A few years ago, fake support call scams were one of the most likely cybercrimes that would reach out and touch you at home.
And, boy, how those guys used to reach out.
Boiler rooms full scammers would make cold call after cold call, ploughing day and night through lists of phone numbers to scare victims into paying up for technical support they didn’t need for malware infections they didn’t have.
Here’s how we summarised the MO of these scummy scammers back in 2014:
The crooks call up and say they’re from “Microsoft” or “Windows”; tell you they’re following up reports of malware activity coming from your computer; convince you that you are infected; and charge you a fee of about $300 to sort you out.
All a pack of lies.
They’re not legitimate IT support technicians; they have no idea whether there is malware on your computer or not; the “evidence” they come up with is harmless and could be found on an uninfected computer; and the $300’s worth of fiddling around they do is simply $300’s worth of fiddling around.
You could achieve the same technical outcome for yourself by doing nothing at all – LITERALLY nothing.
If you didn’t hang up right away – or even if you did – then the crooks would often come back, sometimes calling again and again, ramping up the pressure, the fear and the threats in the hope that you’d eventually cave in.
For better or worse, technical support scams don’t make the headlines as much as they did.
Firstly, other, more directly pernicious threats such as ransomware have understandably grabbed our attention instead; secondly, this fake tech support “business” has become slightly more sophisticated.
We presume that more and more people have become less and less tolerant of cold calls, thus reducing the hit-rate of scammers who rely on contacting you first.
In recent years, support scams usually start from a website that’s poisoned with dubious advertising.
You’ll often get a pop-up a warning urging you to phone the crooks (typically via an in-country tollfree number to add legitimacy), so you end up pre-selecting yourself as a potential victim.
Well, don’t get fooled this Christmas, because the scammers are still hard at it.
Here’s one we saw over the weekend, while reading a legitimate news site, albeit not a mainstream one.
We clicked on one of those “you’ll never believe what happened next” stories (for research purposes only, of course!), and then mis-clicked (honestly!) on an ad simply by tapping the trackpad by mistake just short of our intended on-screen destination:
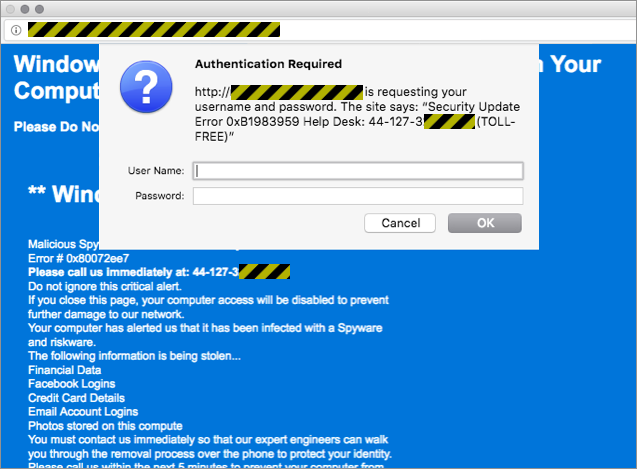
This one even uses an automatic voiceover, reading out a warning in plummy-sounding English to drive the point home:
Listen to the pack of lies spouted in this scam
The crooks haven’t lined things up perfectly, as you’ll probably realise, especially if you’re a native speaker of English who currently lives in the UK.
For example:
- The automatic text-to-speech conversion has messed up the pronunciation of some of the words. Pornography comes out as poor and/or graphic. The word logins is spoken with a soft -g-.
- The phone number is written US-style, wrongly assuming a three-digit area code. The dialling code for this number would be grouped as four digits, like this: +44-1273-XXX-YYY.
- The number isn’t toll free, as claimed. Numbers starting +44-1237 are paid calls to the Brighton area on the South coast of England.
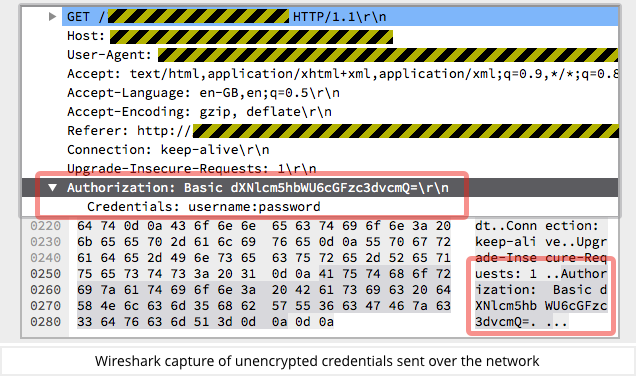
- The password request is superfluous, and so it should stand out as suspicious. Also, this is not an HTTPS page, so if you put in your password, not only will the crooks get it, but anyone else on the same network will be able to see it, too.
But these are details that are easy to overlook; the crooks often get the details right, anyway; and plenty of legitimate websites make similar mistakes.
What to do?
We haven’t called the number shown above; we don’t intend to; and we recommend that you don’t, either, no matter how much fun you think you can have messing with the criminals.
They’re crooks – why engage at all, especially when you might accidentally give something away about yourself in the process?
This festive season, even if trying new websites, buying from new vendors, contacting people you haven’t heard from in ages, and otherwise living a larger life online that you have all year…
…don’t let anyone, especially someone you don’t know, and whom you didn’t ask for help, pressurise you into doing, saying, posting, calling, texting, clicking or buying anything.
If you’re worried, ask someone whom you know and trust for help, face-to-face.
If you’re one of those “askees” who end up stuck with friends-and-family technical support over the holidays, please try to do it with good grace, to keep your loved ones out of the clutches of fake support sleazebags like the ones shown here.
If in doubt, STOP.THINK. And only then CONNECT.

Tom
A couple of questions: Do add-ons like No Script in Firefox block these pop-ups from occurring?
Are drive by viruses still a threat, if you use an up to date browser? Thank you.
Paul Ducklin
Generally speaking, this sort of scam does use JavsScript somewhere, so NoScript will help. (This one wasn’t a popup, it was a page served up directly by a rogue ad/link, so IIRC the background text and phone number would show up anyway, NoScript or not.)
As for drive-by malware, where just visiting a page triggers an exploit that loads malware without any popup or warning – yes, that’s possible even with a bang-up-to-date browser, but only if the crooks have a totally unpatched exploit (what’s known as a zero-day). Thanks to aggressive attitudes to security by the browser makers, plus bug bounty programmes that encourage the finding and reporting of bugs by third parties, zero-days aren’t easy or cheap to acquire these days…
…so, patch early, patch often! Most drive-by attacks rely on old exploits that only work on computers that haven’t been patched recently (XP, here’s looking at you :-)
Tom
Thanks Paul.
0laf T. Hairy
And you’ve reported this to the police via the Action Fraud website, yes?
One of the things the police are struggling with is a lack of reporting; OK, plus resources to follow up, but they won’t get the resources without reports to produce the stats to show the need.
And you’ve reported to the legitimate site hosting the malicious advert so they can remove it and stop anyone else getting scammed?
These “XYZ will hate that you know this!”, bottom crawling clickbait adverts don’t half wind me up anyway.
Paul Ducklin
As it happened, I didn’t report the dodgy advert for the simple reason that by the time I had taken that screenshot I had inadvertently closed the window in which it all started, and I didn’t have any of the intermediate links to tie it all together. In short, the sequence was news site X -> link-promoting service Y -> advert Z -> scam at site Q. All I know right now is Q (and that’s the crooks).