Emotet is truly a threat to be reckoned with. In fact, the US Department for Homeland Security considers Emotet to be among the most costly and destructive threats to US business right now. Not that it limits itself to any one country; its reach is global with infections reported on every continent.
Emotet is a very sophisticated threat that, once in, can quickly infect an entire organization. Like other worms, it spreads without the aid of a user, enabling it to wreak widespread damage.
Once on a computer, Emotet has three main goals:
- Spread onto as many machines as possible.
- Send malicious emails to infect other organizations (damaging your sender reputation in the process).
- Download a malware payload. Traditionally the payloads have mostly been banking Trojans, with Trickbot the most prevalent. Its payload injects code into your browser to automatically debit your bank and PayPal accounts when you next login.
In many cases Emotet also tries to steal data, turning a malware infection into a data breach. Some Emotet variants skim email addresses and names from email client data and archives, likely so they can be sold as part of a wider list and used to spread more malicious spam. Others inspect your web browser, stealing histories and saved usernames and passwords.
To compound the pain, Emotet can also be a smokescreen for targeted ransomware attacks. While organizations are dealing with Emotet infections, ransomware like BitPaymer takes advantage of the distraction to hold the organization’s data hostage.
What makes Emotet so dangerous?
Emotet earns its reputation as one of the most costly and destructive threats for several reasons.
- It only needs one computer that’s not fully protected to infect an entire organization. Once it gets in, it quickly spreads laterally across the network.
- It constantly evolves. The cybercrooks behind this threat work 24/7, publishing multiple new variants and call-home addresses every single day.
- It keeps re-infecting. Emotet constantly tries to spread, often re-infecting machines that have been cleaned up.
Stop Emotet in its tracks with Sophos
Sophos’ advanced technologies can help protect your organization against Emotet.
Intercept X Advanced with EDR uses the power of advanced machine learning to identify and block Emotet files, even new variants that have never been seen before.
Cross-estate threat search enables you to hunt for hidden threats, while guided investigations show you exactly how the threat got in, which machines have been impacted, and how the threat is spreading so you can take remedial action.
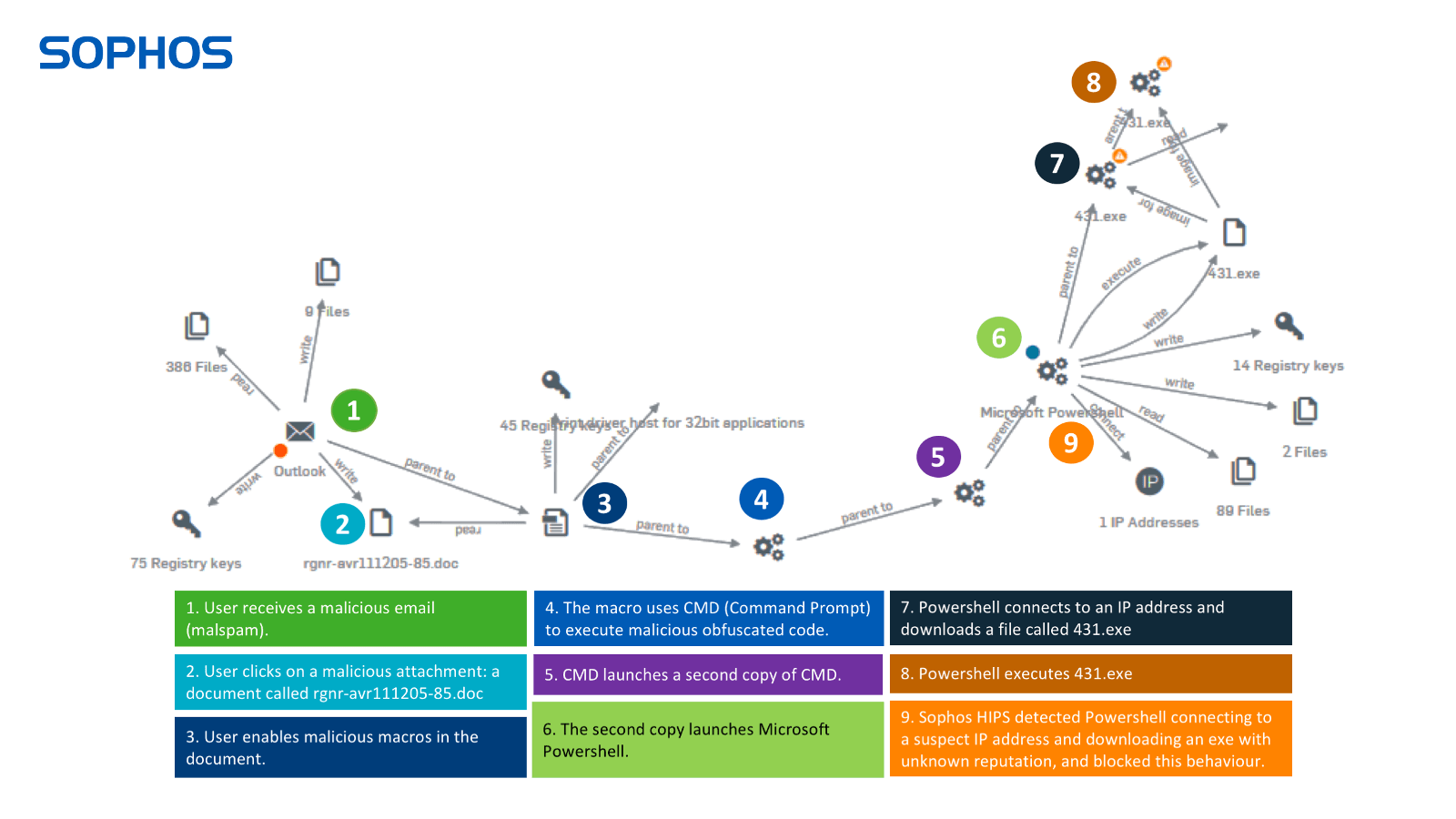
In the example below you can see how Intercept X gives you full visibility of every step in the attack chain. Note: we had to disable multiple layers of protection to allow the attack to get this far – it would normally be blocked much earlier.
Sophos XG Firewall’s advanced sandboxing examines the executable files. The HIPS behavioral monitoring detects Emotet, blocking it from entering the organization. XG also blocks all known IP addresses associated with Emotet.
Email protection (both in XG Firewall and Sophos Email) can also scan outbound emails to detect Emotet spam and identify which machines are sending it.
Join forces against Emotet with Synchronized Security
Intercept X and XG Firewall are powerful tools to stop Emotet on their own – and even better together. They share real-time threat information and automatically respond to incidents. When Intercept X detects Emotet running, it notifies XG Firewall which automatically isolates the infected machines, preventing lateral movement. Intercept X then cleans up the infection, telling the firewall once the malware is removed. At this point, XG Firewall restores network access.
Uniquely, by working together, they stop Emotet from moving across your organization. And the best news? All this happens automatically. Zero-touch. In seconds.