What’s worse than ransomware that scrambles all your files and demands money for the key to unlock them and get them back?
Well, WannaCry certainly added a new dimension to the ransomware danger, because it combined the data-scrambling process with self-spreading computer virus code.
As a result, WannaCry could worm its way through your network automatically, potentially leaving you with hundreds or even thousands of scrambled computers in a single attack, even if only one user opened a booby-trapped attachment or downloaded a file from a poisoned website.
The crooks behind the SamSam ransomware have also latched onto a rather different approach: instead of trying to reach thousands or tens of thousands of victims around the world with a hard-hitting spam campaign, and squeezing each of them for hundreds or thousands of dollars each, the SamSammers seem to attack one organisation at a time.
Indeed, the SamSammers generally keep their hand hidden until they have broken into the network and figured out, using similar techniques to penetration testers, a list of computers they know they can encrypt all at the same time.
Then they let fly on all of those identified devices at once, giving them a much higher chance of scrambling at least some computers that are critical to the workflow of your company,
Finally, they make a payment demand, typically charging a few thousand dollars for each individual computer you want to unlock, but also offering an all-you-can-eat deal of $50,000 to decrypt everything.
But now there’s a back-to-front approach – a bunch of scammers who aren’t saying, “If you don’t pay we won’t fix your files,” but instead saying, “If you do pay we won’t scramble them in the first place.”
Simply put, it’s a protection racket, where you’re being stood over to prevent bad things happening, rather than a ransom-based racket, where you are being squeezed to recover from bad things that already happened:
From: WannaCry-Hack-team
To: **************
Subject: !!!Warning Wannacrypt!!!
Hello! WannaCry is back! All your devices were cracked with our program installed on them. We have improved operation of our program, so you will not be able to regain the data after the attack.
All the information will be encrypted and then erased. Antivirus software will not be able to detect our program, while firewalls will be strengthless against our unique code.
Should your files be encrypted, you will lose them forever.
Our program also covers the local network, erasing data on all computers connected to the network and remote servers, all cloud-stored data, and freezing website operation. We have already deployed our program on your devices.
Deletion of your data is scheduled for June **, 2018, at **:** – **:** PM. All data stored on your computers, servers, and mobile devices will be destroyed. Devices working on any version of Windows, iOS, macOS, Android, and Linux are subject to data erasion.
With an eye to ensure against data demolition, you can pay 0.1 BTC (~$650) to the bitcoin wallet: ****************
The bad news is that this WannaCrypt “demanding money with menaces” threat email is very widespread – we’ve had people worried about it from all over, which is why we decided to write up this warning.
The good news is that these particular crooks don’t actually have any malware to back up their threat.
Indeed, their claim that “antivirus software will not be able to detect [the] program” is one of the few truths in this scam, for the simple and fortunate reason that, in this case, there is no program to detect.
Just to be clear here: disk wiping malware – think of it as ransomware with no decryption key, so you can’t buy your files back from the crooks even if you want to – most certainly exists.
So, these WannaCrypt scammers could, in theory, have been telling the truth, giving you just a few hours to hunt down and turn off their attack code before your data was destroyed.
In this particular case, however, the whole thing is a fraud, right down to the existence of the malware in the first place.
What to do?
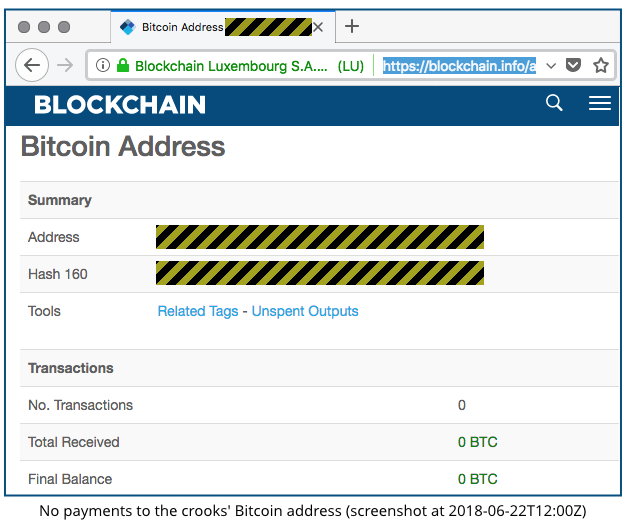
- Don’t pay up. As far as we can see from the Bitcoin blockchain, no one has yet sent any funds [2018-06-22T12:00Z], at least to the Bitcoin address in the spam samples we’ve seen so far.
- Don’t contact the scammers “just in case”. Letting them know you’re there and worried is giving away information about yourself that you dont need to.
- Make sure you’re patched and protected. To pull off an attack like this would mean infecting you first but then giving you a fighting chance to track down the malware before it went off (ransomware, in contrast, only alerts you after it has triggered), so be prepared.
Remember that ransomware, disk wiperware, protection racketware and other malware that destroys your data is only one of many ways to lose your precious digital stuff – software bugs, fire, flood, loss, theft, and plain old hardware age can all result in abrupt and catastrophic data loss, too…
…so get those backups sorted, and do it today!
Richard
We had a batch of these scareware messages arrive yesterday. The odd thing is that one of the recipients is a pretty unique mailbox that should be resistant to spam. As yet, we can’t figure how that mailbox address ended up on a spam list. We know our mail servers are clean and haven’t been breached and we can infer from other data that I can’t share that the recipient couldn’t have had their address hoovered up by a breach of a 3rd party. So how did the bad guys hit on it?
Analysis of the internet headers of the messages received suggests they exploited open relays or compromised mail servers. Anecdotal checks of the other (3rd party) addresses on the To: line suggests these are real people too. Finally we observed that all addresses on the To: line were business addresses and wonder if they have something in common, like all using a common cloud hosted mail service, as we do? That thought fills me with dread.
Anonymous
Is it possible a corporate account was compromised and they scraped an internal directory to get a list of all valid email addresses?
Paul Ducklin
Remember that any email address that has ever sent out email will be in the “From:” field of messages in other people’s inboxes, so if any of the recipients ever get infected by data-stealing malware (code that grubs around for emails is astonishingly easy to write because the format is so recognisable) then you’re known to at least one lot of crooks… until they sell the list on to the next lot, and so on.
Anonymous
Just thinking back at my university we’d receive phishing emails pretty regularly and as soon as someone got phished, a bot would login into their account and send the same email out to everyone they’ve ever contacted (and the Help Desk would usually get a copy sent to it since a lot of people have emailed them before)
Anonymous
Thanks for the article Paul.
What if ( a big if ) some ransomeware has already gained entrance into the network , although not yet detected but a similar mail is received, how would you advice to deal with such ?
Paul Ducklin
We addressed the “What if” issue here:
https://soundcloud.com/sophossecurity/wannacrypt-ransomware-scam-widely-spammed-out
(It’s a podcast but just 7 minutes long.)
Technically, an infect-warn-wipe attack like this is possible, but given that the crooks need to give you enough time to get bitcoins together (if they push you too hard for time then they make no money), they have to be certain that their malware will sneaky enough to remain invisible even after they have tipped you off to go looking for it.
BTW, that’s why we wanted to warn people this time that we couldn’t find any evidence of malware behind this one…
Hugo K.
Hi Paul, thanks for your article.
However I was wondering about this menace. Wasn’t it that Wannacry was defused by creating the searched-for domain? I mean, these guys are menacing people with something that’s has suppossedly been neutered in May 2017. Social engineering at its most.
Paul Ducklin
I think they just used the name “WannaCry” to get your attention – the premise is that this is like a whole new WannaCry, comparable to when WannaCry was at its worst.