The ransomware known as GandCrab is, for the moment, the most prolific ransomware in circulation. In many ways, its operation is very similar to other ransomware, but its ransomware-as-a-service business model seems to have propelled it forward.
GandCrab appeared just over a year ago, promoted on public websites but sold exclusively through the dark web. Independent security researcher David Montenegro was the first to come across it. At that time, it was being distributed by the RIG exploit kit, which was being used in a malvertising campaign, leveraging banner ad networks to deliver the malicious code to unsuspecting visitors to public websites.
Since then, the ransomware has developed a large pool of customers, and an unfortunately large pool of victims as well. The authors have kept pace with a team of cryptography experts working for Europol and Bitdefender who have released several decryptor tools, and continue to release updated versions of the malware that bypasses the decryptor features every time a new decryptor hits the street.
The ransomware may owe some of its early success to its unique software licensing scheme, which the creators called Dashboard Essential and has become widely referred to as ransomware-as-a-service. For $100, neophyte ransomware crime lords could build a criminal fiefdom of up to 200 victims in a two month period, working their way up to earning enough to afford more premium-rate services and features.
In essence, the GandCrab creators provide a criminal franchise system.
How do you get it?
Initially delivered via RIG exploit kit, once licensees began using the ransomware, they chose whatever distribution method suited them best. By a month later, malicious spam began to appear with malicious office documents that, when opened, delivered GandCrab to victims.
The malware itself uses a deviously clever fileless approach to execute itself, and encrypt the victim’s files. A maldoc spawns PowerShell code that looks like this example:
This instance of PowerShell is pointed at a file hosted on a reputable, public website, such as Pastebin, but we’ve also seen them pointed at malicious domains. The file contains .Net-based PowerShell code that calls a module named ‘Invoke-GandCrab’ (naturally), which, by this point, is already loaded in the memory of the victim’s machine.
What makes this attack special and unique is its ability to be fileless. To achieve that, the authors leveraged a feature called Reflective PE Injection, made available in a Github code repository named PowerSploit, to inject GandCrab’s malicious binary into PowerShell’s running memory. In Reflective PE Injection, PowerShell is made to load the ransomware directly from memory, and never writes a copy of its PE to disk. This is an effective countermeasure to traditional antivirus software, which would not be able to detect or clean the (conspicuously absent) malicious file.
More recent variants of GandCrab have been spreading by means of known vulnerabilities (including Fallout Exploit Kit, which only recently appeared in the wild), and the rest of the “usual suspects” varieties of Trojans. Like Ryuk and SamSam, some purveyors of GandCrab attacks leveraged JBoss, Oracle Fusion and WebLogic, and Tomcat vulnerabilities to spread onto enterprise networks. The PowerShell scripts are also encoded, though they perform the same function as before; They just not human-readable. Attack traffic targeting Oracle WebLogic on port 7001/tcp is now part of the Internet background radiation. Attackers will never stop actively scanning the internet for this port.
How does it work?
The creators of GandCrab release frequent version updates. These notes refer to version 5.0.5.
The malware checks for a mutex on start. If it finds it, the program quits. In our case, the mutex looked like this:
The malware also halts and does no damage if your computer language settings are configured to any of these specific language IDs.
The malware sends a profile of the hardware, OS, and other information back home
GandCrab uses a lot of lists. It kills the process of some programs in order to correctly encrypt the data files they might have open. It of course has a target list of filetypes to encrypt, and files and paths to whitelist. It deletes the Volume Shadow Copy of the drives, and enumerates all mounted drive letters.
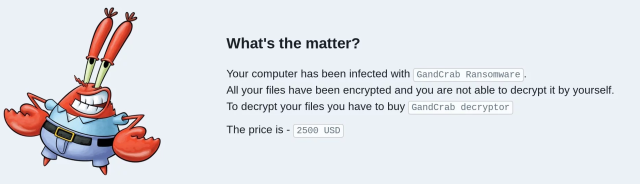
The encryption takes a little time to complete, depending on how full the drive is. Free decryptor tools have been released for some versions of GandCrab, but the authors quickly update to another version, and the decryptor tools stop working. All the ransom notes include a GandCrab key you must provide if you meet their demand for payment.
How much do you have to pay?
The business model for GandCrab gives the franchisee the option of choosing their ransom amount, among other features. Some victims report ransoms as low as $300 but they can run an order of magnitude higher.
GandCrab tends to communicate with a wide range of what appear to be hacked sites running WordPress. It transmits data in GET requests to files with image file extensions (jpg, png, gif, bmp)