App developers have, for years, embedded ad-code into their apps as a way to help defray the costs of development, but some developers simply use their apps as a borderline-abusive platform solely to launch ads on mobile devices.
SophosLabs recently discovered 15 apps on Google’s Play Market that engage in such practices; They generate frequent, large, intrusive ads and literally hide their app icons in the launcher in order to make it difficult for you to find and remove them. Several of them go a step further by disguising themselves in the phone’s App settings page.
According to the Play Market pages for these apps, more than 1.3 million devices worldwide have installed at least one of them. If history is any indication, there are likely many more waiting to be found.
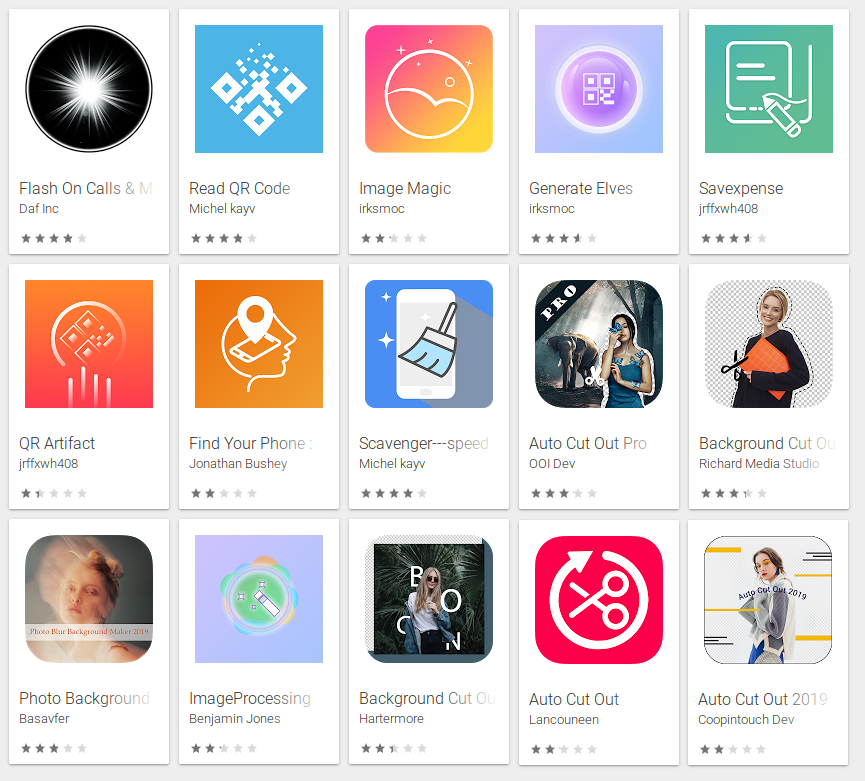
