Less than a month after WannaCry hijacked hundreds of thousands of computers across the globe, those attending InfoSec Europe 2017 are grappling with lingering questions about how it spread so rapidly and what comes next.
The conference agenda is packed with talks and exhibits on the subject.
Sophos worked around the clock following the outbreak to analyze what made WannaCry tick and turn the lessons into a more ironclad defense. To help InfoSec attendees along in their discussions, we offer the following perspective.
Sophos CTO Joe Levy recently showed how it spread on the back of an NSA exploit for Microsoft Windows SMB, which was leaked by the Shadow Brokers hacking group. He gave the technical perspective on what happened, how the attack worked, the timeline of events, how this latest attack can be prevented, and what to do now. You can watch the entire presentation on Sophos’ webinar page.
Sequence of events
The story of WannaCry began sometime between 2013 and 2016, when the NSA’s exploit tools were stolen. In August 2016, Shadow Brokers revealed itself, and six months later announced the auctioning of NSA tools it had acquired.
Learning that the exploits targeted Windows SMB, Microsoft released a patch in March. When the outbreak hit two months later, it was clear that organizations and individuals had either neglected to apply the patch or were using outdated versions of Windows.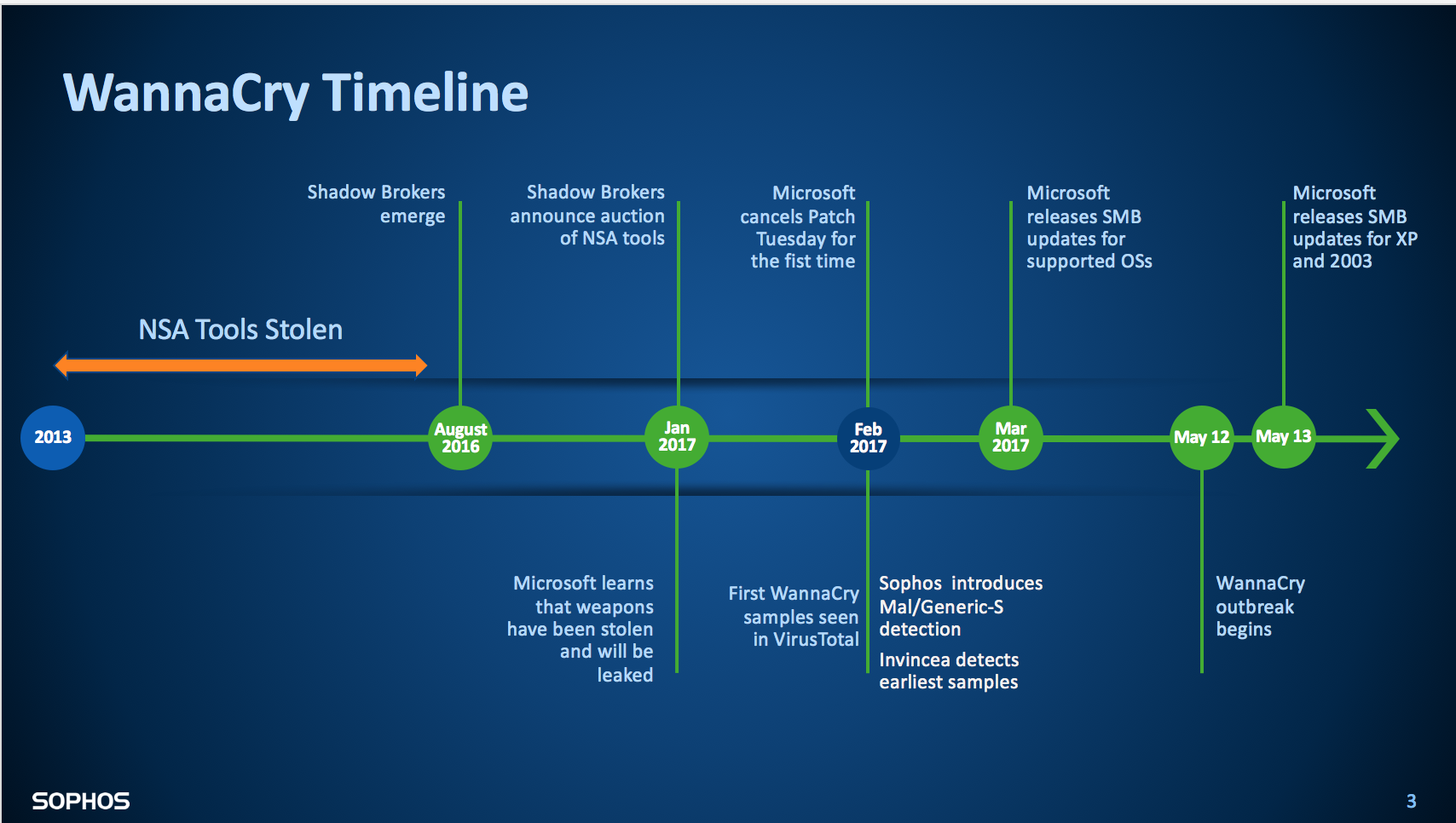
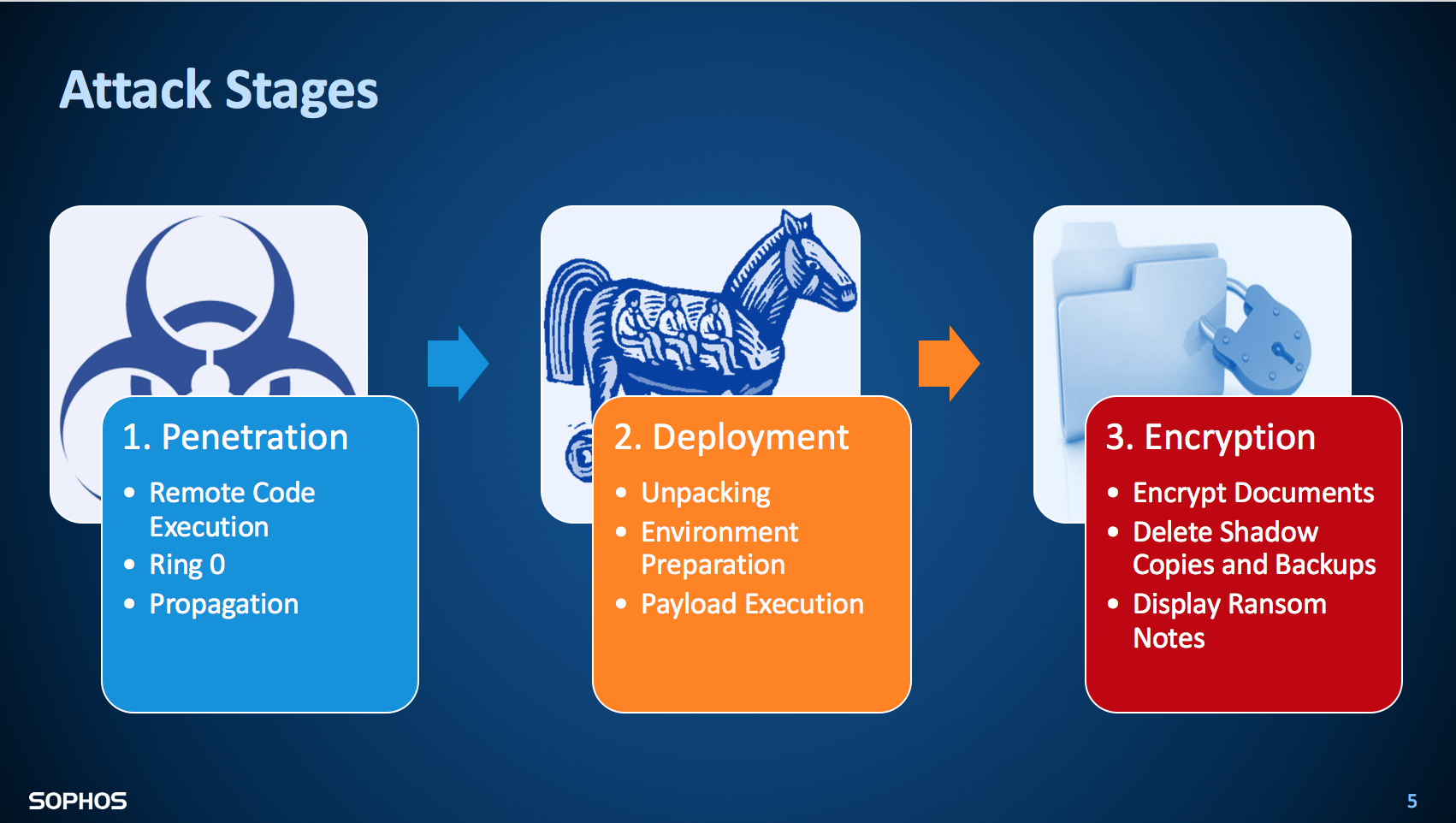
The investigation revealed a three-stage attack, starting with remote code execution and the malware gaining advanced user privileges. From there, the payload was unpacked and executed. Once computers were hijacked, it encrypted documents and displayed ransom notes.
