Thanks to Dorka Palotay of SophosLabs for her behind-the-scenes work on this article.
Last week, we heard tell of a new ransomware strain dubbed Popcorn Time.
We didn’t write about it back then because it seemed like a bit of a publicity stunt.
The sample we analysed only encrypted files in a single test directory and the encryption process was just a placeholder, so it wasn’t so much ransomware as vapourware.
Sadly, the crooks seem to have put it a bit more effort over the weekend and come up with a new version that mostly works, and that has a couple of interesting angles in what you might call its “marketing spin”.
We aren’t aware of any emails in which this malware has been spammed out, so we’ll start at the point where, for some reason, you’ve either agreed to or been tricked into downloading and running the malware.
First, it pretends to be downloading and installing something:
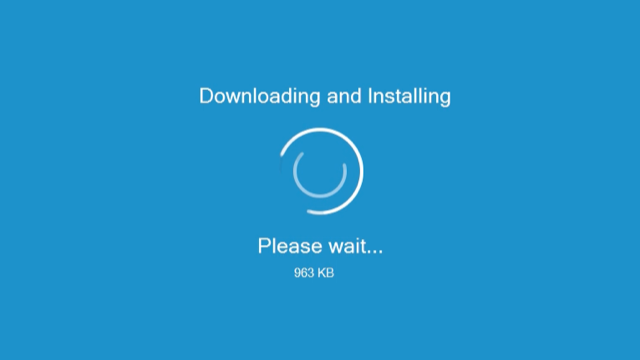
Ironically, considering how many malware attacks involve some sort of well-hidden download along the way, often triggered by document macros or a disguised JavaScript program, Popcorn Time isn’t downloading anything at this point.
This is just a cover story, or decoy, for what happens next, which leaves you at a page like this:
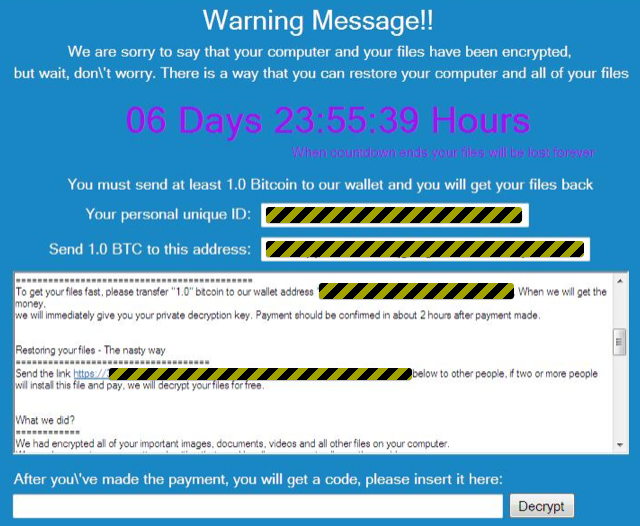
By this point, files in MyDocuments, MyPictures, MyMusic and your Desktop folder will be encrypted and renamed to end in .filock:
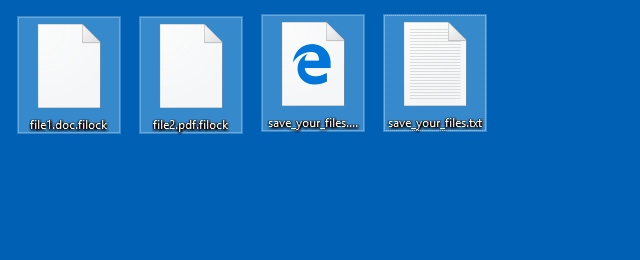
The crooks haven’t got their ransomware workflow quite right yet, because the save_your_files.html file that appears on the Desktop starts off by thanking you for paying and implausibly claiming that all the ill-gotten gains will be given to the needy:
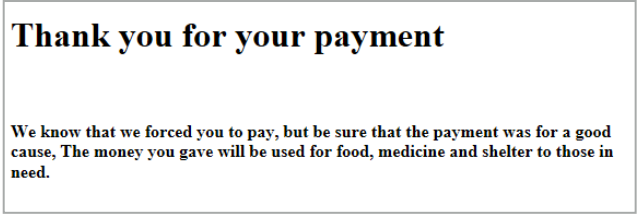
In fact, the ransom process has only just started, as you will see if you open the save_your_files.txt file, where the reason for the unlikely claim above is revealed:
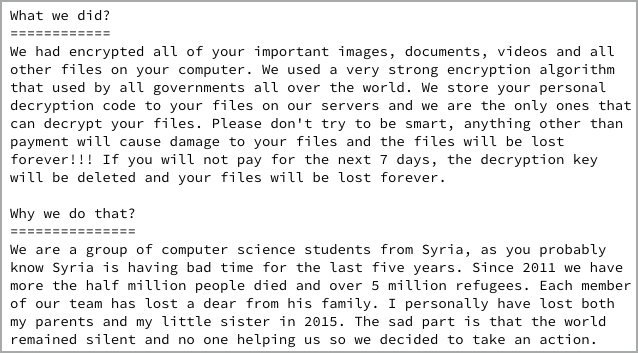
As well as playing the “charitable giving” card as an excuse for blackmail, the crooks have also introduced what we’re calling an affiliate program, by which you can get your files decrypted for free if you infect two other victims who pay up:
The link we’ve redacted above contains the same personal ID as the one on the pay page above, so it is plausible that the crooks could keep track of any downloads and subsequent ransom payments instigated by you.
