Updates as of 2017-05-15T17:15:00Z:
- Multiple news reports have focused on how this attack was launched using NSA code leaked by a group of hackers known as the Shadow Brokers. That’s certainly what seems to have happened based on SophosLabs’ own investigation. A more detailed report on that is planned for early next week.
- Sophos will continue to update its Knowledge Base Article (KBA) for customers as events unfold. Several updates were added today, and are summarized below in the “More guidance from Sophos” section.
- Microsoft took the highly unusual step of making a security update for platforms in custom support (such as Windows XP) available to everyone. The software giant said in a statement: “We know some of our customers are running versions of Windows that no longer receive mainstream support. That means those customers will not have received the Security Update released in March. Given the potential impact to customers and their businesses, we made the decision to make the Security Update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download here.”
- With the code behind Friday’s attack in the wild, we should expect copycats to cook up their own campaigns in the coming days to capitalize on the money-making opportunity in front of them, said Dave Kennedy, CEO and founder of information security consultancy TrustedSec.
- The attack could have been worse, if not for an accidental discovery from a researcher using the Twitter handle @MalwareTechBlog, who found a kill switch of sorts hidden in the code. The researcher posted a detailed account of his findings here. In the post, he wrote: “One thing that is very important to note is our sinkholing only stops this sample and there is nothing stopping them removing the domain check and trying again, so it’s incredibly important that any unpatched systems are patched as quickly as possible.”
***
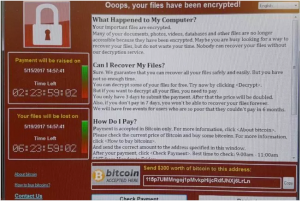
It was a difficult Friday for many organizations, thanks to the fast-spreading Wanna Decrypter 2.0 ransomware that started its assault against hospitals across the UK before spilling across the globe.
The attack appears to have exploited a Windows vulnerability Microsoft released a patch for in March. That flaw was in the Windows Server Message Block (SMB) service, which Windows computers use to share files and printers across local networks. Microsoft addressed the issue in its MS17-010 bulletin.
SophosLabs said the ransomware – also known as WannaCry, WCry, WanaCrypt and WanaCrypt0r – encrypted victims’ files and changed the extensions to .wnry, .wcry, .wncry and .wncrypt.
Sophos is protecting customers from the threat, which it now detects as Troj/Ransom-EMG, Mal/Wanna-A, Troj/Wanna-C, and Troj/Wanna-D. Sophos Customers using Intercept X will see this ransomware blocked by CryptoGuard. It has also published a Knowledge Base Article (KBA) for customers.
NHS confirms attack
National Health Service hospitals (NHS) in the UK suffered the brunt of the attack early on, with its phone lines and IT systems being held hostage. NHS Digital posted a statement on its website:
The UK’s National Cyber Security Centre, the Department of Health and NHS England worked Friday to support the affected hospitals, and additional IT systems were taken offline to keep the ransomware from spreading further.
Victims of the attack received the following message:
More guidance from Sophos
Here is an update of the specific ransomware strains in this attack that Sophos has now provided protection against:
| Threat name | Sophos IDE | Protection available since |
|---|---|---|
| Troj/Ransom-EMG | cerb-ama.ide | May 12, 2017 17:25 UTC |
| Mal/Wanna-A | wanna-d.ide | May 12, 2017 19:13 UTC |
| Troj/Wanna-C | wanna-d.ide | May 12, 2017 19:13 UTC |
| Troj/Wanna-D | wanna-d.ide | May 12, 2017 19:13 UTC |
| HPMal/Wanna-A | pdfu-bfo.ide | May 13, 2017 02:18 UTC |
| Troj/Wanna-E | rans-emh.ide | May 13, 2017 07:04 UTC |
| Troj/Wanna-G | rans-emh.ide | May 13, 2017 07:04 UTC |
| Troj/Dloadr-EDC | chisb-qv.ide | May 13, 2017 23:16 UTC |
| Troj/Agent-AWDS | chisb-qv.ide | May 13, 2017 23:16 UTC |
| Troj/Wanna-H | wanna-h.ide | May 14, 2017 02:53 UTC |
| Troj/Wanna-I | wanna-i.ide | May 14, 2017 06:38 UTC |
| Troj/Ransom-EMJ | wanna-i.ide | May 14, 2017 06:38 UTC |
| Troj/Wanna-J | emote-cb.ide | May 14, 2017 22:03 UTC |
| Troj/Wanna-K | emote-cb.ide | May 14, 2017 22:03 UTC |
As noted above, Sophos has issued protection for customers. Users of Intercept X and EXP don’t have to do anything. Users of Sophos Endpoint Protection and Sophos Home should update their versions immediately.
