We are only 5 weeks away from the anniversary of the birth of modern ransomware, Sept. 5, 2013. I mark that day as a turning point because it was the day anyone spotted the first sample of Cryptolocker.
That fledgling ransomware pioneered a new technology to extract wealth from victims, which, in past cyberattacks, had always been the hardest path to success. Money is inherently traceable and is difficult to obtain electronically if you are a criminal, but Cryptolocker had a new trick up its sleave. Bitcoin.
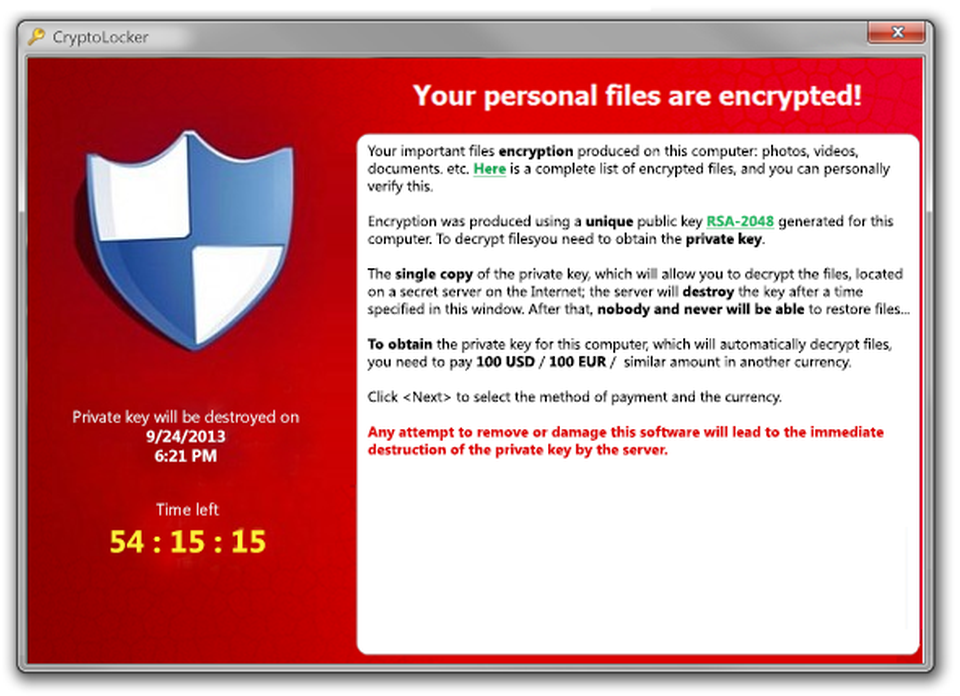
Here we are seven years later scratching our heads, still thinking about what to do to defend ourselves against ransomware. You would think in seven years we ought to have gotten better at deterring attackers from this type online crime.But, like almost everything in information security, ransomware is a complicated, and an attack that has only grown more complex, particularly in the last 10 months.
One measure of our success is to force the criminals to up their game, and if we are effective at this we should see a reduction in attacks or a shift to something else or new techniques. For example, when we got together to stop fake anti-virus from using shady credit card processors, criminals moved onto ransomware.
Based on this, you could argue that we, as an industry, have been very successful at stopping ransomware. When ransomware was introduced it depended on infecting large numbers of innocent people and demanding $400-$1000 US dollars each to make money, causing widespread harm. These attacks were automated and were largely a numbers game. This is not how ransom attacks look today. Once again, the attackers shifted.
We have upped our security game with regard to patching and far more sophisticated endpoint security technologies which make mass infection not worth the effort, if you’ve got skill. Bypassing security tools is hard and if you hurt millions of people per month, vendors will be sure to make sure your attacks fail. Attackers need a bigger payoff to make it worth bypassing the security protections. Ideally they want it to be harder for security companies to get samples to analyze the latest bypass, extending its useful time as a tool of ill repute.
