New York resident Jay Brodsky has filed a class action lawsuit against Apple, claiming that the company forces users into a two-factor authentication (2FA) straitjacket that they can’t shrug off, that it takes up to five minutes each time users have to enter a 2FA code, and that the time suck is causing “economic losses” to him and other Apple customers.
The lawsuit, filed on Friday in Newport Beach, California, is accusing Apple of “trespass,” based on Apple’s “locking [Brodsky] out” of his devices by requiring 2FA that allegedly can’t be disabled after two weeks.
From the filing:
Plaintiff and millions of similarly situated consumers across the nation have been and continue to suffer harm. Plaintiff and Class Members have suffered economic losses in terms of the interference with the use of their personal devices and waste of their personal time in using additional time for simple logging in.
The reference to two weeks comes from support email that Apple sometimes sends out to Apple ID owners after it enables 2FA. That email contains what the lawsuit claims, with italicized emphasis, is an unobtrusive last line that says that owners have two weeks to opt out of 2FA and go back to their previous security settings.
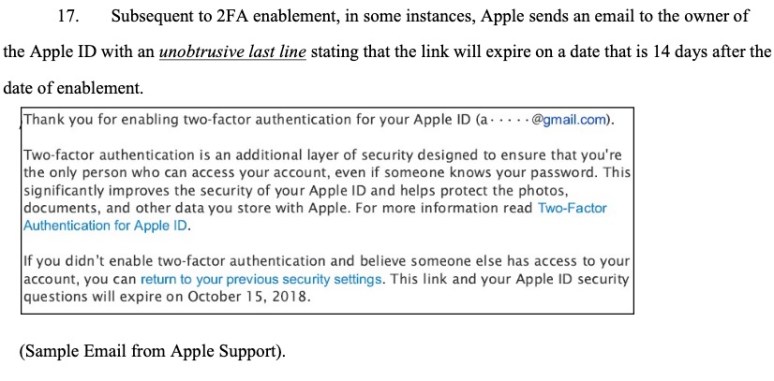
The suit claims that around September 2015, Brodsky’s Apple devices – including an iPhone and two MacBooks – were updated to have 2FA turned on, “without [his] knowledge or consent,” thus “[locking] up access” to Brodsky’s own devices and making them “inaccessible for intermittent periods of time.”
How dare you smear security all over my device
The main gist of Brodsky’s claim: it’s my device, you didn’t ask me if I wanted 2FA in the first place, using it is a pain, and you don’t give users the right to stop using 2FA.
The suit iterates what it claims is the onerous slog of logging in:
Logging in becomes a multiple-step process. First, Plaintiff has to enter his selected password on the device he is interested in logging in. Second, Plaintiff has to enter password on another trusted device to login. Third, optionally, Plaintiff has to select a Trust or Don’t Trust pop-up message response. Fourth, Plaintiff then has to wait to receive a six-digit verification code on that second device that is sent by an Apple Server on the internet. Finally, Plaintiff has to input the received six-digit verification code on the first device he is trying to log into. Each login process takes an additional estimated 2-5 or more minutes with 2FA.
Apple is causing injury to class members by “intermeddling” with the use of their devices and not letting them choose their own security level or “freely enjoy and use” their gadgets, the suit claims.
Also, by “injecting itself in the process by requiring extra logging steps,” Apple is allegedly violating California’s Invasion of Privacy Act – Section 637.2 of the California Penal Code. A third count is allegedly violating California Penal Code section 502: California’s Computer Crime Law (CCL). A fourth count is that Apple allegedly violates the Computer Fraud and Abuse Act (CFAA) by accessing people’s devices without authorization.
Finally, count five: Unjust Enrichment. By better-securing people’s devices, Apple has the gall to make money off all this, be it by selling devices or because it…
… received and retains information regarding online communications and activities of Plaintiff and the Class.
The suit wants Apple to knock it off with the 2FA. It’s also seeking disgorgement of Apple’s “ill-gotten gains,” payable to Brodsky and other class members.
What the what, now?
Where to start? When Apple introduced 2FA for Apple ID for iOS 9 and OS X El Capitan, it did so with opt-in. The feature became available first for iCloud after a spate of celebrity iCloud hacking incidents, and then more broadly to secure Apple devices soon after.
Implementing 2FA requires an explicit, multiple-step opt-in procedure requiring users to consent. However, 2FA is, in fact, required to take advantage of some of Apple’s services, like Home Sharing and HomeKit Hubs.
As far as Brodsky’s claims that logging in with 2FA eats up 2-5 minutes of his time, well, user mileage may vary. Apple Insider reports that it “hasn’t been randomly presented” with 2FA authentications, even following OS updates to an iPhone XS Max, an iPhone X, and two sixth-generation iPads. However, the publication managed to force the issue on a new device.
