The next-generation firewall was essentially born out of a need to provide much-needed visibility and control over users and their applications.
So why does your app control report look like this?
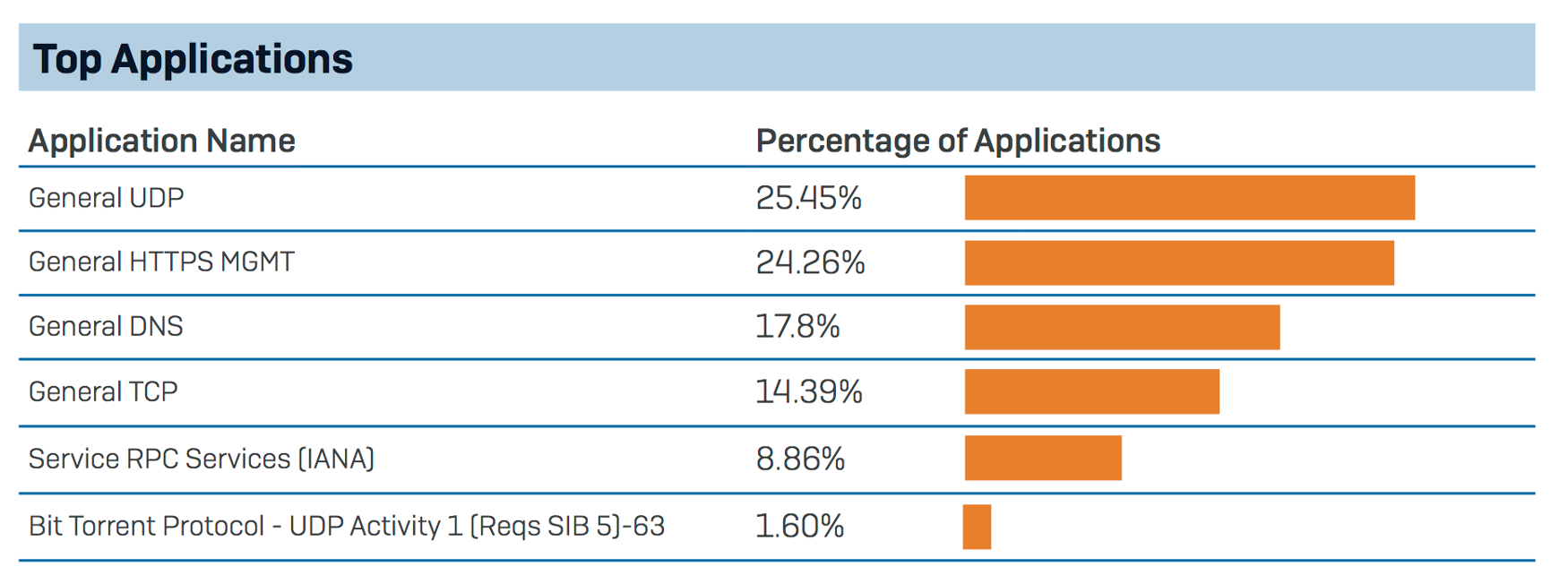
In my recent article the problem with firewalls I explained why, for many network administrators, firewalls aren’t the trusted enforcers they once were. In this article I focus on why most of the traffic passing through a modern firewall remains unknown, unidentified or simply too generic to be classified or controlled.
Why application control matters
Over the years, firewalls have evolved, changing from outward looking perimeter sentries into network guardians that protect against threats from inside a network, as well as outside.
This change in focus has been driven by the threat of malware, the danger posed by application vulnerabilities, the risk of data breaches and data loss, compliance obligations, and the need to optimize network performance.
To accomplish these things the next-gen firewall literally rose above the ports and protocols of earlier stateful firewalls to higher layers in the OSI model, to provide visibility and control over users and their applications.
They use deep packet inspection to identify applications and associate them to users or hosts on a network, allowing administrators to do things like prioritizing the ERP system, VoIP traffic or CRM software over streaming media, or blocking and identifying users of peer-to-peer file sharing apps.
That kind of control relies on your firewall being able to identify applications successfully, which it does by looking for patterns in traffic, referred to as signatures. Some applications wear the equivalent of a name tag, making their traffic easy to identify, most apps don’t though and some even go out of their way to slip through firewalls unidentified.
Applications that many organizations consider risky, such as BitTorrent clients, can try to fool your firewall by constantly changing their traffic patterns and the way they connect out of your network. Other applications evade detection by using encryption or masquerading as something else, such as a web browser.
Signature-based detection can also fail when an application is updated and its traffic pattern changes, or when an application is bespoke or simply too obscure to have a matching pattern.
It’s a situation that doesn’t just leave potential risks undetected, your essential business applications – things like ERP solutions or CRM software – can also go undetected, leaving their traffic to get crushed or squeezed out under the weight of web surfing and other less important or unwanted application traffic.
Without a match, your firewall has no idea what it’s dealing with and no control.
How big is the problem?
Sophos recently conducted a survey of mid-sized organizations to determine how much of their application traffic was going unidentified and uncontrolled.
Nearly 70% of organizations surveyed had a next-gen firewall or UTM with application awareness. Respondents revealed that, on average, 60% of traffic is going unidentified… and many organizations reported that up to 90% of their application traffic was unidentified.
If you’re concerned about the security, liability, or performance impact this lack of visibility is having on your organization, you’re not alone…
- 82% of survey respondents are rightfully concerned about the security risk
- 65% were concerned with the impact on network performance
- 40% worried about potential legal liability and compliance risks
The survey also revealed the applications that organizations were most concerned about either because of the high risk of security vulnerabilities, compliance risks caused by potentially inappropriate or illegal content, productivity impact or bandwidth consumption:
- IM and conference apps like Skype and TeamViewer
- BitTorrent and other P2P clients including uTorrent, Vuze and Freenet
- Proxy and tunnel clients such as Ultrasurf, Hotspot Shield and Psiphon
- Games and gaming platforms like Steam
Your next-gen firewall’s signatures aren’t going to help you control these applications because they’re simply not going to find a match in most cases. The traffic will simply appear as HTTP, HTTPS, TLS, web browsing and other general, non-helpful categories in your reports.
Fortunately, we’ve come up with a rather elegant solution to this problem. Download our white paper Keep your network under control: Why network admins need complete application visibility to learn more.

Dries
ssl decryption & constant updates and you are set. besides its not only signatures, but true you should keep using url filtering next to it.