Three seasons into Mr. Robot, we can easily recognize callbacks to hacks we’ve seen in previous episodes and seasons. And by now, this show has also made it really clear that no tactic, no matter how seemingly ironclad, is a guarantee – when the stakes are high, every move means measuring risk and reward.
In this week’s episode, we also saw some hacks and security concepts that exemplify how sometimes the very unlikely is still possible, and how – even in hindsight and with entirely new information – you might make the same decision twice.
WARNING: SPOILERS AHEAD – SCROLL DOWN TO READ ON
RFID skimming: reading your badge at a distance
RFID chips can be found in a number of very important things that many of us have, like passports, debit and credit cards, train tickets and office badges, so any threat that puts this data at risk gets a lot of attention.
RFID stands for Radio Frequency Identification, and it works wirelessly. The RFID reader emits a magnetic field that generates just enough current to power up a coiled antenna attached to the chip; the magnetic field is then used to transmit data back from the card to the reader. In theory, then, you can skim RFID data off people’s cards just by getting close enough (typically from a few feet to a couple of inches, depending on the type of chip in use).
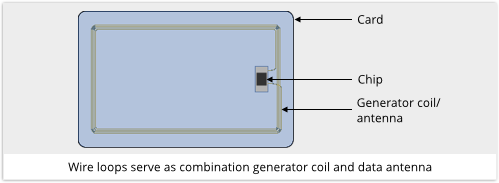
However, RFID skimming takes a lot of effort, you have to be there and close-up every time [*], and there are much easier ways to gather valuable data in greater volumes, so RFID skimming isn’t currently a big threat to the general, walking-around public.
But RFID skimming is a real and credible threat when it is targeted, which is exactly what we saw in tonight’s episode when Darlene repeatedly tried to get Dom’s FBI badge data by brushing up against Dom (and her badge) in the bar. We briefly saw that Darlene was using a real tool called RFID Thief. Had she nabbed the data from Dom’s badge, it is credible that she could have managed a way into to Sentinel.
For whatever reason, Darlene wasn’t able to get a read on the badge, and I didn’t see any obvious RFID shielding on Dom’s badge, so perhaps it was a decoy?
I didn’t get the impression Dom knew what Darlene was up to right away, so I’m skeptical there, but tools won’t always work 100% of the time in any case. Good thing Darlene had a backup plan… but bad luck that it didn’t matter in the long run.
[*] RFID skimming is not to be confused with ATM skimming, which reads magstripe data off contact-based cash cards at the point they’re inserted for use.
SOCs and Hindsight
The opening scene, which gave us some season one nostalgia for Gideon perhaps, shows E Corp and Allsafe in discussions about doing business together. To jog your memory, E Corp is the Typical Hugebig Company and Allsafe is the external vendor they hire to manage their security.
After the negotiation’s complete, we see Tyrell tell Price briefly that he’d rather not use an external security firm like Allsafe and would prefer to establish his own security operations center (or SOC) internally. When Price dismisses his concerns, Tyrell says – almost comically understated, this line – “I just hope it doesn’t come back to haunt us.”
Arguably a company like E Corp should be able to pull together its own security team internally – they have a lot at stake and they have the money to hire. But deciding whether to hire an outside security firm or build one in-house is a huge decision that many companies of all sizes struggle with. There are just as many decisions for and against on either “side,” and as much as the common thinking is that it’s cheaper to hire someone outside the company, there’s a lot more that goes into the in-house versus outsourcing decision.
Tyrell’s line about not regretting their decision was a key plot device, but in the security context, it’s worth pointing out that he could have had his wish and built his own SOC internally and still had issues thanks to the inside threat. (There’s no reason why Elliot couldn’t have been hired by E Corp directly if Allsafe wasn’t in the picture.) Despite the Captain Hindsight-esque line, this was never going to be an easy decision.
Other notes:
- Did Elliot use the same car hack on Irving that Irving did in this season’s opener? That was a pretty cute callback. Irving seemed to know exactly what was going on as it happened and was already very over it.
- Price’s line to Mr. Robot was a great statement on perception vs. reality in cybercrime: “Catastrophes don’t happen because of lone wolves like you, they happen because men like me allow them to happen.” Mr. Robot and Elliot represent the old stereotype of the brilliant hacker in the hoodie; the reality is most cybercrime nowadays is more pedestrian, with crooks often using well-known tools and techniques to break in to anyone who’s behind the curve on patching and protection.
- In the show during a news segment you can hear a news anchor refer to the 2nd stage of the five/nine attack as a “cyberbombings,” a term I haven’t really heard before. (I’ve heard of “cyberbombs” in reference to really big, sudden, targeted cyberattacks against a virtual target, but not in the context of actual physical damage or bombings.) It makes sense – a cyberattack used to bomb 71 buildings, hence cyberbombing. But I really hope this term never ever joins the IRL lexicon.
It’s the season finale next week, which means I’ll be wrapping up these reviews until next year (and going to bed at a more reasonable hour). Still, I can’t help but wonder what we’re in for next week: Elliot seems to think he has things with Dark Army all neat and tidy with a bow on top. “And now I own Dark Army,” he said. Especially after all we’ve seen these past three seasons, that seemed way too easy.
There’s no way Dark Army would just grab a USB key from Elliot and run it sight unseen, there’s no way they’d underestimate him that badly. So how is it that Elliot would underestimate them to assume they’d get pwned so easily? I really hope we don’t have to wait until next season to get an answer.

Laurence Marks
Maria wrote “RFID stands for Radio Frequency Identification, and it works wirelessly. The RFID reader emits a magnetic field that generates just enough current to power up a coiled antenna attached to the chip; the magnetic field is then used to transmit data back from the card to the reader.”
Not quite, Maria. You can’t transfer enough power wirelessly to the passive RFID chip that way. (Power falls off as the square of the distance.) What they do is much more clever.
The RFID chip receives the probe from the RFID reader and charges up using its tiny internal antenna. (Google for images.) The reader continues to transmit a steady signal. Once charged, the RFID chip periodically short-circuits its antenna in a coded sequence corresponding to its RFID code. The RFID reader senses the changing load, heavier when it’s transmitting into the short-circuit and captures the coded sequence.
Paul Ducklin
Well, the chip (in the sort of chips we are talking about) has no battery, yet it can receive data, perform cryptographic calculations, and supply replies… all from power extracted from the magnetic field generated by the reader. And it’s that same magnetic field that is used for wireless data transmission.
Seems like that’s what you’re saying. If the magnetic field from the reader can’t induce enough power to fire up the RFID chip…
…where does the energy come from?