Apple Insider’s Mike Wuerthele whipped out a stopwatch and found that the resulting 2FA time sink was 22 seconds.
Of course, even if Apple didn’t force users into 2FA, it certainly isn’t shy about nudging them into it… for good reason.
2FA: It’s not perfect, but it’s good
2FA – particularly older forms that use SMS to deliver the code – isn’t an impenetrable shield. Way back in 2016, the US National Institute for Standards and Technology (NIST) updated its official “rules for passwords“, announcing that phone-based 2FA would no longer be considered satisfactory, at least as far as the public sector goes.
More recently, we’ve seen new methods to attack 2FA: Last month, researcher Piotr Duszyński published a tool called Modlishka (Polish: “Mantis”) capable of automating the phishing of one-time passcodes (OTPs) sent by SMS or generated using authentication apps.
If you’re worried about the risks of SMS-based 2FA for your own accounts, consider switching to an app-based authenticator instead, such as the one built into Sophos Free Mobile Security (available for Android and iOS).
Of course, the security of an authenticator app depends on the security of your phone itself, because anyone who can unlock your phone can run the app to generate the next code you need for each account.
What else causes “economic losses”?
You can’t really argue with people over 2FA being a bit of a bother. It does take more time to enter a second authentication factor, for sure. But whether it takes up 22 seconds of your life or the two to five minutes of Brodsky’s life, how much time, and potentially money, does it take to untangle a hijacked bank account, or that of a kidnapped Facebook or Twitter account?

Wiley Yates
Security is laudable, but forcing users into a straight jacket devised by the ever knowing supreme Apple guru is tantamount to similarly applied forms of guvmint coercion. Why is it there are so many people with good ideas that for them to work the population has to be drafted into the nannystate. Enough already. We get it. Apple is good at what they do. But they also are not out here were the rank and file have to deal with nannystatism that serves as another impediment in the real world. Keep in mind that often the last words spoke by a corporation are, “But it worked in the lab”.
Meir
No one forced to use apple products, and it’s your choice to do business with them.
When I got a car insurance, every insurance company “forced” me to put an immobiliser otherwise I won’t get insured. And guess what? No one sued them or complained about it.
yesIHave
No one forced me to use any Apple products, that was my own choice because I liked the way they worked and I loved the differences that I noticed very early on between Apple and Microsoft computers. So yes, that was my choice. The fact that today I cannot update any app on my phone without giving my phone number or sharing my macbook so I can receive codes on any of the screens whenever I try to update something on the other screen, is just horrible, feels fishy and I NEVER ASKED FOR THAT. Me and my wife have a phone and a laptop in our house for both use, for who the heck should I act paranoia and secure all my devices with extra authentications??? What’s the next step, obligated to buy a laptop if you want to use a phone???
Paul Ducklin
To be fair, Apple’s additional security protections are as much to protect your accounts (and the data stored in them) as they are to protect your physical devices.
The fact that your device are locked away at home (which they probably aren’t at all times… who has a phone and a laptop but never takes the phone out with them?) doesn’t protect your devices or your data from attack across the internet by cybercriminals, for example through phishing (luring you to bogus websites where you give away information you ought to have kept to yourself), malware (tricking you into installing untrustworthy apps that keep track of you from afar), or just plain old social engineering (where they remotely sweet-talk/wheedle/cajole you into telling them things you shouldn’t).
Paul Ducklin
Who coerced you into buying an Apple device? How is 2FA an impediment in the real world? (It doesn’t take 2 to 5 minutes in real life to login using 2FA, not even with the most intrusive and annoying system I can think of.)
If compromised devices affected only the owner, I wouldn’t care so much about security. But your insecure device has a knock-on insecurity effect and an overall cost on everyone else, including me, and that does matter.
Anonymous Coward
I’d argue that if you buy an Apple device, you know you’re buying into this.
Daniel Spain
nothing during the buying process states you are forced to use 2FA so you buy it unknowing you HAVE to use it.
Mahhn
“Second, Plaintiff has to enter password on another trusted device to login.”
What if you only have the one device?
Will
It falls back to text or phone call for the code.
Donna A. Dietz
Say I lose the phone. I log in to use FindMyPhone on a computer. I will be asked to use phone to accept 2FA…Yeah….
Ian
Apple needs to enforce 2FA as most users remain willfully ignorant of security but at the same time always want to blame corporations when their account/data is compromised. People need to get smarter about security and it seems like forcing it on them is the only way it will happen. If you don’t want security on your phone then buy a cheap Android device.
Simon McAllister
How ridiculous.
I use a thumb to unlock my phone to get my 2FA token/password. And I use it because it’s faster than entering my phone password.
You know I meant ‘a’ thumb as in ‘my’ left or right thumb, right? I use either so as not to wear one down, otherwise I could sue Apple for having uneven thumbs…!