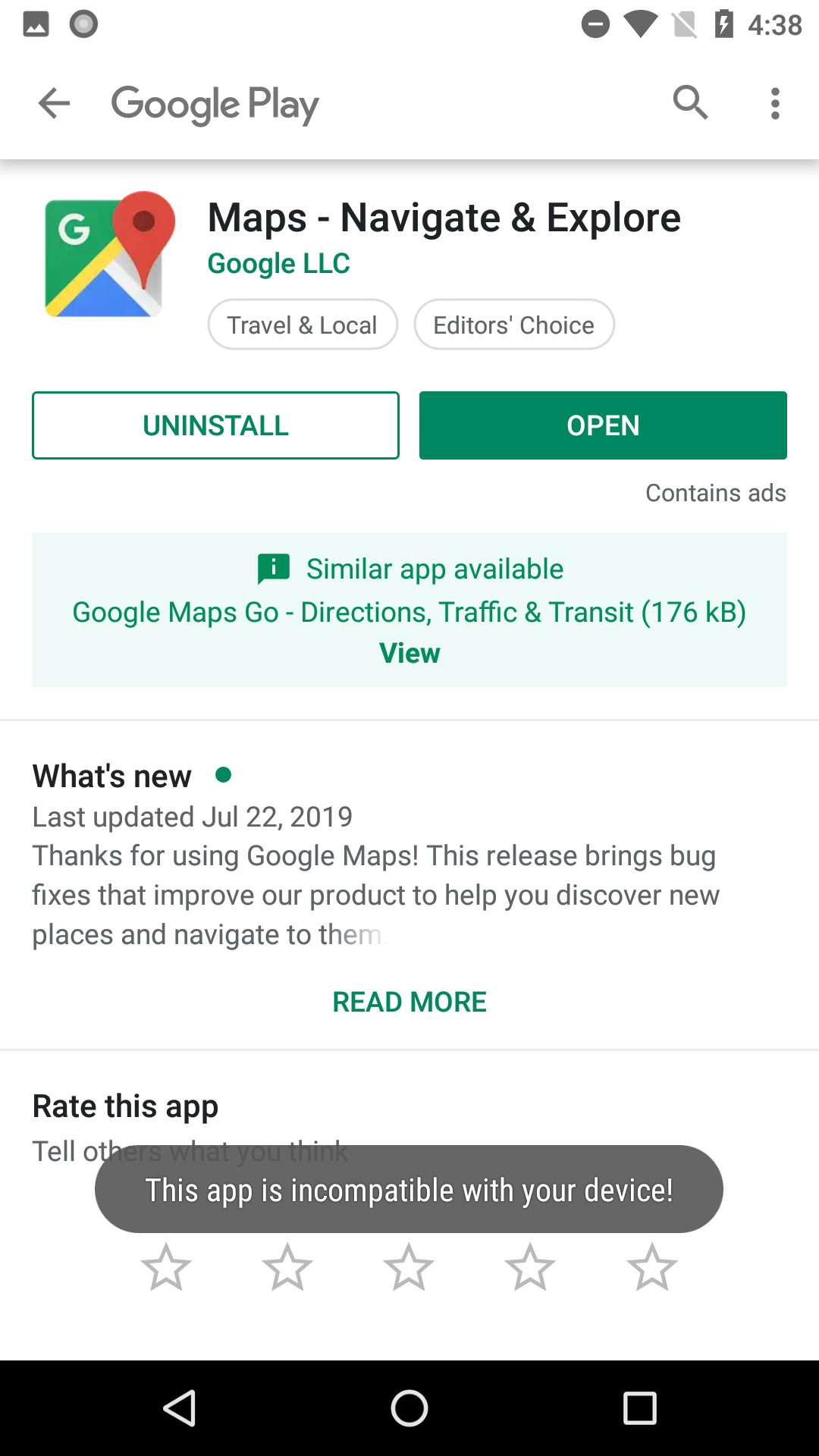
For example, the app free.calls.messages (Flash On Calls & Messages – aka Free Calls & Messages – shown below) engages in some clever trickery to prevent users from uninstalling the app.
When first launched, the app displays a message that says “This app is incompatible with your device!” You might think that the app has crashed, because, after this “crash,” the app opens the Play Store and navigates to the page for Google Maps, to mislead you into thinking that the ubiquitous Maps app is the cause of the problem. It is not. This is a ruse.
The app then hides its own icon so it doesn’t show up in the launcher’s app tray. Others in the list hide their icon, too: Some do this on the first launch, while others simply wait for a while after you install the app.
