Thanks to Dorka Palotay of SophosLabs for her behind-the-scenes work on this article.
Locky was once among the most dominant strains of ransomware. Over time, it receded from view, replaced by ransomware such as Cerber and Spora. But in the last couple of weeks, Locky has returned.
Last week it sported a new extension: .diablo6. This week researchers are seeing more new variants, now with a .lukitus extension. SophosLabs researcher Dorka Palotay said the new variants perform the usual Locky behavior:
It is spread by spam email and comes with a .zip attachment with a .js file inside (e.g. 20170816436073213.js). It downloads the actual payload, which then encrypts the files.
Email characteristics, payloads
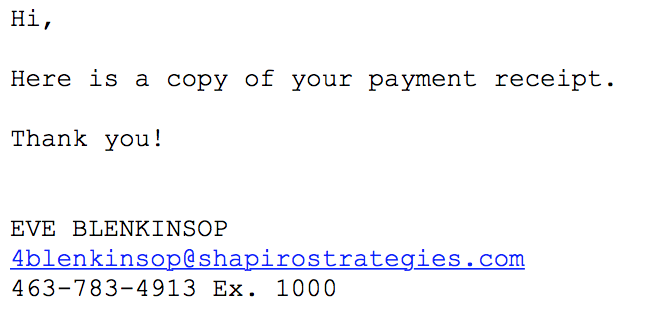
The .lukitus variant comes with email subject lines like “PAYMENT” and the following body content:
The Diablo variant used the body content “Files attached. Thanks” and the sender’s email address had the same domain as the recipient’s. The emails came with the .zip attachment “E 2017-08-09 (957).zip”, which contained a VBScript downloader called “E 2017-08-09 (972).vbs”. The script would then download the Locky payload from an address ending with /y872ff2f.
The .lukitus version connected to its command-and-control server via these addresses:
- hxxp://185[.]80[.]148[.]137/imageload.cgi
- hxxp://91[.]228[.]239[.]216/imageload.cgi
- hxxp://31[.]202[.]128[.]249/imageload.cgi
The diablo6 version connected to its command-and-control server via these addresses:
- 83.217.8.61/checkupdate
- 31.202.130.9/checkupdate
- 91.234.35.106/checkupdate
Defensive measures: malicious attachments
Sophos is protecting customers from the latest Locky campaigns. But it helps to keep the following advice top of mind:
- If you receive an attachment of any kind by email and don’t know the person who sent it, DON’T OPEN IT.
- Configure Windows to show file extensions. This gives you a better chance of spotting files that aren’t what they seem.
- Use an anti-virus with an on-access scanner (also known as real-time protection). This can help you block malware of this type in a multi-layered defense, for example, by stopping an initial booby-trapped PDF or HTA file.
- Consider stricter email gateway settings. Some staff are more exposed to malware-sending crooks than others (such as the order processing department), and may benefit from more stringent precautions, rather than being inconvenienced by them.
Defensive measures: ransomware
The best defense against ransomware is not to get infected in the first place, so we’ve published a guide entitled How to stay protected against ransomware that we think you’ll find useful:
You can also listen to our Techknow podcast Dealing with Ransomware:


Johnny
Country blocking implemented on the firewalls stops the virus from being able to get to command and control outside the US so it cannot download encryption keys to encrypt documents. Local virus defs on the PC eventually catch up and kill it before it gets the keys to encrypt.