We typically think of malware as something used to steal data from corporations or knock down websites in politically motivated attacks. But if you’re a gamer, sometimes it’s simply a tool for winning.
SophosLabs threat researcher Tamás Boczán has been studying this trend, and recently gave a talk about it at BSides Budapest. This article reviews his findings and offers us a chance to share some of his presentation slides.
Anatomy of a cheat
In the presentation, Boczán explained his motivation for the gaming research:
I see a lot of different malware at Sophos, and I’ve also heard a lot about video game cheats. Then I started to dig into cheating, and I found that it’s very similar to malware. What I mean by cheat is a software for changing an online, competitive game in real time.
He shared video examples of what some of the cheating looks like, though we’ve chosen to only show still shots because advertising the behavior is illegal.
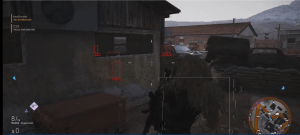
In one clip from Ghost Recon: Wildlands, he shows how the player can see things he shouldn’t. He can see from the frames where the enemies are behind the walls, and some data about them, like what weapon they are holding. The enemies here are other players:
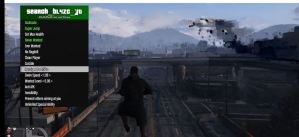
In another video sample for GTA online, we see that the cheater does a huge jump, then goes invisible. He couldn’t do these normally in the game, Boczán said.
The security industry’s baby brother
He said games are similar to malware in that their methods are exactly the same. The difference is in the purpose. Their economy is also similar. There are cheat groups and companies creating anti-cheat solutions, and there has been an arms race between them for 15 years. He added:
Both attacks and defenses got pretty sophisticated over the years. They are behind the security industry about five years, but comparable. They are like a little brother to the security industry.
He described the basic set-up of the games, in which many players are connected by a server, a mutual game state is computed and the attacker – the cheater, in this case – is one of the players. The goal is to gain an unfair advantage.
As cases of cheating have risen, so have the examples of anti-cheat technology from various companies. As various sides have upped the ante, both sides have drawn in people of greater skill. He said:
Hacking an online game is not that easy any more. In the old days, script kiddies could to do it, but now hacking is a serious game that requires a skilled attacker. So why would a skilled attacker waste their time and skill on a video game?
He mapped out the sequence of events this way:
- All this was originally about having fun.
- Then the gaming industry grew.
- The games went online.
- People began to cheat for profit, just as hackers often do when targeting companies.
- In response, an anti-cheating movement has sprouted up that mirrors security companies.
Evolution of cheating tactics
Boczán told his audience that the oldest cheating method is file injection. He mapped out the process:
- The cheater modifies game data or code in memory.
- They access memory through DLL injection.
- They find relevant structure and go to town.
- The goal is either to override some part of game data or code in memory.
Nowadays both cheat and anti-cheat developers are focused on this method, he said. Anti-cheat solutions heavily obfuscate the memory contents and try to detect injections.
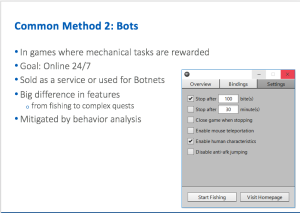
A second method is the use of bots, which he mapped out in this slide:
The wild cards
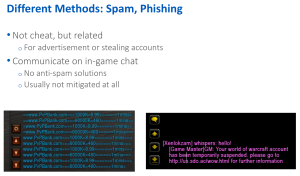
Spam and phishing are the wild cards in the world of game cheating. They don’t require technical skills, and they are the easiest way to steal accounts or advertise. He said:
Spamming can happen on the chat in-game, where there are no anti-spam solutions, and attacks are not mitigated at all.
In the following example, the window on the left is a spambot advertising a website. On the right is someone impersonating an admin of the game in a phishing attack:
Defensive measures
In a couple of slides, Boczán mapped out the defensive measures that are either in use or under development:
For the client side:
For the server side:
He said the anti-cheat software developers are following a similar trajectory as that of anti-malware software. Despite its problems, he said, behavioral analysis is taking more of a role in the defensive tools under development, and he has hope that such tools will work better in the near future. He also has hope for the tools under development that incorporate machine learning. He said:
About two weeks ago someone representing Valve announced that they’ll be doing machine learning as part of their anti-cheat solution, stepping on the same road some security companies have.
Though anti-cheating software developers have some work to do in improving their tools, Boczán said there are immediate actions users can take in the event they’re targeted by cheaters, though none of the options are perfect:
- Report the cheater to the game company, who will likely review it and ban the offender. Such a process does take weeks, though.
- The usual password and authentication rules apply here, specifically the use of complex passwords and two-factor authentication in games where it’s possible.
- If someone’s account gets stolen, they can report that too, and it will be restored in its current state after some time.



John
Pretty interesting. As shown in the case of Ghost Recon, ultimately the client has to know information about the other players including their position, weapons, etc. so it’s a matter of getting that information, which is already in the computer’s memory. The first trick is accessing it. Anti-cheat methods can look for loaded processes known to attach to the client or otherwise read memory, but more sophisticated cheats could appear in the form of applications that “root” your system and conveniently leave themselves out of the list of running processes altogether. The second trick is interpreting the information once you access it. While encrypting the data will help, the client application must have the means of decrypting, so cheaters only have to reverse engineer that. Not that any of these things are necessarily easy, but it seem that the cheaters have the advantage.
Anonymous
This all point at computer gaming, but also happens a lot on game consoles (PS & XBox mainly). I’ve been a victim of attacks on the games I’ve played online, not the console itself that left me with my game being hacked and ruined account. I’m not sure if game companies can do anything to stop that, but in the meantime I’ve heard they allow these kinds of practices, I mean modding on purpose which somehow lead to hacking. Very annoying and frustrating!