Over the weekend, researchers at cybersecurity intelligence firm Cyble came across a database with 267m Facebook user profiles being sold on the Dark Web.
Looking to verify the records and add them to the firm’s breach notification service, the researchers bought it … for the grand total of £500.
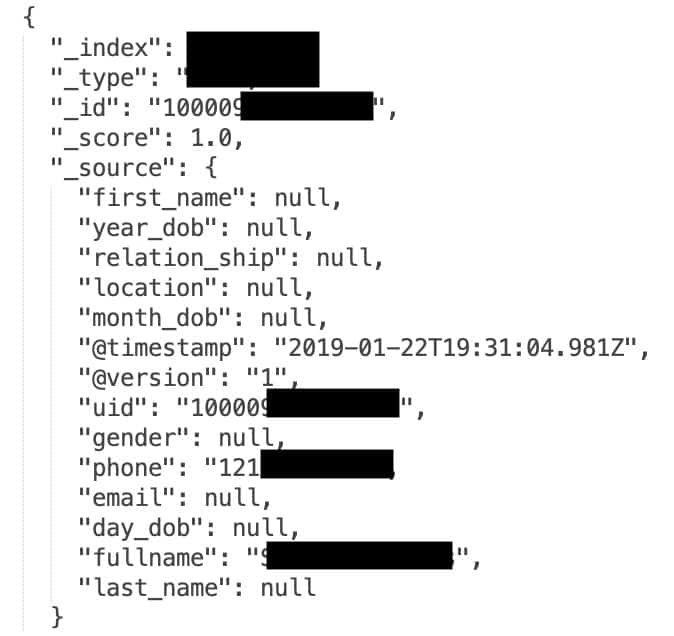
That works out to USD $540 — or about 0.0002 cents — per record. The records held Facebook users’ IDs, which are unique, public numbers associated with specific accounts that can be used to figure out an account’s username and other profile info. The records also included full names, email addresses, phone numbers, timestamps for last connection, relationship status and age.
Fortunately, there were no passwords exposed, but the breach still forms a perfect tool kit for an email or text phishing campaign that looks like it’s coming from Facebook itself. If enough users get fooled into clicking on spearphishers’ rigged links, it could lead to the exposure of even more, and more valuable, data.
How did the data get leaked? In a blog post, Cyble said that it doesn’t know, but its researchers suspect that the records could have either come from a leak in Facebook’s developer API or from scraping: the automatic sucking up of publicly available data (like the kind people often publicly post on Facebook and other social networks).
It keeps popping up
The story doesn’t stop there, however. In fact, it doesn’t begin there, either. It turns out that this same database had been posted before; spotted by security researcher Bob Diachenko; taken down by the ISP hosting the page; reappeared, fattened up with another 42 million records in an Elasticsearch cluster on a second server; and then been destroyed by unknown actor(s) who replaced personal info with dummy data and swapped in database names labelled with this advice: “please_secure_your_servers”.
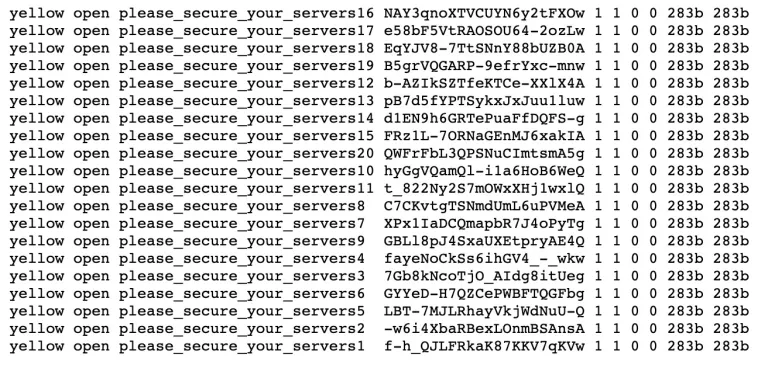
Diachenko partnered with the tech comparison site Comparitech on this work last month. Comparitech said that the database was exposed for nearly two weeks, available online with no password protection, before it was taken down.
The timeline
This is what happened when, Comparitech says:
- 4 December 2019: Database first indexed by search engines.
- 12 December 2019: The data was posted as a download on a hacker forum.
- 14 December 2019: Diachenko discovered the database and immediately sent an abuse report to the ISP managing the IP address of the server.
- 19 December 2019: Access to the database was removed.
- 2 March 2020: A second server containing identical records plus an additional 42 million was indexed by search engine BinaryEdge.
- 4 March 2020: Diachenko discovered the second server and alerted the hosting provider.
- 4 March 2020: The server was attacked and destroyed by unknown actors.