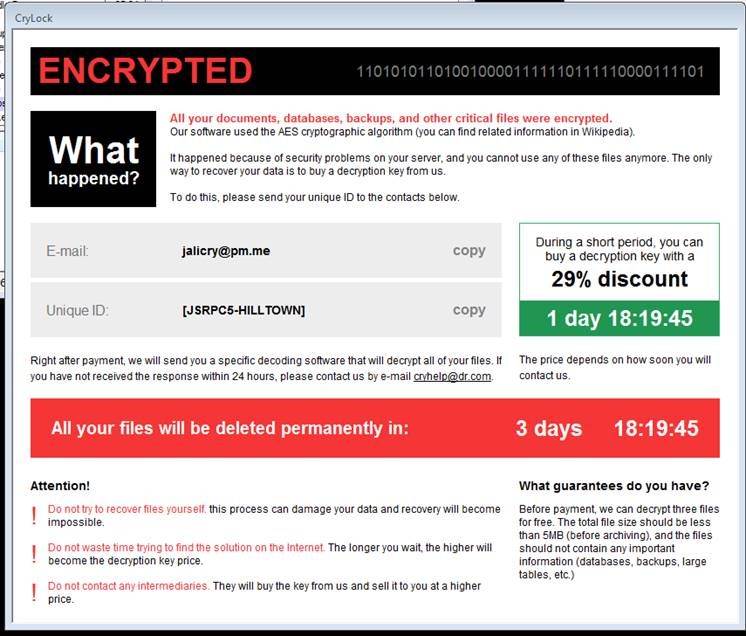
Drastically reducing the super low-hanging fruit like out-of-date Adobe Flash Player and abandoned versions of Oracle Java has also forced a shift and has kicked off a stratification in the malware operator ecosphere. “Script kiddies” will never go away, but the harm they cause is less than ever before and the risks they pose have been minimized by our improved hygiene. The response to this has been those with actual skills separating from the pack and upping their game.
Mass scale attacks are risky, so those with these skills began to develop far more sophisticated attacks, often taking pages from nation-state playbooks, but being just cautious enough to avoid activities that could potentially land them in prison. Because of these attacks require a higher caliber skill set more time is invested, the payoff needs to be much higher. .
The result is that average organizations, not just governments and defense contractors, now have human adversaries. This was not in most organizations’ plans. They were and are woefully unprepared for this new reality which has led to the deluge of news stories about ransom, extortion and data breaches.
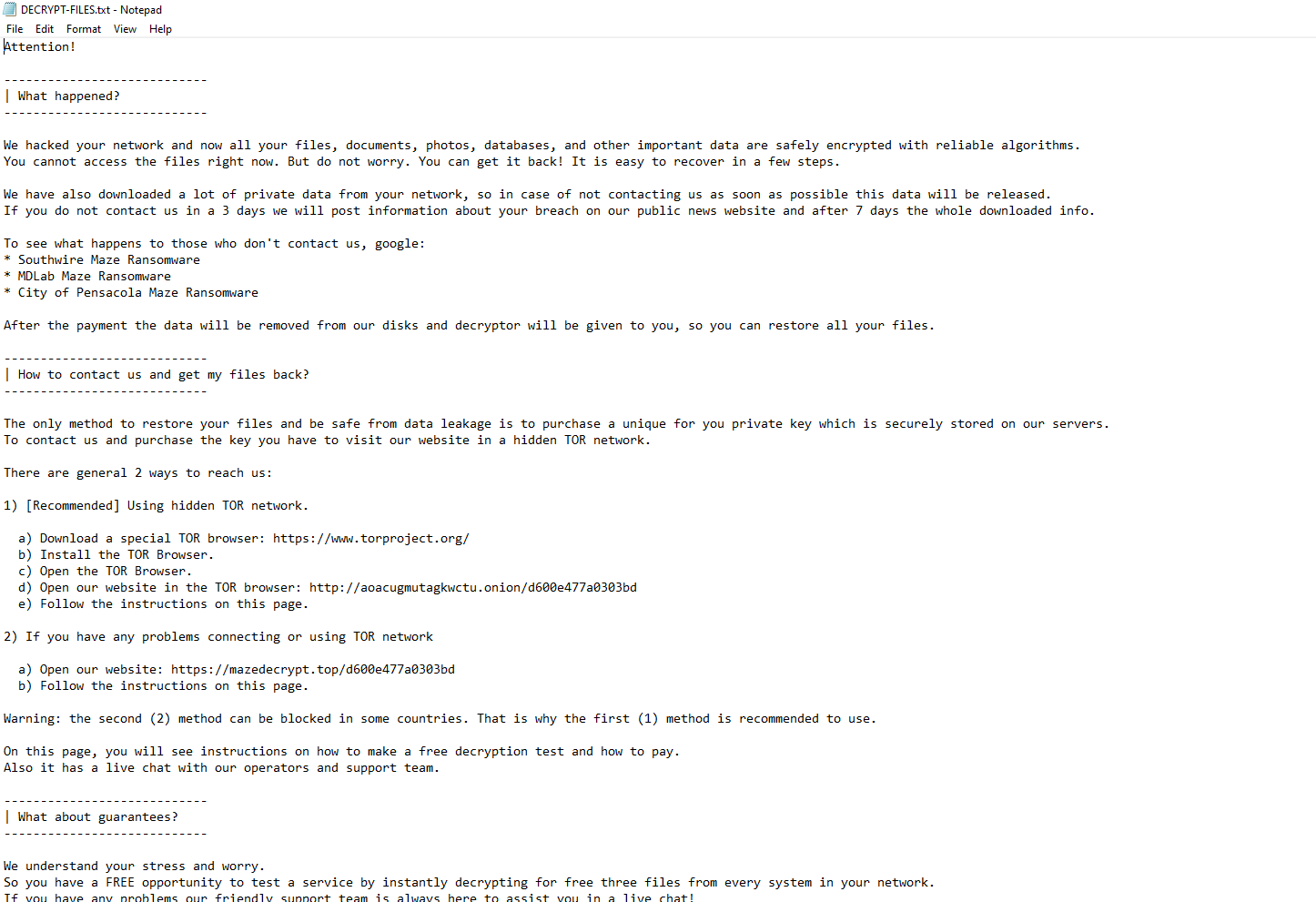
One of the most significant of the recent innovations has been a concerted effort to bypass security tools. Because there is a human at the keyboard, the methods and tactics utilized differ in nearly every attack. If they can phish a password for an admin, they log into the security management console and simply turn everything off. If that doesn’t work, groups like Snatch have turned to booting into Windows “safe mode” where many security protections are disabled before launching their encryption routines. And, now, with Wasted Locker, we are seeing the depths of internal Windows behaviors like memory mapping and caching being abused to bypass behavioral anti-ransomware technologies.
