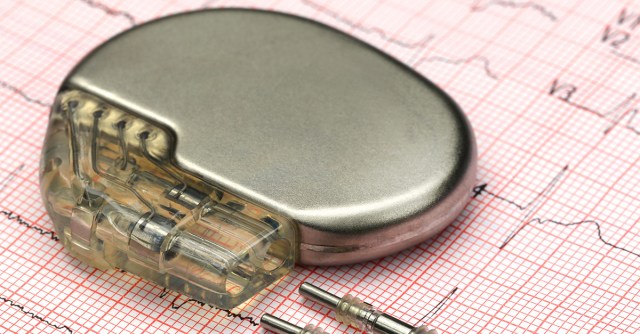
There are more than 8,000 vulnerabilities in the code that runs in seven analyzed pacemakers from four manufacturers, according to a new study.
And that’s just a subset of the overall medical device scene, in which devices have scarcely any security at all. A second, separate, study that looked at the broader market of medical devices found that only 17% of manufacturers have taken serious steps to secure their devices, and only 15% of healthcare delivery organizations (HDOs) have taken significant steps to thwart attacks.
Cyber-tampering with medical devices such as insulin pumps or pacemakers can seem far-fetched – the product of researchers’ wild imaginations and their theoretical scenarios, unlikely to happen in the real world.
Case in point: even after the US Food and Drug Administration (FDA) and the Department of Homeland Security (DHS) released advisories about potentially life-threatening bugs in cardiac monitoring technology from St Jude Medical — on the same day in January 2017 that St Jude issued security fixes — St Jude shrugged off what it called “extremely low cyber-security risks.”
St Jude’s attitude was far from surprising, given that the company had sued IoT security firm MedSec for defamation after MedSec published what St Jude said was bogus information about the bugs … as in, the same bugs it went on to fix.
Companies like St Jude may shrug off the risks, but according to the Ponemon Institute — which conducted research into medical device security that was sponsored by the Internet of Things (IoT) security company Synopsys — patients have already suffered adverse events and attacks. Its findings:
- 31% of device makers and 40% of HDOs surveyed by Ponemon Institute said that they’re aware of patients suffering from such incidents.
- Of those respondents, 38% of HDOs said they were aware of inappropriate therapy/treatment delivered to patients because of an insecure medical device.
- Another 39% of device makers confirm that attackers have taken control of medical devices.
These are the causes of the adverse events or harm to patients:
Granted, these things aren’t easy to secure. A majority — 80% — of medical device manufacturers and users said the gadgets are “very difficult” to secure. Only 25% of respondents said that security protocols or architecture built inside the devices adequately protect clinicians and patients.
Still, the lack of quality assurance and testing that lead to the vulnerabilities is pretty appalling. Respondents said that these are the reasons for the vulnerable code:
As far as the pacemaker-specific vulnerabilities go, Researcher Billy Rios and Dr Jonathan Butts from security company WhiteScope found that few manufacturers encrypt or otherwise protect data on a device or when that data was being transferred to monitoring systems.
Neither were any of the devices they looked at protected with the most basic authentication: login name and password. Nor did the devices authenticate the devices or systems to which they connect.
Rios agreed with the Ponemon Institute: the small size of devices and low computing power of internal devices make it tough to apply security standards that help to keep other devices safe.
There’s still work to be done, he said in a longer paper (PDF):
To mitigate potential impact to patient care, it is recommended that vendors evaluate their respective implementations and validate that effective security controls are in place to protect against identified deficiencies that may lead to potential system compromise.
In the paper, WhiteScope provided questions that vendors can use to evaluate device security.
Dr Larry Ponemon, co-author of the study that looked at the security of the broader medical device market, said that it’s urgent for the industry to prioritize security:
The security of medical devices is truly a life or death issue for both device manufacturers and healthcare delivery organizations.
One thing that should help would be for manufacturers to implement advice from the US Food and Drug Administration (PDF) about how to secure devices.
As it is, the study found, only 49% of manufacturers are now following that advice.