WikiLeaks has launched a new series of leaks on the US Central Intelligence Agency it calls “Vault 7”. It claims this will represent the largest dump of confidential documents on the agency in history.
The first full part of the series dropped Tuesday. Called “Year Zero”, this release yields 8,761 documents and files from an isolated, high-security network inside CIA headquarters in Langley, Virginia. If it proves to be authentic, then it paints an intimate picture of America’s cyber-espionage efforts.
Wikileaks said in its press release that Year Zero introduces the scope and direction of the CIA’s global covert hacking program, its malware arsenal and dozens of zero-day weaponized exploits against a wide range of US and European company products, include Apple’s iPhone, Google’s Android and Microsoft’s Windows and even Samsung TVs, which are apparently turned into covert microphones.
By the end of 2016, the CIA’s hacking division, which formally falls under the agency’s Center for Cyber Intelligence (CCI), had over 5000 registered users and had produced more than a thousand hacking systems, trojans, viruses, and other ‘weaponized’ malware. Such is the scale of the CIA’s undertaking that by 2016, its hackers had utilized more code than that used to run Facebook. The CIA had created, in effect, its ‘own NSA’ with even less accountability and without publicly answering the question as to whether such a massive budgetary spend on duplicating the capacities of a rival agency could be justified.
The CIA hadn’t yet confirmed or denied the information at the time of publication, but WikiLeaks does have a long track record of releasing top-secret government documents.
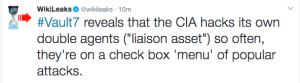
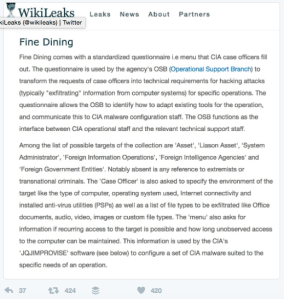
WikiLeaks made the following claims from Twitter:
For example:
So far, experts who have had a look say the document dump looks authentic. One is Dave Kennedy, CEO and founder at TrustedSec, an information security consultancy based near Cleveland, Ohio:
This looks to be tons of code, lots of capability overviews and tactics. This is the largest intelligence dump I think I’ve ever seen and it appears to be largely legitimate.
Kennedy said the documents show that the CIA hasn’t cracked strong-grade encryption, but that it has made a concerted effort to go after endpoints and mobile devices in order to circumvent encryption and eavesdrop on communications.
It also shows a number of methods for how they deployed implants, went after security technology and more. It appears they had vast methods for getting around the top security products out there to evade detection including more targeted approaches to EMET and more direct exploits.
We’ll update this story as details continue to unfold.

Mahhn
I will rest my final judgment until I’ve read most of it, but I will be surprised if the CIA turns out to be anything besides the scourge and shame of the US. But now with documentation for the first time. They do have an evil reputation, to say the least.
PF
Have there been any examples of Malware that Sophos has stopped?