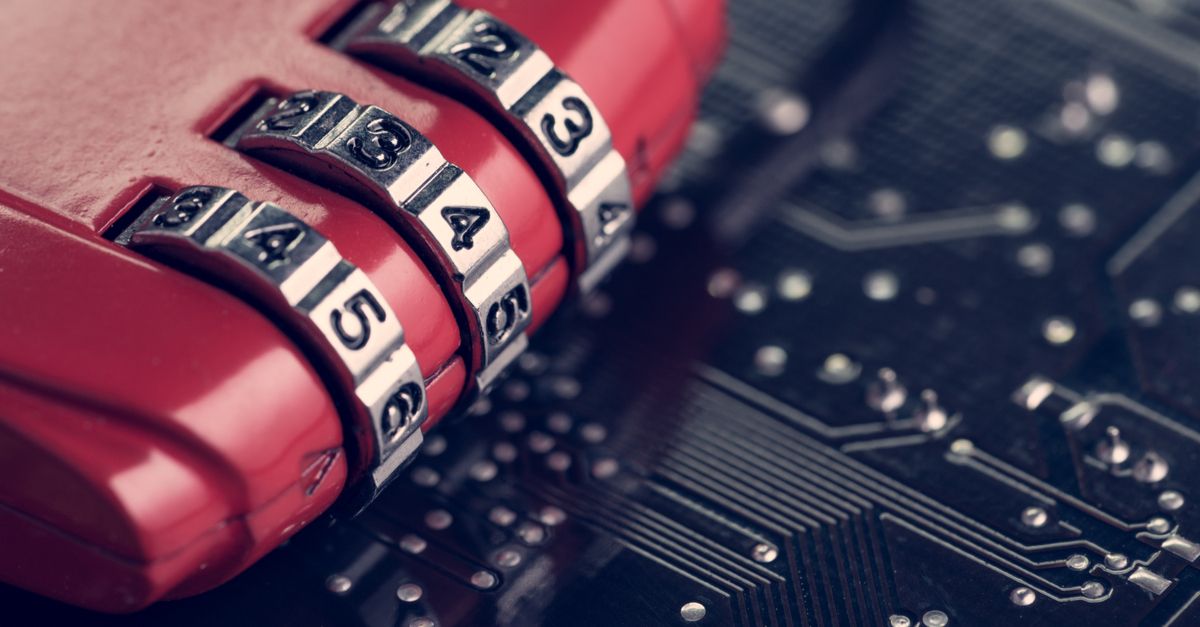
An alliance of national intelligence partners known as the Five Eyes – Australia, Canada, New Zealand, the UK and the US – is demanding encryption backdoors in apps such as Facebook’s WhatsApp.
As reported by the Telegraph on Wednesday, the UK’s new Home Secretary, Priti Patel, accused Facebook of helping out child abusers, drug traffickers and terrorists plotting attacks with its plans to help them hide messages behind the end-to-end encryption it plans to spread across all of its messaging services.
In March, Facebook CEO Mark Zuckerberg announced what he framed as a major, more privacy-focused strategy shift, with end-to-end encryption being a key component. He said at the time that the company would develop a highly secure private communications platform based on Facebook’s Messenger, Instagram, and WhatsApp services.
The prospect is unanimously seen as bad news by the Five Eyes nations. Patel’s warnings come on the heels of a two-day Five Eyes meeting she hosted in London along with Geoffrey Cox, the UK’s Attorney General. In attendance were security and law enforcement officials from the Five Eyes nations who said that they were worried about high-tech companies moving to “deliberately design their systems in a way that precludes any form of access to content, even in cases of the most serious crimes.”
In a communique that reportedly came out of the meeting, the Five Eyes nations called for backdoors:
Tech companies should include mechanisms in the design of their encrypted products and services whereby governments, acting with appropriate legal authority, can obtain access to data in a readable and usable format.
In September 2018, Five Eyes governments had called on their governments to demand that tech giants build encryption backdoors – by force, if necessary.
From a memo that the Australian government issued on behalf of the pact at the time:
Should governments continue to encounter impediments to lawful access to information necessary to aid the protection of the citizens of our countries, we may pursue technological, enforcement, legislative or other measures to achieve lawful access solutions.
Reuters spoke with a former senior European security official who said that the Five Eyes is using “very general” language, at best, in its demand for government access in telecoms systems.
He or she noted that there’s been a proposal floated recently by some British officials that wouldn’t drill a hole through encryption, per se. Rather, it would entail the equivalent of wiretapping encrypted systems, as in, secretly slipping a law enforcement agent into encrypted calls so they could tap a device at one end of the conversation after a message is decrypted.
The ex-official:
It doesn’t mean weakening encryption, just going around it.
Facebook has pointed out that it just doesn’t work that way. End-to-end encryption means only the sender and recipient can read encrypted messages. That excludes everybody else, including Facebook itself.
This option to insert a government body into encrypted conversations, which was proposed by the UK spy agency GCHQ, is known as the Ghost Protocol.
In an open letter to GCHQ published in May, a coalition of tech companies, privacy experts and human rights groups claimed that letting governments listen in “would undermine the authentication process …introduce potential unintentional vulnerabilities, [and] increase risks that communications systems could be abused or misused.”
While the Five Eyes nations may want to insert their agents into encrypted messaging, they most certainly want to keep that power to themselves. The Telegraph reports that the Five Eyes nations agreed that Huawei – a company that’s worried governments for years – should be kept out of the 5G phone network unless it can be guaranteed that the Chinese government wouldn’t get unauthorized access.
Experts say that governments’ reinvigorated anti-encryption push appears to be – no surprise here – directed not only at Facebook, but at Apple: the company that famously dug in its heels when the FBI was trying to decrypt the phone of the San Bernardino, California mass shooter in 2015.