Playing dirty
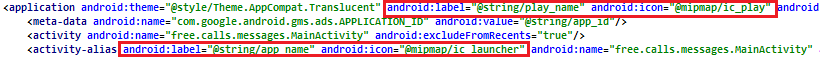
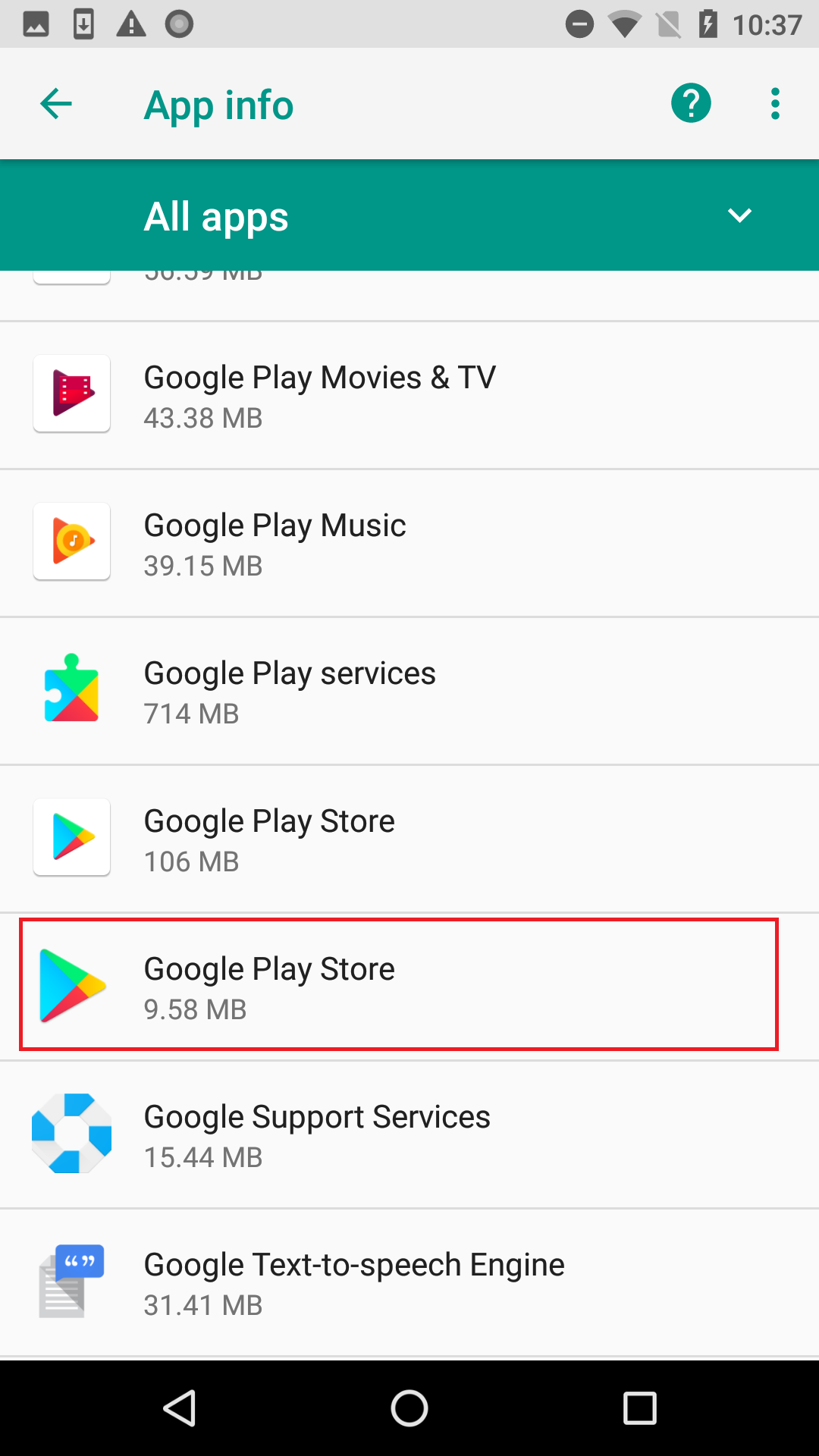
SophosLabs has also observed these apps pulling a different dirty trick: using one name and icon for the application (which is visible in the phone’s Apps settings page), and a different name and icon for the Main Activity (the running app window).
Nine out of the batch of 15 apps used deceptive application icons and names, most of which appeared to have been chosen because they might plausibly resemble an innocuous system app. (The app icon is still visible in the phone’s “gear” Settings menu, under Apps.)