These evasion techniques are rapidly changing and we don’t expect this to slow down. Humans are hand crafting artisanal malware and carefully deploying it at low volumes in an attempt to stay below the radar. They don’t just clobber everything in sight, they carefully select which systems to steal data from and only incapacitate your most valuable assets. This takes a bit of time which can be an advantage to defenders, if they are well prepared to hunt down the telltale signs.
If the door is even open a crack, they can and likely will get in. Exposed servers with remote desktop (RDP) enabled, administrators without multi-factor authentication for remote access, unpatched web servers or even these same issues at a trusted partner or service provider are enough to provide opportunity to take you down this well-trodden path.
If your tools succeed at blocking the initial attack, they will not just give up. They are humans and will find a way around any programmatic barrier. Humans are tenacious, we are creative and we don’t give up easily. To defend against this you need humans to sort the wheat from the chaff. Tactics change on a weekly basis and knowing the signs of your own tools turned against you is the key to early detection.

This is a war, not a battle. To stay ahead you need to be vigilant and have the right people, the right training and the right tools. The days of loading security software on your endpoints, dusting off your hands and walking away are long gone.
The criminals have hybridized their attacks combining automation to find victims with a gap in their defenses and humans to creatively use existing tools from the victims own network against themselves. This business model can net them millions of dollars per victim and cause uncountable additional damage.
Our defense needs to use the same approach. Computers, automation and tools are amazing, but combined with human intellect, pattern recognition and our ability to extrapolate from the past into the future they provide a formidable defense. Those that are having success at defending themselves almost always have the right mix of investment in people, training and tools.
