Moving data and other corporate resources to the cloud makes a whole lot of sense, especially with more of us than ever needing flexibility in how, when, and where we get work done.
While cloud providers like AWS give you the flexibility to make your move to the cloud as temporary or permanent as you need, there are some practical considerations you need to manage.
For example, you need to provide users with essential virtual desktop services required for day-to-day work. You also need to provide secure remote access for administrators and developers to private applications running on virtual machines in the cloud, which is the focus of this article.
Simple, secure remote access with Sophos XG Firewall
VPN connections are crucial to enabling secure remote working. Sophos XG Firewall provides two options for creating secure access to services hosted in AWS:
Option 1: SSL VPN
If you have users working remotely the XG Firewall User Portal is a convenient and secure way to access resources within AWS. From it, users can download a customized SSL VPN client software bundle, which includes an SSL VPN client, SSL certificates, and a configuration.
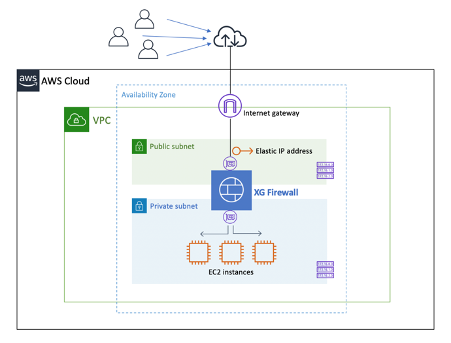
You first need to deploy XG Firewall in your organization’s Virtual Private Cloud (VPC). In the example below, the XG is deployed in a single Availability Zone, with one Elastic Network Interface (ENI) in each of the two subnets, a Public subnet and a Private subnet.
The Public subnet ENI has an Elastic IP address mapped that can be either used directly or in a DNS record. (View instructions for deploying Sophos XG Firewall on AWS).
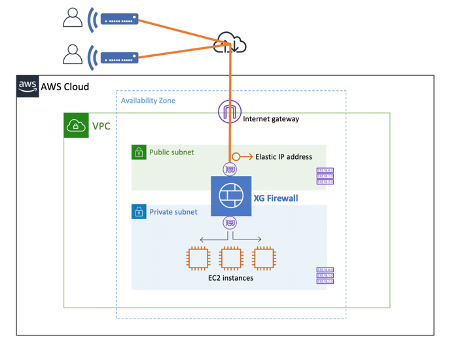
 An alternative to the XG Firewall User Portal is to install the SSL VPN client (or SophosConnect) on user systems.
An alternative to the XG Firewall User Portal is to install the SSL VPN client (or SophosConnect) on user systems.
View SSL VPN Client Instructions or SophosConnect Instructions / Video.
To complete this setup in your AWS console:
- Confirm your AWS route tables have a route for the Internet via the XG’s private interface (ENI) that the internal subnets use, and the public subnet table has an Internet route via the Internet Gateway, for the XG to use.
- Confirm your XG security group(s) allow the SSLVPN port in use (may not be 443)
- Confirm your other security group(s) allow traffic internally for the SSLVPN connections
Option 2: Sophos Remote Ethernet Device (RED)
If you want the ultimate in VPN reliability and security between your remote workers and your cloud environments, unique to Sophos is the Remote Ethernet Device (RED).
While perhaps not every employee in a business may require a RED, it may be a suitable choice for senior managers and people who deal with confidential information. Using a RED is simple:
- The IT team preconfigures and registers the RED with the XG Firewall, then mails it out to the recipient.
- The recipient plugs the device into their home router.
- The recipient sets up a wireless or wired connection between their laptop and the RED device.
Once connected to the router the RED connects back automatically to the XG Firewall (in AWS) and establishes a secure RED Tunnel. (Full Instructions – with video).
Helpful Resources:
- Getting started with AWS (Account setup and hands on tutorials for a range of services)
- XG Firewall on AWS FAQ (Benefits of XG Firewall on AWS including new licensing information)
- XG Firewall on AWS Deployment Guide (Step-by-step guide to deploying XF Firewall on AWS)
- XG Customer Resource Center (How-To Videos, Documentation, and more)
- XG How-To Video Library (Dozens of video tutorials to get you started)
- XG Community (Tap into the vast knowledge and expertise of the XG Firewall community)
