If you’ve had a chance to review our latest 2019 Threat Report, you know that threats and attacks are changing, and so is the role your firewall plays in providing a defense.
For most of the past decade, attackers have built up a vast repertoire of automation, coupled with exploitable vulnerabilities, in an attempt to rapidly attack targets and evade security measures or protection at the network and endpoint level.
But now, some sophisticated attackers are turning to more targeted and inherently unpredictable manual network hacks, using brute force to gain a foothold on the network, and strike out from there as if they were a resident network administrator. In some respects, we’ve now come full-circle with modern attacks now taking advantage of age-old security issues like weak passwords.
The role of the firewall in protecting against these hacks and attacks has similarly evolved. Long gone are the days where the firewall was like a medieval moat and castle wall for your protected network. We’re now at a point where you can’t necessarily trust who or what is operating within the proverbial castle walls.
Forrester refers to this situation as “zero-trust”. Essentially it means that devices and users on your network need to establish or prove trust, and if something proves untrustworthy – take action. It’s a great model that’s having widespread positive impacts on IT security. A perfect example is the use of multi-factor authentication as an extremely effective tool in establishing user trust.
On the firewall side, network segmentation or even micro-segmentation is gaining a lot of momentum in response to the evolving threat landscape.
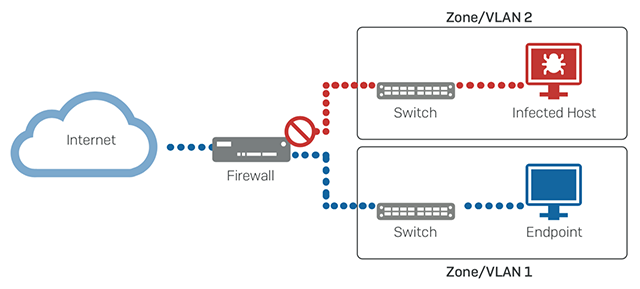
The principle is sound – segment your network into smaller and more granular subnets, and secure them together through your firewall to limit exposure in the event that one segment becomes compromised. In practice, it works great, but in some cases it can add unwanted expense, infrastructure, management overhead, and impact performance.
While the ideal solution would obviously be to firewall every device on the network separately, it’s simply not practical. However, you can get one of the key benefits of that strategy, today.
Introducing Lateral Movement Protection
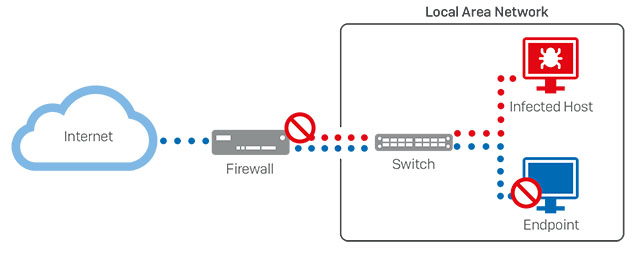
Sophos XG Firewall v17.5 recently introduced Lateral Movement Protection, a new Synchronized Security feature that effectively provides an adaptive micro-segmentation solution. With Lateral Movement Protection, each individual endpoint is effectively on its own segment – able to be isolated in response to an attack or threat – regardless of the network topology. And without any added cost, infrastructure, overhead, or performance impact.
How do we do it?
By integrating our firewall and endpoint products together, they can share health, status and other important security information through a continuous Security Heartbeat™ connection. That enables both products to use this shared telemetry to respond to an active adversary or threat on the network. When any kind of attack is detected, the endpoint Heartbeat status changes, and triggers an automated response that has the firewall coordinating and synchronizing a defense.
Not only will the firewall cut-off network access for the compromised device at the firewall, it will also advise all the healthy endpoints on the network to isolate and ignore all traffic originating from the compromised host. The combined solution provides an adaptive micro-segmentation – at the individual endpoint level. And it doesn’t require any additional infrastructure or management, and has zero performance impact. It’s the ultimate emergency response strategy, for any network.
How do you get it?
All you need is our award-winning XG Firewall and the world’s best next-gen endpoint, Intercept X. They are both super easy to deploy. In fact, you don’t even need to replace your existing firewall to get all the great benefits of Sophos Synchronized Security.
You can deploy XG Firewall inline with your existing firewall and even deploy Intercept X alongside your existing desktop AV product – it’s easy, risk-free, and brings tremendous visibility, protection and response benefits to your network.
Firewall best practices
Check out our Firewall Best Practices Guide for more information on how to optimize your network protection.