Will
This is just another example of a litigious country such as the US where if we make a decision and don’t like the result, it’s clearly someone else’s fault. Apple’s 2FA is still opt-in at last I knew, and the article is simply saying if you want to use a few specific services (relating to Home Kit, etc.) it may be required. So other frivolous/hyperbolic claims from the suit aside, he must have at one point enabled it, missed the requirement to disable within two weeks if he didn’t like it and is now angry that he no longer has the option to disable it.
He always has the option to dump the Apple devices and switch to something else. He’s probably the type to have a blank login password on his computer anyway…oh, and door locks – you should probably just leave those open too, as they take a good 10 seconds or more to unlock.
Please, for all that is good in this world, let this lawsuit get dismissed immediately!
Daniel Spain
not everyone is locked into their phones all day and realize life goes on without a cell phone in their hand. So if you’re in the garage and the phone is upstairs in the bedroom in the house yes it does cause a “waste” of time and thus does give the lawsuit an argue point.
Anonymous
Oh the ignorance. 2FA is for your protection. Not Apple’s.
James Stevie Welburn
And if he has 2FA removed and his account is then hacked, will he sue them for not securing his account properly?
Anonymous
And so if this genius’s information was compromised and he didn’t have 2FA, he’d sue Apple for NOT having it installed. Some people just need to take responsibility for themselves and stop blaming others.
Anonymous
Something was forced on him that he didn’t want. Saying “they need to take responsibility” is tantamount to “we know better than you how to let you use the device you paid for” and only further justifies this lawsuit.
NoGoodOptioon
One bank I use for ATM withdrawals and credit card purchases while traveling overseas forces 2FA on me every time I log in online, mainly because I use a VPN at all times (and especially on untrusted networks abroad). This was fine when they included email as an option for receiving the security code. But then suddenly they eliminated the email option and I’m left with only text message or phone call options for the security code. How am I supposed to rely on either of those when I’m traveling abroad? When overseas I will have a different cell phone number (local, foreign SIM), which I won’t know in advance, so I won’t be able to add it to my account beforehand. And my US cell phone number won’t be operational. And I won’t be able to add a foreign number or a hotel room number AFTER I arrive overseas…because 2FA!
Will
I agree that more options should be available in these circumstances, but email (true for SMS too) was likely removed because it’s not a very secure option. Someone could have access to your email, or even be monitoring network traffic if you’re using an email client. As mentioned, SMS isn’t that reliable either, so the best bet would be to use one of those services like Google Voice that gives you a free phone number you can access from anywhere with an internet connection…
NoGoodOption
Agreed…except for the suggestion of my ever using anything Google (not gonna happen). There are other voice call options, though, as you point out. Thanks for the idea.
Daniel Spain
if you trust the browser it should be trusted. if you text me the code and I say trust this does not change in 2 weeks, if I were on a public or a pc that is not mine I can always say no but trusted browsers should stay.
anonymous coward
When traveling abroad, leave your regular phone with a trusted friend or relative. Never travel with your regular phone because it’s searchable by every customs agent and a theft target. The advantage of leaving your phone with someone you trust is that you can always get around that authentication problem described in your comment, simply by having your trusted someone receive the code for you.
Badrajith
Human factor will always be the loose end in cybersecurity.
JeffO
Wow, I wonder if all of his passwords are lowercase with 3 letters since he can’t bear the hassle of typing in something longer or more secure? It takes too long.
Anonymous
Or simply no password whatsoever on a phone or personal computer.
Daniel Spain
that is not the point. the minute you begin allowing companies to force security on you is the minute you also agree to allow them to begin tracking and recording you because after all it is a security feature intended on keeping you safe.
Bryan
Note to Evil Self…
Don’t bother searching for Jay Brodsky’s “elsewhere” accounts; his passwords will most assuredly be diverse, complex, and unique.
Spryte
In a way I have to agree. I do not own an apple or a mobile device. If my OS vendor forced me to to use 2FA, I would have to purchase a mobile device ***and*** subscribe to some overpriced mobile plan. Both an effort on a wee pension.
Paul Ducklin
AFAIK, the 2FA is neither compulsory nor dependent on any sort of mobile plan at all.
(At least in Europe and the GSM world, mobile phone connectivity for *receiving* texts is incredibly cheap. Notably, you don’t pay to receive texts at all, and you don’t need a contract.)
Steve
I really don’t think this has anything to do with security or inconvenience; I smell shyster shenanigans. Class action, huh? Where the lawyers always make out like bandits while even legitimate victims get a silly credit voucher for something they didn’t want anyway. If you lose, all you lose is whatever you put into the case, but if you win, the other guy pays your bill. WIN/WIN! Some attorneys make their careers out of cases like this.
