Imagine if you could walk up to your bicycle, unlock it within two seconds, and ride off without grubbing in your pocket for keys, without spinning a combination dial with cold, wet hands, and without fiddling around with a mobile phone app to tell the lock to open.
What if you could just swipe your finger over the lock and open it as easily as you unlock your mobile phone with its fingerprint scanner?
Well, Canadian company Tapplock sells a product that not only works that way, but also boasts “unbreakable design”.
Admittedly, the small print on its website ultimately tones that punchy claim down to say “virtually unbreakable”, but the Tapplock is certainly pitched as a secure product.
Tapplock claims that unlocking takes just 0.8 seconds, and that up to 500 different fingerprints can be registered with the lock, making it suitable for even the most extended family.
Those cool features are supposed to be what makes the Tapplock cost a bullish $99 – big money for a padlock.
Unfortunately, as well-known UK hackers-and-crackers (we mean this in a neutral sense, of course!) Pen Test Partners (PTP) rather too rapidly discovered…
…the Tapplock’s unbreakability was, indeed, virtual rather than actual.
PTP researchers were able to write an app that unlocked any Tapplock in just 2 seconds, compared to 0.8 seconds for one that was opened using a fingerprint or Tapplock’s own secure app.
Additionally, they found that the protocol used to grant access to multiple users access couldn’t handle revocation.
That’s a fancy way of saying that the unlock code transmitted to the lock was identical for every user, which is like having the same password for every account on a server – if one person goes rogue, you can’t lock them out without locking everyone else out, too.
Conventional locks suffer from the same problem, of course. Once you’ve given a friend a copy of the key to your flat, you can’t keep them out in future without changing the lock. Even if they give you back their copy of the key, you can’t be sure they haven’t made their own copy of the copy for later.
Copying the key
The “one key to rule them all” was found by running a Bluetooth traffic sniffer on Tapplock’s app-to-lock communication, and recording the data stream that was transmitted when two different users unlocked it.
Lo and behold, the data was the same every time, meaning that the Tapplock is no more flexible in respect of multiple users than a conventional lock with a physical key – once made, a copy of the digital “key” works over and over again.
Given that the Tapplock app allows to you add and remove users, and pitches its multi-user capability as a cool feature to help you justify spending $99 on a padlock…
…that discovery didn’t fill Pen Test Partners with confidence.
Reconstructing the key
Copying a Tapplock key turned out to be trivial, but that only allows a crook to open a lock for which they’ve already sniffed out an app-to-key Bluetooth conversation.
In other words, being able to clone an existing key is bad, but nowhere near as bad as getting a skeleton key that will open locks you haven’t seen before.
So PTP’s next step was to try to answer the question, “How is the block of random-looking key data computed?”
The researchers found that Tapplock derived the key for the lock not from a shared secret that you could choose yourself, but directly from the MAC address (the physical network ID) of the lock’s Bluetooth network hardware.
That’s bad!
We’ve written about MAC-address-used-as-password SNAFUs before, because there’s never an excuse for using a network card’s hardware address as the basis to construct a secret.
Repeat after me: MAC addresses aren’t secret, because their purpose is to be publicly unique.
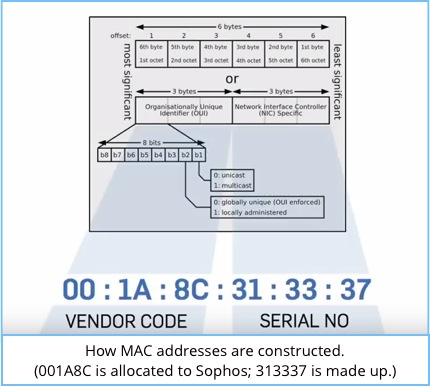
Indeed, the MAC is openly added to every network packet sent from a specific device precisely because it is unique, and is therefore a convenient way of tagging packets so their source can easily be identified.
Because of this, the researchers were able to write an app that could rapidly generate the keycode for any Tapplock as soon as it sent out network traffic over Bluetooth.
As a result, the “open any lock” app takes just 2 seconds compared to the “open one specific lock” app’s 0.8 seconds.
What to do?
Deriving a keycode from a computer’s MAC address is like using your username as your password: it was a terrible idea back in 1988, and it’s a similarly terrible idea in 2018.
Tapplock has acknowledged Pen Test’s findings in an official communique:
Tapplock is pushing out an important security patch. Please be attentive to update your app once it becomes available to your region. We highly recommend you also upgrading the firmware of your locks to get the latest protection.
This patch addresses several Bluetooth / communication vulnerabilities that may allow unauthorised users to illegal gain access. Tapplock will continue to monitor the latest security trends and provide updates from time to time.