By hiding their launcher icon, and using an application icon and name that resembles a system app, these apps make a convincing case to a casual observer that there’s nothing unusual installed on the phone.
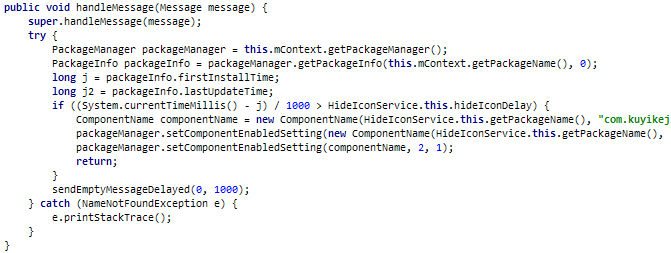
Other apps make use of a library, called koolib, that installs a service to hide the icon after a predetermined time after the installation of the app. Not kool, app.
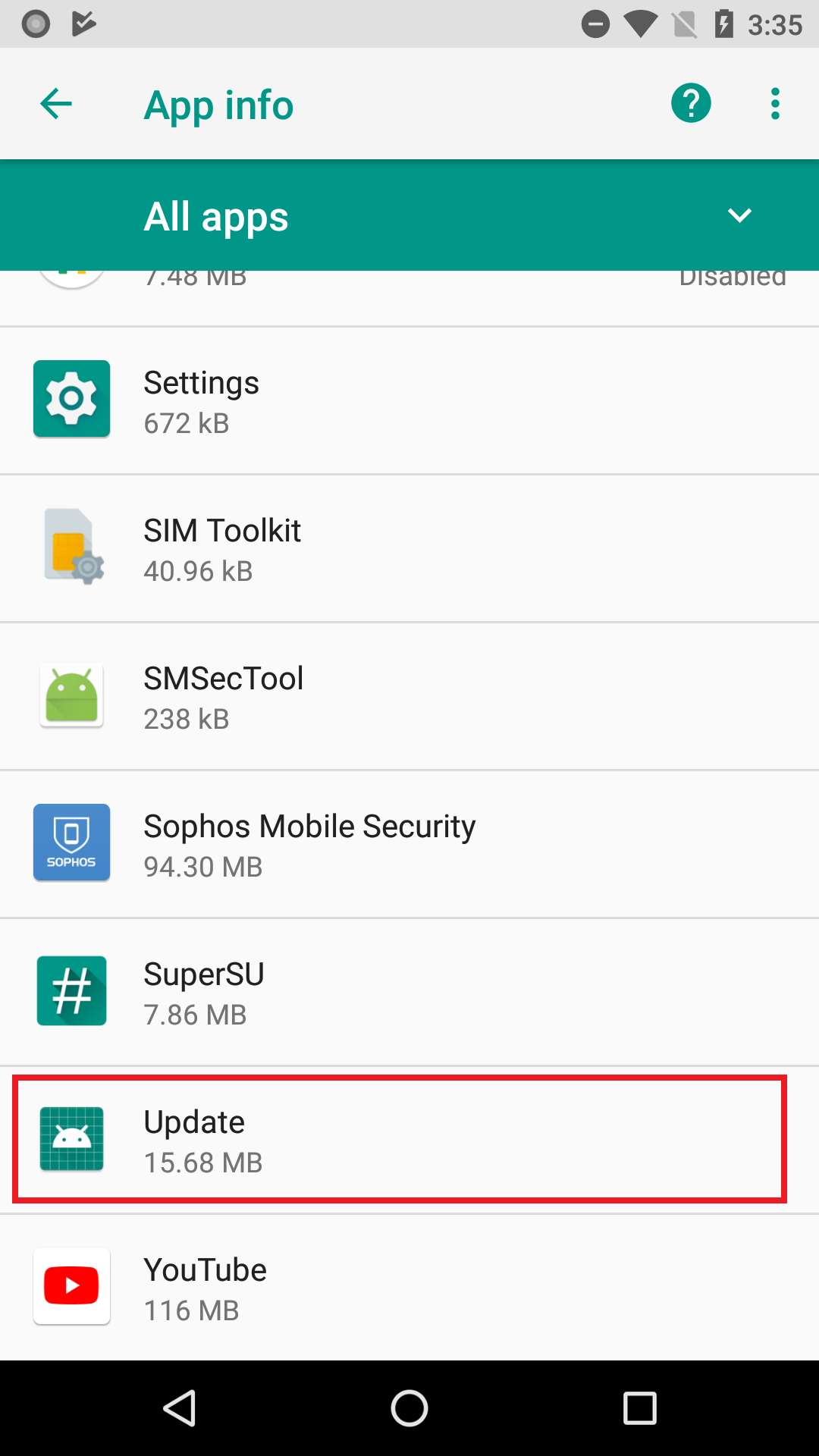
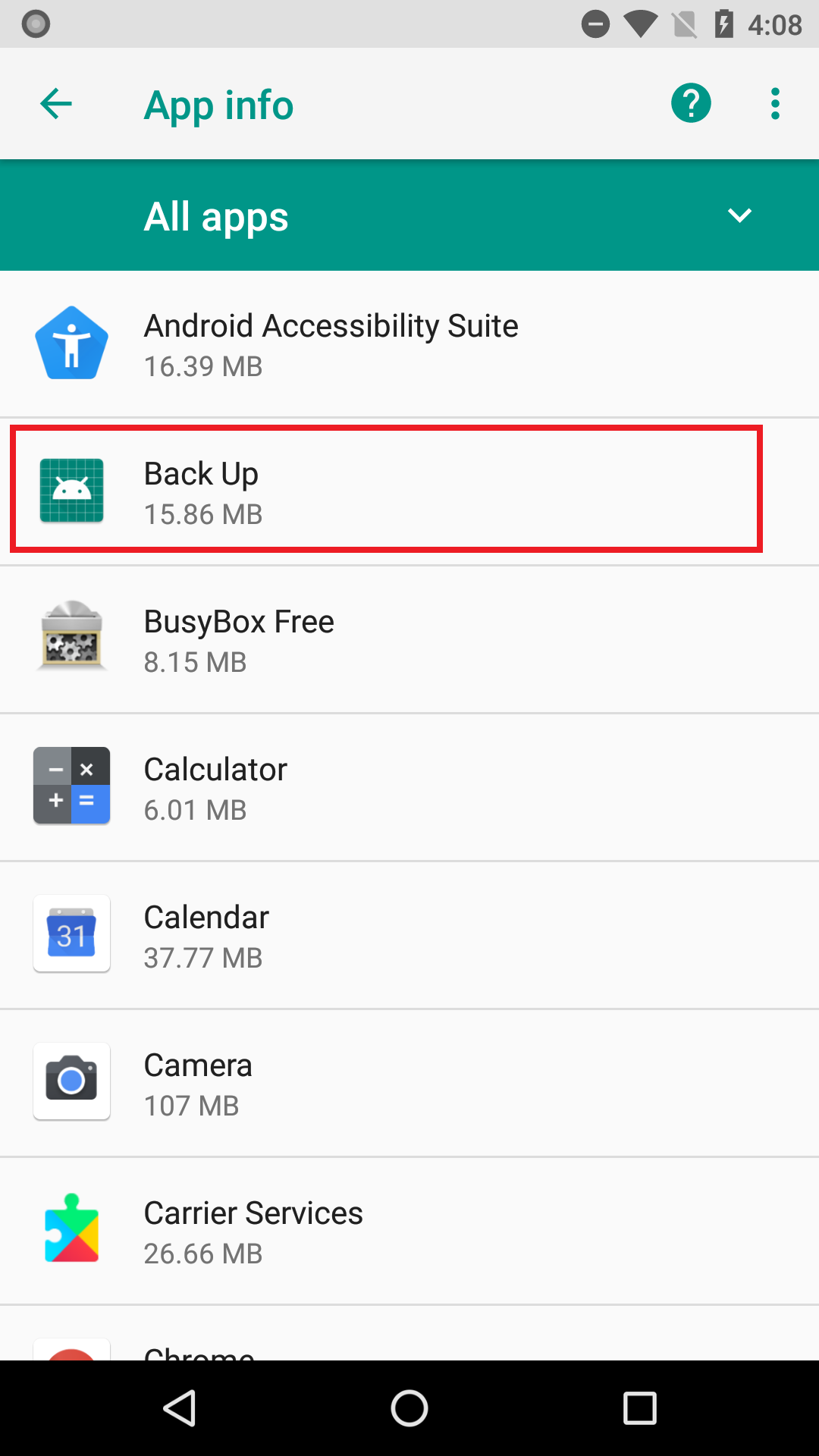
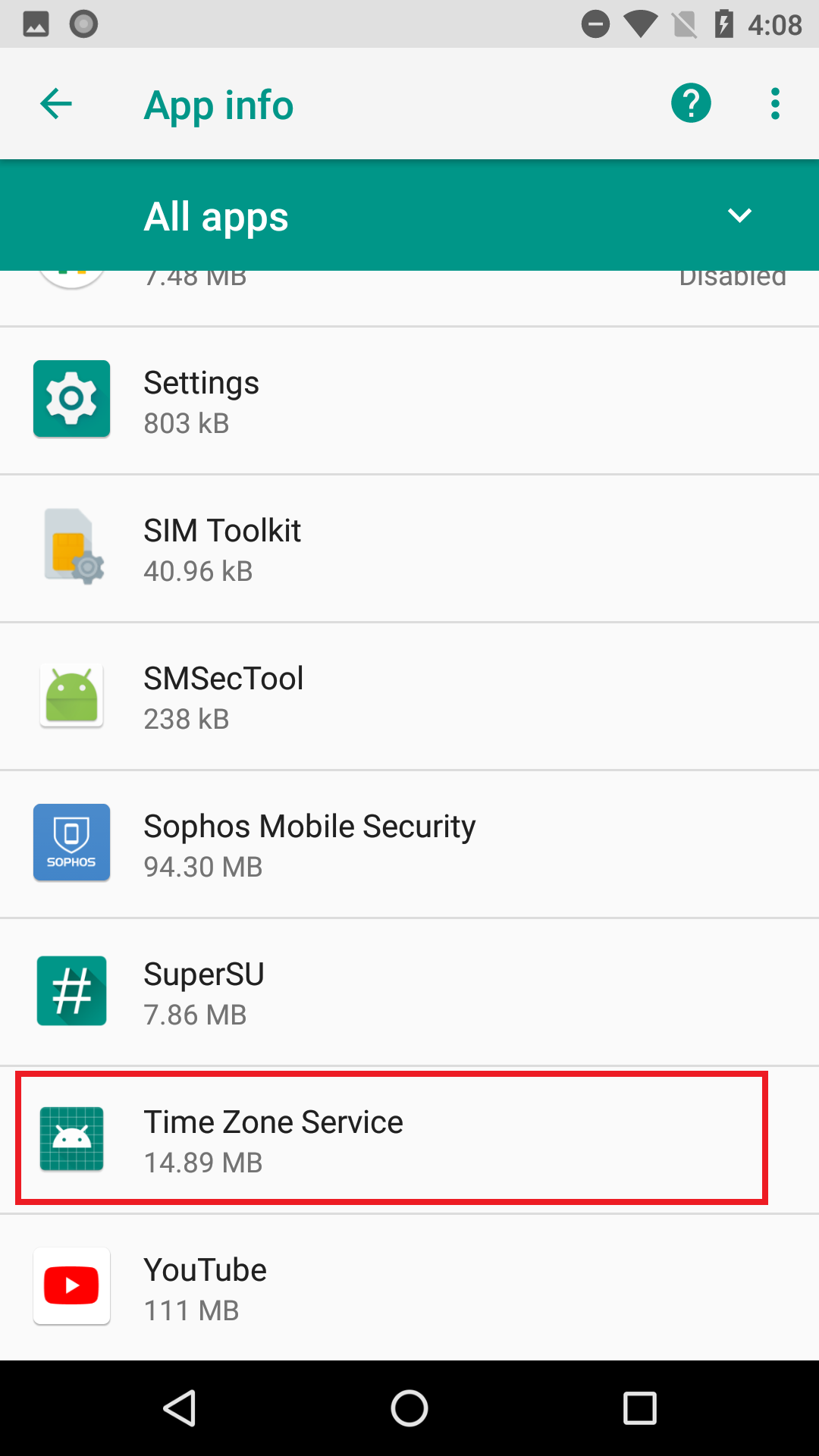
Most of these apps were presented to the user as one kind of utility app or another. QR code readers, image editors, backup utilities, a phone finder, and most ironically. a utility ostensibly to scrub your phone of private data. The apps further disguised themselves using a name representing a harmless app, such as Google Play Store, Update, Back Up, or Time Zone Service. These names appear only in the phone’s settings.