Recovering without paying
Whether they actually do let you off the payment if you stitch up two or more other victims, we can’t tell you, but we can tell you that we were able to recover our own files without paying.
The encryption component of the sample we used for this article used a cryptographic key that was saved inside the malware executable, and when we pasted this key into the pay page shown above, we saw this sequence of popups:
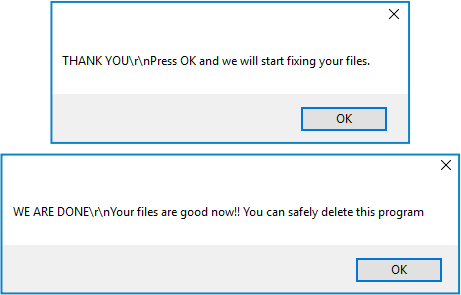
The encrypted files we showed above were, indeed, restored and the save_your_files files vanished from the desktop:

Entering a series of incorrect decryption codes, however, took us down a sequence of popups that went down this path:
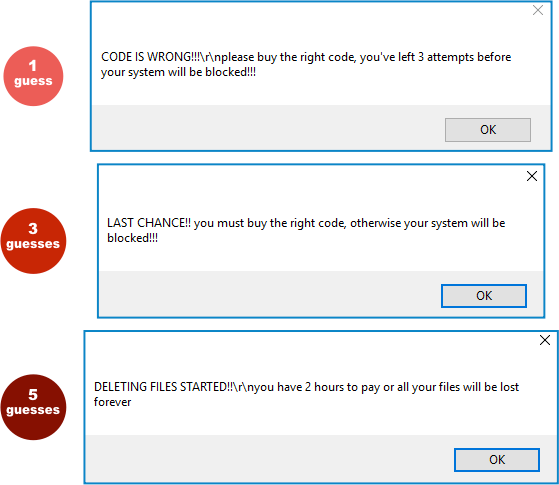
We didn’t wait for the specified two hours, so we can’t tell you what might have happened next.
What to do?
We don’t think that you’ll encounter this ransomware, and even if you do, you may be able to recover without paying.
(We didn’t share our decryption code above, just in case it uniquely identifies the sample that we analysed, but the key was recovered directly from the executable file.)
Whatever you do, if you are hit, don’t even think of trying to engage with the “affiliate program” offered by the crooks by passing the malware on to other people.
As far as we know, paying the ransom off your own bat is legal in most countries, but trying to evade the ransom by infecting someone else and hoping they’ll cover your costs is both morally and legally rotten.
As usual, your best defence is not to get infected in the first place:
Note. Sophos products block this malware as Troj/Ransom-EAV.
Image of popcorn by Bill Ebbesen via Wikimedia under CC BY-SA 3.0 licence.


Nikola Hadjinikolov
What about infecting two VMs :)
Dan
I doubt this would work, as the malware writers would probably add anti-forensic capability to the malware and as such wouldn’t allow it to run in a Virtual Machine.
Alan
According to the article, just infecting somebody else isn’t enough. Two of your victims need to pay in order to unlock your files.
Paul Ducklin
Indeed…your affiliate bonus isn’t paid when two “prospective customers” install the malware, but when two actual victims pay up. So you’d have to spend BTC 2 to save BTC 1 :-)
John
What kind of human POS would do this to “friends”, or anyone else for that matter?!
Guy Vegoda
I guess to the people of such high moral caliber as to actually write the ransomware in the first place, this doesn’t sound unreasonable option.