-2021-1660, CVE-2021-1666, CVE-2021-1667, and CVE-2021-1673) are Remote Procedure Call (RPC) runtime bugs. Two are video-related—one (CVE-2021-1643) in Windows’ HEVC Video Extensions, and another (CVE-2021-1688) in the Microsoft DTV-DVD Video Decoder. Another, CVE-2021-1665, is in the GDI+ graphics library.
The final one is a memory corruption bug in the Microsoft Edge browser. The vulnerability, CVE-2021-1705, is HTML-based. But while the HTML-based attack can cause memory corruption, it would be difficult to leverage that into remote code execution.
Beyond the critical bugs, the RPC runtime had five more vulnerabilities addressed in this month’s patch release, for a total of ten. Four of them (CVE-2021-1664, CVE-2021-1671, CVE-2021-1700, and CVE-2021-1701) are additional remote code execution bugs, while one (CVE-2021-1702) results in elevation of privilege.
SharePoint has six problems patched this month, including one rated as more likely to be exploited: a remote code execution vulnerability (CVE-2021-1707) based on abuse of SharePoint’s SafeControl assembly mechanism for trusted ASPX and “Web Part” components. It requires an authenticated user with default access to execute, but can execute code on the server with the permissions of the SharePoint service account. The other SharePoint issues are two spoofing vulnerabilities (CVE-2021-1641 and CVE-2021-1717), two elevation of privilege bugs (CVE-2021-1712 and CVE-2021-1719), and one server tampering vulnerability (CVE-2021-1718)—all rated as less likely to be exploited.
Another big source of bug fixes this month was Windows’ Client Side Cache (CSC) Service, with seven vulnerabilities (CVE-2021-1652, CVE-2021-1653, CVE-2021-1654, CVE-2021-1655, CVE-2021-1659, CVE-2021-1688, and CVE-2021-1693) which could potentially be used by attackers for elevation of privilege.
Rounding out the top bug sources is Windows’ WalletService, with four escalation of privilege vulnerabilities (CVE-2021-1681, CVE-2021-1686, CVE-2021-1687, and CVE-2021-1690).
Sophos protection
Here is a list of protection released by SophosLabs in response to this advisory to complement any existing protection and generic exploit mitigation:
| CVE | SAV | IPS |
| CVE-2021-1647 | Exp/20211647-A | SID:2304750 |
| CVE-2021-1707 | SID:2304754 |
Sophos aims to add detections for critical issues, based on the type and nature of the vulnerabilities, as soon as possible and where we have been given sufficient information to be able to do so. In many cases, existing detections in endpoint products such as Intercept X will catch and block exploit attempts without the need for updates.
≈

Leave a Reply