It’s Microsoft patch time again, which this month sees admins coming face-to-face with 81 CVE-ranked vulnerabilities, 27 rated “critical”, with an interesting zero-day for added excitement.
Assessing which of these patches should be the priority will depend on your perspective. It’s always tempting to start with the headline zero-day, which this month is an interesting example in a year that has, so far, seen 17 in Microsoft’s products.
Designated CVE-2017-8759, it’s a serious remote code execution flaw in .NET, researchers noticed being exploited through malicious Microsoft Office RTF documents intended for Russian-speaking targets. Other document types probably featured too.
The intrigue is that the exploit was noticed in July being wielded by what is surely the world’s most notorious commercial spyware, FinSpy, aka FinFisher or WingBird.
Ostensibly sold to governments as “lawful intercept” software for spying on criminals, it’s also widely known to have been used to spy on citizens for political purposes. It’s a bit of a chameleon, and in 2013 was accused of trying to spread itself by masquerading as Firefox, which ended with Mozilla sending makers Gamma International a cease and desist.
The chances of the average Naked Security reader encountering FinSpy is small – it’s targeted malware – but that shouldn’t stop everyone applying the patch for it as soon as possible.
Just to underline the importance of this, earlier this year FinSpy was outed for exploiting another zero-day, CVE-2017-0199, which was simultaneously being used by the Latenbot crimeware. The message is clear: a zero-day is bad news and countering it should always be a high priority.
Office 365 already mitigates the exploit associated with the newer zero day for customers using the suite’s Advanced Threat Protection (ATP) but that’s really a secondary defence.
As a background aside, the number of zero-days uncovered in Microsoft products has been pretty stable in recent years at 15 in 2013, 12 in 2014, 13 in 2015, and 11 in 2016. This year looks as if it might tick up to as many as 20.
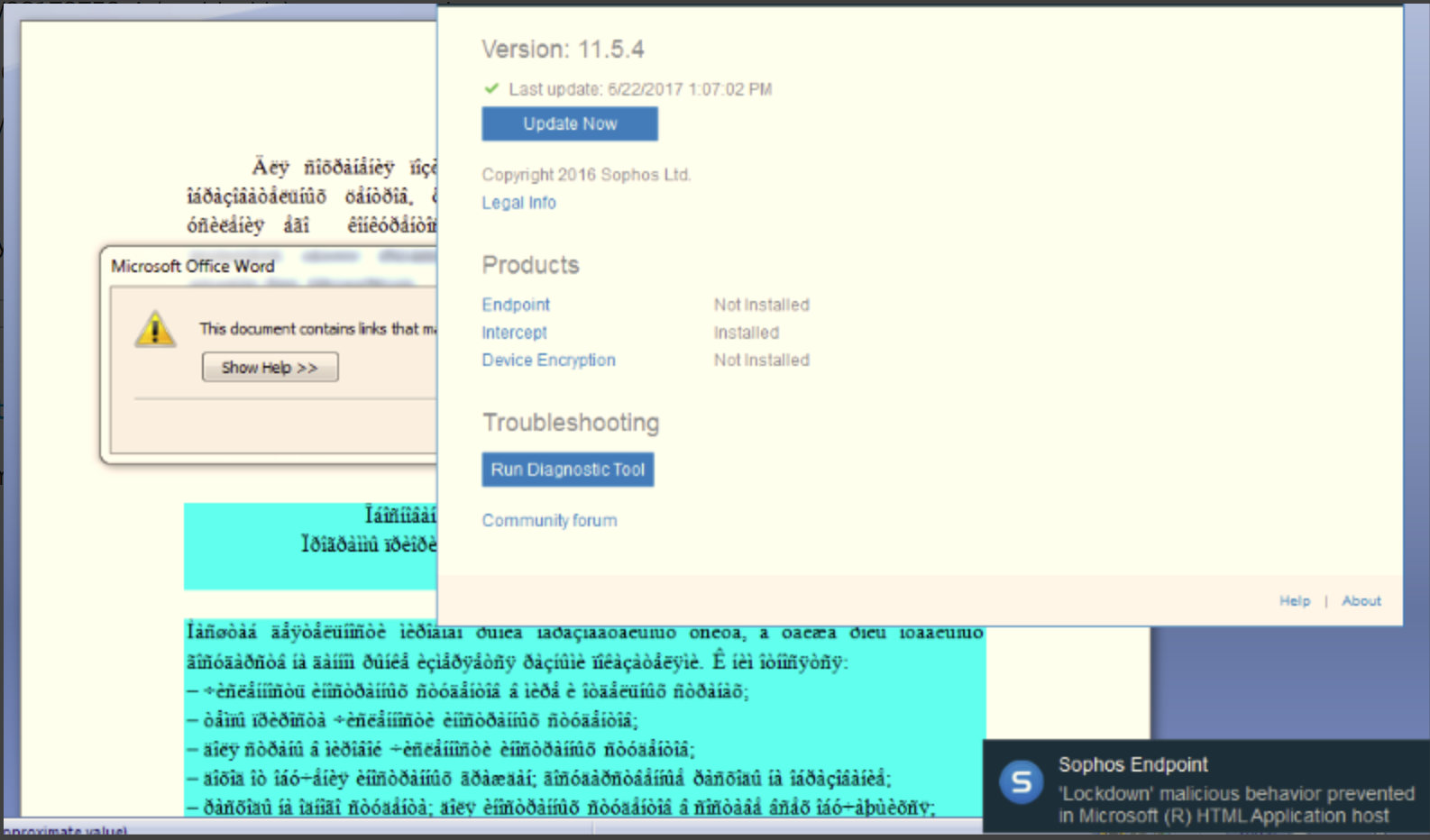
Status of Sophos customers
Some Sophos customers have asked if they are protected from this latest threat. The answer is yes. For antivirus, SophosLabs detects the offending RTF files as Troj/RTFDrp-BH and Troj/20178759-A. They detect the FinSpy payload as Troj/Wonton-ABX.
Intercept X blocks the attack via its application lockdown function, as seen here:
Other zero days
The bulletin lists three other important zero-days that haven’t (as far we know) been exploited, which are: CVE-2017-8723 (an Edge browser bypass loading through malicious a website), CVE-2017-9417 (a Broadcom chipset flaw relating to HoloLens), and CVE-2017-8746 (a bypass of Device Guard affecting PowerShell sessions).
‘BlueBorne’ super-flaw
Another worth noting is CVE-2017-8628, the ‘BlueBorne’ Bluetooth driver flaw, which was actually quietly patched in July but which the company has only now mentioned. This is really the Windows element of a clutch of vulnerabilities affecting Bluetooth across a range of platforms.
The bulletin total includes one Adobe Flash vulnerability across a wide range of Microsoft products. There are also 14 affecting Edge, three affecting Internet Explorer, 11 for Office, nine different aspects of Windows’ graphics components, and seven Hyper-V, with an assortment of flaws in the kernel.
Most of the worst Remote Code Execution (RCE) action is in the Edge and IE browsers, and the scripting engine that links these to Office, which along with the zero days should be the focus of attention.
The important bulletins covering critical vulnerabilities are MS17-006, MS17-007, MS17-008, MS17-009, MS17-010, MS17-011, MS17-012, MS17-013 and MS17-023.