Here’s a thing: numerous apps on your phone have permission to access your microphone.
Some, like the Phone app itself, were on the phone when you got it, but you’ve almost certainly added others – WhatsApp, Skype and Facebook, for instance – along the way.
From the moment you gave those apps audio permission, they’ve been able to listen in whenever they want, without telling you.
In theory, you’ll never know if an app is overstepping the mark; in practice, however, there are some cool ways of checking to see when an app is listening in.
Keeping track of an app’s behaviour is a handy technical skill to have, so we’re going to show you how to look at the system calls made by your Android mobile to the audio subsystem.
No more audio secrets!
By following our tutorial, you can keep track of exactly when when an app is accessing the microphone.
Note. For this article, we used a test device that was wiped first and then rooted. This means we deliberately altered the security settings to give us administrative access – on Linux/Android, the admin account is called root, so getting root access is colloquially called rooting. We strongly recommend that you don’t do research of this sort on your regular phone, just in case something goes wrong. And definitely don’t try this on your work phone!
Tracing Android API calls
The tool we’ll use to find out if apps are listening to us is called AppMon.
AppMon’s Android Tracer can monitor apps on your phone by tracing Java classes when they’re called (almost all Android apps are written in Java).
Apps that want to use the microphone use the AudioRecord class. By monitoring this with Android Tracer, we can see how and when apps are interacting with the microphone.
Most of AppMon’s documentation is focused on macOS and Linux, but in this article we’ll show you how to install it on Windows.
AppMon talks to Android via a utility called Frida, monitoring software that you’ll need to install on your test Android device first.
Frida allows you to inject scripts into Android processes, hook into functions and spy on crypto APIs. For this reason it’s a scary app to have installed on any phone outside of a test environment.
You won’t find it in the Google Play Store, so you have to sideload it. For that you’ll need to have debugging enabled on your mobile, and the Android Debugging Bridge (ADB) installed on Windows.
Here’s how to get started.
Enabling USB Debugging on Android
Firstly you’ll need to make sure your Android device is in developer mode, and that USB Debugging is enabled:
- Open the Settings app.
- Select System (Only on Android 8.0 or higher).
- Scroll to the bottom and select About phone.
- Scroll to the bottom and tap Build number 7 times. (Yes, that’s officially how you do it!)
- Return to the previous screen to find Developer options near the bottom.
Switch developer mode on, scroll down until you see the newly revealed option USB debugging, and turn it on. Now plug the Android device into your Windows machine with its USB cable, ready for the next phase.
Installing ADB on Windows
ADB is a handy tool for interacting with Android phones, and we’ll be using it to install Frida onto our device.
Download the android-sdk command-line tools for Windows.
Once the tools are downloaded and unzipped, you can run adb.exe from the command line.
Open a command window in the directory where adb.exe is currently located. You can do this by holding shift whilst right clicking on the explorer window where adb.exe exists, and selecting “open command window here”.
With your newly opened command prompt, type adb devices and hit return.
This will show you a list of the Android devices with debugging enabled that are currently connected.
Example:
C:\Users\User1> adb devices
List of devices attached
XXXXXXXXX device
Running Frida on Android
Download the frida-server app, which you need on your Android device to monitor apps that are running.
Download the compressed binary with the file name “Frida-server-NN.N.NNN-android-MMM.xz” where NN.N.NN represents the version number, and MMM is the processor type in your phone (one of arm, arm64, x86 or x86_64).
Most older Androids have ARM chips; many newer phones have the more powerful ARM64 processor – if you choose the wrong version of frida-server you won’t break anything, but it won’t work. If you aren’t sure, use a search engine to find the CPU type for your specific model of phone.
Unzip the downloaded file to the same location as adb.exe, and rename the file to Frida-server.
Back in the command prompt you opened earlier, push the Frida-server file onto your Android device and run it:
adb push frida-server /data/local/tmp/
adb shell "chmod 755 /data/local/tmp/frida-server"
adb shell
su
/data/local/tmp/frida-server &
Here we’ve pushed the Frida-server file to our Android device in the location of /data/local/tmp/, which is a directory on the Android file system that permits you to execute a script.
Then we used chmod to edit the file permissions of the Frida-server to make sure it’s allowed to run.
Finally, we ran the Frida-server program (the ampersand at the end of the command makes it run in the background).
Prepping Windows
Windows now needs to be prepared to run Android Tracer. Tracer is written in Python, and Python must be installed for it to run.
By placing Python and adb within the Windows Environment Variables, you can run both ADB and Python without having to be in the directory where adb.exe or python.exe are installed.
Installing Python 2
Here’s a quick guide on getting started with Python 2.7, which at the time of writing is the most current version of Python 2.
Browse to the Python website, select “download” next to the latest version of python 2 (2.7.15 at the time of writing). Scroll down until you see the MSI for 64 bit and 32 bit environments, and select the respective MSI based on your version of Windows. Once downloaded, launch the MSI file and follow the installation instructions.
