Emotet operates on a mass scale. Everything it does, it does in bulk. A typical infection begins when the victim receives a specially crafted spam email. Emotet’s creators send these out by the thousands and, in some cases, the bots themselves send more. The lures employ mass-created malicious document files. The payload URLs, from where the malware eventually gets downloaded, come in large batches, with the same file hosted in multiple locations in case some of those sites get shut down (and they do).
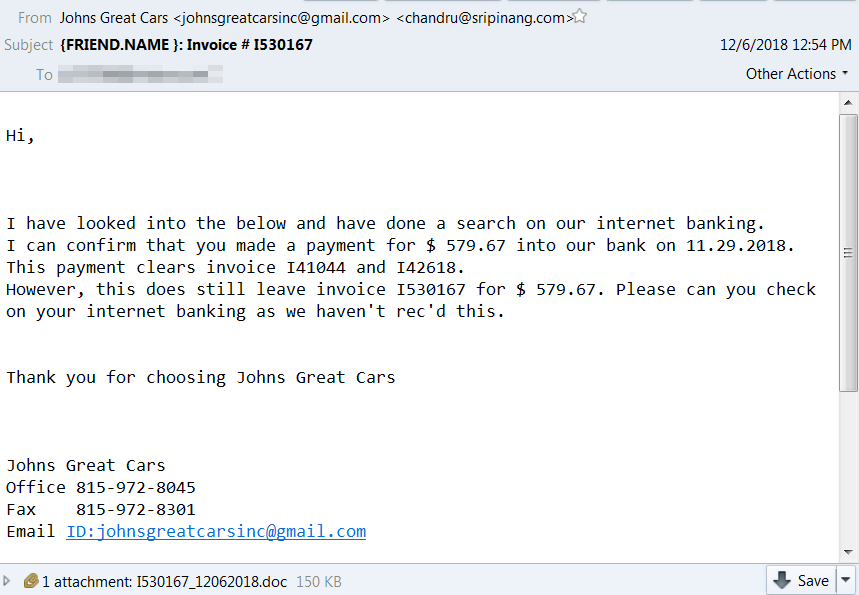
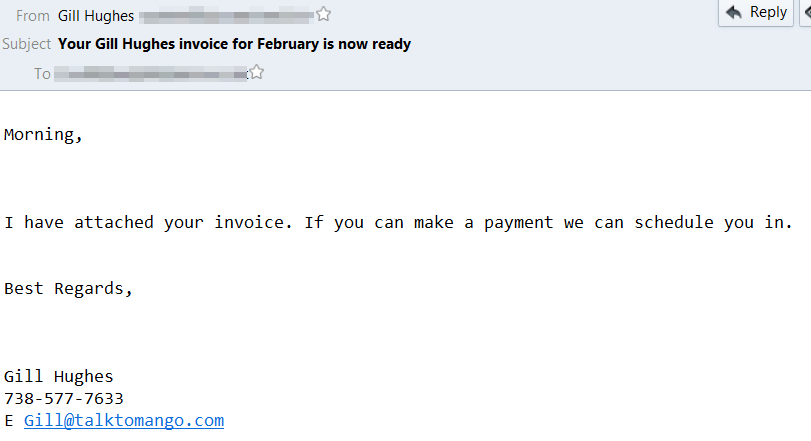
In order to operate at this scale, Emotet’s creators seem to have refined the process by which they customize each batch of messages they transmit. The message changes slightly, though it may follow a common trope, or thematic pattern: A shipping confirmation, purchase order, or an invoice asking the recipient to pay the sender (whom the recipient will likely never have heard of).
The messages take effort to randomize the body, subject, and attachment content; to “personalize” some details, which enhances the social engineering aspect of the attack. But there’s been very little effort at tweaking the rest of the content plugged in between {RECIPIENT.NAME} and {IMAGINARY TRANSACTION} in their mail merge template.
But perhaps the one thing that makes the spam messages used to deliver the Emotet family of malware most dangerous is how painfully dull they are.
Someone, somewhere comes up with this stuff, and they’ve continued to do it for years because, maybe, they’ve discovered that boring is better. They might be right. The only thing that might be more amazing than the sheer volume of effort expended on Emotet by security professionals is the success rate it achieves using the most mundane topics imaginable to convince recipients to open weaponized document attachments, or to click a link that downloads a malicious document.
Crafting the lure
“This invoice has been placed into query as it includes the error(s),” one message says, as if its author wasn’t sure how many errors was in their own invoice. It makes a request for a large (but not excessively) large amount; A few thousand dollars is enough to get anyone’s attention.
The mundaneness is the point: A UPS delivery tracking update; a utility or phone bill; a notification from a local tax authority about a missing or late payment, or even just an obscure update to tax deduction rules from the “Department of Treasure.” It doesn’t matter how the social engineering gimmick is dressed up, as long as it’s somewhat plausible and the mail attachment or links work.
Moreover, people who look at this kind of spam, day in and day out, can’t help but notice the profusion of spelling errors, typos, grammatically challenged copy, and other small failures of attention to detail in these messages. I’m as guilty of this as anyone else. And yet, it doesn’t seem to matter that these messages contain oddly constructed sentences, or misspellings of the name of a government agency in a messages ostensibly sent by that government agency.
Emotet’s operators seem to have internalized an important lesson they’ve learned after sending out this much spam. These errors don’t matter all that much. In fact, the small mistakes seem to skirt the edges of human attention, and may actually lend the lure credibility that it has been written by an imperfect human being, just like it pretends.
Localization
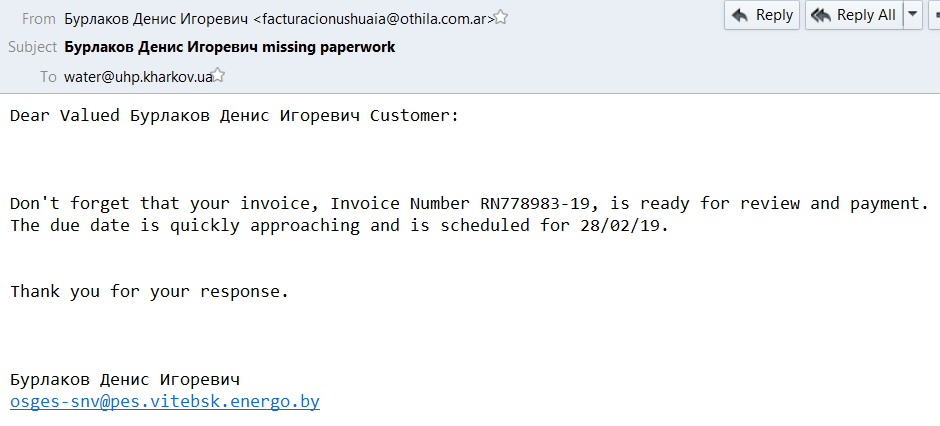
The Emotet distributors target their global audience geographically with their local language, references to in-country businesses, and even craft suitably culturally-specific fictitious identity name-combinations.
The Emotet spammers regularly get the language and target mix wrong.
The attachments have varied over time. At the time of this writing, the typical Emotet malspam uses either a malicious Word document, an XML file attachment with a .doc extension, or a PDF file with a link embedded in the body.