|
|
|
|
|
All of these apps appeared during this calendar year. The oldest one among these, free.calls.messages, was published in January; Two months after it appeared, it had more than a million installs. Although these apps were uploaded to the market by different publisher accounts, many shared similar code structure, UI, package names, and behavior — too many for it to be considered a coincidence.
For example, the app com.cc.image.editor contained a reference to a different app, com.bb.image.editor, within its code. The two apps, despite their similar names, were published by completely different entities. This suggests to us that the former might have been derived from the latter, but we can’t definitively say that the same author(s) developed both apps.
Users not fond of adware
Most of these apps had negative reviews from users, many of which had complained about these apps not being able to run, app icon disappearing from the launcher, and of course the aggressive ads.
 Android adware took a dark turn with the use of these persistence tricks. By leveraging increasingly innovative techniques to stay resident on the phone, apps like these can quickly infect mass numbers of victims within a few weeks of their release. Users should pay close attention to user reviews before installing apps from Google Play (and don’t be the first person to try out a brand new app).
Android adware took a dark turn with the use of these persistence tricks. By leveraging increasingly innovative techniques to stay resident on the phone, apps like these can quickly infect mass numbers of victims within a few weeks of their release. Users should pay close attention to user reviews before installing apps from Google Play (and don’t be the first person to try out a brand new app).
SophosLabs notified Google about these apps in July and, as far as we know, they have been taken down. These apps are detected by Sophos Mobile Security as Andr/Hiddad-AB and Andr/Hiddad-AC.
IOCs
| Package Name | Installs | Published |
| free.calls.messages | 1,000,000+ | Jan 2019 |
| com.a.bluescanner | 10,000+ | May 2019 |
| com.bb.image.editor | 10,000+ | May 2019 |
| com.cc.image.editor | 100,000+ | June 2019 |
| com.d.bluemagentascanner | 10,000+ | June 2019 |
| com.doo.keeping | 1,000+ | May 2019 |
| com.e.orangeredscanner | 10,000+ | July 2019 |
| com.hz.audio | 10,000+ | June 2019 |
| cos.mos.comprehensive | 10,000+ | April 2019 |
| com.garbege.background.cutout | 10,000+ | July 2019 |
| com.hanroom.cutbackground | 50,000+ | July 2019 |
| com.jiajia.autocut.photo | 100,000+ | July 2019 |
| com.jiakebull.picture.background | 50,000+ | July 2019 |
| com.fruit.autocut.photo | 10,000+ | July 2019 |
| com.huankuai.autocut.picture | 10,000+ | July 2019 |




Kathryn Ruth
Thank you for helping protect unwary and uneducated users.
