Legitimate cryptomining programs ask users for permission to run. Malicious versions don’t, opting instead to quietly leach a computer’s resources. SophosLabs is seeing more of the latter variety, with a new twist:
Instead of showing up as executable files, they take the form of scripts hidden on websites, mining for cryptocurrency in the browser. Visitors to these sites see no evidence of the mining. The only clues that something may be amiss are their computer slowing down and their fans revving up.
A clear example of this is Coinhive, a Monero miner that first appeared in mid-September. The number of sites hiding it has steadily increased in recent weeks, as cryptocurrency values have taken a wild trajectory skyward.
Given their parasitic nature, Sophos has decided to start tagging Coinhive and other JavaScript-based cryptominers as malware to be blocked when users stumble upon a site harboring them.
Sophos CTO Joe Levy explains why:
Our position is that when this software is run in any user’s browser without an organization’s consent, it is parasitic, and should be considered malware because we don’t have something called parasiteware today. In instances where an organization really wants to donate its CPU/GPU cycles, and where the mining operation has gone to sufficient lengths to enable vendors like us to easily differentiate between consensual and non-consensual versions, then we can have a discussion about different classifications.
Cryptomining takes a sinister turn
Cryptomining is a process used to discover Bitcoin, Monero, and such other cryptocurrencies as Ethereum and Litecoin. It requires massive amounts of computer processing power, which slows down performance and leaves wear and tear.
This wasn’t always a problem because the activity was largely limited to those who chose to do it. That began to change as cryptocurrency prices skyrocketed. A single Bitcoin was worth $1000 at the start of 2017 and was valued at around $17,000 by year’s end.
Cyber thieves have taken notice and started using cryptominers to make money.
As noted above, JavaScript miners like those from Coinhive are added to websites and run in the browser, using visitors’ CPUs to generate cryptocurrency. Users may notice poor performance, a spike in CPU usage and batteries draining faster than usual.
Coinhive also works on mobile devices and over short periods the user may notice the device’s temperature increasing dramatically.
Coinhive rises with cryptocurrency values
As the value of such cryptocurrencies as Bitcoin (BTC) and Monero (XMR) skyrocketed in the last couple of weeks, SophosLabs has noticed a steady rise in sites using Coinhive scripts.
Here’s what the rise of Coinhive looks like compared to rising BTC and XMR values:
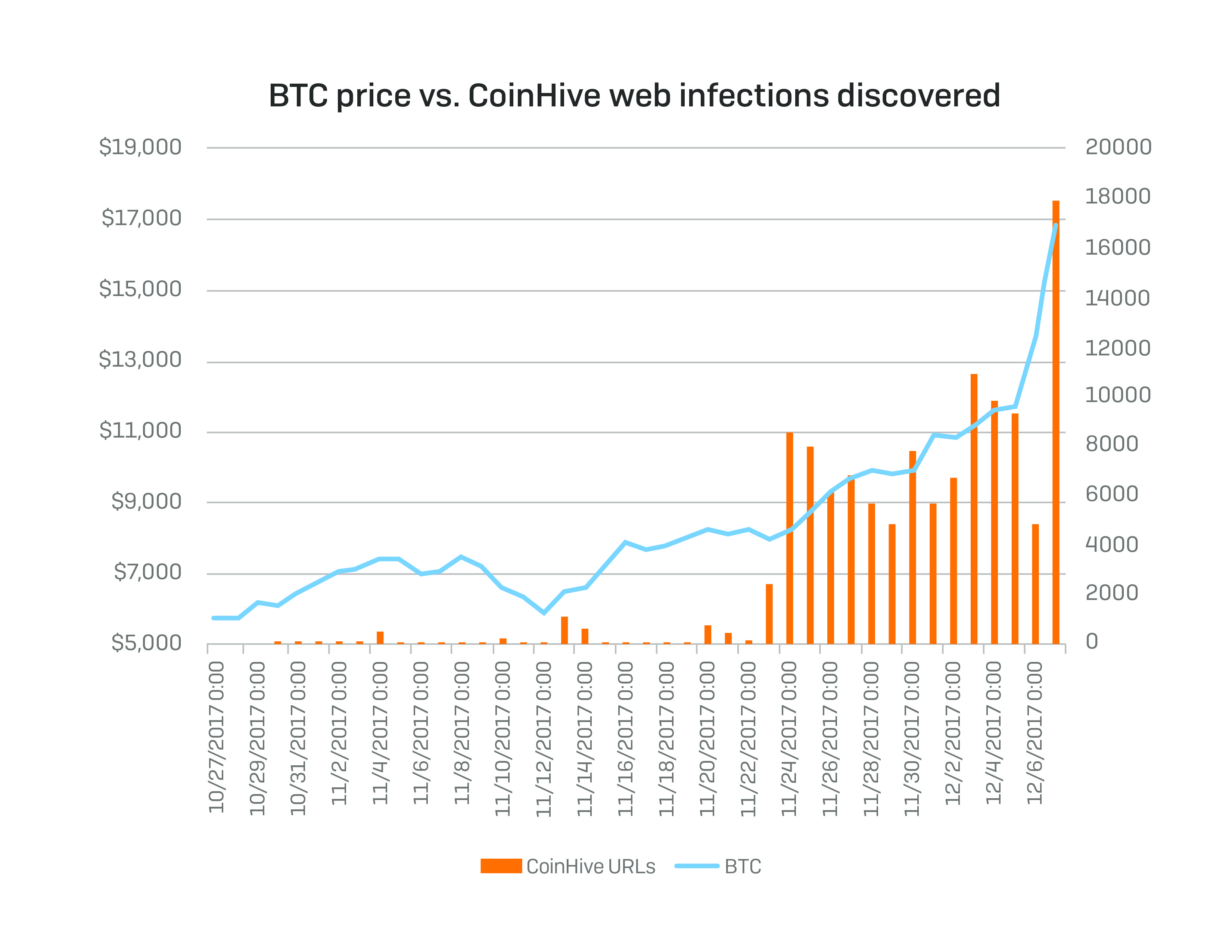
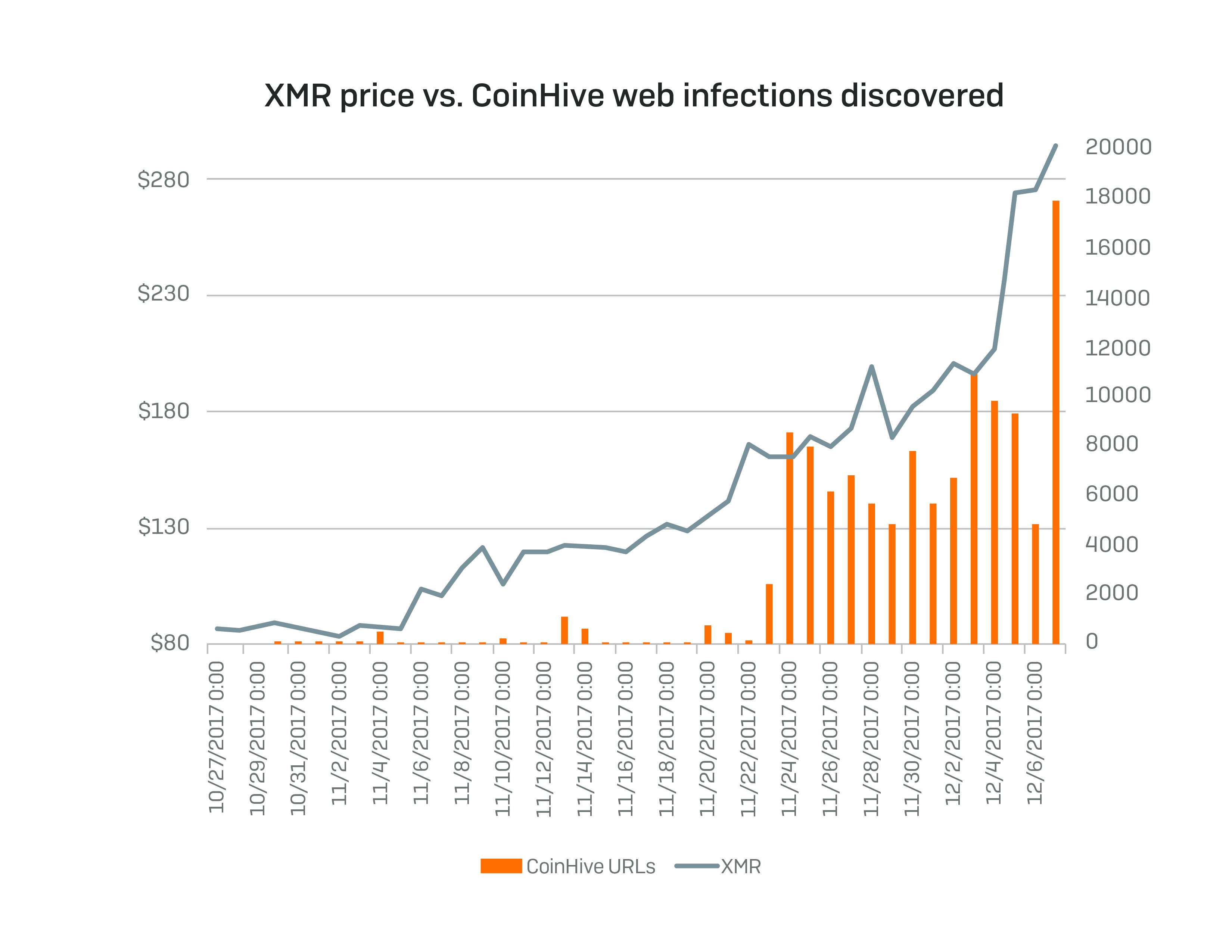
Coinhive markets itself as an alternative source of revenue to advertisements.
Infamous torrent site The Pirate Bay is among those to have used its code and neglected to tell visitors it was using their browsers to mine cryptocurrency. The site embedded Coinhive JavaScript code on search pages to mine for Monero.
