Remember GandCrab?
It was a well-known strain of ransomware that was sold as a ‘service’ on the cyberunderground.
The idea of CaaS, or crimeware-as-a-service, is borrowed from the outsourcing and cloud computing models that regular businesses use.
These days, for example, if you want to publish your own videos, you don’t have to learn about video compression, colour gamut, pixel formats, transcoding, bitrates, how to run a live streaming server, or any of that stuff…
…you just press [Record] on your phone, capture your video footage and then click a button to share the video with anyone you like via a whole range of free video hosting networks such as YouTube.
CaaS works in a similar fashion – if you want to have a go at making money out of ransomware, for example, and you know the right places to go in the cyberunderground, you can get someone else to take care of the technical side in return for a cut of the takings – no upfront fees.
Instead of learning about malware, teaching yourself how encryption works, writing ransomware code, running an anonymous webserver on Tor to collect the loot, distributing decryption keys, and so on…
…all you have to do is sign up, download your malware samples as needed, and victimise individual and organisations with your ready-made ransomware.
The crooks behind the service collect the ransoms, distribute the decryptors, even offer online ‘tech support’ to victims to make sure they know how to buy bitcoins, how to make payments, what to do after they’ve paid, and so on.
You take the front-line risk of getting caught red-handed using the malware; the crooks run the back-end systems in comparative anonymity and take a cut of the proceeds in return.
Notorious ransomware-as-a-service (RaaS) platforms have gone by names such as Satan, Philadephia and RaaSBerry.
And, until this year, there was GandCrab, a crimeware group that claimed to have shut up shop at the start of June 2019:
All the good things come to an end… Earnings with us per week averaged $2,500,000. We personally earned more than 150 million dollars per year. […] We are leaving for a well-deserved retirement.
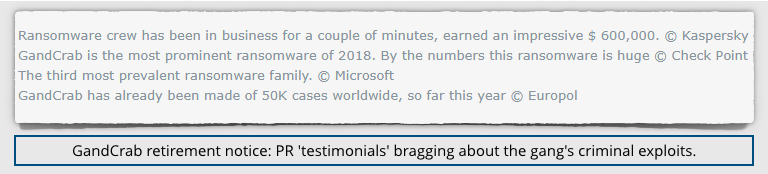
The crooks even finished their announcement with a series of ‘testimonials’, publishing quotes from organisations including Microsoft and Europol to brag to the world just how criminally disruptive they had been:
However, according to cybersecurity journo-sleuth Brian Krebs, the gang may well have shifted sideways within, rather than moved out of, the RaaS game.
Krebs argued in a recent article that similarities between a recent ransomware strain that dubs itself Sodinokibi suggest that the GandCrab crew never really went away.
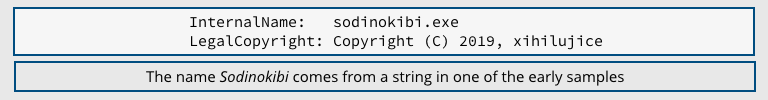
Sodinokibi is also known more catchily as REvil, and as Sodin for short. Sophos products block the samples mentioned in this article as Mal/Kryptik-DJ, if you want to look through your logs for detections.
Krebs describes how an underground forum operator known only as Unknown announced a new ransomware project, months before the GandCrab “goodbye’ message.
Unknown was seeking a small number of affiliates (the legitimate-sounding name callously given by crooks to their online partners-in-crime) to join a low-key malware distribution network that aimed to “go under the radar”.
Affiliates would pocket 60% of the ransom revenue for their first three payments, said Unknown, followed by 70% thereafter.
The core crooks keep 30% for running everything behind the scenes – a ‘royalty’ fee that is eerily copied from mainstream cloud services such as iTunes.
Sodinokibi samples have already appeared in real-world attacks – Cisco Talos researchers documented a case they investigated earlier this year where the attackers used an web server exploit against the Oracle WebLogic product to initiate their attack.
The malware was deliberately implanted by the attackers after they’d broken into a network rather than mass-mailed as attachments or spammed out as download links.
Many modern ransomware attackers follow this approach – sadly, the theory seems to be that if you attack one organisation at a time and encrypt some, most or all of their network in one go, then it’s easier to to blackmail your victims that if you try to squeeze money out of hundreds or thousands of scattered, individual victims, each with one infected device.
It’s also easier to “go under the radar”, to borrow Unknown’s words, if you deploy your malware samples one-at-a-time, playing your ransomware cards close to your chest by targeting just one organisation with each sample.
What an attack looks like
Once the Sodinokibi ransomware detonates, you’ll see a README file on your Windows desktop, telling you what to do next:

The pay page itself is surprisingly professional looking, with the clean, clear appearance of many modern corporate websites, but with a very different sort of sales pitch.
The price when we checked was $2500, converted to Bitcoin at the current rate, but we were warned it would double to the equivalent of $5000 after four days:

What to do?
Sadly, ransomware attacks show little sign of abating, and whether the Sodinokibi crew are just the GandCrab crooks back for more or a new wave of criminals doesn’t change the defensive strategies you need to take.
So, our usual anti-ransomware advice applies, including the rather obvious reminder that “the only backup you’ll ever regret is the one you didn’t make.”
In short:
- Patch early, patch often. Don’t make it easy for the crooks to get in through the back door.
- Pick proper passwords. Don’t make it easy for the crooks to get in through the front door.
- Use two-factor authentication. Lock the front door, and bolt it too.
- Make regular backups. Ransomware isn’t the only way you can lose your files, so don’t risk keeping only a single copy.
- Keep an off-site backup. Ransomware often tries to find and wipe out any online backups first – so offline backups are your backup’s backup.
- Think before you click. Never open attachments or click through to web links just because an email tells you to.
- Use an up-to-date anti-virus, web filter and exploit blocker. Ransomware that can’t run can’t even read your files, let alone overwrite them.
For more advice, please check out our END OF RANSOMWARE page.