Many thanks to the Pen Test Partners for the timely prompt and ethical disclosure.
It’s not immediately clear how upgrading the app is an “important security patch” while upgrading the firmware of the lock itself is merely “highly recommended”…
…so if you have a Tapplock, be sure to do both.

Cameron
This is the same lock that can be physically disassembled in a matter of minutes which updated firmware isn’t going to help.
[URL removed]
Paul Ducklin
The physical disassembly of the lock (unscrewing the back with a glued-on GoPro mount) turns out to be an interesting story that the PTP article discusses.
Apparently there is a locking pin that pops up after the back is screwed on that prevents you removing it – but there was no QA procedure to make sure it had engaged properly before shipping, so there was a small chance it hadn’t. Tapplock says it has now implemented a pre-shipping check.
I left that bit out to concentrate on the cybersecurity part (this article was about the digital attack not the physical one) but if you want to know more, including watching the video URL redacted above, just go to the PTP analysis I linked to in the article. PTP also tested the lock it for cutting resistance and claim that very modest bolt cutters (just 30cm long) could snip the shackle – there’s a pic in their piece.
FreedomISaMYTH
wow….
Anonymous
Also can open it with grinder with a cutting wheel too pretty fast
Paul Ducklin
Takes longer than 2 seconds, and requires a bigger power supply that a mobile phone!
Nobody_Holme
I’m interested to see how it handles a MAC collision, and if you can change it’s key with that.
Also, if you manage to change it’s key, which one unlocks it afterwards, does it survive power loss, etc.
I’d buy one to test it, but $99 for a lock with physical security weaknesses no matter how i play with the firmware sounds like a poor choice anyway.
Paul Ducklin
I don’t see how a MAC collision (where you put a device within range that has been deliberately reconfigured to use the same MAC as the lock) would make any difference.
It might cause a temporary Bluetooth networking DoS but it seems vanishingly unlikely that the lock’s firmware has any sort of “auto-adjust the MAC in case of collision”. What would be the point? You’d just sniff out the new MAC and derive the key from that.
shaun jamers
Another thing to add, anyone with a GoPro holder and a screw driver can get inside the padlock and dismantle it in 30 seconds.
Paul Ducklin
See my reply to @Cameron above – it turns out that “anyone can open it with a GoPro mount” isn’t quite true.
A YouTuber who made a video of himself opening the lock was able to do it with a GoPro mount on the first sample he bought, but not the second sample. PTP also tried and couldn’t do it (the mount snapped before the lock opened). So *some* locks are unscrewable, but they aren’t supposed to be.
The digital unlocking part was badly designed, and then implemented to match. No amount of quality assurance can save that sort of blunder because the QA tests merely confirm that it is “correctly” substandard :-(
In contrast, the anti-unscrewing protection was there by design, and should have worked, but a lack of QA meant that locks that hadn’t latched tight weren’t detected before shipping.
See the PTP report linked to in the article for more about the physical security of the lock…
0laf
Much as I enjoy the technical wizardry involved in cracking this lock I suspect as a bike thief I’d probably leave the bluetooth sniffer at home and hit this lock very hard a couple of times with a 2lbs hammer. It doesn’t look very strong.
Even if I don’t unlock the bike I’ll have destroyed your $99 Idiot lock which will mean you’ll have to leave the bike for longer, possibly overnight, when I can take my time to steal your stuff.
Paul Ducklin
In theory, you could just walk around with an “autounlocking app” that popped every Tapplock as you went past (2 seconds each!), with your mobile phone in your rucksack. You wouldn’t even need to get your hammer out, or find somewhere to rest the lock to hit it.
Bill
I’ll bet a bolt cutter could remove it in about 2 seconds.
Paul Ducklin
See my reply above to @Cameron.
PTP did take a glance at its physical security and they were able to cut through the weak part of the shackle with a very modest 30cm cutting tool. Click the link to their analysis in the article above.
An unlocking app is in many ways worse, of course (unless you are stealing a visible item that’s locked up with it, such as the bicycle I alluded to in the article -), because the lock is still 100% functional afterwards – you can lock it back up if you like. So if you were breaking into a shed, it wouldn’t be obvious from the outside that you were in there at all… and you wouldn’t need to carry any “going equipped” tools in your bag, or to make any noise cracking the shackle.
0laf
Or steal the lock as well and sell it to the next gadget obsessed numpty on Ebay. When I had a motorbike the chain and lock I used to secure that weighed about 5kg and it would only hold off a determined attacker for so long. That motorbike probably was worth less then some of the cycles being ‘protected’ by this bit of tinsel.