| Product | Actions |
|---|---|
| Sophos Intercept X | none required |
| Sophos EXP | none required |
| Sophos Endpoint Protection | update immediately |
| Sophos Home | update immediately |
Defensive measures
We urge those who haven’t yet done so to:
- Patch your systems, even if you’re using an unsupported version of XP, Windows 8 or Windows Server 2003 and read Microsoft’s customer guidance for WannaCrypt attacks.
- Review the Sophos Knowledge Base Article on Wana Decrypt0r 2.0 Ransomware.
- Back up regularly and keep a recent backup copy off-site. There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
- Be cautious about unsolicited attachments. The crooks are relying on the dilemma that you shouldn’t open a document until you are sure it’s one you want, but you can’t tell if it’s one you want until you open it. If in doubt, leave it out.
- Use Sophos Intercept X and, for home (non-business) users, register for Sophos Home Premium Beta, which stops ransomware in its tracks by blocking the unauthorized encryption of files.
Resources
Other links we think you’ll find useful:
- To defend against ransomware in general, see our article How to stay protected against ransomware.
- To protect against JavaScript attachments, tell Explorer to open .JS files with Notepad.
- To protect against misleading filenames, tell Explorer to show file extensions.
- To learn more about ransomware, listen to our Techknow podcast.
- To protect your friends and family against ransomware, try our free Sophos Home for Windows and Mac.
Techknow podcast — Dealing with Ransomware:
LISTEN NOW
(Audio player above not working? Listen on Soundcloud or access via iTunes.)



Gmd
What i am intrigued to know is how they managed a simultaneous attack of such magnitude at multiple locations? Was it downloaded over the last month & triggered by the date (unlikely or it risked being discovered), or does it really spread so fast from a server on the same network? (It takes time to encrypt files)
trefunny
curious to know more as well!
Mahhn
From what I’ve read- it sounds like the method of infection is that the systems are open on the internet, not firewalled over inbound 443. Once the worm is on a network hits everything it can with the credentials from each system it owns. I’ll bet there was a Shodan report pulled just before this started by the perpetrators to compile the main list of targets. (I say shodan, like the professor from Futrurama says Wernstrom)
Mahhn
If/when my other post shows up, correction: SMB ports 139 and 445
Xin
Me too as well !!!
Richard Andrew
From my experience of similar malware campaigns, they are usually sent out on mass to huge lists of email addresses. If the bad guys know the structure of an organisations email address (e.g. first name.surname@company.tld) they can also guess users from lists of names and surnames. Obviously this would generate lots of ‘postmaster’ responses, which is worth watching for in a SIEM. As is large numbers of emails with the same subject/sender/filename coming from an external email address. Had the NHS been keeping a close eye on their mail traffic they could have detected this threat sooner and mitigated or certainly reduced the extent of the damage caused. There are many other ways this attack could have been mitigated through proper defence in depth, it seems the NHS has failed on many levels. Another factor likely contributing to the magnitude of this attack is the use of an SMB vulnerability, effectively making this a ransomeware worm that spreads through a network. Most locky ransomware that I’ve seen doesn’t exhibit this so tends to remain localised to the initial machine (however many do look for files on network shares to encrypt too).
Laurence Marks
Didn’t you read the article before posting? WannaCrypt starts with a phishing email to introduce itself onto a subnet. WannaCry then spreads by using the Server Message Block (shared disk) vulnerability, no email required.
Stephen Cook
It appears not to have been a simultaneous attack. It progressed from a number of “seeds”, and probably started spreading several days previously. It only becomes apparent as a more significant problem once it gets beyond a certain critical point, when larger numbers of systems become infected.
Mossy Rock
What does “in custom support only” mean? Does this mean that you have to be engaged in some paid Microsoft service to get the patch, or is the patch available to everyone?
trefunny
everyone, usually you would need to pay for access to the new XP patches but this is an exception.
russell styles
I think that it means that you are running XP, Vista, or Win 8. They are not in general support.
