Popular photo-sharing site Imgur is the latest social media platform to have suffered a massive data breach without realising it.
On November 23, we were notified about a data breach on Imgur that occurred in 2014. While we are still actively investigating the intrusion, we wanted to inform you as quickly as possible as to what we know and what we are doing in response. More: https://t.co/qElAetGVIc
— Imgur (@imgur) November 25, 2017
According to the Imgur company blog:
Early morning on [2017-11-24], we confirmed that approximately 1.7 million Imgur user accounts were compromised in 2014. The compromised account information included only email addresses and passwords. Imgur has never asked for real names, addresses, phone numbers, or other personally-identifying information (“PII”), so the information that was compromised did NOT include such PII.
You read that correctly: the crooks have had the data for at least three years, but only let the secret slip recently.
Imgur says it found out when an “mail was sent to [us] by a security researcher who frequently deals with data breaches”.
If you’re wondering if they’re referring to well-known data breach discloser Troy Hunt, well, yes, that’s who it was.
I want to recognise @imgur's exemplary handling of this: that's 25 hours and 10 mins from my initial email to a press address to them mobilising people over Thanksgiving, assessing the data, beginning password resets and making a public disclosure. Kudos! https://t.co/jV8MDscXLT
— Troy Hunt (@troyhunt) November 25, 2017
Hunt has done on the record to say he thinks Imgur handled this well – he chose the word “exemplary” – given that it investigated and responded over the Thanksgiving weekend.
Sadly for Imgur, its processing and storage of users’ passwords was far from exemplary: the company has admitted that until last year (2016), it hashed your password simply by using SHA-256, rather than using a salt-hash-stretch process such as PBKDF2, bcrypt or scrypt:
We have always encrypted your password in our database, but it may have been cracked with brute force due to an older hashing algorithm (SHA-256) that was used at the time. We updated our algorithm to the new bcrypt algorithm last year.
The description of bcrypt as “new” is interesting, given that the algorithm was first published in 1999.
Straight hashing of passwords is way better than storing passwords in plaintext, because at least a crook who steals the database can’t simply read off everyone’s password.
The crooks have to try a whole dictionary of likely passwords, which certainly slows them down.
But without a salt – a unique, random string added to a user’s password before hashing it – you can predict in advance that everyone with a password of, say, password will have a SHA-256 hash of 5e884898da28047151d0e56f8dc6292773603d0d6aabbdd62a11ef721d1542d8.
In other words, you can hash each word in your dictionary and if anyone in the password database matches that hash, you’ve cracked their password.
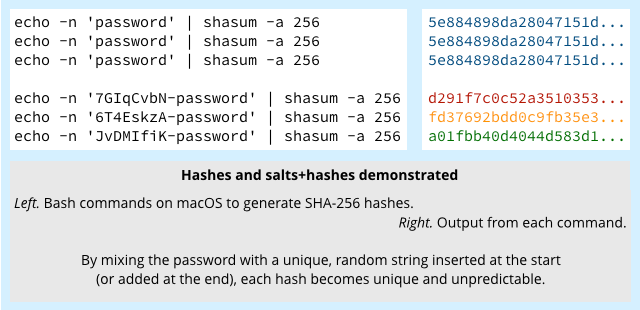
With a salt that’s unique for each user added into the cryptographic mix, you need to hash each word in your dictionary for each user, which is a much more onerous task – and can’t be done in advance, either.
And stretching means that you don’t just do one loop of your hashing algorithm, but thousands of loops, or tens of thousands, or even more.
This slows down dictionary cracking linearly – there are just under 10,000 hours in a year, so slowing down your password hash check by a factor of 10,000 means that the crooks would take a year to mount an attack that would otherwise take them just one hour.
Increasing the number of loops needed to compute and check a password hash will, obviously, slow down legitimate logins slightly, but not to the extent that users will care, or even notice, given that they don’t need to login billions – or even hundreds – of times a day.
What to do?
If you’re an Imgur user and your email address was on the list of accounts known to have been breached, Imgur will notify you, and force you to change your password next time you login (if the crooks haven’t logged in and done so already).
Don’t forget, however, that the crooks have already had three years to crack your password and meddle with your account, and cracking passwords was a lot easier than it should have been due to Imgur’s poor password handling.
And that leaves you with the question, “Do I still want to keep on using Imgur?”
For example, Naked Security’s Mark Stockley closed his Yahoo account immediately after finding that it had committed a similar sin to Imgur, namely choosing a password hashing-and-storing process that was a decade behind the security curve.
What else, reasoned Mark, might Yahoo have done sloppily that he didn’t know about?
As Troy Hunt says, the company reacted quickly and didn’t try to make any excuses, so our inclination is to give Imgur the benefit of the doubt, at least for now.
Nevertheless, you’ll have to make up your own mind on whether to close your Imgur account – a decision that will depend, at least in part, on how much you get out of the service.
If you’re a developer, please read our article How to store your users’ passwords safely, just to make sure this doesn’t happen to you.