Ben Wizner, an expert in national security law with the American Civil Liberties Union, echoed what backdoor opponents (including Sophos) have repeatedly pointed out: putting a backdoor in encryption means that you’ve broken it. Once there’s a hole, it will be found and exploited, and not necessarily by nations that (purportedly) have respect for innocent people’s privacy.
If the US and other nations get access to private messages, Wizner told Reuters, that means that adversarial nations, such as Russia, could demand that they get the same access.
This fight isn’t going away anytime soon. Last week, US Attorney William Barr – who attended the Five Eyes meeting – said that the proliferation of “warrant-proof encryption” was making it easier for criminals to evade detection.
The response from long-time privacy advocate and vocal opponent of government efforts to weaken encryption, Senator Ron Wyden, from the floor of the Senate:
[Barr has presented an] outrageous, wrongheaded and dangerous proposal. [The AG has] raised a tired, debunked plan to blow a hole in one of the most important security features protecting Americans’ digital lives.
Yea… What he said.
Sophos has always, and will continue, to defend end-to-end encryption. Paul Ducklin has explained why in this article.
SOPHOS STATEMENT ON ENCRYPTION
Our ethos and development practices prohibit “backdoors” or any other means of compromising the strength of our products for any purpose, and we vigorously oppose any law that would compel Sophos (or any other technology supplier) to weaken the security of our products.
Citizen 901567852
I know that
The prospect is unanimously seen as bad news by the Five Eyes nations.
Is “technically accurate” as despite not having a popular majority, our (UK) government (even its newly rehabilitated Home Secretary) can “speak for the nation”, but do you lose anything by saying:
The prospect is unanimously seen as bad news by the Five Eyes governments.
Too many people seem to want to “go with the flow”, “if it is reported that the nation has said something, it is bad form, even undemocratic, to voice opposition or even dissent”. Such is the way governments get to claim “popular support” for weak encryption and more surveillance.
BTW Does the SOPHOS STATEMENT ON ENCRYPTION need a canary?
Mahhn
They will end up making encryption illegal, then everyone that uses it will be a criminal. Time to give up computers, take money out of the banks (since they will be insecure) and quit jobs that hold employees PII. Way to drive us back to the stone ages politicians…. Dropping anti-tech bombs on the world. Just who are they working for? (answer- themselves)
If they though breaches were common now, just watch how the internet, banking systems and governments will crumble without functional security.
Ian
Do these people really not understand that criminals will just use different technology that the Five Eyes nations don’t have control over? Or that if the NSA/OPM/every business can’t even keep their data secure that there is no way they will be able to keep their proposed backdoors secure? It’s baffling to me that we are still having this debate.
David Pottage
Most criminals are fairly stupid, and will use whatever messaging app is on their phone already. These days, and in most countries, that will be SMS, WhatsApp or Facebook messenger. If the ordinary police can get the message content, then they can be more successful in suppressing ordinary gangsters who control terotory to traffic drugs and run protection rackets. (Though experience has shown that terrorist foot soldiers are often just as dumb as young gangsters).
Yes, there will be a minority of terrorists and gangsters with the technical savvy to use something different if the mainstream options share their traffic content with law enforcement, but they will always be rare, especially among ordinary criminals who won’t be motivated to swtch to a “holy” messaging app.
Raylund
I could foresee. If there’s encryption backdoors in the Five Eyes nations, there will be one day that these backdoors were hacked and all people are under the “hacker(s)” surveillance.
Paul Ducklin
The ETERNALBLUE exploit (as used, for instance, by WannaCry) was IIRC stolen from the NSA. They must have been ropeable (a fantastic Aussie word meaning ‘so annoyed that you need restraining to help dissuade or inhibit you from headbutting the wall’) to lose it, because it was quickly patched and thus no good to them any more. But perhaps not as ropeable as the rest of the world, because the exploit was now ready and available to everyone to use on anyone, and someone used it on a lot of us.
Typhoonandrew
Ropeable because they lost it, not because it’s the wrong headed thing to do; bloody awful lack of foresight.
Thanks Paul, seeing that slang gave me a laugh none the less.
Spryte
Back in the last millennium the Honourable Pierre Elliott Trudeau, the father of now Canadian Prime Minister, Justin Trudeau, told Parliament that “The police [government] had no business in the bedrooms of Canadians” and was a great proponent of privacy and basic human rights.
Today young Justin and his peers in the five eyes do not seem to get the concepts of privacy, personal space or client confidentiality (where it applies).
Matt Parkes
Talk about pot calling the kettle black, so the 5 eyes want encryption to spy on us all just in case they come across criminals making plans yet when it comes to Huawie they don’t want the Chinese Government doing the same. Bunch of uneducated people running these governments when it comes to privacy, security and the technology that supports it, sad, sad, sad.
Tony King
This is an element of the privacy debate that I just don’t understand. How is Huawei supposedly being subservient to the Chinese government when it comes to data security any different from what the Five Eyes governments are demanding from tech companies in their own countries? Or what the Australian government has already legislated in relation to “technical assistance”?
Wilderness
Tony, under Chinese law, the government and military can order any private enterprise within their borders to do anything, include assist in espionage or attacks.
Tony King
Doesn’t seem very different to the Australian law which requires tech companies to assist with access to systems or data including by developing and inserting weaknesses (aka back doors) in products.
Adam
Which is no different from Australian law, as Tony mentioned in regard to Australia’s “technical assistance” legislation.
Wilderness
The difference is the willingness to abuse such laws.
Anonymous
Willingness is an emotional state which changes with circumstance.