Some people pay extra for continued support.
Microsoft is giving the patches away, if you can get through. The servers are busy.
Mahhn
Thank goodness the NSA went right to MS when they realized their exploit was being released into the wild so this could be patched, preventing this from ever happening. Where would we be without the NSA watching over us.
Danny Agro
Truly the NSA are our guardian angels…
Anonymous
Ransomware attacks what you need to know:
Stop using Windows XP. Im referring to home users but really, even businesses too. If a business claims they can’t upgrade to a better OS then they’re lying or being lazy.
You’re only helping the people that would harm computer systems.
Don Funkhouser
Not always. Quite often the hardware and/or software won’t function under a newer version of Windows. It isn’t due to lack of money or lazyness by the company using the system, it’s due to the manufacture not making or providing an update/upgrade. We aren’t talking about a regular PC running normal software here, but specialized hardware/software for mission critical purposes with absolutely NO upgrade path at all. Many don’t have newer products (even from other vendors) that can replace these systems. This is quite common in the medical field which is why they tend to be more vulnerable. There only option is to use the outdated and unsupported system or don’t provide what is in may cases life supporting services. They can’t let the people die so they are stuck between a wall and a hard place.
For the average home user or for basic word processing, accounting uses there is no legitimate excuse, but that doesn’t account for everyone.
Viktoria
Thank you for saying everything I intended to say but couldn’t…
Viktoria
I have to politely disagree. Many systems do not use older OS because they’re lazy, they use them because they’re better for the use they want to give them.
For example, even though USB ports have trumped the serial ports for many years now, some companies still use them because of the flaw the USB has of not being able to pass data from a certain distance.
You cannot simply ask them to switch so easily. There are many implications and variables.
FreedomISaMYTH
you do not work in a very large environment or are not in IT…
Bernhard Kanduth
Are there any Informations about the Decription of the Files, after a Payment was made? Do they provide a Key to unlock or not? If so how fast? Does it work?
Other Viruses like Cyberl0cker where realy fast, after the payment was made.
Lou1z
Thank goodness the NSA went right to MS when they realized their exploit was being released into the wild so this could be patched, preventing this from ever happening. Where would we be without the NSA watching over us.
????
The NSA were probably responsible for this and were using this technology long before it got out.
Just look at the Stuxnet saga.Between the Americans and Isrealis, they really screwed it up and gave rise to the state sponsored Cyber armies. There is now a race between countries to discover the next zero day exploit and try and get one over on the other.
And this lot want you to put your data in the cloud?? Not a flaming chance!!
Max
Sarcasm is not for everyone.
Danny Agro
Ah, the power of sarcasm…
Max
What I am still not quite sure of, is the SMB vulnerability only used to spread some payload that a potential target still needs to execute, or is this a ransomware that uses the exploit to already run itself on your system without you doing anything? I.e. can I be hit by this if I am on an unpatched system but I don’t execute anything?
Mark Stockley
Yes
Max
But someone on my network needs to have executed something, right?
vikas
How long this attack will comtiue and is there any news that this ransomeware attack is over or not????
Mark Stockley
It isn’t an attack, it’s an outbreak. The malware is in the wild now and will remain so until such time as there are no computers left to run it.
As a result of antivirus updates, better-late-than-never patching, the release of patches for unsupported operating systems from Microsoft, the so-called “kill switch” domains, firewall rule changes and no doubt many other ad-hoc measures the window of opportunity for the malware to spread is closing but it probably won’t close completely for years. For an object lesson in this take a look at Conficker https://nakedsecurity.sophos.com/2011/11/24/the-conficker-worm-three-years-and-counting/.
It’s why the antivirus on your computer doesn’t just detect the threats released last Friday but the entire history of malware. It’s all still out there.
Steve
“It isn’t an attack” OK… but take a look at the words in big type at the top of this page!
FreedomISaMYTH
a lot was learned about it from Friday when this was posted originally, to the 15th when Mark Stockley replied…
Magyver
Bill, Mark, I didn’t see Vista mentioned in the article. Is Vista automatically patched?
Kate Bevan
Yes, Vista was included in the initial patch in March https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
Anonymous
“…then people will continue to learn the hard way of sticking with old operating systems.”
Im probably preaching to the choir…