Mary
So how do we find these apps and delete them?
Sheila
Hi, so it doesn’t look like you really explain how to find these apps so we can get rid of them, could you please help with this?
Zirimenya Michael
Thanks
j
this article learned from the same folks it reports on – where’s the beef ( how to search and destroy these 15 )
Anonymous
Where do we go
Marcelo
Gracias por el aporte ¿Existe alguna app que escanee y elimine estos maliciosos? Gracias
dhunter
Any technology that connects to the internet is subject to malware. Anyone who chooses to use this technology needs to take the time to educate themselves on how the devices they use work and to understand the risks of using them. Computers, phones, routers, IP cameras, baby monitors, smarthome devices etc.
While I can understand that even the best of us can on rare occasions be tricked into installing bad software, It boggles the mind that there are those who do not know how to uninstall (with extreme prejudice) these malicious programs and otherwise clean their devices. We get stung by these software developers because there are sufficient incompetent device users to make the effort worthwhile.
50% of the blame rests squarely with the malware creators. The other 50% of the blame rests with the users who have no clue what they are doing and what they are giving up when they click .
Ryan O'Dell
” 50% of the blame rests squarely with the malware creators. The other 50% of the blame rests with the users who have no clue what they are doing “…
Really??
So you are basically saying that every user of a smartphone should be as clever as the devious minds that put together these terrible apps and that there’s no place for a security software/company or any need for those companies that manage market places that serve these terrible apps, to take any precautions in reviewing, blocking and preventing such apps and developers?
You’re saying the risk is entirely on the consumer.
Personally, I disagree, I expect everybody involved to take responsibility, some more than others.
I would expect the companies that provide the market places to serve these apps, to take prevention methods and block and remove developers/apps that pose a security risk.
I would expect smartphone manufacturers to take necessary security measures to help protect the devices.
And I would expect authorities to work with these companies and individuals to take action against the developers or companies that cause security mayhem.
50/50 is not very realistic.
Jennifer Poullion
I have been finding out people are shopping w my personal info. Hacking into my accounts and putting things together in my phone that I NEVER WOULD OR WANTED. Please tell me or call me to help with this. Jennifer@ 313- 980- 7729. Thank you
Pankaj Kohli
You should change the passwords of your accounts (from a secure device or computer). Many services provide an option to use second factor authentication using SMS or a code generator app on your phone, use it if it is available. Do not install apps from links from untrusted sources such as in emails or SMS. Also, ensure your phone has mobile AV such as Intercept X to defend against malware.
Dr Sebastian Armstrong
This is great nfo, all ways love reading lists like this, many thanks my friend. 🐍💨
Ryan O'Dell
For those that are wondering how to detect and remove these terrible apps, it was mentioned towards the end of the article and a little obvious by this web page sponsor 😁
” These apps are detected by Sophos Mobile Security ”
Stay secure, install antivirus protection.
A note to the author, please test the web page in mobile browsers, I couldn’t see all screen shots (those that go off to the right) or read all text associated.
Anonymous
I thought it was my phone, lol but I had the same problem
a1smith
It’s VERY bad that you help users to identify malware with no link to any articles showing how to remove it. All it would do is add a few extra words to the article, and you’d get lots of hits on the linked article (written that way to show that you will get an advantage because you don’t seem to care about giving real help to users, just cause worry or panic).
How hard is it for you to offer practical advice rather than panic?
Leo Simons
This is amazing,my school use sophos and you have now protected me I kept getting these pop ups and now I have finally known the truth
Jamie Costello
Guys, I love your blog it’s amazing.
Google Play really need to do better, I know it’s always a balance between profit and security but they have the resources to do so much more.
Well spotted, keep up the excellent work!
Take care
Jamie
Milton Macaulay
Pankaj,
Thanks for the info. What an insight. A platform to build on. A simple search on Google would take one further. Cannot understand those who wish to be spoon-fed.
Kazem
It’s very interesting. Your explains are greats. It improved my vision.Thanks.