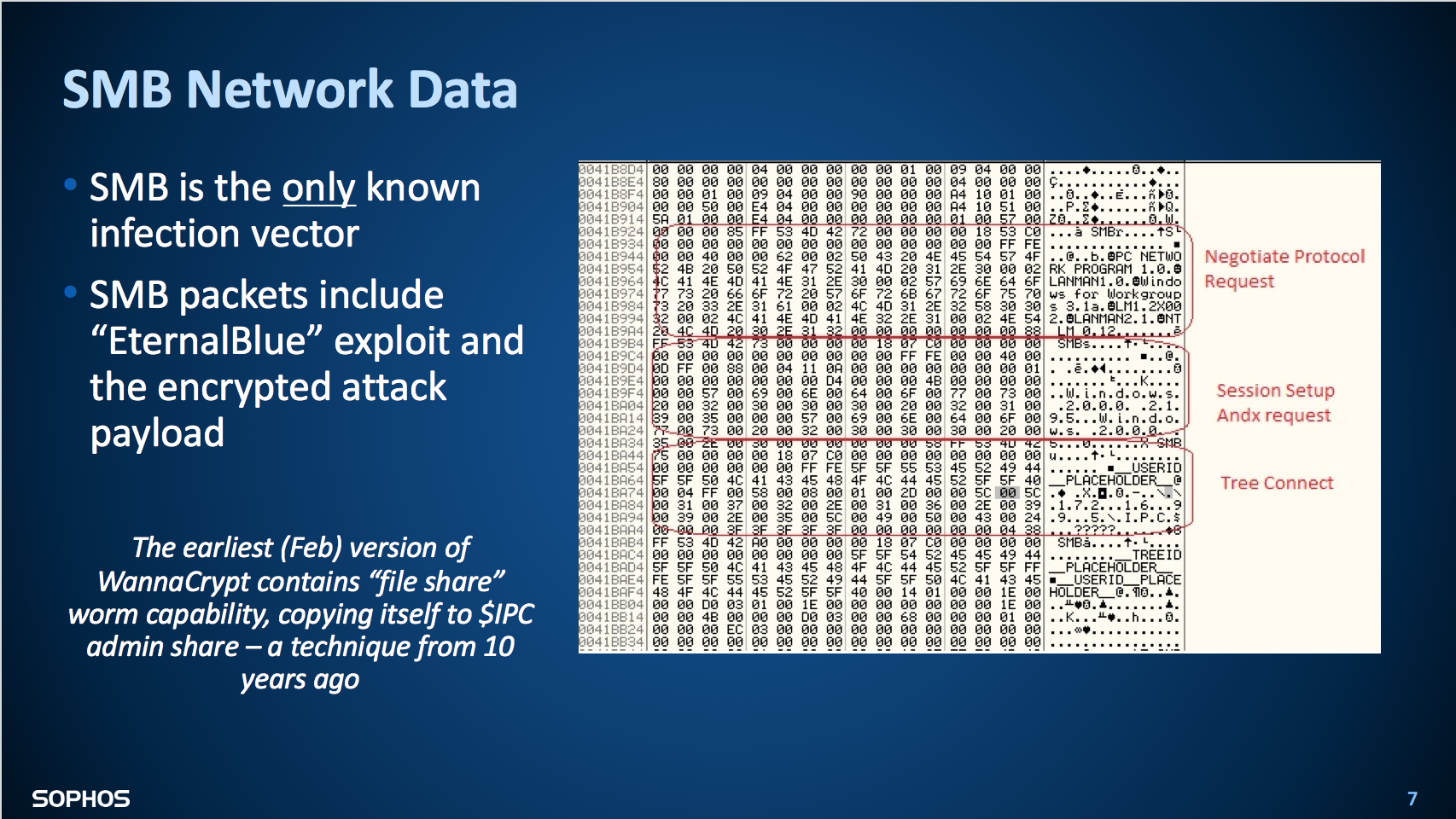
SophosLabs and others determined that this was no typical ransomware attack. True, that was the payload, but it didn’t spread via the usual tainted email links and attachments. It spread with the classic precision of a worm, exploiting the flaw in the Windows Server Message Block (SMB) service, which Windows computers use to share files and printers across local networks. Microsoft addressed the issue in its MS17-010 bulletin.