The initial breach exposed 267,140,436 records of what were mostly Facebook users in the US. Diachenko said that all of the records seemed to be valid. The same 267m records were exposed on the second server in March 2020, but this time, the exposure included an additional 42 million records, hosted on a US Elasticsearch server.
Comparitech said that 25 million of the new records contained similar information: Facebook IDs, phone numbers, and usernames. But 16.8 million of the new records had even more, including gender, email address, birth date and other personal data.
How did they get this data?
Both Cyble researchers and Diachenko aren’t sure how the breach happened, but both suggest that it could have been a hole in Facebook’s third-party developer API that existed before the platform restricted access to phone numbers. … or which lets crooks get at our user IDs and phone numbers even after Facebook restricted that access in the API.
Both Cyble and Diachenko say that alternatively, the records might have been harvested by scraping, which is a good reason why you might want to rethink how much data you’re publicly sharing on Facebook. In other words …
Stop exposing yourself!
The less PII you spread around, the less ammunition you give scammers to lure you into clicking on something dangerous in email or SMS text, or into telling them more than you should on the phone. The more scammers know about you, the more convincing they sound. All too often, the thinking of a would-be victim goes like this: “Hey, they know my birthdate and/or phone number and/or home address and/or fill in the blank. They must be legit!”
Be careful of unsolicited emails and texts — they might be phishing attempts. Here’s how to limit how much these con artists can glean about you from Facebook:
- In Facebook, go to Settings & privacy.
- Select See more privacy settings
- Set all relevant fields to either Friends or Only me.
- Set “Do you want search engines outside of Facebook to link to your profile?” to No.
There were no passwords involved in this breach, but it’s still a good opportunity to ensure you have a strong password on Facebook, and that you’re not reusing it (or any other passwords) on any other site.
This breach has already given attackers one piece of the authentication puzzle they need to hijack your accounts: namely, it exposed Facebook users’ email addresses. Once they know the email you use on Facebook, they can use it to search through lists of breaches that have included passwords. Then, they’ll plug login name/password combinations into other sites to see where else you’ve (re)-used those credentials. … All of which adds up to it being a truly bad idea to use a password twice.
Finally, if you’re not already securing your Facebook account with two-factor authentication (2FA), now is a good time to turn that on. It will keep your account from being hijacked if your credentials do get hacked, via this or other breaches. Even if attackers get your username and password, 2FA can prevent them from taking over your accounts. In Facebook, you can turn on 2FA by going to Settings > Security and login.
Latest Naked Security podcast
LISTEN NOW
Click-and-drag on the soundwaves below to skip to any point in the podcast. You can also listen directly on Soundcloud.
Spryte
They always ask… I always decline.
As for 2FA… that would mean I would have to buy a mobile phone, then add a monthly fee for service.
There has got to be a better way.
DownyZ
You really don’t have to use a phone as a second way to get in. You can choose 3-5 friends that you know and can call and then say, “Hey facebook locked me out, can you give me a code?” I don’t like the phone thing either. Quite a few years back, I put my phone number in for them to verify me, and a friend told me my phone number was listed on my account. I freaked and got it off, but it was an old number, so I don’t worry about it now, but the thing is, they said no one would use the number but them for verification. No more numbers for them. In fact, I have been playing with the idea of just getting a new email as well. Over the holidays I actually had over 600 junk emails in one day! Yep. Twenty years is too long to have the same email!
Raffles
I deactivated my facebook account about 2 years ago. Don’t miss it at all. What is annoying is that they don’t have a “wipe all your data” feature and I don’t really have the time to manually delete all my stuff. If anyone knows if there is a way to delete one’s data in bulk please let me know.
Paul Ducklin
According to Facebook, if you *delete* your account rather than deactivate it, then (I am parahprasing here):
* Your data goes offline immediately so no one can see it.
* For 30 days it sits there inaccessible but not removed, in case you change your mind and decide to keep your account after all.
* After 30 days, removal of your data across Facebook’s massive distributed storage network starts.
After 90 days, Facebook invites you to assume that it’s all been wiped, except that “[c]opies of your information may remain after the 90 days in backup storage that we use to recover in the event of a disaster, software error, or other data loss event. We may also keep your information for things like legal issues, terms violations, or harm prevention efforts.”
Whether you think that counts as “wiped”, it’s sort of what you are after – and that’s because deactivating your account is explicitly defined as suspending the account without removing the data, which is why you didn’t get any messages about your data being removed permanently. (It wasn’t.)
I got this info here:
https://www.facebook.com/help/224562897555674
Raffles
Thanks Paul
Hilarious
Easy solutions for anyone: Don’t give away any real info, if you have to, then offer fake name, address, etc.
Because your real friends should have your info, not some stranger like zuzkerberg, that’ll inevitably sell, and leak your info accidentally. Who cares what the reason, or excuse is.
No one needs to know you, unless you want them to.