Have you ever wanted to know what your phone is up to?
Good, then this article is for you.
Phones are locked down so you don’t have to worry about what’s going on under the hood. That’s great if you want a device that Just Works, and it’s the exact opposite if you’re the kind of person that worries about what it might be up to – like me.
Fortunately, if you have a bit of time and some technical skills, there are some simple ways to see what your apps are up to.
One of the things I worry about is oversharing – apps sending out more data than they need to, or transmitting data in insecure ways – such as using unencrypted HTTP requests instead of HTTPS.
My concerns led me to do some network analysis on popular Android apps, following the methodology set out in the OWASP Mobile Security Testing Guide.
I’ll tell you what I did, what I discovered and how you can do it to.
Oversharing apps
I looked at the charts of the most popular apps on Google Play, picked a few at random, installed them and then monitored their traffic to see what they were sharing.
I tested fourteen popular apps:
- Four of them sent data unencrypted, making them easy to spy on over public Wi-Fi.
- One app shared email addresses and authentication tokens in plain text.
- Another shared my ZIP code, Android version and battery charge (a potential fingerprint).
I was shocked at how easy it was to discover such basic security blunders, and shared what I found with the apps’ developers.
There are millions of apps on Google Play, and millions more on other markets – far too many for me to test on my own. That’s where you come in – here’s how I did it, so you can do it too.
A simple way to spy on your phone
This basic setup will get you up and running, looking for one thing: apps that use HTTP instead of HTTPS. It won’t catch everything your apps are doing, but it’s a very good place to start.
To see what my Android phone was up to, I installed Fiddler on a Windows computer that was on the same Wi-Fi network as a Nexus 5 phone running Android 6.0.1.
Fiddler is a freely downloadable web debugging proxy that lets you capture and view the traffic going into and out of your Android device (other proxy applications are available, such as BURP Suite and Charles).
Windows setup
Install Fiddler on your Windows machine. Open it, and go to Tools > Options > Connections.
The Connections tab shows you which port Fiddler is listening on (it’s port 8888 by default). If you want to use a different port, change it and then write it down, you’ll need it later.
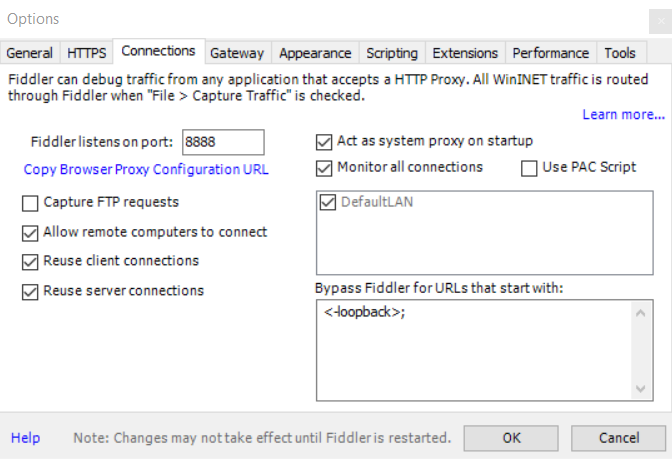
Next, we need to find out the Windows machine’s IP address.
Open a command prompt and type ipconfig. Your IP address is listed as IPv4 Address under whichever network adapter your computer is using to connect to your Wi-Fi network (for obvious reasons, your Windows and Android devices will need to be on the same network).
Android setup
With Fiddler setup on Windows, you now need to get your Android device using it as a proxy so that it routes traffic through it. Here’s how:
- Open Settings.
- Open Wireless Settings.
- Select the Wi-Fi network your Windows machine is on.
- Select Advanced Settings.
- Change the proxy configuration from None to Manual.
- Set the proxy hostname to your Windows machine’s IP address.
- Set the proxy port to whichever port Fiddler is listening on.
Fiddler is now set up to capture traffic from your Android device.
Analysis
Fiddler is now setup as a Man-in-the-Middle (MitM), so we’re going to open our apps and watch their traffic passing through it to see if they’re using HTTP and potentially sharing more than they should.
(A handy feature of Fiddler is that you can double click on a packet that you want to inspect and it will automatically identify what it thinks is the most important information in that packet.)
So what should you look for?
- Images: Like the recent issues with Tinder, my tests showed that some apps encrypt all of their traffic apart from images.
- JSON data: One of the apps I tested sent a JSON file (a data structure in plain text) that contained a username, email address and authentication details.
- URLs: You’ll be surprised at what you can see in a URL sometimes. I saw my IP Address, Android version, phone make and model, ZIP code, geo-coordinates, battery charge – all in one URL!
The list goes on, of course, and if you have any suggestions on things to look out for based on what you find, please leave them in the comments below.
A word to app developers: If you’re an Android or iPhone app developer and you’ve yet to implement SSL/TLS in your apps… get on with it!
You can pay a few dollars for a server certificate from your hosting company, or get one for free from Let’s Encrypt. Information about what to do in your app to support SSL/TLS can be found on the Android Developer’s Security with HTTPS and SSL pages.
A word to would-be hackers: Eric S. Raymond famously said, “many eyes make all bugs shallow”. It’s not entirely true, but it helps and I think the more people that hold their Android and iPhone apps to account, the more chance we have of finding misbehaving apps and improving the overall standard.
If you decide to start looking more closely at what your apps are doing, I’d love to hear about what you find, either in the comments below or via our tips email address, tips@sophos.com.
But remember: If you do find something, please practice responsible disclosure.
Going to Infosec Europe 2018?
I’ll be talking about this very subject on the Sophos stand (F160) at Infosec in London next week, with a presentation titled “Hacking Android: How to find out which apps are spying on you”. I’ll be presenting at 15:00 on Tuesday 5th June and 14:00 on Wednesday 6th June.
Please stop by and say hi if you’ll be at the event. If you haven’t done so already, you can register for Infosec Europe here.

NK
this is what i needed!!! thank you.
i wish there was an app i could install that would tell me which other apps i have are not using https. maybe grant it access to the internal phone logs?
David
Is there a way to do this with ios apps?
Matt Boddy
Hey David,
Indeed there is.
1. Go to settings
2. Select Wi-Fi.
3. Press the info button next to your Wi-Fi network.
4. Select configure proxy.
5. Select manual proxy.
6. Set the “server” to your Windows computer’s IP address.
7. Set the “port” to whichever port Fiddler is listening on.
I’ve just tested this on IOS 11.1. Please let me know if this is different on your device.
Hope this helps.
Steve
Excellent follow-up to an excellent write-up. Might I suggest updating the article to include the IOS procedure with the other two?