Bryan
@Steve
Yeah, until they get nearly caught and nearly killed–then frantically switch to managing an Omaha Cinnabon.
Lisa Vaas
Better Call Saul.
Bryan
You don’t need a criminal lawyer… you need a CRIMINAL lawyer.
:,)
Thomas Facbach
Wow, ONE person with a brain, and the ONE LAWSUIT IN THE UNIVERSE that I can WHOLEHEATEDLY SUPPORT!!!!!!!!!
jim
“Nobody is forced to buy into it”
This is false, I bought into Apple for years before 2FA and have thousands of photos, videos, media, books and software tied to my apple ID. I didn’t enable 2FA, in fact, I avoided it for as long as possible until an apple rep at the genius bar enabled it while setting up a replacement phone without my knowledge. Now, trying to leave Apple, partly due to the 2FA thing but mostly because they’re actively blocking nvidia drivers that software I use for work requires, I can’t access the content tied up in my apple ID. I no longer have a “trusted apple device” and they won’t accept my non-US phone number to try to regain access to it. All of that content, years and years of family photos and access to disable subscription billing is gone.
Mine is a niche situation, for sure, but nothing that requires a phone number should be mandatory, especially if it’s going to lock you out of photos and videos that are your intellectual property.
rm3o4
I hope this moron gets his account hacked.
Anonymous
You’re not forced to buy into it but if you want 100% functionality you’re being forced to use it. This isn’t about whether or not this is better security for people who use apple products but it’s more about the freedom of choice which is being taken away from us. Another sign of a Big corporate giant forcing us to use what they think is best for us! Wake up people….were intelligent enough to decide for ourselves! Stop letting Tim Cook force us to use what he thinks is best for us. I applaud this lawsuit and think it’s ridiculous Apple can get away with this BS.
Narelle
I had apple devices when they brought this in. Just get rid of them like I did. All my devices now Samsung. The issue is who gave Apple permission to decide for me? I buy a product it’s mine. I decide what I want and don’t want. The growing need for Apple to interfere with my right to choose is concerning.
Anonymous Coward
Apple should not force 2FA because it is not secure, since it depends on SMS and SMS sims can easily get hacked.
I hope he is successful in his lawsuit. It irritates me that as a long time Apple user with many older products and newer ones as well, Apple is now trying to force people into 2FA. There are many features that no longer work unless one has 2FA.
I would rather make my own decisions about my hardware and my devices. I really don’t want Apple making decisions that they think are best for me and my own personal situation.
Paul Ducklin
Yes, mobile phone SIMs can be swapped out so the crooks end up with your number. (For clarity, I would avoid saying “SIMs can be hacked” because it sounds as though the SIM card itself can be cloned or have its secrets extracted, but SIM swapping does not actually hack the SIM card itself.)
But SIM swapping is not “easily” done and can not be done in bulk like phishing can.
Remember that with SMS-based 2FA, the crooks need your username plus your password plus a swapped-out SIM card. Without it, they need only your username and password, so it’s a bit of a myth that 2FA of this sort makes you less secure.
As for Apple “making decisions that they think are best for you”, well, that’s a pretty well-known given already in Apple’s ecosystem. Want to sideload apps other than from the App Store? Not allowed. Want to downgrade to an older version of iOS? Not allowed. Want to replace iOS with Android or Linux when the phone gets old? Not allowed.
Of all the reasons you might choose to avoid Apple phones, I suggest that the requirement to use 2FA would be way down the list, given that it does generally improve your account security, as long as you don’t use 2FA as an excuse to set a terrible password (which would turn it back into 1FA).
Nonya
People, security starts with being smart, and not getting conned, by going to idiotic web pages, or clicking on obvious links that hack your devices. Create a complex 15 digit password, and being done with it, is how I would like this to happen, and not for me to have to use a trusted device to make apple feel all warm and fuzzy about people not being smart enough to avoid being hacked. I had my pw, for 10 years, and never had an issue, now I am being forced to change my pw, and verify my pw, with my devices, including my watch, which shouldnt have anything to do with my pw… I just want my watch for the (other than time/date) running and work out features, I dont need it to pay my bills for me.
George McKenzie
Wow. I don’t have a smartphone or even a stupid one. I refuse. I have an iPad and email and am very careful about passwords and log off every time I’m not online. I also clear my cookies regularly. I am appalled that the industry is forcing everyone to have a smartphone because you need one for 2FA. It’s outrageous. If people want to do that, fine but it seems criminal to me to force us to buy a thousand dollar phone plus $50/month contract. I’d rather take my chances. Haven’t been hacked yet and my password is not 123456. This world sucks.
Paul Ducklin
Why can’t you just use your iPad for the 2FA part? (You don’t need a phone contract for 2FA. There are numerous ways of doing it, including via an app, and you already have a smartphone-like device that can run phone apps.)