It’s this sort of activity that is leading Sophos to take a tougher stance.
From PUAs to malware
As noted above, we previously detected cryptominers as PUAs (Potentially Unwanted Applications), which meant no automatic cleanup. Admins were instead presented with alerts for PUA detections and could manually choose from three possible options: Cleanup, Authorize or Acknowledge.
For Coinhive and equivalent web-based JavaScript miners, the situation is now different. Customers using Web Control will now see something like this off the bat: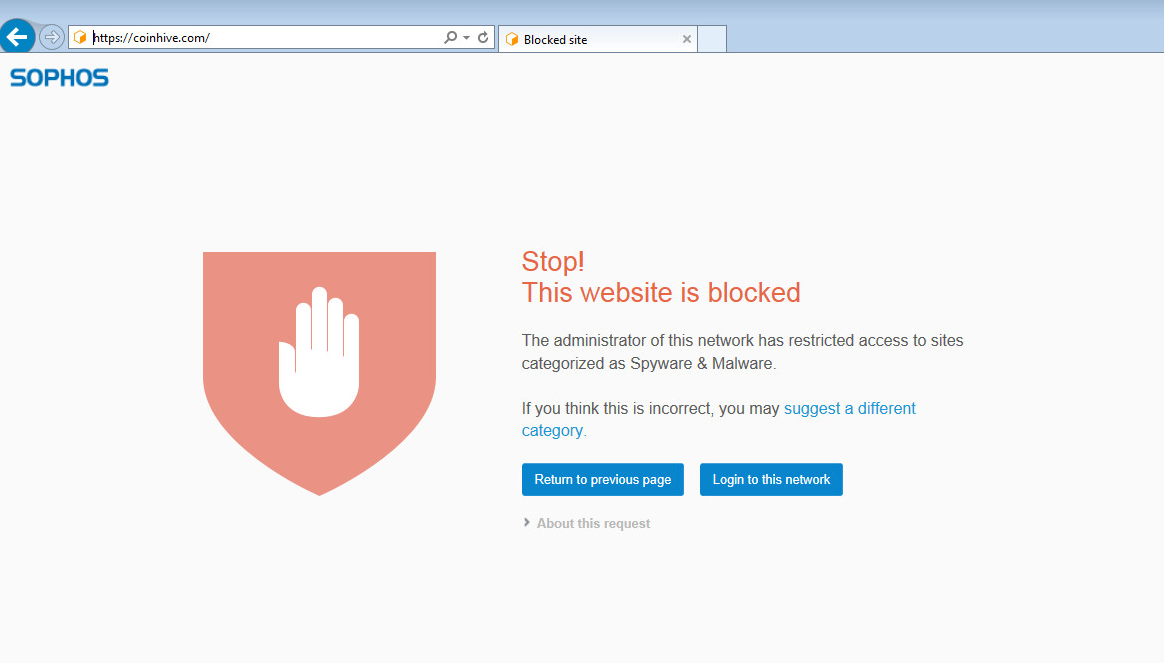
What to do
Sophos customers can block cryptominers by using the Web Control features included in our Endpoint and Network Protection products.
Once enabled, blocking websites categorized as “Hacking” will stop users from visiting the offending sites.
Customers can read our Knowledge Base article to find out more about how to block JavaScript cryptominers.

Tom
I like the article, I do not like the headline. I think it is wrong.
I hate ads-contaminated Websites. Script-based Crypto-mining might be an alternative to paid ads. I would definitely prefer an ad-free Website Crypto-mining with some defined percentage of my CPU against a standard Website full with ads today. Yes, we are not there. We would need Crypto-mining services paying Websites, while the Website hosts their Crypto-miner. And get rid of the ads. Of course we need the user agreement, similar to accepting proxies today. But the headline somewhat excludes this excellent opportunity to get what I think could be a better Cyberspace.
Bill Brenner
Hi, Tom. We absolutely understand the idea that cryptomining programs can be a viable alternative income source to ads. And in a perfect world that’s how it would be. However, this is a case where Sophos had to make a decision to protect its customers. In the past month, we’ve seen a steady increase in JavaScript cryptominers that run silently on websites and take from the user without asking first. For us, the key is simple: The user must be asked for permission before their computers can be used in this manner. Anything else is a deception and amounts to theft of resources. The key going forward is that cryptominers be used in an open and honest way.
Shadow
this is why i have a script running coinhive on my forum under /miner.php it explains this,
” Mining on KingForums will grant you Teir upgrades in return of your computing power, more specifically your CPU’s processing power. The service which we use to mine is called Coinhive and it mines the cryptocurrency Monero.
Using this miner might shorten the lifespan of your computer and raise your electricity bills.”
spacemyths
Hello Bill, May you please name top 5 cryptomining malware that are currently most dangerous to normal internet users?
Bill Brenner
Hi, there. We don’t have a top 5 list per se, but these are the variants we’re seeing most often:
XMRig miner
XMR-Stack Miner
WannaMine
CoinHive
CoinMiner