Python and ADB Windows Environment Variables
On Windows 10, open Control Panel and search for “environment variables”. Under System select Edit the system environment variables.

Select Environment Variables at the bottom of the window. This pops open a new window where you’ll see User variables for <your user> and System variables. Under System variables there is a variable named Path. Select this so that it’s highlighted as shown in the screen grab below and then select Edit….
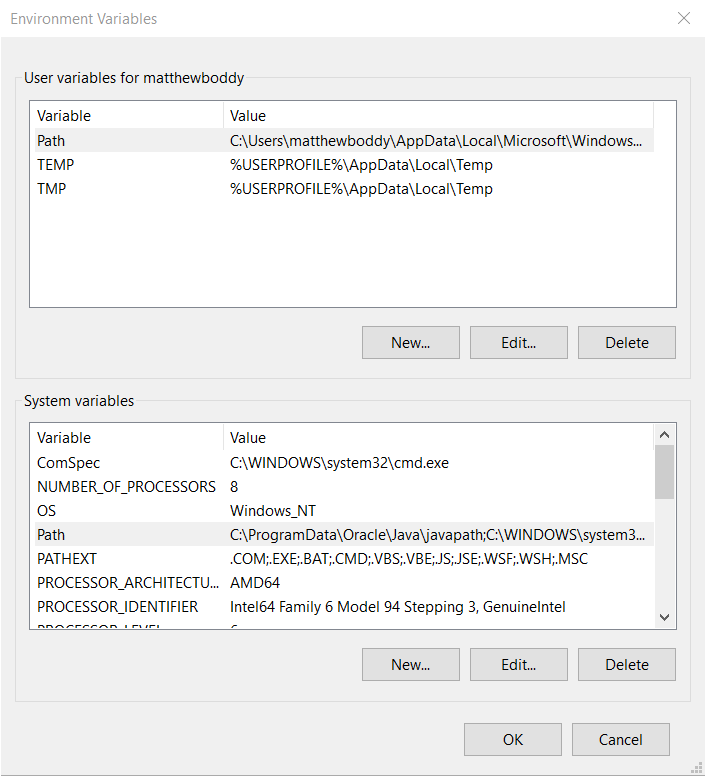
Select New to add the adb directory to the existing list, and enter the directory where adb.exe is currently located (e.g. C:\Program Files\ADB\).
Select New a second time and add the location of python.exe (e.g. C:\Python27\).
Select New for the last time and add the location of pip.exe (e.g. C:\Python27\Scripts\).
Installing AppMon Dependencies
In order to run AppMon on Windows, there are a few Python dependencies which are required.
AppMon makes use of argparse, frida, flask, termcolor and dataset.
Run the following command on your Windows device to install these dependencies:
pip install argparse frida flask termcolor dataset --upgrade
Installing AppMon
On the AppMon github page, select clone or download and download the zip file containing AppMon. You’ll have to unzip the appmon-master folder to a convenient location on your windows device.
Now navigate to the location where AppMon is unzipped and go into the folder named tracer. Hold shift and right click in this directory and then select the option to Open command window here.
You can now use Tracer to monitor if a mobile app is eavesdropping when it shouldn’t be.
An example command to see if WhatsApp is listening when it shouldn’t is provided in the following section.
Monitoring Your Microphone
This is where all the hard work pays off.
We can now run Android Tracer to monitor when the microphone starts to record:
python android_tracer.py -a "com.whatsapp" -c "*AudioRecord*" -m "startRecording"
above, -a "com.whatsapp" says you want to monitor an app called com.whatsapp; the ‑c option specifies the class (Java sub-program) to monitor; and -m says which specific method (Java function) to watch out for.
The asterisks in the text string “*AudioRecord*” denote that you want to match any characters at the start and end of the text.
This makes it easy to keep an eye on a whole set of related classes or methods without listing every one explicitly – any method that has “AudioRecord” somewhere in its name will match.
Android’s comprehensive developer documentation has a complete list of classes and methods you might want to monitor – for example, we’re monitoring startRecording in the AudioRecord class here, but you might want to look at takePicture in the Camera class instead.
Here’s what we uncovered on our test device:
(Watch directly on YouTube if the video won’t play here.)
If you’ve enjoyed researching into what your mobile is getting up to behind the scenes, check out this article on oversharing apps.
New! Improvements to Android
Since writing this article, Android 9 Pie has been released, bringing with it some much-needed privacy for us all. In a statement on the Android Developers Blog, Dave Burke, VP of Engineering, said that the microphone won’t be accessible whilst the app is idle:
The system now restricts access to mic, camera, and all SensorManager sensors from apps that are idle.

Kurt S
Very useful info. I will be doing some listening. I suspect that my colleagues will once again look at me like a practitioner of the dark arts if I start talking about what their phones are doing without them knowing
Matt Boddy
Thanks Kurt S! They’ll have to learn defense against the dark arts.. Unless they’re muggles.
Mike
Samsung has the App Permissions Monitor (at least on the S8) which notifies you when permissions are used (customizable). Nice feature.