The worm generated random IP addresses. Once the IP addresses were defined, the worm sent malicious SMB packets to the remote host, spreading itself.
Lessons learned
James Lyne, Sophos head of security research, offered this advice yesterday at InfoSec:
- Don’t get distracted by the “big, sexy talks” like government-sponsored attacks and nation-state cybercrime. They are interesting topics to be sure, but …
- Stay grounded in the opportunistic attacks that target businesses every day, like ransomware and the recent WannaCry outbreak.
- Focus on the security basics — the simple things like using endpoint security, staying on top of patching and using strong passwords.
That advice could have saved organizations from a lot of pain last month. Paying attention now could help them prepare a much stronger defense against attacks to come.
Of course, acting on advice is often easier said than done. Some organizations have been criticized for being slow to patch or use the latest Windows versions. But slow patching or the use of outdated versions of Windows wasn’t entirely the result of laziness or apathy.
It’s long been the case that IT shops hold back some patches because they need to tweak their systems for compatibility. Otherwise, they risk deploying a patch that breaks other programs. Meanwhile, some organizations have continued to use old versions of Windows because they lack the financial and human resources to upgrade, and their legacy systems simply aren’t yet equipped to work with the likes of, say, Windows 10. There are other reasons, but those are two big challenges.
Hardships aside, Lyne said organizations can no longer afford the status quo. There’s already evidence of more trouble ahead, including:
- The emergence of a ransomware-as-a-service (RaaS) market on the dark web that even includes a rating system where criminals earn stars for stealth, evil, value and price.
- The determination of Shadow Brokers to launch a monthly subscription service for more zero days. By making these tools more readily available, future WannaCry-style outbreaks are a lot more likely.
Lyne told attendees:
When we look at some of these cyber-attacks, we’re talking about failures verging on negligence. We can’t rely on continued tools to help us decrypt ransomware – WannaCry is a wake-up, but it could be worse.
Parting advice
Since WannaCry, we’ve offered the advice below. To guard against malware exploiting Microsoft vulnerabilities:
- Stay on top of all patch releases and apply them quickly.
- If at all possible, replace older Windows systems with the latest versions.
Since the worm payload was ransomware, a reminder on defenses for that are in order:
- Back up regularly and keep a recent backup copy off-site.There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
- Be cautious about unsolicited attachments.The crooks are relying on the dilemma that you shouldn’t open a document until you are sure it’s one you want, but you can’t tell if it’s one you want until you open it. If in doubt, leave it out.
- Use Sophos Intercept X and, for home (non-business) users, register for Sophos Home Premium Beta, which stops ransomware in its tracks by blocking the unauthorized encryption of files.

Gary
I know it’s certainly not infallible, but, Linux. It has all of the tools that I use on a daily basis for work, so it’s perfect for my needs. That being said, I do use Windows on occasions (usually virtually), and, of course, while gaming. I keep their services trimmed, patched, and internet activity to a minimum. It’s really about the only way that I’ve found that works best for *me*. Sorry… websites scare me, particularly while using Windows. hah!